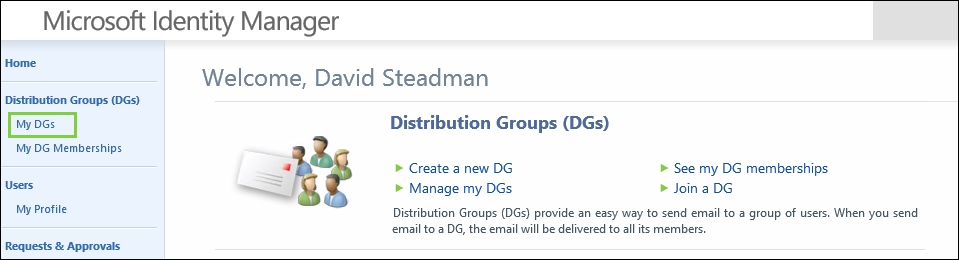
Once you have user management in place, it is usually time to start looking at group management. In many MIM implementations that we have done, group management capability has been the key reason for choosing MIM. Yet, in order to manage groups, we need to also have the users, who are supposed to be members, managed by MIM.
In this chapter, we will look at the following topics in depth:
Group scope and types
Modifying MPRs for group management
Creating and managing distribution groups
Managing groups in AD
Installing client add-ins