If you have followed this book, you will now have a freshly installed FIM 2010 R2 environment. In this chapter, we will discuss some of the basic configurations we need to look at, no matter how our environment looks or how we plan to use FIM 2010 R2.
If you have an environment already set up, I hope that this chapter can act as a guide for you to verify that you have not missed any important steps causing your FIM environment to not work properly.
In this chapter we will focus on the initial configuration of FIM Synchronization Service and FIM Service. Specifically, we will cover the following topics:
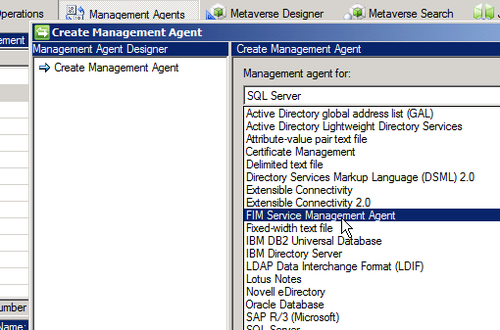
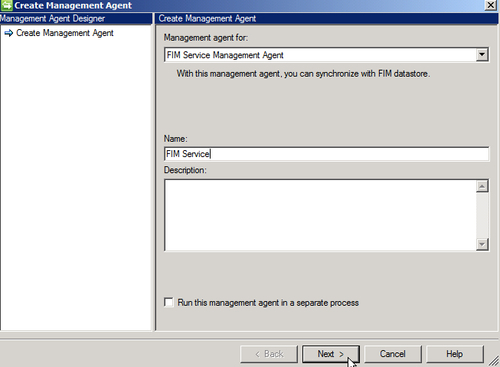
Creating Management Agents
Schema management
FIM Service MA
Initial load versus scheduled runs
Moving configuration from development to production