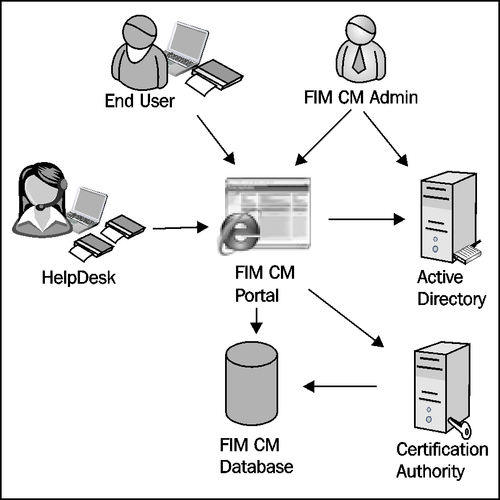
We have earlier stated that FIM CM is the outcast of the FIM product family. In this chapter, we will take a look at how we can use FIM CM to issue Smart Cards. FIM CM is not a requirement for starting to use Smart Cards, but as you will see, FIM CM will add a lot of functionality and security to the process of managing the complete lifecycle of your Smart Cards.
In this chapter, we will look at:
How to run the FIM CM configuration wizard
Installing and configuring the FIM CM CA files
An example of allowing a manager to enroll a certificate on behalf of a consultant