Introduction
This chapter covers the eighth objective in Domain 4.0, Security Operations of the CompTIA Security+ Exam.
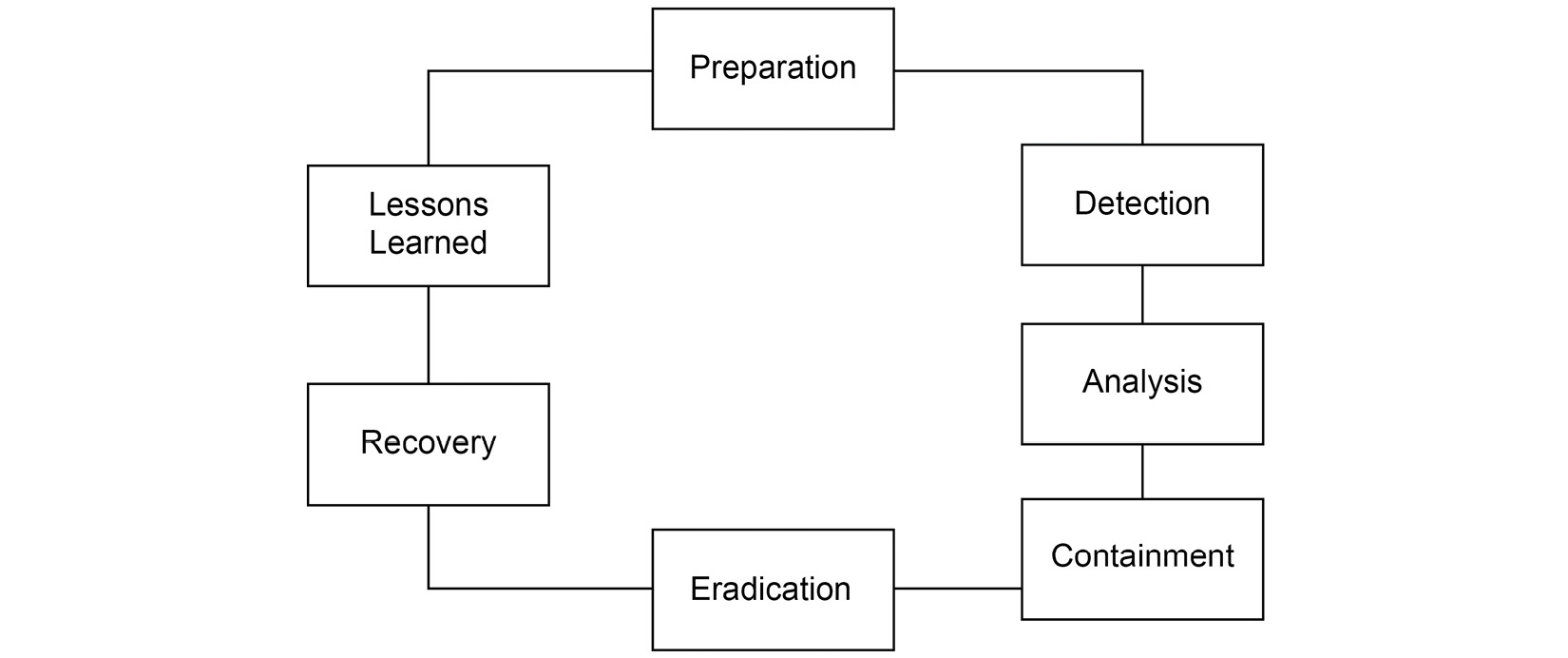
In this chapter, we will review the incident response process, paying particular attention to the sequence of stages from preparation to lessons learned in our post-response analysis.
We will also discuss training practices, including interactive exercises and other methodologies, to prepare the team to deal effectively with these incidents. The final sections will explore root cause analysis, threat hunting, and digital forensics.
This chapter will give you an overview of how modern IT departments respond to security incidents and ensure you are prepared to successfully answer all exam questions related to these concepts for your certification.
Note
A full breakdown of Exam Objective 4.8 will be provided at the end of the chapter.