What is a Microsoft OS?
As a forensic examiner, understanding the concept of an OS is crucial. Microsoft announced Windows for the first time on November 10, 1983, as a graphical user interface (GUI) that provided users with a friendly interface and layer to interact with the command-line-based MS-DOS code that was released previously. This started a new era for user interfaces and made it easy for people who did not know how to interact with a disk operating system (DOS) to work and learn with computers.
According to the latest articles and research, a Windows OS is installed on almost 76% of devices across the globe (desktop and laptop). The desktop OS market share is illustrated in Figure 1.1:
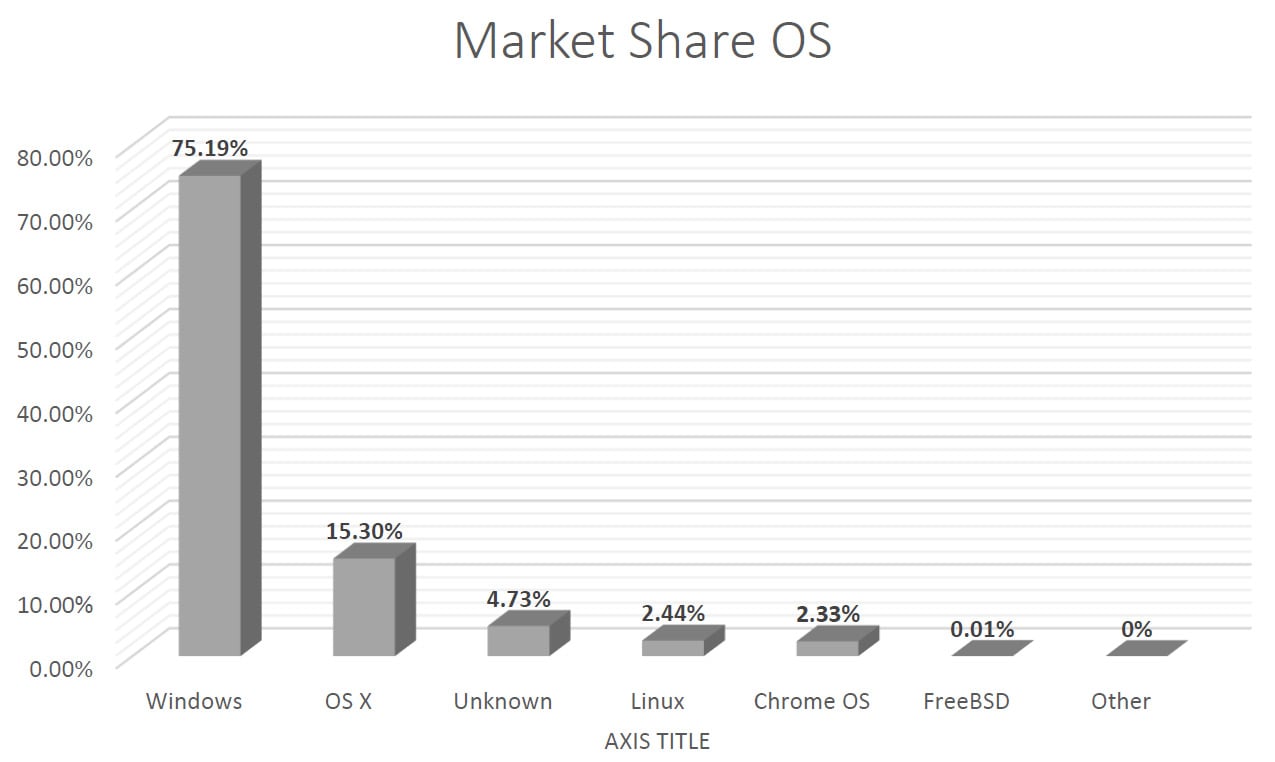
Figure 1.1 – Desktop OS market share
As we can see in the preceding chart, Microsoft OSs dominate the market for desktops and laptops. Microsoft developed multiple versions of the Windows OS including Windows NT, Windows NT 3.1, and most famously, Windows XP, to name a few.
We now know that the Windows OS is one of the most widely used OSs in the world, providing an interface between the user and the computer hardware. The main components of the Windows OS are the kernel, drivers, system utilities, and user-mode components. In this part of the book, we will take a closer look at each of these components and their roles in how the Windows OS functions:
- Kernel: The kernel is the core component of a Windows OS. It is responsible for managing the system’s resources, such as memory, process scheduling, and input/output operations. The kernel also provides an interface between the user-mode components and the hardware. The Windows OS uses a hybrid kernel that combines the features of a microkernel and a monolithic kernel. The microkernel approach provides a small, secure, and stable kernel that is responsible for managing the basic system resources. The monolithic kernel approach provides a single, large, and complex kernel that is responsible for managing both basic system resources and more advanced features, such as device drivers.
- Drivers: Drivers are software components that allow an OS to interact with a computer’s hardware. They act as intermediaries between the OS and the hardware, translating the requests from the OS into instructions that the hardware can understand. A Windows OS includes a wide range of drivers, including device drivers, filesystem drivers, and network drivers.
- System utilities: System utilities are software components that provide basic functionality to an OS. They are responsible for tasks such as disk defragmentation, disk cleanup, and system backup and restore. Some of the most commonly used system utilities in a Windows OS include Task Manager, Control Panel, and File Explorer.
- User-mode components: User-mode components are software components that provide a user interface to an OS. They allow users to interact with the OS and perform tasks such as creating, editing, and deleting files, launching applications, and accessing system settings. Some of the most commonly used user-mode components in the Windows OS include the Start menu, the desktop, and the taskbar.
- Security component: A Windows OS plays a critical role in protecting a user’s data and the system itself from various threats such as viruses, malware, and hacking attacks. There are several security components and functionalities in the Windows OS that work together to provide a secure environment for users, such as the following:
- User Account Control (UAC): UAC is a feature in Windows OSs that helps prevent users from making unauthorized changes to the system by requiring them to enter their credentials beforehand. This helps prevent malicious software from making unauthorized changes to the system, such as installing malware or modifying system settings.
- Windows Defender: Windows Defender is a built-in antivirus software that provides real-time protection against malware and other threats. It uses a combination of signature-based detection and heuristics-based detection to identify and remove malware, and it also provides regular updates to keep its threat definitions up-to-date.
- Windows Firewall: The Windows Firewall is a network security system that helps protect a system from unauthorized access by controlling incoming and outgoing network traffic. It provides a range of configuration options, including the ability to block incoming traffic, allow outgoing traffic, and create rules to allow or block specific traffic.
- BitLocker: BitLocker is a full-disk encryption feature that helps protect user data by encrypting an entire hard drive. It provides a secure environment for sensitive data and helps prevent unauthorized access to data if a system is lost or stolen. This is one of the challenges we face as forensic investigators; if an acquired image is encrypted, then a decryption key is needed to perform memory forensics.
- Security Accounts Manager (SAM): SAM is a component of a Windows OS that manages user accounts and security policies. It is responsible for maintaining a database of user accounts and their associated security policies, such as password policies, account lockout policies, and access control lists.
- Internet Explorer Security: Internet Explorer is the default web browser in a Windows OS, and it includes several security features to help protect users while browsing the web. These features include security zones, which allow users to specify the level of security for different websites, and ActiveX controls, which help prevent malicious software from being installed on the system.
- SmartScreen Filter: SmartScreen Filter is a feature in a Windows OS that helps protect users from downloading and running malicious software by analyzing the contents of downloaded files and warning the user if the software is known to be malicious.
- Windows Management Instrumentation (WMI): WMI is a set of tools and technologies that allow you to manage Windows-based computers. WMI can be used to automate administrative tasks, collect data about computers, and monitor computer health.
In addition to these main components, a Windows OS also includes a number of additional features and components such as the registry, the filesystem, and the security model. The registry is a database that stores information about the system configuration and the installed applications. The filesystem is responsible for organizing and managing files and directories on a computer’s hard drive. The security model is responsible for enforcing the system’s security policies and controlling access to the system’s resources.
One of the key strengths of a Windows OS is its compatibility with a wide range of hardware and software. This is achieved through the use of device drivers, which allow the OS to interact with a wide range of hardware devices such as printers, scanners, and digital cameras. The Windows OS also includes support for a wide range of filesystems, including New Technology File System (NTFS), File Allocation Table (FAT), Extensible File Allocation Table (exFAT), and Resilient File System (ReFS), making it easy for users to access their files and data on different types of storage media.
Another important feature of a Windows OS is its user-friendly interface. The OS includes a range of GUI elements such as icons, windows, and menus that make it easy for users to navigate and interact with the system. The Start menu provides a central location to access system utilities and installed applications, while the desktop provides a convenient workspace for performing tasks and accessing files and folders.
Understanding the Windows OS and its filesystem is crucial for forensic investigators. With the knowledge gained from this chapter, investigators will be able to effectively collect and analyze digital evidence.
In the next main section, we will delve into the history of the Windows OS, exploring its various versions and features and how they have evolved over time. This knowledge will provide a solid foundation for understanding the inner workings of the OS, which is essential for conducting thorough digital investigations.

