Digital forensics and common terminology
In this section, we will delve into the basics of digital forensics by discussing the common terminology, types of investigations, and the overall process involved. This will deepen your understanding of a digital forensics life cycle and offer insights into each stage of the process. We will also take a closer look at how typical casework is carried out.
What is digital forensics?
Digital forensics, also known as computer forensics, is the branch of forensic science that deals with the preservation, collection, examination, and analysis of electronic data to investigate digital-related crimes and incidents. The goal of digital forensics is to uncover and recover evidence from digital devices such as computers, smartphones, and other electronic devices, and use this evidence in criminal and civil investigations.
Digital forensics is a multidisciplinary field that draws on expertise from various areas such as computer science, information technology, and law enforcement. Digital forensics experts use a variety of tools and techniques to perform their investigations including data acquisition, data analysis, and data visualization. They must be familiar with a wide range of OSs, software applications, and file formats, and must be able to navigate the intricacies of digital data storage and retrieval.
Digital forensics is used in a variety of contexts including cybercrime investigations, intellectual property disputes, civil litigation, and other legal proceedings. Digital evidence is often critical to the outcome of these cases, and digital forensics plays a key role in uncovering and preserving this evidence. Digital forensics is also used to determine the cause of security breaches and system failures, and to identify potential vulnerabilities in digital systems. In the modern era of technology, digital forensics is an important part of analyzing suspicious cybercriminal attacks with the objective of identifying them. The mitigation and eradication of threat actors is a critical aspect of the work performed by digital forensics and incident response engineers and consultants.
There are several types of computer forensics, each of which is used for specific purposes and requires different techniques and approaches. Some of the most common types of computer forensics include the following:
- Criminal forensics: Criminal forensics is a type of computer forensics that is used in the investigation of criminal activities such as cybercrime, hacking, identity theft, and other digital-related crimes. Criminal forensics focuses on uncovering and preserving evidence that can be used to prosecute the individuals responsible for these crimes.
- Civil forensics: Civil forensics is a type of computer forensics that is used in civil litigation such as intellectual property disputes, contract disputes, and other civil proceedings. Civil forensics focuses on uncovering and preserving evidence that can be used to support or refute a party’s claims in a legal case.
- Incident response forensics: Incident response forensics is a type of computer forensics that is used to investigate and respond to security breaches and other incidents that impact the security and integrity of digital systems. Incident response forensics focuses on identifying the cause of the incident, assessing the extent of the damage, and developing a plan of action to prevent future incidents.
- Network forensics: Network forensics is a type of computer forensics that focuses on the examination of network traffic and system logs in order to uncover evidence of security breaches, cyberattacks, and other network-related incidents. Network forensics involves the use of specialized tools and techniques to capture and analyze network traffic, and to identify and track the source of the incident.
- Mobile forensics: Mobile forensics is a type of computer forensics that focuses on the preservation, collection, examination, and analysis of data stored on mobile devices such as smartphones and tablets. Mobile forensics is often used in criminal investigations but can also be used in civil and incident response forensics.
- Live forensics: Live forensics is a type of computer forensics that involves the collection and analysis of data from a live computer system while it is still running. Live forensics is often used in incident response forensics, and it is considered a critical component of the incident response process because it can provide valuable insight into the state of a system at the time of an incident.
- Memory forensics: Memory forensics is the branch of digital forensics that focuses on the examination of a computer’s volatile memory, or RAM. The goal of memory forensics is to uncover information that is stored in memory and to use this information to assist in the investigation of digital crimes and incidents. Memory forensics can be used to uncover information about system processes, network connections, and malicious activity, and is considered a critical component of the digital forensics process because it can provide valuable evidence that would otherwise be lost if a system were shut down. Memory forensics requires specialized tools and techniques to capture and analyze data stored in memory, and it is often used in conjunction with other forms of digital forensics to provide a comprehensive understanding of a digital incident.
Regardless of the type of computer forensics, the process typically involves several key phases, including the following:
- Preservation: The preservation phase involves the collection and preservation of evidence in a manner that ensures its authenticity and integrity. This often involves making a forensic image of the evidence and storing it in a secure location.
- Collection: The collection phase involves the acquisition of evidence, which may involve the use of specialized tools and techniques to capture data from the source. The collection phase is critical to the success of the investigation, as it is important to collect as much evidence as possible in order to ensure a comprehensive examination.
- Examination: The examination phase involves the analysis of evidence to uncover relevant information and identify potential sources.
The future of digital forensics is promising. The increasing reliance on digital technology in all aspects of our lives will continue to drive the need for forensics experts who can investigate and resolve digital crimes and incidents.
As technology continues to evolve, digital forensics will also need to adapt to new and emerging technologies. For example, cloud computing, the Internet of Things (IoT), and blockchain will all present new challenges and opportunities for digital forensics experts.
Artificial intelligence and machine learning are also expected to play a major role in the future of digital forensics. These technologies can be used to automate the process of data collection and analysis, making it faster, more efficient, and more effective.
With the increasing number of digital crimes and incidents, the demand for digital forensics experts is expected to continue to grow in the coming years. This provides a bright outlook for those interested in pursuing a career in this field.
A forensic analyst/examiner should have a great detailed understanding of the operating system to be able to identify the proper evidence related to incident or case he is working on, and document his finding based on analyzed evidence.
While we are conducting an examination of forensic artifacts, the main goal is to investigate digital crime, which is an illegal activity committed using a digital device such as a PC or mobile device, and extract the evidence via a proper forensic process to present it. Also, the evidence extracted needs to be preserved with integrity; in some cases, the examiner might need to recover evidence such as deleted files to justify an action or point to a suspected criminal.
As a forensic examiner or analyst, it is important to have a comprehensive understanding of various aspects of digital forensics, including the following:
- Technical knowledge: A strong understanding of computer systems, software, and hardware is essential for a forensic examiner or analyst. This includes knowledge of OSs, filesystems, data storage, and networking concepts.
- Legal knowledge: Forensic examiners need to be familiar with the laws and regulations that govern digital forensics, including privacy laws, data protection laws, and intellectual property laws. They also need to understand how to preserve the chain of custody of digital evidence and how to present evidence in a court of law.
- Investigative techniques: Digital forensics is an investigative process, so it is important for forensic examiners to have a thorough understanding of the methods and techniques used in conducting a digital investigation. This includes knowledge of data collection, analysis, and preservation techniques, as well as the use of specialized tools and software.
- Communication skills: Digital forensics is a complex and technical field, so it is important for forensic examiners to have strong communication skills in order to effectively explain their findings to others. This includes the ability to translate complex technical information into layman’s terms and to present findings clearly and concisely.
- Professional ethics: Digital forensics involves access to sensitive and confidential information, so it is important for forensic examiners to understand and adhere to professional ethics and standards. This includes being impartial and unbiased in their analysis, maintaining confidentiality, and protecting the privacy of individuals.
- Continuing education: Technology is constantly evolving, so it is important for forensic examiners to stay up-to-date with the latest developments and techniques in the field. This requires a commitment to ongoing learning and professional development.
By developing a deep understanding of these key areas, forensic examiners and analysts can become effective and professional in their work, contributing to the advancement of the field of digital forensics and providing valuable support to law enforcement and organizations in the fight against cybercrime.
Cybercriminals
Cybercriminals are individuals or groups who engage in illegal activities using digital technology. They use the internet, computer systems, and other digital technologies to carry out a variety of crimes including hacking, identity theft, fraud, extortion, and intellectual property theft. These individuals often operate in secret, making it difficult to detect and prevent their criminal activities. They can target individuals, organizations, and even entire governments, and can cause significant harm by stealing sensitive information, disrupting critical systems, or causing financial losses.
Digital forensic terminology
When working as a forensic examiner, you will, on a daily basis, encounter people talking about certain terms when it comes to investigation. Understanding the terminology helps us as examiners to communicate properly – for example, when we talk about a forensic image, what do we mean? Do we need a full image or a triage image? What are SSD and HDD?
In this section of the book, we will cover most of these terms. The following table lists some useful keywords for a digital forensic analyst:
|
Keyword |
Description |
|
Acquisition |
The stage in a computer forensics investigation where the data involved is collected |
|
Allocated space |
The logical area on a hard disk or other media assigned to a file by the OS |
|
Bit |
The smallest unit of measurement used to quantify digital data |
|
Bit-by-bit copy |
A copy of every consecutive sector on a hard disk or other media, without regard to the allocation of data |
|
Chain of custody |
A detailed record of the handling and control of digital evidence from the time it is collected until it is presented in court; used to demonstrate the authenticity and integrity of the evidence and to establish the credibility of the investigation |
|
Disk mirroring |
When data is copied to another hard disk or another area on the same hard disk in order to have a complete, identical copy of the original |
|
File carving |
A process used to recover files and data from unallocated disk space or damaged filesystems; involves identifying and extracting complete files based on their unique file headers and footers |
|
File format |
The structure by which data is organized in a file |
|
Forensic image |
A forensically sound and complete copy of a hard drive or other digital media |
|
Hash value |
The numerical value of a fixed length that uniquely identifies data |
|
Live analysis |
The process of performing an on-the-spot analysis of digital media, rather than switching it off and shutting it down |
|
Metadata |
Data that is stored in a filesystem or the header of a file, and provides information about the file |
|
Registry hives |
Subfiles that make up a Windows registry; individual Windows user settings and some histories of usage are kept in various hives and can be updated as a computer is used |
|
Steganography |
Hiding information within a seemingly ordinary message so that only the intended recipient knows of its existence |
|
Unallocated space |
The free space on a hard drive that can be used to store data |
|
Write block |
Hardware and/or software methods to prevent the modification of content on a media storage unit, such as a CD or thumb drive |
Table 1.1 – Terminologies for digital forensics
Important note
We will cover forensic artifacts of Windows separately in upcoming chapters. Each artifact will be explained and analyzed, so be prepared to be amazed by how rich Windows is when it comes to artifacts.
To become a great digital forensics examiner, you need to have a strong foundation in informatics and computer science. Many people, like me, started their careers on helpdesks, as computer technicians, or in IT security, where they gained familiarity with some of the tools needed to recover data. If you have similar experience, this book will help you prepare for your dream career as a digital forensics investigator.
The process of digital forensics
Like any other science branch, digital forensics has its own processes and procedures to follow. The following is a brief explanation of each step:
- Identification: This is the first step in the digital forensics process and involves identifying the need for a digital forensics investigation. This may be the result of cybercrime, such as hacking or data theft, or it may be part of a larger investigation, such as an internal audit or compliance review.
- Preparation and preservation: Before conducting any type of digital forensics investigation, it is important to prepare and plan for the process. This includes identifying the goals of the investigation, determining the scope of the investigation, and obtaining the necessary resources and equipment. It is also important to preserve evidence in its original form. This includes making copies of data and storing it in a secure and tamper-proof manner.
- Collection and evidence seizure: This is the first step in the actual investigation process. The goal of this phase is to preserve the evidence and prevent any potential modification or destruction of data. This can involve seizing physical devices, such as computers and storage media, or collecting data from a remote source, such as a cloud service.
- Examination and analysis: In this phase, the forensic examiner will examine the collected data in detail in order to identify relevant information and evidence. This may involve the use of various tools and techniques, including file carving, data extraction, and data analysis.
- Documentation and presentation: In some cases, a forensic examiner may be required to present their findings in a court of law or other legal proceedings. This requires clear and concise communication skills and the ability to explain complex technical information in a way that is easily understandable to non-technical audiences.
When conducting an investigation using the aforementioned process, taking detailed notes of each step and action is critical to ensuring that the evidence is not tampered with. Additionally, if another examiner is collaborating with you during the investigation, having detailed notes can facilitate effective communication and ensure that everyone is on the same page.
The five key steps of this process are illustrated in Figure 1.3:

Figure 1.3 – Digital forensics process steps
Digital evidence
Digital evidence can be any form or type of digitalized file or media from an electronic source, including logs, files, social media posts, and much more.
Conducting a forensic examination requires knowledge of the technical concepts of digital evidence, such as computers. You need to know the main components and how they are structured, as well as the type of digital media to handle the evidence. In this book, we will cover some technical theory before jumping into practical analysis for each evidence type.
Some of the digital evidence types are as follows:
- User activity generated in an endpoint
- Documents and text files
- Audio and video files, including CCTV
- Digitalized images
- Security control logs, such as IDS and PCAP
- Digital file metadata
For example, let’s take metadata, which is data about data. Most digital files hold valuable information that adds forensic value to an investigation, such as who created a file, owner information, and creation time, as we can see in the following screenshot, which illustrates the use of ExifTool, which displays metadata for a file:
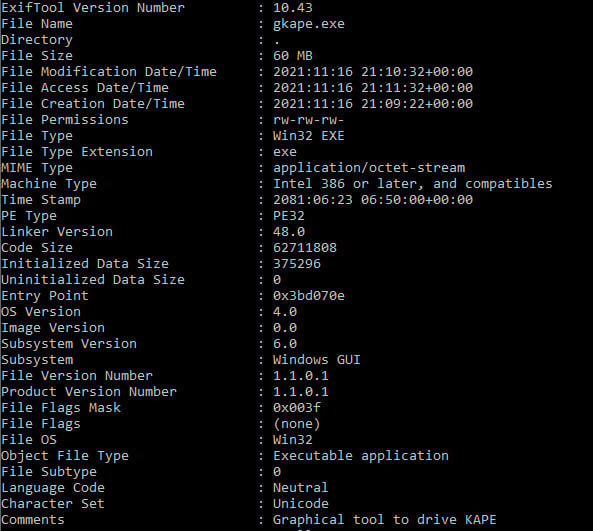
Figure 1.4 – ExifTool output for an executable Kroll Artifact Parser and Extractor (KAPE)
With the fast growth in technology and types of digital evidence, when dealing with different types of incidents and cases, we need to focus on the most important type of evidence. When collecting digital evidence, an examiner needs to know that they can lose data once a system is shut down – in the case of a computer, for example. When responding to an incident, the most immediate priority should be collecting volatile data.
Volatile data refers to information that is stored in temporary memory and lost when a system is powered off. This includes data stored in a system’s random-access memory (RAM) and any data that is being processed or temporarily stored in a cache.

Figure 1.5 – RAM sample image
Volatile data can include active system processes, network connections, and open files and applications. In a digital forensics investigation, capturing volatile data can provide valuable information about the state of a system at a specific point in time.
On the other hand, non-volatile data refers to information that is stored on a persistent storage device, such as a hard drive, which remains intact even when a system is powered off. Non-volatile data can include files, documents, images, and system configurations. In a digital forensics investigation, non-volatile data can provide a more comprehensive view of the system’s history and activity.
It is important to note that while volatile data can be lost when a system is powered off, it can still be captured and analyzed through a process known as live analysis. This involves collecting data directly from a live system, without first creating a forensic image of the data. Live analysis is typically used in time-sensitive investigations or when it is not possible to obtain a forensic image of the data.
In digital forensics, it is critical to preserve and analyze both volatile and non-volatile data in order to obtain a complete picture of a system’s activity and state. Volatile data can provide insight into the current state of the system, while non-volatile data can provide a historical view of the system’s activity. By combining these two types of data, forensic examiners can build a more comprehensive and accurate picture of the system’s behavior and any potential digital evidence.
In the upcoming chapters, we will talk about the acquisition of a memory image and how to perform analysis of a memory image.
In the next section, we will explore the concept of Windows Shadow Copy and its significance in digital forensics and incident response.

