The three key pillars of PowerShell
PowerShell has three key pillars:
- Cmdlets: Small programs that do useful things, such as retrieve a set of files in a folder. Some cmdlets come with PowerShell, some come with applications and services, and you can leverage a huge library of third-party tools.
- Objects: Data structures representing entities within your computer and containing properties and methods. Cmdlets can consume and produce objects.
- The pipeline: The pipeline enables you to chain two cmdlets – the output of one cmdlet is sent, or piped, to a second cmdlet.
Cmdlets
Cmdlets are small programs that do useful things, such as getting the details of all the running processes. Cmdlets developers write these cmdlets as .NET classes, typically using C#.
Cmdlets come either with PowerShell itself or as part of an application such as VMware or the various Windows Server features. In Chapter 5, you can read more about the tools you can use to manage Windows, including the Remote Server Administration Tools (RSAT).
Cmdlets are named using a strict noun-verb syntax, based on a restricted and well-known set of verbs. For example, you use the Get-Process command to get details of the processes. Likewise, you would use the Get-Service command to get details of all the services on a system. The strict naming of cmdlets is a great feature that helps you to discover other cmdlets.
Cmdlets take parameters that affect how the cmdlet operates. You specify a parameter with a parameter name (which always begins with a - character) and usually some value. For example, if you wanted to get details on the DHCP client service running in Windows 11, you would type as follows:
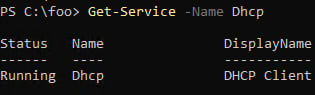
Figure 2.6 – Using Get-Service to view a Windows service
For more details on Powershell cmdlets, see https://packt.link/f9ZTD.
Objects
In PowerShell, an object is a data structure that contains properties and methods about some entity, such as a file or a Windows process. The properties of an object are specific attributes of that object, such as the file’s full name or the process’s current CPU usage. You can create objects using cmdlets (for example, the Get-Process command returns objects of the system.process.diagnostics type).
You use objects in PowerShell when you manage Windows and write scripts to automate some activity, such as deleting all the files in temporary folders. Objects are fundamental to PowerShell and are great at simplifying scripting.
A benefit of objects is that the details of the object are easy to view. Just pipe the output of a cmdlet to Get-Member, and you can discover precisely what is inside each object. There is no prayer-based text parsing, as is more usual in Linux environments. See https://packt.link/KULU6 for an explanation of prayer-based parsing.
For example, you can get details of the optional features available In Windows 11 using the Get-WindowsOptionalFeature cmdlet. When you use this cmdlet, PowerShell returns an array of objects, each representing one of the optional features. You can then pipe the output of that command to Get-Member to show what is inside each object occurrence like this:
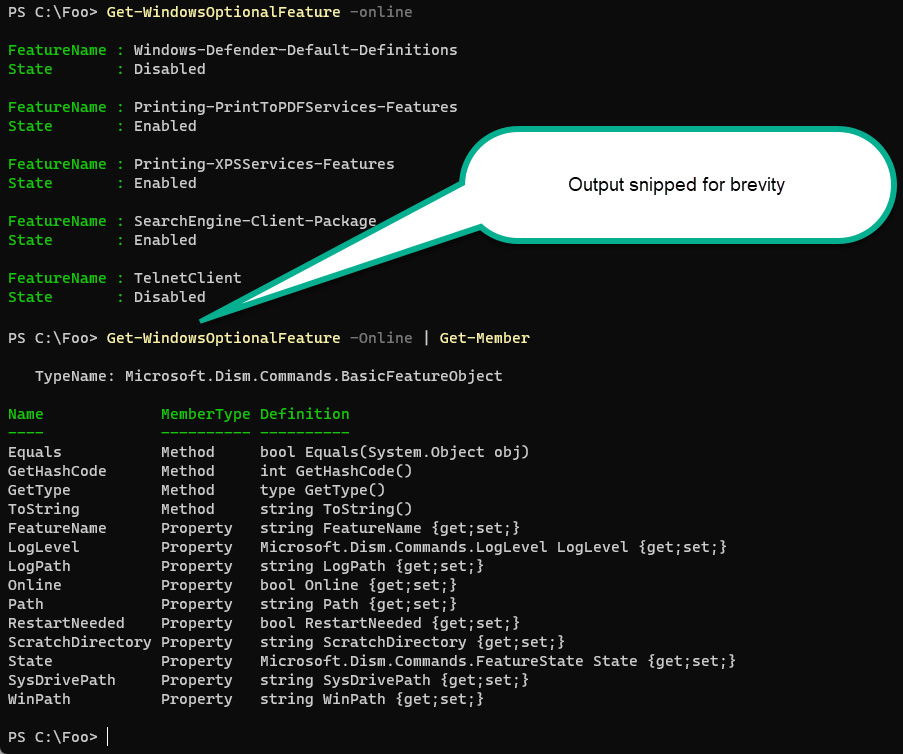
Figure 2.7 – Using Get-Member
When you automate Windows optional feature management, you easily discover that the property’s name, holding the feature’s current status is state. As you use PowerShell, this behavior becomes more and more useful.
For more details about objects inside PowerShell, see https://packt.link/QKxyh.
The pipeline
The pipeline is a feature of PowerShell that takes the objects a command creates and uses them as input for another PowerShell command. You use the | character to indicate the pipe operation, which you saw previously when you piped the output of the Get-WindowsOptionalFeature to the Get-Member command. The first cmdlet produced several objects (one for each Windows optional feature). By sending those objects to the next cmdlet, Get-Member can tell you what those objects look like.
The incredibly powerful pipeline enables you to create simple scripts to accomplish complex tasks. For example, suppose you wish to know which company made the software that uses the most virtual memory on your system. On Windows 11, each running application uses one or more (or a lot more) Windows processes. So, we can do this:
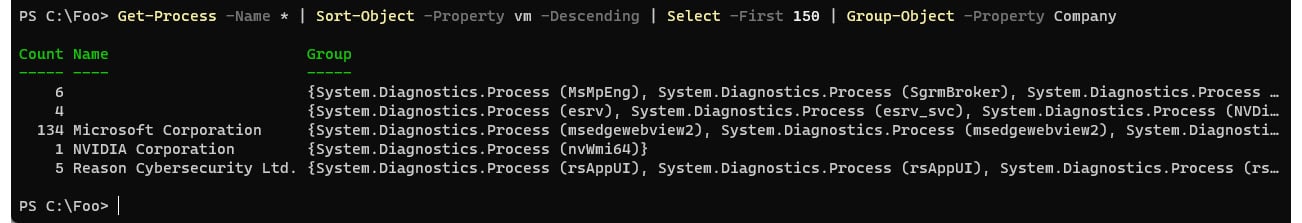
Figure 2.8 – Using the pipeline
In this example, you use Get-Process to get all the processes on your system. Powershell returns a process object for each Windows process. You then pipe it to Sort-Object to sort the objects based on VM usage (with the greatest VM usage sorted to the top). Then you take the top 150 of those processes (that is, the 150 processes using the most VM) and group them by the company attribute of the process object, which should be the application manufacturer. However, some apps do not populate that property!
PowerShell rests on top of .NET, so each PowerShell object, each service, each process, and so on is a .NET object. .NET provides a rich set of objects that enable you to interact with all the key Windows services and applications. In many cases, PowerShell is merely a wrapper around the functionality provided within .NET.
For more information on the pipeline, see https://packt.link/QVl4S.
Understanding these three pillars is fundamental to learning and mastering PowerShell.

