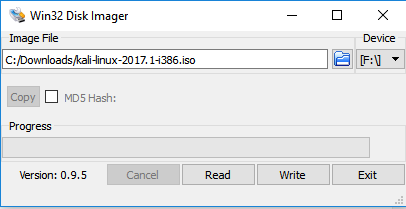
As you will see in the pages that follow, there are a tremendous number of uses for Kali Linux, and for these uses, it is not always practical to dedicate a device to one particular use case, as this would be a tremendous waste of resources. To address this, you can use the Kali Linux installation ISO downloaded in the previous section as a live CD as well; or you can maintain persistence with a live USB drive with persistence (with or without Linux Unified Key Setup encryption).
We will show you how to create the Live USB (no persistence, no history maintained).
Additional options such as live USB with persistence, live USB with encrypted persistence, and custom rolled Kali Linux ISO (which can be incorporated into the bootable USB options) can be found on the Kali Linux documentation wiki at http://docs.kali.org under the section called 02. Kali Linux Live.