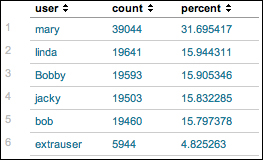
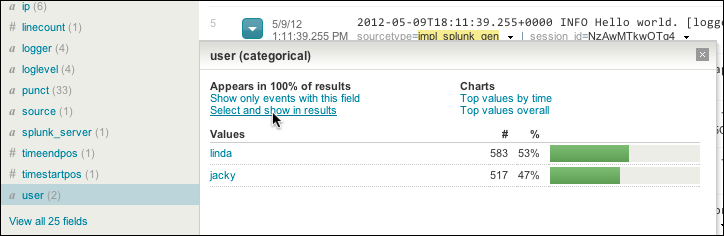
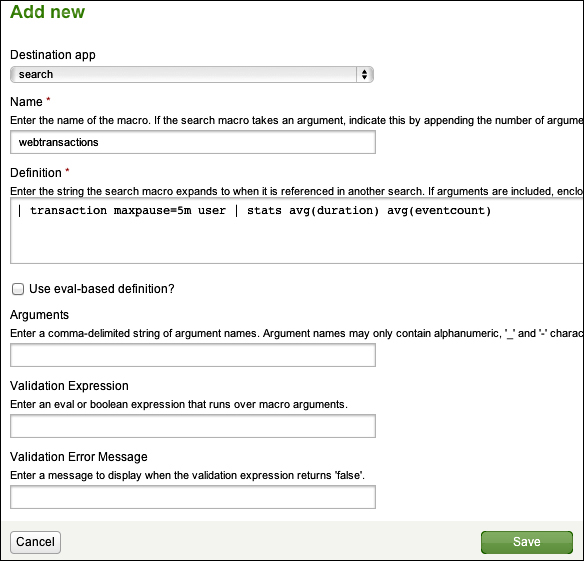
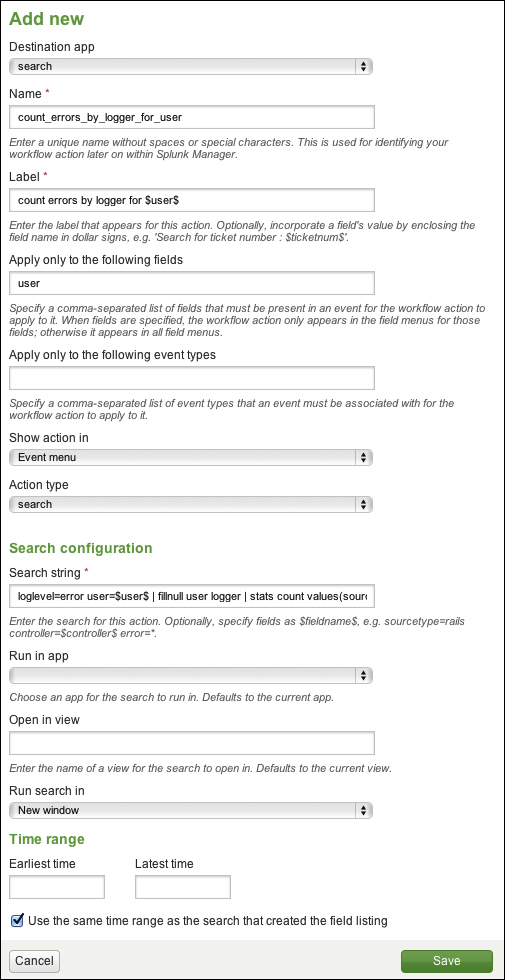
In this chapter, we will look at some of the features that Splunk provides to go beyond its already powerful search language. We will cover the following with the help of examples:
Tags and event types that help you categorize events, both for search and reporting
Lookups that allow you to add external fields to events as though they were part of the original data
Macros that let you reuse snippets of search in powerful ways
Workflow actions that let you build searches and links based on field values in an event
External commands that allow you to use Python code to work with search results
In this chapter, we will investigate a few of the many commands included in Splunk. We will write our own commands in Chapter 12, Extending Splunk.