QRadar Rules and Offenses
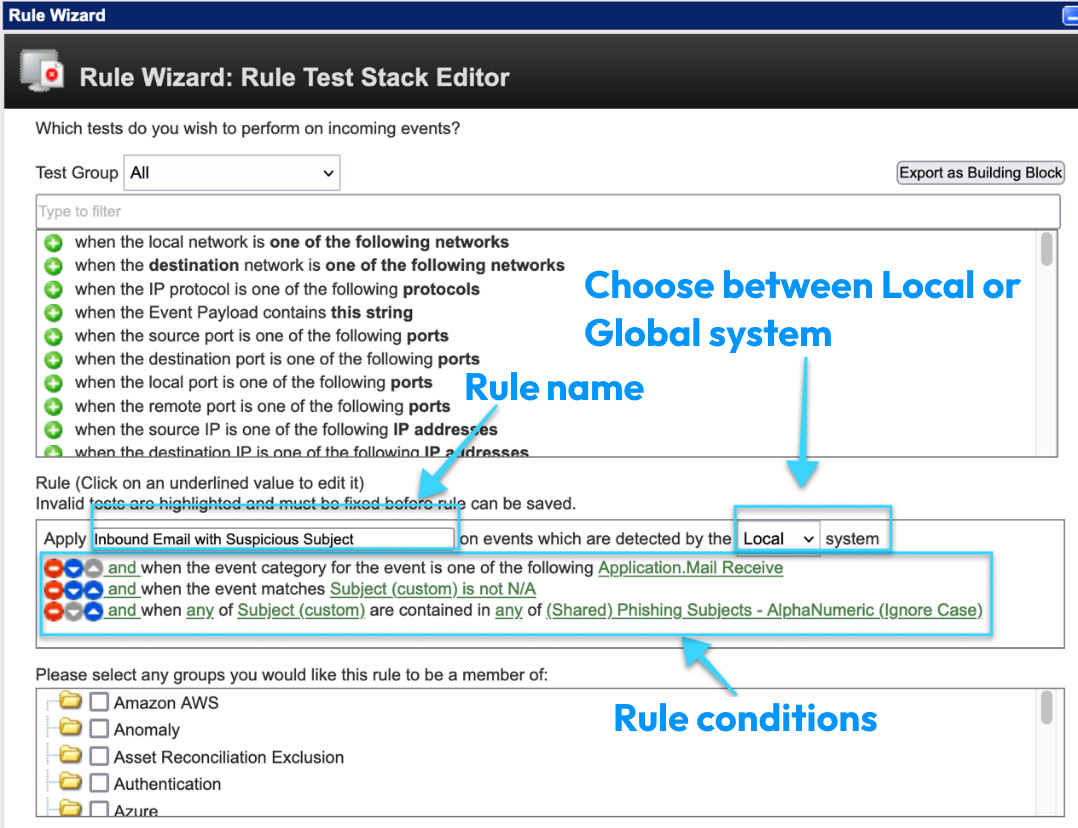
The greatest challenge for any security team across organizations is to receive informed alerts and then perform incident management. Now, what do we mean by informed alerts? In QRadar, we have discussed how data is collected (Chapter 4). What do we do with this data? We correlate this data against the rules that are defined in QRadar.
Rules are security conditions against which every event is matched. If the event matches the rule, the event is tagged with the rule name. If the rule conditions are matched, then an alert is generated. In QRadar, we call security alerts offenses. For every offense triggered, we correlate events and flows to break down and explain the offense. So, when it comes to offense analysis, the Security Operations Center (SOC) analyst wants to get relevant information about the offense or attack. Once the analyst has the information, the analyst can look up whether it has happened before. If it has happened before, there will be a...