Chapter 1: Structured Query Language for SQL Injection
Today's world relies on the concept of cyberspace every day: the internet allows people all around the globe to connect to computers in any part of the world. This enables instant fruition of many services that rely on a plethora of technologies, protocols, and mechanisms that constitute the basis for whatever is available on the World Wide Web. Unfortunately, the theme of security is relevant for this intricate web of connections and services in the same way it is for the real world.
Malicious agents perform attacks against computers worldwide every day, mostly just for personal gain or advantage. By exploiting online applications and services, in fact, it may be possible to gain control of computers or entire networks, thereby taking advantage of specific of the intrinsic vulnerabilities of some technologies, protocols, frameworks, or just applications. One of the most common – and notorious – ways to do...
Technical requirements
For this chapter and the next, the topics we will cover will mostly be theoretical. However, we suggest that you read the SQL technical documentation. Here, we have provided, for reference, the MySQL, Oracle, and Microsoft SQL Server documentation:
- https://dev.mysql.com/doc/refman/8.0/en/
- https://docs.oracle.com/en/database/oracle/oracle-database/index.html
- https://docs.microsoft.com/en-us/sql/sql-server/?view=sql-server-ver15
An overview of SQL – a relational query language
One of the most common ways to keep data memorized in computer systems is by relying on databases. Databases can be seen as large software containers that can hold lots of information in a structured and accessible way, in order to optimize how to store data and access their operations.
Depending on the approach and model used, the way in which this is achieved can vary in terms of implementation. One of the most common ways is to use the relational model, which is based on relational algebra, for which data is a collected as a series of records that describe the relationships that exist among objects. SQL is a query language that is based on such concepts, and it is widely adopted in many database systems. This section will deal with these topics in depth by first explaining database management systems, relational databases, and SQL.
Database management systems and relational databases
The implementation of a database...
The syntax and logic of SQL
As mentioned earlier, SQL is an easy to use and understand language capable of many different types of operations. Like all languages, it is based on interpreting command strings that are inserted with an expected syntax, with specific statements corresponding to one and only possible operation. SQL's main statements can be of many types. Let's take a look at the most important ones:
- SELECT statement:
SELECTis the most common SQL command. Its purpose is to allow the database to be searched, showing the specified attributes from the records that satisfy (optionally) a specific condition; for example:SELECT color, shape FROM objects
This statement shows the
colorandshapeattributes of all the records from theobjectstable. SQL also allows for a wildcard – in this case, the character*– to make general selections:SELECT * FROM objects
- This statement will return all the records from
objectstable, showing all the attributes...
Security implications of SQL
As we've seen, SQL allows us to perform a very large set of instructions, making interacting with the whole database possible at many different levels. We can do this by modifying its structure too. With such a powerful language that can be used to perform any sort of operation on a database, it is natural to start wondering, what could go wrong? With a vast array of possible statements and operations, of course, a malicious attacker could have a wide selection of tools that could be used to damage databases, stored data, and applications using such data, in different ways. One simple instruction, such as DROP DATABASE <database name>, for example, could entirely compromise the functionality of an application that relies on databases to query data or even authentication data (that is, usernames and passwords).
For this reason, SQL code is never, at least directly, conceived to be interacted with inside an application. Instead, it is the application...
Weaknesses in the use of SQL
The main problem that leads to code injection – and obviously SQL injection too – is the way programming (and query) languages themselves inherently work.
Since commands are just strings of characters that are interpreted as code, and user input is made of text, we could, in principle, insert code syntax within user input. If not correctly validated and simply accepted without us applying any control, this injected code could result in the execution of arbitrary commands that have been manually inserted by a malicious user.
This is because a naïve string reader does not make any distinction between text and code as it is essentially binary data coded as text – the same is done from the standpoint of a computer program or an application. Usually, in order to inject specific instructions or code objects, specific characters are used to trick the parser – the software component in charge of reading the text input &...
SQL for SQL injection – a recap
This chapter served as an introduction to, in a general sense, the basic topics behind SQL injection. The following is a summary of the main points to focus on in this first chapter so that you can memorize the main concepts we have mentioned thus far:
- SQL injection is a software weakness of SQL, a specific language and engine for interacting with database structures based on the relational model that treats data in a structured format using tables. It can allow malicious users to execute arbitrary commands, thus interacting with the database of an application in a way that is not originally intended by the application SQL injection can be used by attackers in many ways:
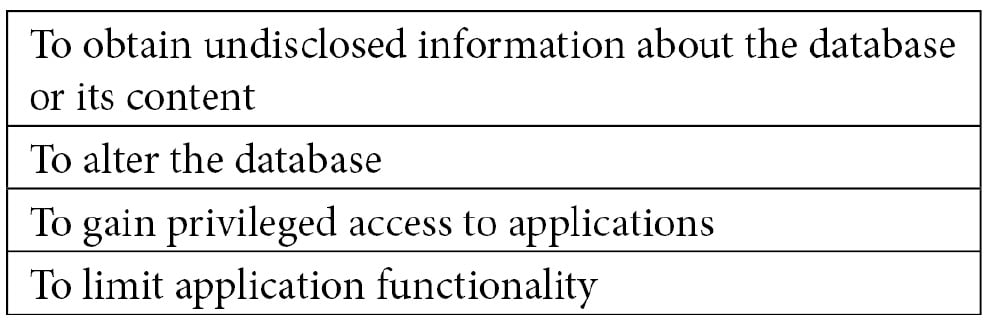
- SQL provides a simple language that can be used to perform operations on relational databases. SQL processes statements with simple structures in most cases. Some SQL statements are as follows:
-SELECT, to extract information from the...
Summary
So, to sum this up, let's take a look at what we covered in this chapter. SQL works using relationships, and it accepts a wide range of commands. We've also seen that, in general, some of these can be abused by malicious attackers. For this reason, we should keep security in mind when designing and developing applications that rely on databases. This chapter gave you a taste of the main security issues and possible solutions.
The next chapter will focus on what a malicious attacker can do by taking advantage of SQL capabilities. We will provide examples of this, all while dealing with aspects related to non-relational databases.
This first chapter, despite being more abstract, is essential for focusing on the main concepts behind SQL injection. Of course, this just an introduction to what we are going to cover throughout this book, but with more concrete examples. Be sure to keep these topics in mind when dealing with the practical aspects of SQL injection.
...Questions
- What is a database?
- What is a relational database?
- What is SQL? What is it used for?
- Can you name some examples of SQL implementations in terms of database systems?
- What does
SELECTmean in SQL? Why is it so important? - Can you describe SQL injection in your own words?




















 Download code from GitHub
Download code from GitHub






