Chapter 1: Building Your AWS Environment
Amazon Web Services (AWS) is a growing cloud technology provider that many companies use to help house their data. Originating from Seattle, Washington in late 2006, AWS is steadily becoming the most prominent service provider. Due to its usability and its user-friendly interfaces, AWS is used by over 800,000 companies and makes up 65% or more of the cloud infrastructure space. Some of its better-known services, such as S3, Lambda, and EC2 will be frequently talked about through this book and are services that are commonly used in the real world.
This chapter is going to go over the basics of AWS and will walk through setting up an AWS account. It's important that we learn the basics of getting our AWS account configured and ready so that there isn't any additional housekeeping needed after setting up an account. After setting up an account, we'll walk through and set up a few EC2 instances with various flavors of operating systems, and look at vulnerable services within those operating systems. It's encouraged that, after completing the chapter, you look at building out more EC2 instances with other operating systems for your environment.
In this chapter, we'll explore AWS through the following topics:
- Exploring Amazon Web Services
- Understanding the testing environment
- Configuring the environment
- Exploring vulnerable services
- Attacking vulnerabilities
- The AWS Command Line Interface
Technical requirements
To follow along with the instructions in this chapter, you will need the following:
- A browser of your choice (Chrome, Firefox, Edge)
- PuTTY: https://www.chiark.greenend.org.uk/~sgtatham/putty/ (installation steps are covered in the Connecting with PuTTY section).
Check out the following video to see the Code in Action: https://bit.ly/3kPrVkh
Exploring Amazon Web Services (AWS)
AWS is a cloud service provided by Seattle tech company, Amazon. AWS's comprehensive and easy-to-use setup makes it very attractive to small start-ups and large corporations. It works by allowing companies and businesses to set up their infrastructure off-premises and within the physical resources of Amazon. This type of service, called Infrastructure as a Service, delivers cloud computing as a whole service. You will see more of how easy it is to automate and build in AWS as we set up our lab throughout this book. However, you'll also notice some issues that may commonly be overlooked, such as security.
AWS doesn't take full responsibility for companies' data and security. In fact, Amazon has put out a shared responsibility model that ensures that both parties understand their rights and responsibilities in terms of customers' data. After all, Amazon is a company that is known as customer-obsessed.
AWS security and penetration testing
As you read through this book, you'll be exposed to some different concepts that may not have been discussed before. The reason for this is due to AWS pentesting being a relatively new subject that is gaining popularity in the security space of information technology. The good thing about this is it allows subject matter experts to lend a hand in helping to create a pentesting culture around AWS and provides newer ideas for how penetration testing is executed in both AWS and system security.
Next, you're going to dive into AWS and create an account of your very own. After that, we'll get started by creating our own cloud pentest playground where we will set up a vulnerable host that can be tested later on.
Understanding our testing environment
It's essential to understand all the systems we are going to be deploying and their use in this book. Building a lab benefits security research because it allows you to perform the same tactics and techniques that real hackers would execute, without having to worry about breaking any laws. For our lab, we will be setting up various hosts that mimic real-life systems that you would see incorporated into businesses. The only difference is we will be using some much older versions of software and operating systems. The purpose of using older systems is because they typically are much more vulnerable than their up-to-date, newer versions, making learning pentesting much easier – and fun!
We want to ensure that we learn a little bit of everything, so we will be using both Windows- and Unix-based operating systems. These systems are built drastically differently but are systems that you will face in real-life pentesting situations.
Additionally, we will be using an operating system called "Kali Linux" as our hacking operating system. Kali Linux is a very popular hacking operating system used in the pentesting community, primarily due to its coming preinstalled with various hacking tool suites and being maintained by offensive security.
Configuring your environment
Configuring your environment is the most important task of this book. Without it, you won't have anything to test your skills! Building out an environment will teach you how to configure instances, add resources to them, and connect to them.
Setting up an account
To begin the process of creating your own AWS account, follow these steps:
- Please open a browser of your choice and go to the AWS home page located at https://aws.amazon.com/.
You will be greeted with a landing page and will see a button titled Create a Free Account. Simply click on Create a Free Account to get started with creating your profile:

Figure 1.1 – AWS account creation
- After clicking the button, you'll see how to create an AWS account. Fill out the information accordingly. If you use a student email address, you can get access to extra goodies:

Figure 1.2 – Account creation form
- Once the form's filled out, click Continue and you'll receive an email prompting you with a greeting and welcoming you to AWS:
Figure 1.3 – Email from AWS after account creation
Congratulations, you now have your very own account to access for the rest of this book. Feel free to get a feel for all the resources available in AWS before moving on. AWS is full of resources and information that you can use at your disposal. Once you're ready, move onto the next section as you learn how to create your very own EC2 instances.
Important note
When setting up an account, use a .edu address if possible. There are additional benefits you can use with an AWS account. A link will be available at the end of this chapter for more information about student benefits.
The next section will discuss how to create your very own EC2 instances in your new AWS account.
Setting up EC2 instances
EC2 (Elastic Compute Cloud) instances essentially replace the need for hardware by providing scalable computing within the Amazon cloud. Think of an EC2 instance as a computer with no operating system. This is beneficial because it allows organizations to scale their systems, with little to no overhead! However, while it is a benefit to have such a simple solution, the downside can come in the common form of poor management. It's extremely easy to deploy an EC2 instance only for it to go unnoticed by administrators. But that computer is someone else's computer that you're renting. Keep in mind that a computer is just a computer, so you will need to place an operating system on it.
Before we begin discussing the instances we are creating, let's make a quick mention of why we are setting these instances up. Part of being a pentester is understanding how things are set up. Often, pentesters come from a development and system administrator background and have a fundamental understanding of how systems work. We are setting up various operating systems and taking a first-hand look at how common issues are implemented in EC2 instances and the operating systems. Let's look at what we will be creating throughout this chapter.
We will create three EC2 instances with various images. Doing so will give us the tools and understanding of how accessing each system is different from the other. The first operating system that we are going to install will be CentOS 7.
CentOS is a very popular Unix-based operating system that will allow us to explore how Linux filesystems work in more depth. It is essential that we are exposed to various systems when learning penetration testing because, in the field, you can have a variety of targets that will be in the scope of a penetration test.
Setting up an EC2 instance with CentOS
If you haven't already, go ahead and log into your AWS account. Once you log into your account, you will be in the AWS Management Console. This is where we will start creating EC2 instances for this chapter. The following steps highlight how to deploy an EC2 instance:
- From the main console, you will see EC2 under the word Compute. Click on it to begin the process of creating an EC2 instance:

Figure 1.4 – AWS Management Console
- After clicking on it, you will see a button labeled Launch instance in the bottom left-hand corner. There is also the Instance option in the left drop-down pane. Click on Launch instance to start building out your first EC2 instance:
Figure 1.5 – EC2 launch
After clicking Launch instance, you'll need to configure a host operating system within your EC2 instance. For this exercise, we'll choose the minimal CENTOS 7 install for our host operating system. This operating system is going to be what "lives" in the EC2 instance.
Now that we have set up our AWS account, we will break down, step by step, the process needed to build an EC2 instance. As mentioned, the EC2 instance is what our operating system will be hosted on. I recommend you get comfortable with this process as you will be building instances quite a bit throughout this book. To begin setting up some instances, follow the provided steps to get started. The steps are in sequence with building an EC2 instance. If you miss one step, ensure you go back and cover the step before moving on:
- Choose an Amazon Machine Image: Go to Amazon Marketplace and search for an image to install on your EC2 instance. As stated, we will use CentOS 7 for this example:

Figure 1.6 – EC2 operating system
- Choose an instance type: Ensure that you use the free tier to avoid charges. If you do forget, Amazon will bill you monthly for any usage that goes over your plan. However, feel free to use the paid tiers if you so choose. For this exercise, we are going to be using the free tier since it will serve as enough.
- After that, you'll want to create a new virtual private cloud (VPC) network that your EC2 instance can live in. The VPC acts as a network that allows secure communications between other instances within the VPC. It also allows connections outside of the VPC via a VPN:

Figure 1.7– Creating a VPC
- After that, you'll need to create a subnet that your hosts can connect to. Make sure you remember the VPC and the subnet for later when setting up other instances:

Figure 1.8 – Creating a VPC part 2
- Next, you'll be prompted about storage for the OS. The storage that is allocated will suffice for the exercise:

Figure 1.9 – Storage setup
- Next, we will be configuring routes for the instance. Routes are going to allow and disallow traffic to and from the host on certain ports of your instances. For this exercise, please set up the following routes as illustrated:
SSH : TCP : 22 : ANYWHERE //Allowing any connections over port 22 Custom UDP : UDP : 0 - 65535 : ANYWHERE // Allowing any conections of all UDP Ports Custom TCP : TCP : 0 - 65535 : ANYWHERE // Allowing any conntections over any TCP ports
The following screenshot highlights the changes we are making and inputting:

Figure 1.10 – Creating a security group
- You're going to need to create a key pair that you can use to connect to your instance. Make sure that you save the key pair in a place where you won't lose it. You're going to need to use that key to access the instance. The following screenshot illustrates naming the key
AWS Pentest. Feel free to call yours whatever you like:
Figure 1.11 – Creating a key pair
- Once you name the key pair, download it and save it in a safe place. It's important to make sure you save the key and even make a copy of it in case the original key becomes lost. You won't be able to retrieve the key from your instance.

Figure 1.12 – Dashboard for running EC2 instances
- Once finished, click on Running instances to check your instance. We will discuss how to connect to it via SSH later in the book.
You have now set up your first instance! Don't feel pressured if you're having issues connecting to it, such as a permissions error; ensure that you have the right permissions set to your instance's key. Right-click on the instance and click Connect to be advised on how to set the permissions. We will discuss connecting to instances in just a bit. For now, discover what's available in the AWS console. There is quite a bit that we will talk about, but it doesn't hurt to take a look and get to know it. When you're ready, move on to the next section.
Setting up a Windows host
The following section is going to discuss how to set up a Windows host in AWS. Setting up the host will be very similar to setting up the CentOS 7 server, with a few differences. It's important that we understand how Windows systems work and how we can set them up in AWS. As you move through your penetration testing journey, you'll come to find out that many businesses use Windows in their AWS environments and their onsite devices.
Let's set up the host:
- Let's go back to the AWS Management Console and select Launch instance to bring up another instance, just as we did before.
- Go to AWS Marketplace and select Windows Server 2008 R2 Base.
Important note
We want to use an older version, rather than a new, updated one because security issues are much easier to exploit in the older version. Since the purpose of this book is learning, we want to be able to easily exploit known issues that are typically found in older versions, rather than trying to exploit hardened newer operating systems. Make sure that you select the same VPC settings as before. Doing so ensures that all the VMs, such as your CentOS 7 and Windows host, are on the same network. This will help us later when practicing pentesting because we will be working on the same virtual network, making it easier for instances to communicate with each other.
Here's what it looks like in the marketplace:

Figure 1.13 – Windows 2008 EC2
- Just as before, we need to ensure we have the correct ports open. Take note that RDP is open on the host. The next screenshot highlights that port
3389is open. Port3389is the port that is associated with RDP. Having this set correctly ensures that you can connect to the Windows host later on:
Figure 1.14 – Windows 2008 EC2 open ports
- Now that we have the host all ready to go, we will need to connect to it. Since this is a Windows host, we won't be able to SSH into it like we traditionally do with other hosts. This is because the host uses the Remote Desktop Protocol on port
3389, instead of using SSH on port22. Instead of getting a key, we will need to get the password stored on the Windows host. - To get the password, simply right-click on your Windows instance and select Get Windows Password. If you just set up your Windows host, it could take up to 4 minutes for you to be able to decrypt the password:

Figure 1.15 – Windows 2008 EC2 password retrieval
- Decrypt the password by entering the encrypted password as illustrated. Once you have put the password in the field, click on Decrypt Password:

Figure 1.16 – Decrypting Windows passwords
- Once complete, you'll be prompted with a User name and Password to access your host. Just as before, ensure you save these credentials somewhere safe so that you do not lose them. However, you can recover them as long as you have the encrypted password. Storing the encrypted password can be as easy as storing it in a password vault, or storing it in a cloud storage space, such as an S3 bucket. Make sure that only you have access to where it is stored. For the best results, implement user-based access control to the filesystems:
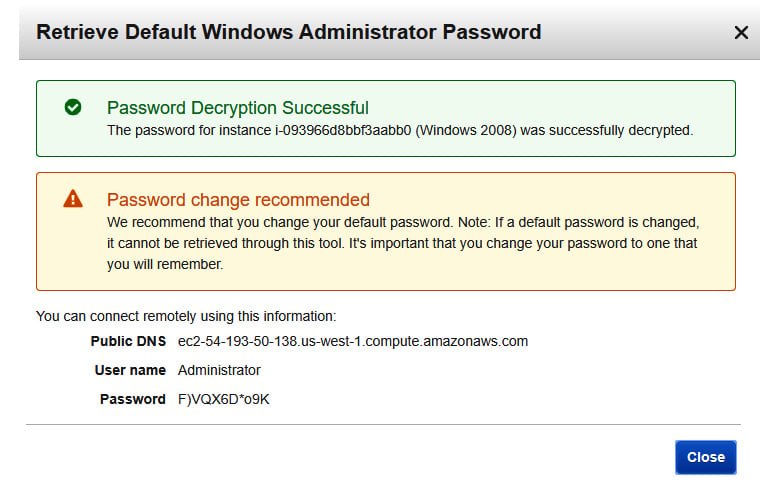
Figure 1.17 – User name and Password
To test the connection, open the Remote Desktop client on your host machine and use the public DNS of the EC2 instance. If all goes well, then you should be able to log in to the desktop!
Attacker setup – setting up a Kali instance
For this section, we will set up a Kali Linux image that can act as our attack host. Kali Linux is a popular operating system used by security professionals to test their systems and applications. This is largely due to the operating system coming preinstalled with tools that can assist in enumeration and exploitation! Kali Linux will be used as one of our main hosts as we go through this book and will be a tool that you will use in your pentesting endeavors!
Since we already know how to set up an EC2 instance, we are going to only focus on how to connect our Kali host using a tool called PuTTY. PuTTY is a tool that allows administrators to remotely access their systems, as we will do later in this chapter. As you set up your Kali machine, ensure that you use the same VPC and subnet settings you did for your other machines:
- To start, go to AWS Marketplace and retrieve an instance of Kali Linux. Then proceed to create the EC2 instance as you did with the previous exercises:

Figure 1.18 – Kali Linux EC2 instance
The same as before, make sure you create a new key pair with a new name.
Important note
It's best advised to create new keys for every instance and not share keys between instances. In a real-world situation, if a key were to become compromised and all hosts used the same key, then it would be assumed that all hosts were to become compromised. It would be a "shared secret" between all hosts.
Here's what the window looks like:

Figure 1.19 – Kali secret key
- Now that we have the key pair, we need to connect to the Kali machine. Right-click on the instance from your console and follow the connection instructions to your instance:
$ chmod 400 "Kali - AWS - Pentest.pem" $ ssh -i "Kali - AWS - Pentest.pem" ec2-user@<AWS instance>
The following screenshot shows the steps and their meaning to help understand what these commands are doing:

Figure 1.20 – Kali information
As you can see in the screenshot, the prompt highlights a few housekeeping steps before we can access our EC2 instance.
- Open the SSH client. In our case, we will be using PuTTY for our connections and will look at how to connect in the next section.
- Locate the .
pemfile that we just saved. The.pemfile acts as the secret key and allows you to authenticate the EC2 instance. - We need to change the permissions of the key using the
chmodcommand. - The public DNS name that is assigned to our instance is the resource name used to connect to the instance.
- Lastly, the command shows us how we can use the SSH command, found pre-installed on our Linux machines, to connect to our cloud resource using the secret key and the username
root.
Next, we will look at how to connect to the instance with PuTTY.
Connecting with PuTTY
PuTTY is a tool that allows users to connect to a host from various ports. Unlike a terminal or command line, PuTTY gives an interface that allows users to interact with their host with the click of a mouse instead of having to connect with the terminal. It's crucial that we understand various ways to connect to our instances, and PuTTY is a common resource to connect to EC2 instances in a real environment.
We can use PuTTY or SSH to connect to any of the instances we set up in our own lab. The purpose of this section will be to walk you through the steps of creating an SSH key from a private key assigned to an EC2 instance:
- To begin, ensure that PuTTY is installed on your computer. You can download the right client for you here (https://www.chiark.greenend.org.uk/~sgtatham/putty/). Once installed, move on to converting the private key.
- Start a program called PuTTY Generator. PuTTY Gen is a key generator used for converting keys into various formats. After starting the program, click Load and put the private key to your instance in the generator. The private key you assign to your instance is the
.pemfile. We created.pemfiles with our CentOS 7 instance before as well. Once you load the key into PuTTY Gen, assign a password phrase and click Generate. This will create a different key with the extension.ppk:
Figure 1.21 – PuTTY key generator
- Now that you have created a
.ppkfile, it's time to start up PuTTY and test your connection. Go to Connection > SSH > Auth and load your new key that you created in the previous step:
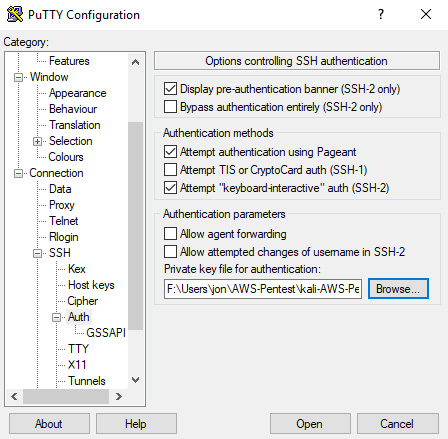
Figure 1.22 – PuTTY key configuration
Once the key is ready to go, it's time to input the specific data needed to start up your connection to your instance. The following steps will guide you through this process:
- Go back to the Session tab in PuTTY. Once in the session tab, input the Host Name of the instance you are connecting to. The hostname is the public DNS record that you can find in the AWS console. You can also click Connect on your instance to be provided the public DNS name.
- Once the hostname is configured, ensure that the port is set to
22for SSH:
Figure 1.23 – PuTTY connection
- Now we're ready to connect to our instance. Click Open and a PuTTY terminal will greet you asking for a passphrase. The passphrase is the password you set when you were creating the
.ppkfile:
Figure 1.24 – PuTTY terminal
- Now you're being logged in as the user
ec2-user. This user doesn't have very high privileges, so feel free to alter them by switching into the root account using the following command:$ sudo su
These privileges allow the user to alter, read, and execute any files on the Linux-based operating system. These high-privilege users can be found in the file path /etc/sudoers. Congratulations, you now have successfully connected to your instance using PuTTY.
Great job finishing this section! You should now be comfortable with setting up EC2 instances within AWS and also under the basics of configuring various operating systems. As stated, it is extremely important that you understand the differences because as you go on pentesting, you will be exposed to numerous operating systems, such as Windows- and Unix-based systems.
Next, we are going to move on to looking at vulnerable services and how we use our knowledge to set up a vulnerable service in our pentesting environment.
Exploring vulnerable services
Vulnerable services can be the Achilles heel of a system if left unpatched. What this means is vulnerabilities, if left unpatched, leave a severe weakness in companies' systems that can allow malicious hackers to gain access. A vulnerability is classed as an issue in a system that, if not fixed, could cause large issues if it were to become an attack vector. Vulnerabilities come in many variants and can come in the form of outdated operating systems, open ports, unauthorized access, and many more. To fix known vulnerabilities and protect systems from attacks, patches and updates have to be installed accordingly. Doing so helps remediate most of the major problems you will see.
Discovering vulnerable services
Now that we know what a vulnerability is, let's mention the typical way pentesting discovers vulnerabilities:
- Ensure that you have a list of targets. Targets are categorized as hosts – we can think of EC2 instances as hosts.
- Once you have a list of hosts, you'll need to scan them and enumerate information from them. Scanning can be used with various tools, which we will use more of in Chapter 9, Real-Life Pentesting with Metasploit and More!.
- You then create the risk associated with vulnerabilities you found while scanning and enumerating. Risk is typically labeled as low, medium, high, or critical – with critical having the most impact.
- You may also find "low-hanging fruit" while scanning. Low-hanging fruit are easy-to-exploit vulnerabilities that allow you to exploit a target quickly.
- Discovered vulnerabilities should be reported immediately so that they can be properly patched. Typically, another team is assigned to fix these issues and apply patches to the systems.
This is the basis of how vulnerabilities are discovered in a pentesting environment. Now let's look at how vulnerable services are created from an administrator's point of view.
Creating vulnerable services
For this short example, we are going to install vsftpd and enable anonymous login on our CentOS 7 machine. Anonymous login is a default feature in quite a few FTP clients and allows anyone to connect to the FTP using the following credentials:
- Username:
Anonymous - Password:
Anonymous
As you can already assume, allowing anyone such easy access to your server creates a huge security risk. We will learn how to set up the server as vulnerable, and then later will learn some security controls that we can put in place to lock down the FTP server:
sshinto the CentOS 7 server that we set up. You will need to log in as the user ec2-user, and not root.- Once logged into the server, run the following commands to update your server and install the
vsftpservice:$ sudo yum update
- Follow this by running the following:
$ sudo yum install vsftpd
If you're having issues due to fewer rights and privileges, run the command
sudo suto switch over to the root user account. This will allow you to run all commands as the root user. - Verify the service is running by typing
sudo service vsftpd status. Now thatvsftpdis installed, we need to ensure that anonymous login is enabled. Run the following command to access thevsftpdconfiguration file:anonymous_enabled=YES
It will look like the following screenshot:

Figure 1.25 – Installing Metasploit
Now your server is set with anonymous login. Later on in the book, in Chapter 3, Exploring Pentesting and AWS, we will discuss how to scan and connect to the service locally and remotely from other instances within our environment.
We now have some understanding of what vulnerabilities are and how to reproduce them ourselves. It's important to understand the full scope of the technical attributes of what we will be doing throughout this book. In regard to vulnerabilities, please note that discovering vulnerabilities is not the same as attacking them. When discovering vulnerabilities, you will be assigned to discover, assess, and evaluate any vulnerabilities found. Pentesting executes this type of testing one step further by attacking and exploiting those vulnerabilities through manual and automated exploitation.
Let's move on to discussing what attacking vulnerabilities entails.
Attacking vulnerabilities
Attacking vulnerabilities is one of the more interesting aspects of cybersecurity. It's one thing to discover and patch an issue that you may have discovered, but actually getting to attack it takes your skills to another level! Attacking vulnerabilities is what sets penetration testing apart from other security careers. While most security positions only discover and remediate, pentesting attacks and exploits discovered issues. Doing so sheds light on how real a system's security posture may or may not be. One of the more popular tools you will hear about is called Metasploit.
Exploring Metasploit
A popular tool in the pentesting community is a framework known as Metasploit Framework. Also known as Metasploit, the automated software comes preinstalled on Kali Linux with exploits and payloads that can be configured and launched at vulnerable hosts. It also comes with exploits applicable to all flavors of operating systems, and payloads of various types. The exploits are known as modules and created in Ruby.
One of the more common exploits is the exploit/multi/handler. The multi handler works as a listener that looks for incoming connections on ports from specific services. For example, a web-based exploit may use a more common service such as HTTPS, which runs on port 443. The listener can be set up to listen on port 443 and establish a connection once the web exploit is executed. We will look at more ways to use Metasploit in Chapter 9, Real-Life Pentesting with Metasploit and More!.
We need to learn to walk before we can run, so now let's take a look at getting Metasploit set up on our Kali Linux host. The next portion is going to give you an exercise to get Metasploit up and running.
For this exercise, we are simply going to connect to the Kali Linux host and update Metasploit. New exploits are constantly getting uploaded to Metasploit, so it is important that you update often:
- Here's how we are going to update Metasploit. Connect to your Kali instance you set up earlier in the chapter by using the PuTTY methods from before. Review the section to connect if you need to. Once connected, you'll want to switch over to the root user. The root user is going to give you privileges to read, write, and execute anything on the machine. To switch to root, type the command
sudo su. - Now that you are the root user, let's update Metasploit to the current version. We want to ensure that Metasploit is updated with the most recent exploits and modules for testing. To update the tool, type the following command:
$ apt install metasploit-framework
The screenshot illustrates the command being executed in our Kali Linux terminal:

Figure 1.26 – Installing Metasploit
- Once connected, you'll be able to start Metasploit with a fresh new database full of exploits. In previous years, you would have had to start up a database in the background before launching Metasploit. However, now, the following command will start Metasploit with a database running in the background:
$ msfdb run
Feel free to get comfortable with Metasploit. There are copious amounts of resources to learn all things about the popular pentesting tool. We will be using the tool quite a bit throughout this book, so don't worry if you don't want to rummage around the internet and books for more information.
In this section, we learned quite a bit about what exactly a vulnerable service is and how it can be set up. We also included a brief introduction to what it means to attack these vulnerabilities and learned a little bit about Metasploit – a very popular tool in the pentesting community.
Next, we are going to learn about the AWS Command Line Interface and how we can install it and use it.
The AWS Command Line Interface (CLI)
The AWS CLI is a great command-line tool that allows you to interface with AWS technology such as S3 buckets, interacting with EC2 instances and others. We will start to see actual use cases of implementing the AWS CLI in more depth in Chapter 4, Exploiting S3 Buckets. The AWS CLI is a great way to learn and get comfortable with using a terminal-like interface because it allows you to interact with everything in your AWS environment. For pentesting, it's always good to be comfortable with using a command line and/or a terminal because you never know when a GUI just won't do the trick. Imagine being in the middle of a penetration test and your tool interface freezes, or the frontend of an application throws an error and ceases to work. This is where understanding the command line proves to be beneficial.
Installing the AWS CLI
Now we will need to move forward and install the AWS CLI on our Kali Linux machine. This will be the command line we will use throughout this book to interact with our AWS environment:
- To begin, let's check and see if the AWS CLI is already installed on our machines:
$ aws --version
- If you have an old version, you should see what version you have. If you haven't used it in a while, it's best to go ahead and reinstall it:
$ apt-get remove awscli -y $ apt-get install awscli -y
- Double-check to ensure that your command-line interface successfully installed by running the
--versionswitch again.
Now your host is set up to interact with resources in AWS and cover the material in this book. Feel free to play around and get comfortable with the command-line interface. It's something that you'll need to get used to as you go through this book and interact with AWS in the real world.
Exploring basic AWS CLI commands
Now we will look at some basic AWS CLI commands, now that there is a general understanding of what the AWS CLI is and how it works. The following shows a few commands that you'll see throughout this book. These commands are meant to interact with various services, such as S3, EC2, and Lambda.
Once you've configured your AWS CLI, use the following command to get a list of commands:
$ aws help
The following command is useful to describe the attributes of an EC2 server:
$ aws ec2 describe instance
The next command will list out the buckets in an S3 environment:
$ aws s3 ls s3://
The last command we will mention is used to list out functions with Lambda:
$ aws lambda list-functions –-region <<region>>
As you can see, there are quite a few services that you can interact with via the AWS CLI. You'll become more and more familiar with interacting with these services as we continue to go through more exercises in this book. Now that we have discussed the last topic in this chapter, let's wrap up and recap!
Summary
In this chapter, we learned how to create an AWS account that will allow us to set up an environment for us to create a host and pentest it later throughout the book. It is essential that we understand how to make labs within AWS, mainly due to it being the sole way we will be performing testing in this book, and how you would in a real-life situation. We learned what an EC2 instance is and how to set up an instance with various operating systems, helping us understand the importance of the various operating systems that we would see in a real-world pentesting situation. We learned about setting up vulnerable services within our host and what vulnerabilities entail regarding pentesting and AWS security. Lastly, we learned how to quickly set up the AWS CLI for us to interact with our AWS resources.
In the next chapter, we will start looking more at Kali Linux, some of its history, and how we will be using it throughout this book, and how it pertains to pentesting.
Further reading
- You can find the files for the AWS CLI here: https://github.com/aws/aws-cli
- More information about AWS Educate: https://aws.amazon.com/about-aws/whats-new/2015/05/aws-educate-students-and-educators-can-access-aws-technology-cloud-courses-training-and-collaboration-tools/
- The PuTTY user guide can be found here: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/putty.html
- More information on S3: https://docs.aws.amazon.com/cli/latest/reference/s3/
- More information on Metasploit: https://www.metasploit.com/




















 Download code from GitHub
Download code from GitHub






