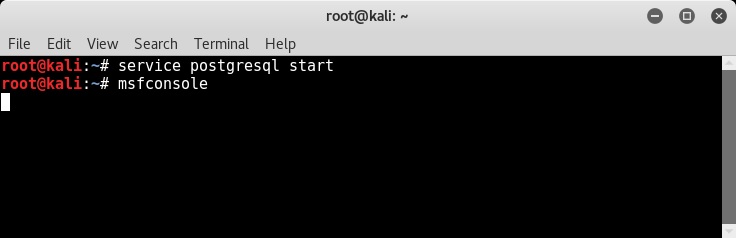
Before we actually start the Armitage console, as a prerequisite, first we need to start the postgresql service and the Metasploit service, as shown in the following screenshot:
Once the postgresql and Metasploit services are up and running, we can launch the Armitage console by typing armitage ;on the command shell, as shown in the following screenshot:

Upon the initial startup, the armitage console appears as shown in the following screenshot:

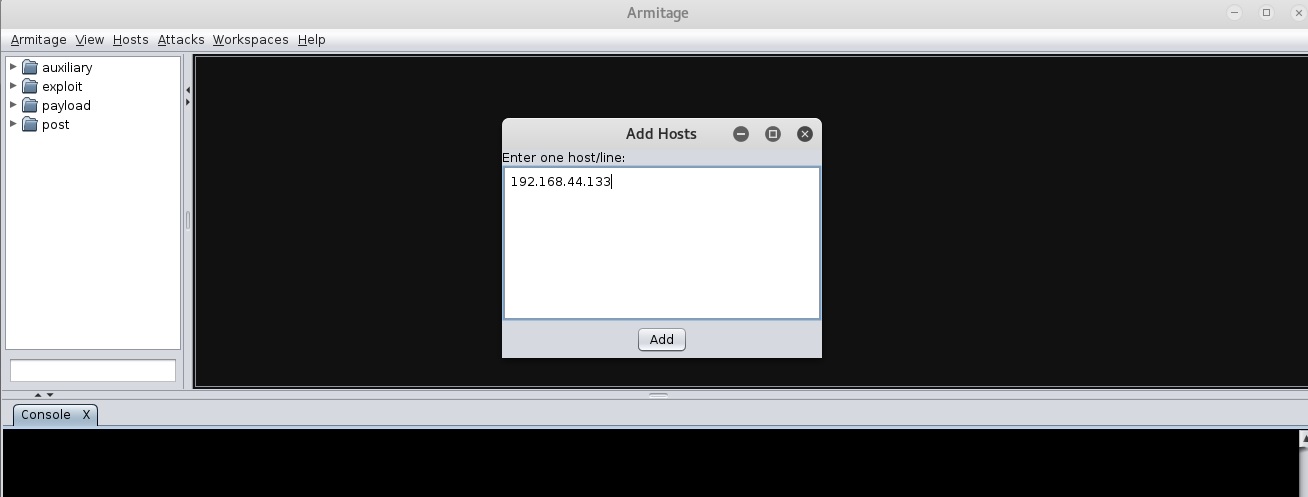
Now that the Armitage console is up and running, let's add hosts we wish to attack. To add new hosts, click on the Hosts ;menu, and then select the Add Hosts ;option. You can either add a single host or multiple hosts per line, as shown in the following screenshot: