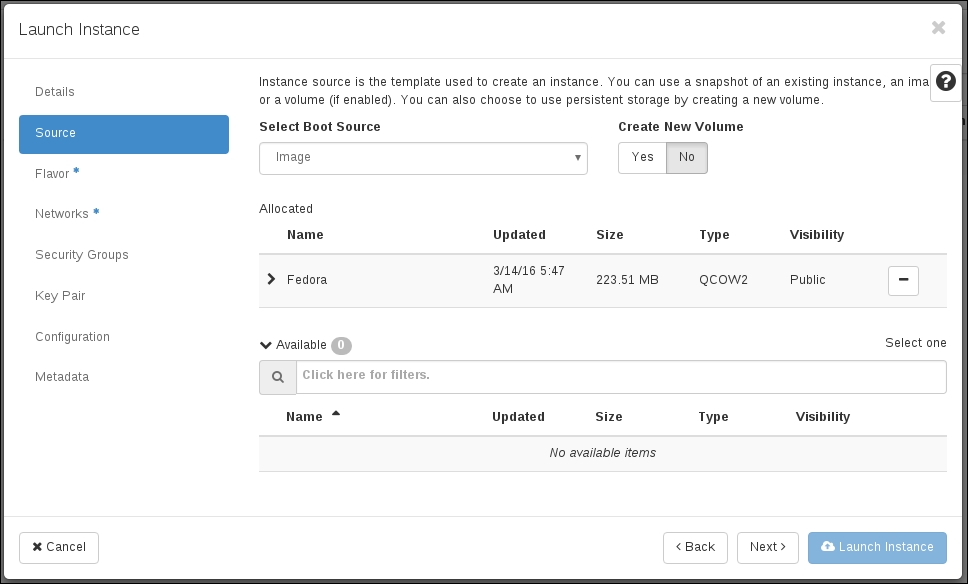
In the past few chapters, we collected resources that laid the foundation to launch an instance. We have created a project – a place for our resources to live in. We added a disk image using Glance that the instance will use as its boot device. We created a network for the instance using Neutron. Now it is time to launch the instance. Nova is the instance management component in OpenStack. In this chapter, we will look at managing the following:
Flavors
Key pairs
Instances
Floating IPs
Security groups