
You're reading from Password Cracking with Kali Linux
Chapter 2
Obtaining Password Hashes for Cracking
Windows Server active Directory has several ways in which it can authenticate users. These authentication protocols include NTLM and Kerberos. Let’s begin by talking about both briefly.

Simplified View of Windows NTLM and Kerberos Security
NTLM (NT LAN Manager) protocol plays a pivotal role in authentication processes within Windows environments, acting as a key mechanism to verify the identity of users and systems. As a legacy protocol, NTLM has been a stalwart component since the early versions of Windows, although its prominence has diminished with the advent of more advanced authentication protocols, like Kerberos.
Unlike Kerberos, NTLM primarily functions through a challenge-response mechanism. When a user attempts to access a resource, the server generates a random challenge that is sent to the client. The client then encrypts this challenge using the user's credentials and sends the encrypted response back to the server...
Kerberoasting
“Kerberoasting” is a security attack that targets the Kerberos authentication protocol used in Active Directory environments. In simple terms, in an Active Directory environment, Kerberos is one of several protocols that helps users and systems authenticate themselves securely. Kerberos is a Ticket Based system. Basically, Kerberoasting is a method where an attacker captures encrypted service tickets, targeting service accounts in an Active Directory environment, and then attempts to crack the encrypted information offline to reveal the service account's password.
Key Components of Kerberoasting
To understand the Kerberoasting attack, we need to understand how Kerberos itself works. Let’s look at some important components involved with Kerberos as it applies to Kerberoasting:
Ticket-granting Ticket (TGT) - When a user logs into a Windows system, they get a Ticket-granting Ticket (TGT) from the Key Distribution Center (KDC), a part of Active Directory.
Service Tickets - The TGT can be used to request service tickets for specific resources, like servers or services in the network.
Service Accounts - are often targeted because they are accounts associated with services running in the background. They have privileged access, many times they are members of the Domain Admin group. The passwords don’t get changed often if at all. Also, many times their password is the length of the Domain minimum password length. This makes them a prime target for attackers.
Kerberos issues these tickets during the authentication process. The TGT is...
Attacking Kerberos
Performing a Kerberoasting attack involves several steps, and attackers often use a variety of techniques to achieve their goals. To avoid detection, attackers may perform the attack in a stealthy manner, limiting the number of service ticket requests and ensuring that their actions do not trigger security alerts.
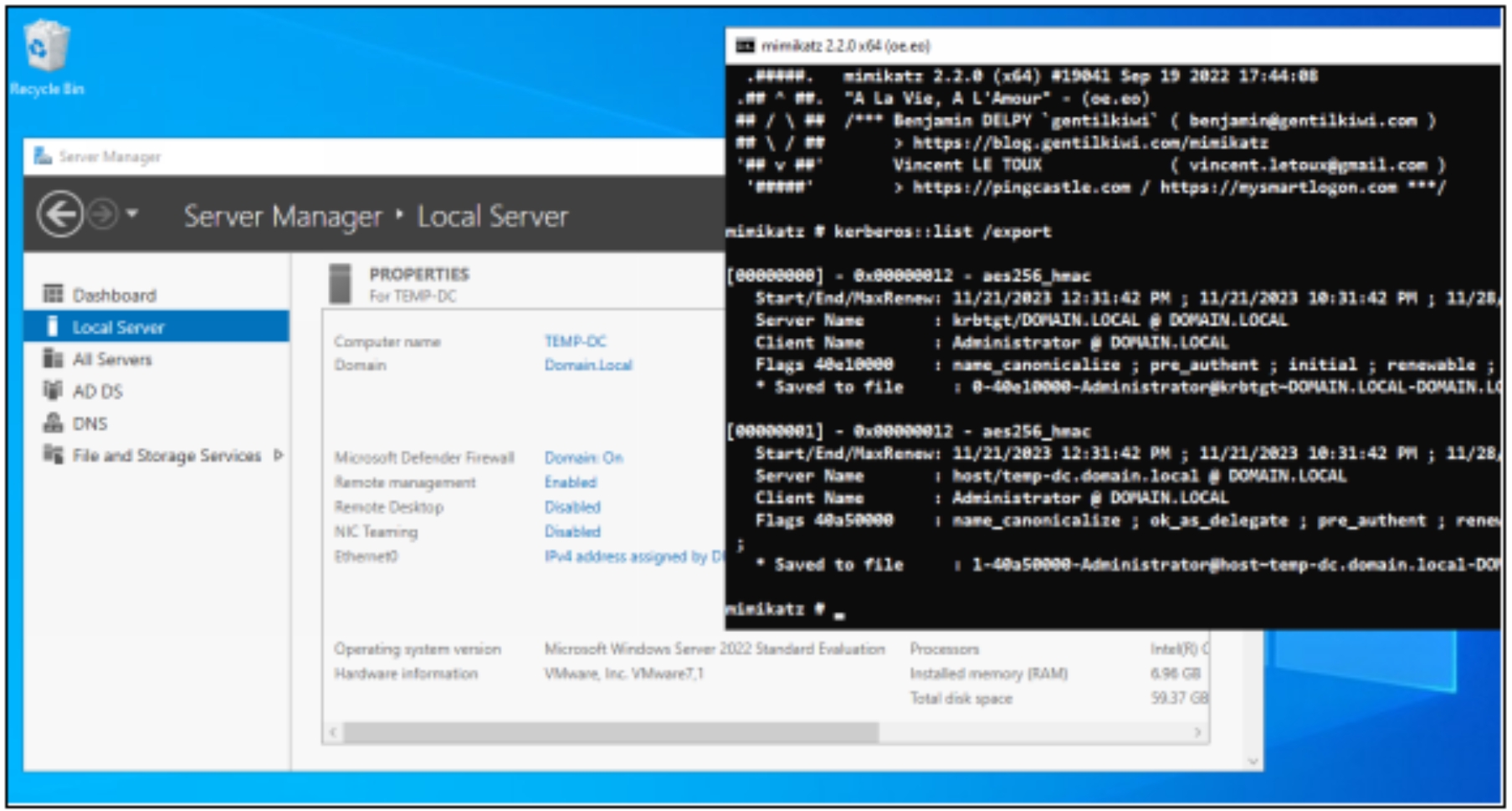
Here are some common techniques associated with Kerberoasting attacks:
- Identifying Service Accounts
The attacker identifies service accounts in the Active Directory environment. Service accounts are often associated with background services and are attractive targets due to their typically long and complex passwords.
- Enumerating Service Principal Names (SPNs)
Service Principal Names (SPNs) are associated with service accounts. Attackers may use tools like BloodHound or PowerView to enumerate and identify accounts with associated SPNs.
- Requesting Service Tickets
The attacker requests service tickets for the identified service accounts. They typically...
Kerberos Attack Tools
That said, understanding the tools that attackers may use is crucial for defenders to be aware of potential threats and take appropriate measures. Some tools commonly associated with Kerberoasting attacks include:
- PowerShell Scripts
PowerShell is a powerful scripting language built into Windows. There are various PowerShell scripts, such as PowerView and Invoke-Kerberoast, that can be used to identify service accounts, request service tickets, and perform other steps in the Kerberoasting process. A lot of these scripts are included as modules in Command and Control (C2) frameworks. Learn more about C2’s and their attack modules in my “Advanced Security Testing with Kali Linux” book.
- Rubeus
Rubeus is a powerful post-exploitation tool that attackers often use in Kerberoasting attacks. It can be used to request TGTs, request service tickets, and perform ticket-related attacks. It includes features for ticket extraction and offline cracking...
Rubeus
Rubeus is a C# based tool for interacting and attacking Kerberos. The tool was originally based off of Benjamin Delpy’s (the creator of Mimikatz) Kekeo, but has since evolved into its own creation. Rubeus can be used in many, many different ways to attack Kerberos, we will only briefly look at one. I highly suggest the reader check out the tool’s Wiki for extensive documentation and usage information.
You will notice there is no executable download on the Rubeus GitHub page. You will need to compile the tool on your own. Obviously in its present form, it will be detected by most, if not all Anti-Virus systems and blocked right away. An experienced Red Team attacker would need to modify some of the code before compiling to avoid AV detection.
Quick Kerberoasting Walkthrough
- Obtaining Initial Access
Before an attacker can use Rubeus, they...
Kerberoast Toolkit
Kerberoast is a set of tools for attacking Kerberos. The complete process for performing Kerberoasting is covered on the tool website. The steps are replicated here for convenience. You will also need to download Mimikatz and place its executable file (Mimikatz.exe) on the target Windows system. Mimikatz is covered in the following section.
➢ Download the Kerberoast Toolkit on your kali system.
➢ In a Kali Terminal, Enter, “git clone https://github.com/nidem/kerberoast.git”
➢ Then change directory to kerberoast
In PowerShell on the Windows Server Target:
➢ Enter, “setspn -T domain -Q */*”
➢ And then, “Add-Type -AssemblyName System.IdentityModel”
➢ Lastly, “setspn.exe -T DOMAIN.local -Q */* | Select-String...
Mimikatz
Mimikatz has been one of the most popular and standby tools for password attacks for many years. I have used this so many times that I couldn’t even count how many, and I still find new ways to use it! Mimikatz is a powerful post-exploitation tool commonly used by attackers to extract plaintext passwords, NTLM hashes, Kerberos tickets, Terminal Server creds and much more!
Dumping NTLM Hashes with Mimikatz
➢ Download the latest version of Mimikatz from the tool website
➢ Deploy Mimikatz on a Windows target
➢ Run “Mimikatz.exe”
➢ Type, “privilege::debug”
➢ And then “sekurlsa::logonpasswords”

If successful you will now have the NTLM hash of the currently logged on user, and any other user who...
Mimikatz Pass the Hash Attacks
Mimikatz can also perform other attacks like, “Pass the Hash”, Golden Ticket and Silver Ticket. These involve using tickets or hashes themselves to gain access. Though beyond the scope of this book, I have given a brief description of each below.
➢ Pass the Hash - Using the encrypted hash directly for access without cracking it.
➢ Golden Ticket Attack - Forge a Kerberos Ticket Granting Ticket (TGT) for persistent access.
➢ Silver Ticket Attack - Forge a service ticket for accessing specific services.
See the tool WiKi for more information.
Conclusion
In this chapter, we covered a lot of practical theory on Microsoft Windows based password security. We covered two of the main Windows security authentication protocols, Kerberos and NTLM. We took a look at Kerberoasting, a popular attack against Kerberos. We also looked at several tools...
The rest of the chapter is locked
You have been reading a chapter from
Password Cracking with Kali LinuxPublished in: Feb 2024Publisher: PacktISBN-13: 9781835888544
 © 2024 Packt Publishing Limited All Rights Reserved
© 2024 Packt Publishing Limited All Rights ReservedRegister for a free Packt account to unlock a world of extra content!
A free Packt account unlocks extra newsletters, articles, discounted offers, and much more. Start advancing your knowledge today.
undefined
Unlock this book and the full library FREE for 7 days
Get unlimited access to 7000+ expert-authored eBooks and videos courses covering every tech area you can think of
Renews at AU $19.99/month. Cancel anytime
