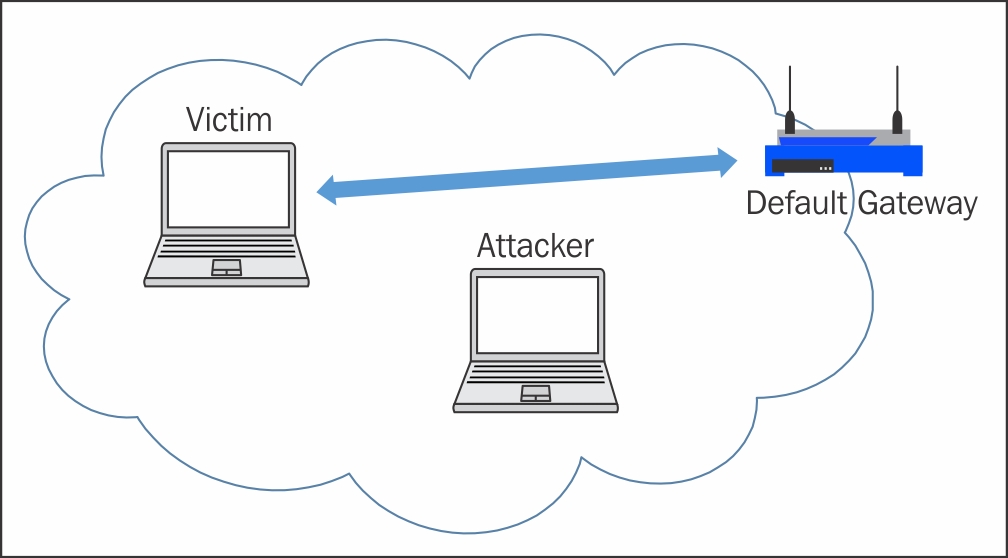
Man in the middle attacks are a class of attacks where a third party can intercept, capture, or alter the communication between two entities. Abbreviated as MITM, these attacks exploit the open nature of wireless networks that allow an attacker to see all wireless traffic being transmitted from clients to the access point. If the communication is sent in the clear or in a way that can be decrypted by the attacker, the information gleaned from a successful MITM attack could lead to a successful compromise of the target client and potentially the network infrastructure.
On wireless networks, capturing the traffic sent between two devices is relatively easy; anyone within range of the wireless signal can capture the traffic. Open networks, such as those found in public hotspots, are notoriously easy to manipulate. Though it is slightly more difficult when the target network is encrypted, it is not impractical. As we have seen in previous chapters, it is possible...