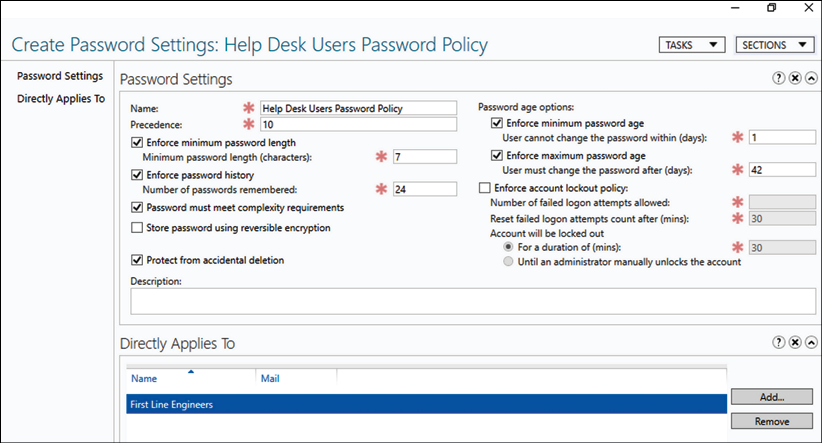
Active Directory Security Best Practices
Hackers are breaking the systems for profit. Before, it was about intellectual curiosity and pursuit of knowledge and thrill, and now hacking is big business.- Kevin Mitnick
Kevin Mitnick was once known as the world's most wanted hacker. Most of the cyber security laws that exist today were first introduced to the world because of him. For anyone who is interested in cyber security, I highly recommend his book Ghosts in the Wires. It not only talks about his life as a hacker, but it also explains the evolution of the "hacker" over time. He started hacking into phone systems first and then, as technology developed, he challenged himself with breaking into computer systems. For him, it wasn't about profit, but today, things are way more complicated. According to https://vz.to/2Zm81bn, 90% of data breaches are finically motivated. Hackers are targeting more valuable assets such as intellectual property, state secrets...