As you start to use XenMobile, you will realize that there is a wide variety of things that you can do with it. This section will teach you all about the most commonly performed tasks and most commonly used features in XenMobile.
XenMobile has one of the most important features of reporting the modules available in the mobile device manager software packages. Reporting gives XenMobile administrators a way to track devices, features, and violations in a mobile policy.
The process to access the reporting module is as follows:
Log in to your XenMobile server (
http://server_ip_address/zdm).
The login screen
XenMobile has numerous reporting options that can be used to track the status of mobile devices, installed applications, and policy compliance. Click on the Reporting tab to see the reporting screen, as shown in the following screenshot:
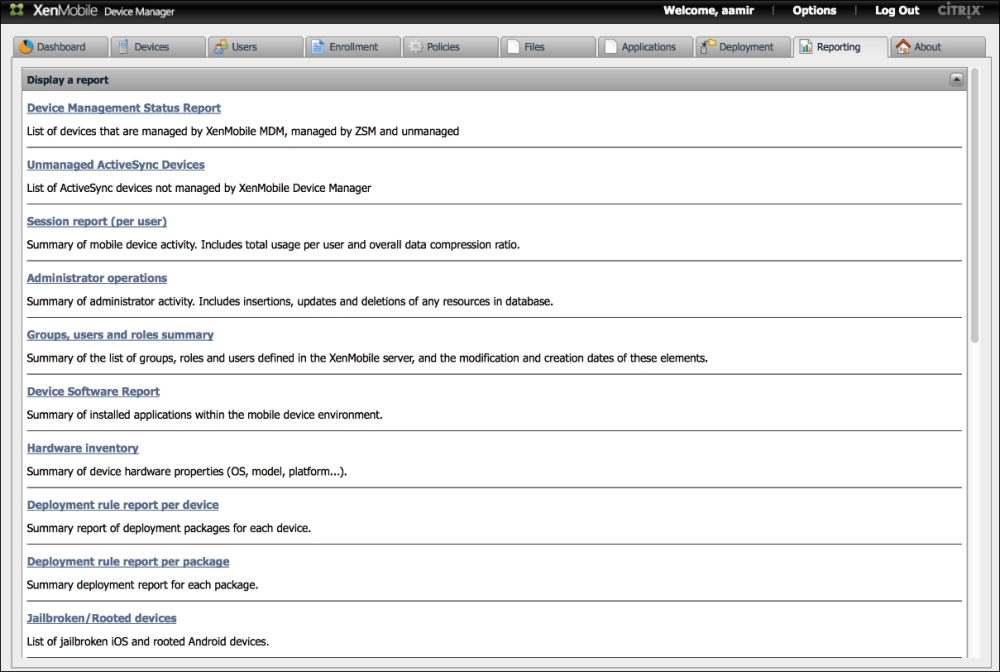
Reports
Select a report.
There are many reports, which you will find interesting. Most of them are self-explanatory. For example, hardware inventory will give you a breakdown of devices, OS, and models. Other reports that are popular are for jailbroken devices and rooted devices that show possible violations of default security settings, which could make the device vulnerable to external attacks. Overall, the reporting section will be used to review the current state of mobile devices in your organization. The following screenshot shows an example of types of devices in an organization by OS and platform (these reports can be exported into the PDF format):
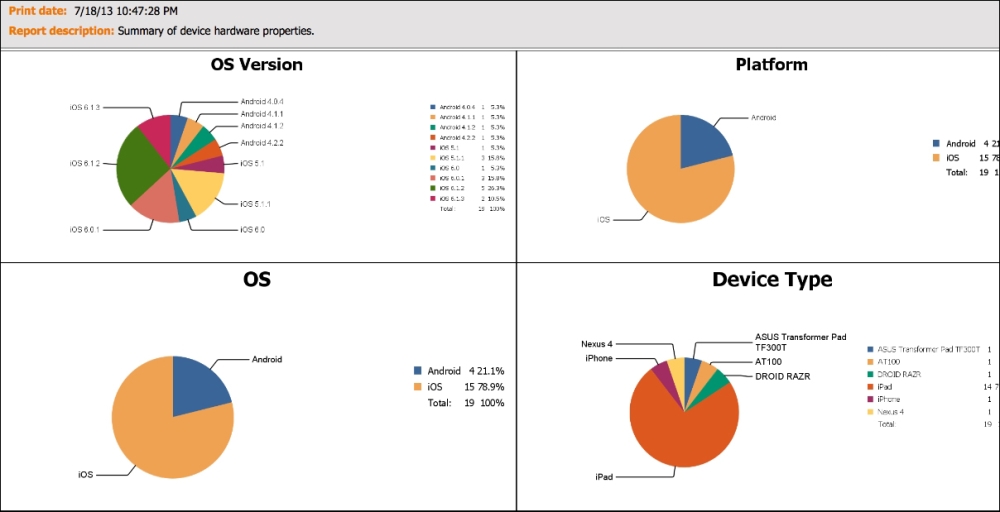
Reports
If you have internally developed iOS apps (.ipa or any iOS apps that you have licensed to distribute, you can upload those apps directly to the device manager database and deploy those apps to users' devices. XenMobile allows administrators to distribute applications to users by allowing an organization to run its own internal application stores. In addition, XenMobile allows administrators to install on or remove the applications from Google and Apple devices via the push method. The push method is an automatic installation or removal of applications to the mobile device without the need for the user to go to an application store to install an application, or manually deleting an application. The installation process is as follows:
Log in to your XenMobile server at
http://server_ip_address/zdm.Click on the Application tab.
Navigate to New | New App.
You have a few options here, which you can select. They are as follows:
Push Remove Application: This option removes the installed application
Do not backup: This option will not back up an application or application data
Install the application via push or make it available via the internal Enterprise AppStore.
Install External Apps from AppStore.
You will now be able to install and manage applications on mobile devices in your organization, as shown in the following screenshot. The following screenshot displays the XenMobile's application store. The table shown in the following screenshot displays applications for every platform. At the time of writing this book, we couldn't filter this view to show only applications for specific platforms:
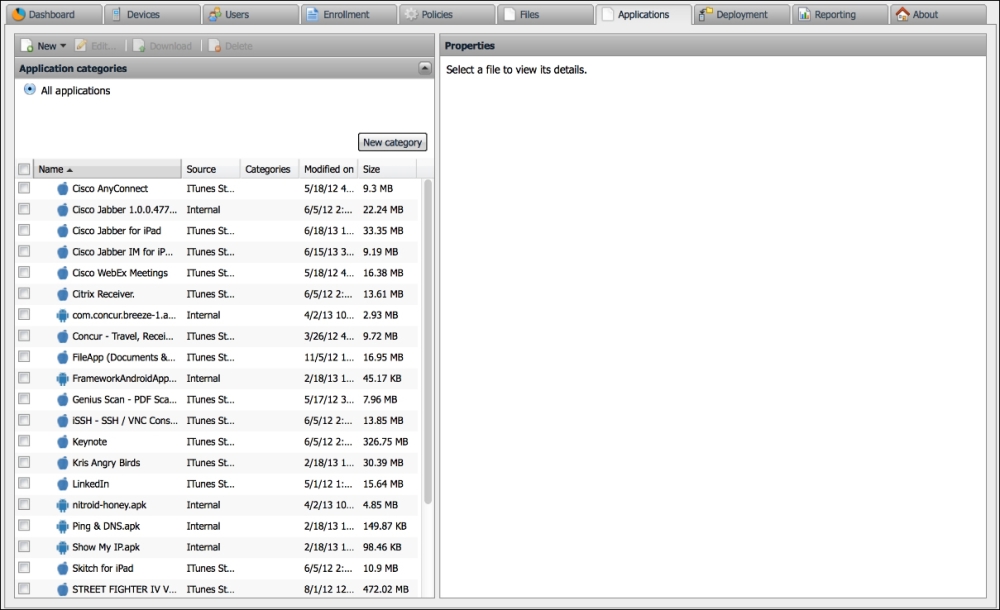
The Application store
Xenmobile provides you the unique ability to import your own applications, or link to an AppStore application for iOS devices. Lastly, you have the ability to add a volume purchase program (VPP) license file. A VPP license file allows an organization to purchase a bulk set of licenses of a single application. Therefore, their users do not have to download the same application and pay for it individually. Currently, VPP is only available for iOS applications of Apple platforms.
Secure Mobile Gateway provides granular access control for e-mail and calendar applications on devices that support Microsoft ActiveSync. You can configure Secure Mobile Gateway to allow or block access to Microsoft Exchange servers from mobile devices based on numerous device characteristics. They include the ownership of the devices, installed applications, devices rooted or jailbroken status, applications installed, and other conditions. When a device is blocked or allowed, it is reported on the XenMobile ZDM dashboard, so that the administrators have one unified view of the status of the devices.
The benefit of Secure Mobile Gateway is that it ensures that a user won't bypass your XenMobile policies that are being enforced on devices. A user who does not agree with your policies may decide to skip enrollment. He may have somehow decided that he does not need corporate applications that are being pushed or other device centric policies. However, typically most users will need access to their e-mail from their devices. If a user somehow figures out the necessary settings and credentials to configure his device manually, Secure Mobile Gateway can intercept that connection and make policies decisions based on an organization's needs. In other words, you could stop a user from accessing e-mails until he enrolls in the XenMobile MDM solution.
XenMobile Secure Mobile Gateway provides access to controls of SSL (HTTPS) ActiveSync requests made by mobile devices against backend exchange Client Access Servers (CAS).
Secure Mobile Gateway uses rules to allow or block access. A device client request is evaluated against the organization's polices. XenMobile Secure Mobile Gateway will make the determination if the mobile device is allowed to connect with the organization's Microsoft Exchange server. Xenmobile will then determine whether to allow or block access to the e-mail server from the mobile device based on the mobile device's status and the organization's security policy.
You can also use Secure Mobile Gateway to encrypt e-mail attachments that pass through the Exchange server, to ensure that only users with approved managed devices can view company documents securely and safely on their devices.
To install Secure Mobile Gateway on Windows 2008 servers you must perform the following steps:
Configure the Microsoft Forefront Threat Management Gateway.
Install Citrix Secure Mobile Gateway on the server running Microsoft Forefront Threat Management Gateway as an ISAPI plugin.
Use the Citrix SMG Installer application that came with your software.
Once Secure Mobile Gateway is installed, you can configure the instructions of Secure Mobile Gateway under the XenMobile server options.

Secure Mobile Gateway Options
We gave some basic highlights on how to install Secure Mobile Gateway. It should be noted that the installation of the Secure Mobile Gateway requires the administrator to have access on the Exchange environment to install the software. Additionally, Citrix's XenMobile documentation should be referred to for updates or changes. The following screenshot outlines how the administrators can quickly manage and view the status of the devices managed via Secure Mobile Gateway:
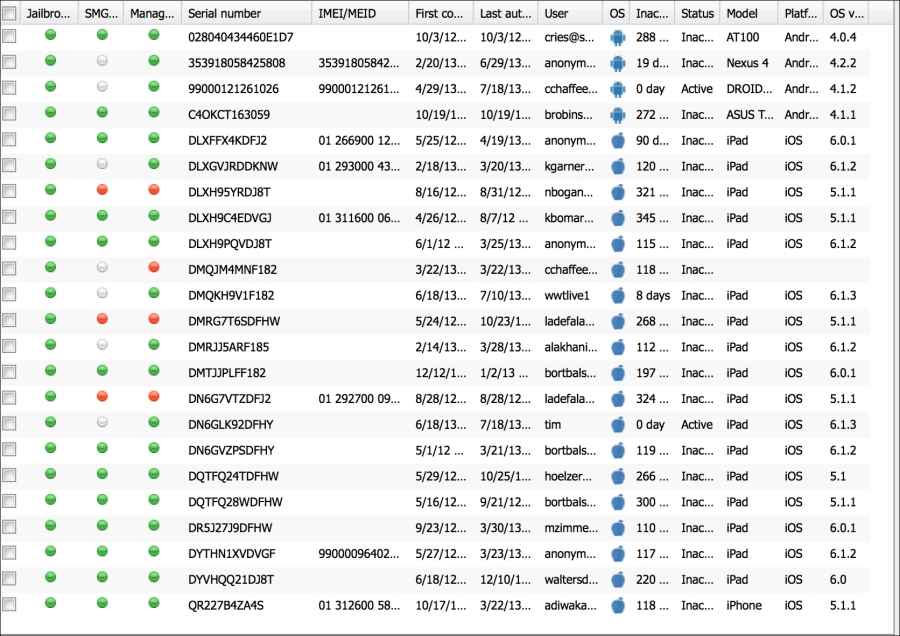
Device Status when managed via SMG
The XenMobile service manager, or commonly referred to as ZSM is an add-on for Blackberry environments. It requires the installation of Blackberry Enterprise Server (in most cases). It allows XenMobile to access Blackberry services and remotely manage, lock, and wipe Blackberry devices. Please note, that ZSM is normally used to manage Blackberry devices prior to version 10 of Blackberry OS. Most Blackberry devices running Blackberry OS 10 can communicate directly with ActiveSync. However, Blackberry OS 10 can still be managed via Blackberry Enterprise Servers, and in those cases it can still be used with ZSM.
To use ZSM, simply install the ZSM file onto the Blackberry device you plan to manage. You may need to complete additional steps on your Blackberry Enterprise Server that are dependent on your specific business configuration.
Citrix XenMobile MDM Dashboard is a way to have a quick view of the status of the current system. The dashboard can be customized by using different graphs and charts that open up based on the settings for the user authenticating the system. The following screenshot is an example of the XenMobile dashboard:
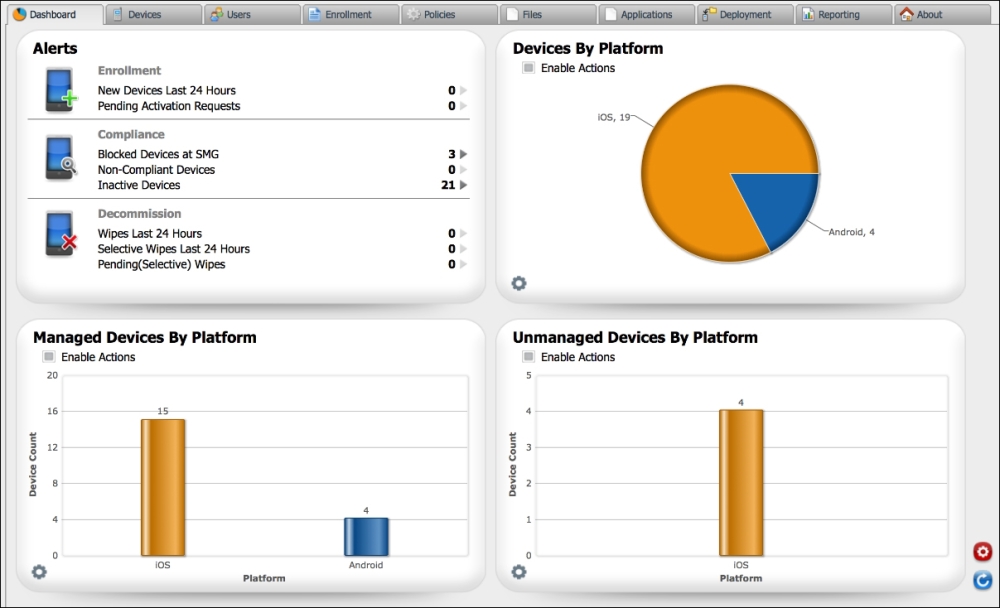
Dashboard
The dashboard's Alerts section gives an administrator the option to monitor the following alerts:
New enrollments
Non compliance
Inactive devices
Secure Mobile Gateway blocked users
Device wipes (completed, full, selective, and pending)
The following screenshot shows the current alerts for recent events:
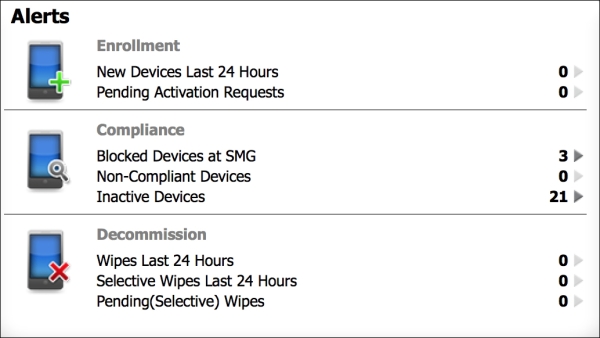
Alert Status
Additional alerts that can be configured on the Dashboard include:
Device Actions: It is an embedded dashboard widget that lets administrators interact with multiple devices and send alerts and messages to those devices.
Charts: It allows administrators to view mobile devices and group devices in multiple views. In addition, charts lets an administrator group devices by their functionality in an organization, such as employee owned or BYOD devices, as well as other categories. It is a great tool for administrators to quickly gain an understanding of devices on their network, as well as to categorize and compare other devices they have in their organization. For example, charts may be used by administrators to compare how many iPhones have been updated to the latest iOS software and how many are running older firmware. The following are the other device categories:
Devices by platform: This displays BYOD devices by their operating system, such as iOS, Blackberry, or Android.
Managed devices by platform: This displays BYOD and corporate managed devices by their operating system, such as iOS, Blackberry, or Android.
Unmanaged devices by platform: This option displays devices that were previously managed by XenMobile, but are no longer managed by the system, nor do they have corporate certificates. The reason these devices fall into this category is because they were previously managed but now have been wiped.
Device by Secure Mobile Gateway status: This option gives administrators status of the devices that have interacted with Secure Mobile Gateway. This option will allow administrators to view what devices have been managed or blocked by Secure Mobile Gateway.
Devices blocked by reason: This option allows administrators to view all the devices that are blocked. This option breaks down for administrators why devices are blocked and how many devices have violated a security policy, or do not have access to corporate resources. Some examples are the devices blocked because they fail a security policy, have blacklisted applications or invalid certificates that can be categorized and viewed by administrators.
Device ownership: This option allows administrators to view all the devices and verify if they are corporate managed devices or BYOD devices.
Android Touchdown license status: This option displays the status of touchdown licenses on Android devices.
Failed package deployments: These options will allow administrators to view what packages or applications have failed to install on mobile devices and which devices they failed to install on.
Citrix XenMobile MDM Dashboard gives administrators the power to customize the dashboard which we explored earlier. Each administrator's dashboard is customized to their own view and setup. The following screenshot is an example of a dashboard that has been customized with the options that were discussed in this section:
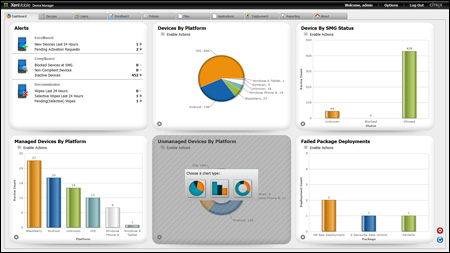
A customized Dashboard by different administrators
Citrix XenMobile MDM Dashboard gives administrators a quick way to handle common management tasks related to XenMobile. In the following example, we will examine how administrators can perform actions on a device from the dashboard, by performing the following steps:
Click on the Devices tab.
Select the device you want to perform a task on and right-click on the device:

Alert Status
Now that we know how to quickly access the menu to perform device actions, let's examine what security options are available.
Select the Security menu.

Alert Status
The Security menu allows us to perform the following options:
Lock: Administrators can lock devices from this screen. If a passcode exists on a device, it will be required to unlock it.
Selective Wipe: This option will wipe all the corporate and managed data. The user's personal data, applications, and pictures will be left intact on the device.
Full Wipe: This option will completely wipe the devices and then the devices will be reset to default factory settings.
Locate: This option determines the location of the device using cellular tower triangulation and, if available, GPS. The results will be displayed on a map. It is important to note that this feature is highly dependent on the device's settings and capabilities. Furthermore, administrators may have legal restrictions on how they track and locate people in their organization.
We just explained the top features in Citrix XenMobile. XenMobile has over 300 features and within the context of this book we cannot cover all of them. However, the features we covered are the most popular and widely used. In the next section, we will cover people and places you should get to know that will familiarize you with some of the resources which will help you in learning more about the other features available in XenMobile and start implementing them in your organization.

