In the previous chapters, we have covered some great new tools and some lesser known techniques which could be very helpful in a Penetration Test. In general, a Penetration Tester is expected to find the vulnerabilities and exploit those vulnerabilities to achieve the highest level of access but in reality, very few can fulfil of whats expected of them. Many Penetration Testers won't be able to reach the final goal due to lack of knowledge and practical experience in topics such as post-exploitation, lateral movement, data exfiltration, and especially when new tools and techniques are being released almost on a daily basis. If we ask ourself, what could be the next level as a Penetration Tester? Our answer would be—a Red Teamer. A Penetration Tester starts from Ethical Hacking and moves up to the level where he/she...
You're reading from Hands-On Red Team Tactics
Technical requirements
- Oracle's Java 1.7 or later
- Cobalt Strike (the trial version lasts for 21 days)
- Microsoft Word
- Visual Basics
Planning a red-team exercise
The red-team exercise is not just a mere pentest; it's an adversary attack simulation exercise that allows us to assess the following:
- If the organization can detect the attack or not
- If an organization is able to contain/ restrict the attack after detection
- If the organization can protect their business critical assets from the red teamers or not
- How the defenders of an organization perform an incident response in the event of such attacks
Before getting into the planning phase of the red-team exercise, first you need to understand the concept of the cyber kill chain.
Cyber kill chain (CKC)
The kill chain is a concept that derives from military operations used to structure an attack. This...
Introduction to Cobalt Strike
According to cobaltstrike.com:
"Cobalt Strike is a software for Adversary Simulations and Red Team Operations. Adversary Simulations and Red Team Operations are security assessments that replicate the tactics and techniques of an advanced adversary in a network. While penetration tests focus on unpatched vulnerabilities and misconfigurations, these assessments benefit security operations and incident response."
Cobalt Strike can be downloaded from https://trial.cobaltstrike.com/ on a trial basis, which is valid for 21 days. It may take few days for the site to provide you with the download link:

Before installing Cobalt Strike, please make sure that you have Oracle Java installed with version 1.7 or above. You can check whether or not you have Java installed by executing the following command:
java -version

If you receive the java command...
Cobalt Strike setup
The team server can be run using the following command:
sudo ./teamserver 192.168.10.122 harry@123
Here, I am using the IP 192.168.10.122 as my team server and harry@123 as my password for the team server:
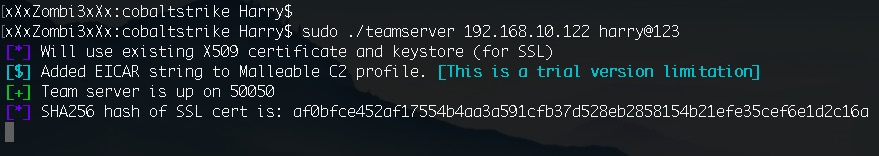
If you receive the same output as we can see in the preceding screenshot, then this means that your team server is running successfully. Of course, the SHA256 hash for the SSL certificate used by the team server will be different each time it runs on your system, so don't worry if the hash changes each time you start the server.
Upon successfully starting the server, we can now get on with the client. To run the client, use the following command:
java -jar cobaltstrike.jar
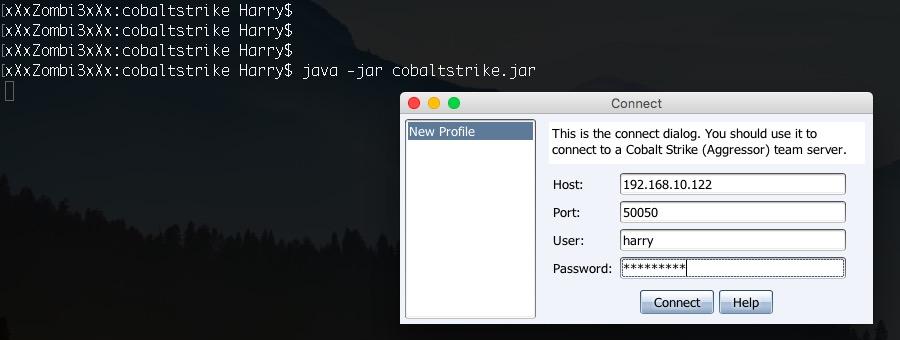
This command will open up the connect dialog, which is used to connect to the Cobalt Strike team server. At this point, you need to provide the team server IP, the Port number...
Cobalt Strike interface
The user interface for Cobalt Strike is divided into two horizontal sections, as demonstrated in the preceding screenshot. These sections are the visualization tab and the display tab. The top of the interface shows the visualization tab, which visually displays all the sessions and targets in order to make it possible to better understand the network of the compromised host. The bottom of the interface shows the display tab, which is used to display the Cobalt Strike features and sessions for interaction.
Toolbar
Common features used in Cobalt Strike can be readily accessible at the click of a button.
The toolbar offers you all the common functions to speed up your Cobalt Strike usage:

Each feature...
Customizing the team server
The team server is just a bash script that executes the cobaltstrike.jar file for starting the server. By default, the Armitage team server runs on port 55553/tcp and the Cobalt Strike team server runs on port 50050/tcp (both use SSL for communication initiation). Being the default port, it's easy for someone else to find your team server on the internet and try to connect to it in order to get access to your compromised hosts. Consequently, to protect your team server from attacks, you need to think of a few ways to protect it from other attackers. These may include the following:
- Use a strong password for team server authentication [EASY]
- Whitelist your IP from the team server firewall and deny all other IPs (this could be messy if your IP is dynamic) [MEDIUM]
- Block the 55553/tcp port from the firewall on the team server and tunnel this port...
Summary
This chapter started by exploring the red-team exercise as well as the concept of the cyber kill chain, which can be used for an attack plan. We then introduced the tool that is used for red-team operations, Cobalt Strike. Here, we also covered team servers, the Cobalt Strike installation and setup, and finally, the Cobalt Strike interface. At the end of this chapter, we customized the team server script by accessing it on a different port.
In the next chapter, you will read about reverse shell connections and how you can get them from the compromised server in a secure way so that the connection is not detected.
Questions
- Is it absolutely necessary to plan the attack? Why not just hack it like we do normally?
- Is Cobalt Strike free?
- Can we run multiple team servers on the same instance?
- My team server's fingerprint is different than the one I'm seeing on the display. What could be the reason for this?
- Does Cobalt Strike require the Metasploit framework?
- How can we use Cobalt Strike to exploit a system and get access to it?
- What else can we customize in the team server script?
Further reading
For more information on the topics discussed in this chapter, please visit the following links:
- Red Team Operations: Determining a Plan of Attack: https://www.fireeye.com/blog/products-and-services/2016/08/red_team_operations.html
- Red-team tools: http://psos-security.com/red-teaming-a-tool-for-continuous-improvement/
- Anatomy of a well-run red-team exercise: https://www.csoonline.com/article/3250249/network-security/anatomy-of-a-well-run-red-team-exercise.html
- redteam-plan: https://github.com/magoo/redteam-plan
- CobaltStrike: https://www.cobaltstrike.com/
 © 2018 Packt Publishing Limited All Rights Reserved
© 2018 Packt Publishing Limited All Rights Reserved