Using GCP Cloud Shell
To launch GCP Cloud Shell, look at the menu bar at the top and click on the icon that looks like >_ to the immediate right of the search bar. Do you notice how similar GCP’s web interface is to the web interfaces in AWS and Azure?
Figure 11.7 – Top menu bar in the GCP console
All of the Bash commands we used in Chapter 5 for AWS and Chapter 8 for Azure will work here. Our Linux VM in GCP is functionally just like any other Linux-based computer; a Bash CLI is standard. If you want, you can review some Bash commands from Chapter 5.
The Cloud Shell screen looks like this:
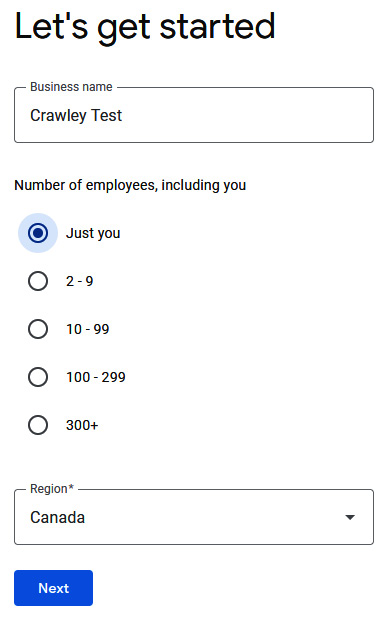
Figure 11.8 – The Cloud Shell screen
Next, let’s check out some of the tools Google provides that will help us when we work as GCP pentesters.

