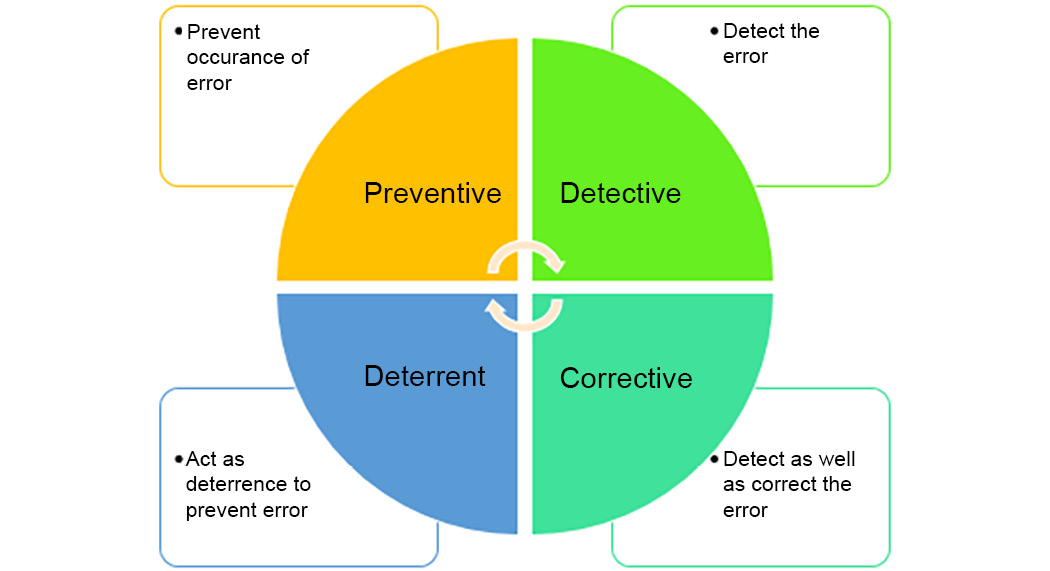
Audit Planning
This Book Comes with Free Online Content
With this book, you get unlimited access to web-based CISA exam prep tools which include practice questions, flashcards, exam tips, and more.

Figure 1.1: CISA online practice resources dashboard
To unlock the content, you’ll need to create an account using your unique sign-up code provided with this book. Refer to the Instructions for Unlocking the Online Content section in the Preface on how to do that.
Accessing the Online Content
If you’ve already created your account using those instructions, visit packt.link/cisastudyguidewebsite or scan the following QR code to quickly open the website.

Figure 1.2: QR Code to access CISA online practice resources main page
Once there, click the Login link in the top-right corner of the page to access the content using your credentials.
An Information Systems (IS) audit examines the management controls in...