What is Kubernetes?
Kubernetes is an open-source orchestration platform for containerized applications that support automated deployment, scaling, and management. It was originally developed by Google in 2014 and is now maintained by the Cloud Native Computing Foundation (CNCF) after Google donated it to the latter in March 2015. Kubernetes is the first CNCF project that graduated in 2018. Kubernetes is written in the Go language and is often abbreviated as K8s, counting the eight letters between the K and the s.
Many technology companies deploy Kubernetes at scale in production environments. Major cloud providers, including Amazon’s Elastic Kubernetes Service (EKS), Microsoft’s Azure Kubernetes Service (AKS), Google Kubernetes Engine (GKE), Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE), Alibaba Cloud Kubernetes, and DigitalOcean Kubernetes (DOKS), each offer their own managed Kubernetes services to support enterprise needs and streamline Kubernetes operations.
A Kubernetes cluster consists of two main components: control plane nodes (often referred to as the master node) and worker nodes. Each of these nodes plays a critical role in the operation of the Kubernetes environment, ensuring that applications run efficiently and reliably across diverse infrastructures, including those that support multi-tenant environments.
Here are some of the features of Kubernetes:
- Automated scheduling: Kubernetes assigns containers to different parts of your system to make sure resources are used efficiently.
- Self-healing: If a container fails or stops responding, Kubernetes automatically fixes it by restarting, replacing, or rescheduling it.
- Horizontal scaling: Need more or fewer resources? Kubernetes can automatically or manually adjust the number of containers to match demand.
- Service discovery and load balancing: It has built-in tools to help containers find each other and manage the flow of traffic to keep everything running smoothly.
- Storage orchestration: Kubernetes can automatically connect your containers to the right storage, whether it’s local, from the cloud, or a network system.
- Automated rollouts and rollbacks: Updating your applications is a breeze with Kubernetes, which can smoothly roll out new updates or revert to previous versions if something goes wrong.
- Secret and configuration management: It keeps sensitive information, and configurations secure without exposing it in your application code.
In short, Kubernetes takes care of the hard work to keep your containerized applications running.
Kubernetes adoption
When the first edition of this book was published back in 2019, the adoption of Kubernetes occupied a whopping 77% share of orchestrators in use. The market share was close to 90% if OpenShift (a variation of Kubernetes from Red Hat) was included:
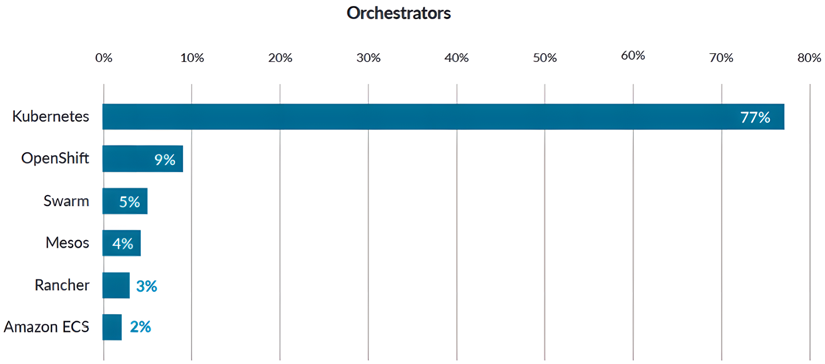
Figure 1.1 – Chart showing the share of Kubernetes adoption in 2019
According to the CNCF Organization, looking ahead to 2025, we expect Kubernetes and the cloud-native ecosystem to continue to grow and evolve.
By now, you should have a solid understanding of the core concepts of Kubernetes. In the next section, we will get into the architectural components that constitute a Kubernetes cluster, providing a detailed overview of their roles and interactions within the system.


































































