In this chapter we will cover:
JAAS-based security authentication on JSPs
JAAS-based security authentication on servlet
Container-based basic authentication on servlet
Form-based authentication on servlet
Form-based authentication with open LDAP and servlet
Hashing/Digest Authentication on servlet
Basic authentication for JAX-WS and JAX-RS
Enabling and disabling the file listing
Authentication and authorization has become a major part of all web applications. Authentication involves checking who is accessing the application. Authorization is a process of checking the access rights of the user. In the native approach, we usually store the user's information in the database and write the code in the application. We also create roles for the user and we do the mapping. Here, it is tightly coupled with the application because we have to rewrite the entire code when we connect to a new database or use any other tools such as LDAP or Kerbose. But there are advance options to handle authentication and authorization. J2EE container provides different ways to authenticate the user by configuring the XML files. We can classify authentication into two types, that is, the container-based authentication and authorization and application level authentication and authorization.
J2EE container provides interfaces and classes to provide authentication. In this chapter, we can see how we authenticate the user using JAAS, basic authentication, and form-based authentication.
In this book, we have used JAAS because it a standard framework for authentication. JAAS works on the PAM (pluggable authentication module) framework.
Authentication and authorization can be provided in the following ways:
Basic authentication: In this technique the application server gives a login form with a username and password textbox, so you don't have to create a login page yourself. You will also know the caller identity.
Form-based authentication: In this technique the container handles the authentication, but the login form is provided by the user as a JSP page.
Digest-based authentication: In this method user credentials are hashed with certain algorithms.
Certificate-based authentication: In this technique the client and the server exchange certificates to verify their identity. Achieving an SSL certificate makes the data transfer over the network secure.
The deployment descriptor is the main configuration file of all the web applications. The container first looks out for the deployment descriptor before starting any application.
The deployment descriptor is an XML file, web.xml, inside the WEB-INF folder.
If you look at the XSD of the web.xml file, you can see the security-related schema.
The schema can be accessed using the following URL: http://java.sun.com/xml/ns/j2ee/web-app_2_4.xsd.
The following is the schema element available in the XSD:
<xsd:element name="security-constraint" type="j2ee:security-constraintType"/> <xsd:element name="login-config" type="j2ee:login-configType"/> <xsd:element name="security-role "type="j2ee:security-roleType"/>
You will need the following to demonstrate authentication and authorization:
JBoss 7
Eclipse Indigo 3.7
Create a dynamic web project and name it
Security DemoCreate a package,
com.servletsCreate an XML file in the
WebContentfolder,jboss-web.xmlCreate two JSP pages,
login.jspandlogoff.jsp
Perform the following steps to achieve JAAS-based security for JSPs:
Edit the
login.jspfile with the input fieldsj_username,j_password, and submit it toSecurityCheckerServlet:<%@ page contentType="text/html; charset=UTF-8" %> <%@ page language="java" %> <html > <HEAD> <TITLE>PACKT Login Form</TITLE> <SCRIPT> function submitForm() { var frm = document. myform; if( frm.j_username.value == "" ) { alert("please enter your username, its empty"); frm.j_username.focus(); return ; } if( frm.j_password.value == "" ) { alert("please enter the password,its empty"); frm.j_password.focus(); return ; } frm.submit(); } </SCRIPT> </HEAD> <BODY> <FORM name="myform" action="SecurityCheckerServlet" METHOD=get> <TABLE width="100%" border="0" cellspacing="0" cellpadding="1" bgcolor="white"> <TABLE width="100%" border="0" cellspacing="0" cellpadding="5"> <TR align="center"> <TD align="right" class="Prompt"></TD> <TD align="left"> <INPUT type="text" name="j_username" maxlength=20> </TD> </TR> <TR align="center"> <TD align="right" class="Prompt"> </TD> <TD align="left"> <INPUT type="password"name="j_password" maxlength=20 > <BR> <TR align="center"> <TD align="right" class="Prompt"> </TD> <TD align="left"> <input type="submit" onclick="javascript:submitForm();" value="Login"> </TD> </TR> </TABLE> </FORM> </BODY> </html>The
j_usernameandj_passwordare the indicators of using form-based authentication.Let's modify the
web.xmlfile to protect all the files that end with.jsp. If you are trying to access any JSP file, you would be given a login form, which in turn calls aSecurityCheckerServletfile to authenticate the user. You can also see role information is displayed. Update theweb.xmlfile as shown in the following code snippet. We have used2.5 xsd. The following code needs to be placed in between thewebapptag in theweb.xmlfile:<display-name>jaas-jboss</display-name> <welcome-file-list> <welcome-file>index.html</welcome-file> <welcome-file>index.htm</welcome-file> <welcome-file>index.jsp</welcome-file> <welcome-file>default.html</welcome-file> <welcome-file>default.htm</welcome-file> <welcome-file>default.jsp</welcome-file> </welcome-file-list> <security-constraint> <web-resource-collection> <web-resource-name>something</web-resource-name> <description>Declarative security tests</description> <url-pattern>*.jsp</url-pattern> <http-method>HEAD</http-method> <http-method>GET</http-method> <http-method>POST</http-method> <http-method>PUT</http-method> <http-method>DELETE</http-method> </web-resource-collection> <auth-constraint> <role-name>role1</role-name> </auth-constraint> <user-data-constraint> <description>no description</description> <transport-guarantee>NONE</transport-guarantee> </user-data-constraint> </security-constraint> <login-config> <auth-method>FORM</auth-method> <form-login-config> <form-login-page>/login.jsp</form-login-page> <form-error-page>/logoff.jsp</form-error-page> </form-login-config> </login-config> <security-role> <description>some role</description> <role-name>role1</role-name> </security-role> <security-role> <description>packt managers</description> <role-name>manager</role-name> </security-role> <servlet> <description></description> <display-name>SecurityCheckerServlet</display-name> <servlet-name>SecurityCheckerServlet</servlet-name> <servlet-class>com.servlets.SecurityCheckerServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>SecurityCheckerServlet</servlet-name> <url-pattern>/SecurityCheckerServlet</url-pattern> </servlet-mapping>JAAS Security Checker and Credential Handler: Servlet is a security checker. Since we are using JAAS, the standard framework for authentication, in order to execute the following program you need to import
org.jboss.security.SimplePrincipalandorg.jboss.security.auth.callback.SecurityAssociationHandleand add all the necessary imports. In the followingSecurityCheckerServlet, we are getting the input from the JSP file and passing it to theCallbackHandler.We are then passing the Handler object to the
LoginContextclass which has thelogin()method to do the authentication. On successful authentication, it will createSubjectandPrincipalfor the user, with user details. We are using iterator interface to iterate theLoginContextobject to get the user details retrieved for authentication.In the
SecurityCheckerServletClass:package com.servlets; public class SecurityCheckerServlet extends HttpServlet { private static final long serialVersionUID = 1L; public SecurityCheckerServlet() { super(); } protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { char[] password = null; PrintWriter out=response.getWriter(); try { SecurityAssociationHandler handler = new SecurityAssociationHandler(); SimplePrincipal user = new SimplePrincipal(request.getParameter("j_username")); password=request.getParameter("j_password").toCharArray(); handler.setSecurityInfo(user, password); System.out.println("password"+password); CallbackHandler myHandler = new UserCredentialHandler(request.getParameter("j_username"),request.getParameter("j_password")); LoginContext lc = new LoginContext("other", handler); lc.login(); Subject subject = lc.getSubject(); Set principals = subject.getPrincipals(); List l=new ArrayList(); Iterator it = lc.getSubject().getPrincipals().iterator(); while (it.hasNext()) { System.out.println("Authenticated: " + it.next().toString() + "<br>"); out.println("<b><html><body><font color='green'>Authenticated: " + request.getParameter("j_username")+"<br/>"+it.next().toString() + "<br/></font></b></body></html>"); } it = lc.getSubject().getPublicCredentials(Properties.class).iterator(); while (it.hasNext()) System.out.println(it.next().toString()); lc.logout(); } catch (Exception e) { out.println("<b><font color='red'>failed authenticatation.</font>-</b>"+e); } } protected void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { } }Create the
UserCredentialHandlerfile:package com.servlets; class UserCredentialHandler implements CallbackHandler { private String user, pass; UserCredentialHandler(String user, String pass) { super(); this.user = user; this.pass = pass; } @Override public void handle(Callback[] callbacks) throws IOException, UnsupportedCallbackException { for (int i = 0; i < callbacks.length; i++) { if (callbacks[i] instanceof NameCallback) { NameCallback nc = (NameCallback) callbacks[i]; nc.setName(user); } else if (callbacks[i] instanceof PasswordCallback) { PasswordCallback pc = (PasswordCallback) callbacks[i]; pc.setPassword(pass.toCharArray()); } else { throw new UnsupportedCallbackException(callbacks[i], "Unrecognized Callback"); } } } }In the
jboss-web.xmlfile:<?xml version="1.0" encoding="UTF-8"?> <jboss-web> <security-domain>java:/jaas/other</security-domain> </jboss-web>
Otheris the name of the application policy defined in thelogin-config.xmlfile.All these will be packed in as a
.warfile.Configuring the JBoss Application Server. Go to
jboss-5.1.0.GA\server\default\conf\login-config.xmlin JBoss. If you look at the file, you can see various configurations for database LDAP and a simple one using the properties file, which I have used in the following code snippet:<application-policy name="other"> <!-- A simple server login module, which can be used when the number of users is relatively small. It uses two properties files: users.properties, which holds users (key) and their password (value). roles.properties, which holds users (key) and a comma-separated list of their roles (value). The unauthenticatedIdentity property defines the name of the principal that will be used when a null username and password are presented as is the case for an unauthenticated web client or MDB. If you want to allow such users to be authenticated add the property, e.g., unauthenticatedIdentity="nobody" --> <authentication> <login-module code="org.jboss.security.auth.spi.UsersRolesLoginModule" flag="required"/> <module-option name="usersProperties">users.properties</module-option> <module-option name="rolesProperties">roles.properties</module-option> <module-option name="unauthenticatedIdentity">nobody</module-option> </authentication> </application-policy>Create the
users.propertiesfile in the same folder. The following is theUsers.propertiesfile with username mapped with role.User.properties
anjana=anjana123
roles.properties
anjana=role1
Restart the server.
Tip
Downloading the example code
You can download the example code files for all Packt books you have purchased from your account at http://www.PacktPub.com. If you purchased this book elsewhere, you can visit http://www.PacktPub.com/support and register to have the files e-mailed directly to you.
JAAS consists of a set of interfaces to handle the authentication process. They are:
The
CallbackHandlerandCallbackinterfacesThe
LoginModuleinterfaceLoginContext
The CallbackHandler interface gets the user credentials. It processes the credentials and passes them to LoginModule, which authenticates the user.
JAAS is container specific. Each container will have its own implementation, here we are using JBoss application server to demonstrate JAAS.
In my previous example, I have explicitly called JASS interfaces.
UserCredentialHandler implements the CallbackHandler interfaces.
So, CallbackHandlers are storage spaces for the user credentials and the LoginModule authenticates the user.
LoginContext bridges the CallbackHandler interface with LoginModule. It passes the user credentials to LoginModule interfaces for authentication:
CallbackHandler myHandler = new UserCredentialHandler(request.getParameter("j_username"),request.getParameter("j_password"));
LoginContext lc = new LoginContext("other", handler);
lc.login();The web.xml file defines the security mechanisms and also points us to the protected resources in our application.
The following screenshot shows a failed authentication window:

The following screenshot shows a successful authentication window:

The JAAS-based security authentication on servlet recipe
The Container-based basic authentication on servlet recipe
The Form-based authentication on servlet recipe
The Form-based authentication with open LDAP and servlet recipe
The Hashing/Digest Authentication on servlet recipe
The Basic authentication for JAX-WS and JAX-RS recipe
The Enabling and disabling the file listing recipe
The JAAS-based security authentication on servlet is an extension of JAAS-based security authentication for JSPs. In this section, we are demonstrating that we can even apply security on servlets.
Create a new Web Project in Eclipse
Create a package,
com.packt.security.servletsCreate a Servlet with name
ProtectedServlets
The following are the steps for JAAS-based security for servlet:
Create a servlet and name it
ProtectedServlets:public class ProtectedServlets extends HttpServlet { private static final long serialVersionUID = 1L; public ProtectedServlets() { super(); } protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { PrintWriter out=response.getWriter(); try { out.println("Hello User"); out.println("Authtype:"+request.getAuthType()); out.println("User Principal:"+request.getUserPrincipal()); out.println("User role:"+request.isUserInRole("role1")); } catch (Exception e) { out.println("<b><font color='red'>failed authenticatation</font>-</b>"+e); } } protected void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { // TODO Auto-generated method stub } }Now, edit the
web.xmlfile to secure the servlet:<web-resource-collection> <web-resource-name>Servlet Protection</web-resource-name> <description>Declarative security tests</description> <url-pattern>/ProtectedServlets</url-pattern> <http-method>HEAD</http-method> <http-method>GET</http-method> <http-method>POST</http-method> <http-method>PUT</http-method> <http-method>DELETE</http-method> </web-resource-collection>
Restart the server and access the URL: http://localhost:8080/jaas-jboss/ProtectedServlets.
You would get a login form, which will authenticate the user. The servlet is the protected resource, and anyone accessing the servlet will be asked to log in. The authentication is handled by JAAS API, which is application-server-specific. Each application server will have its own implementation of security.
The Container-based basic authentication on servlet recipe
The Form-based authentication on servlet recipe
The Form-based authentication with open LDAP and servlet recipe
The Hashing/Digest Authentication on servlet recipe
The Basic authentication for JAX-WS and JAX-RS recipe
The Enabling and disabling the file listing recipe
In our previous examples we used interfaces provided by JAAS to authenticate with loginform.jsp. The previous application had a custom login form design with authentication handled by JAAS API provided by the application server.
Create a simple web-app project
Create a servlet class
Edit the
web.xmlfile for basic authenticationAdd a constraint to restrict the user from accessing the servlet
Now, we will see the basic authentication. The container provides the login form and authenticates the user and redirects the user to the servlet after authentication is successful. There is no login form involved.
Make the following changes in the web.xml file:
<login-config> <auth-method>BASIC</auth-method> <form-login-config>
Export the .war to JBoss, restart the server, and access the servlet.
In the previous example the container decides the mechanism for authenticating the servlet by reading the web.xml file. Here the <auth-method> tag has defined BASIC as the mode of authentication. We should get a login dialog box popped up when we access the secured resource.
The following screenshots show the workflow of the implementation:


In the previous sections, we demonstrated the basic authentication on servlets and JSPs. Now let's use form-based authentication on servlets.
Let's apply form-based authentication on servlet. You will need a simple web application with a servlet, a web container to handle the authentication, and the web.xml file that tells the container what to authenticate.
Let's see some simple steps for implementing form-based authentication on servlets:
Create a JSP file named
Containerform.jsp:<%@ page language="java" contentType="text/html; charset=ISO-8859-1" pageEncoding="ISO-8859-1"%> <!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd"> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=ISO-8859-1"> <title>Insert title here</title> </head> <body> <form method="POST" action="j_security_check"> Username:<input type="text" name="j_username"> password:<input type="password" name="j_password"> <input type=submit> </form> </body> </html>What do you observe in the previous code?
action=j_security_checkis the default URL, which is recognized by the web container. It tells the container that it has the user credentials to be authenticated.Now, edit the
web.xmlfile:<login-config> <auth-method>FORM</auth-method> <form-login-config> <form-login-page>/Containerform.jsp</form-login-page> <form-error-page>/logoff.jsp</form-error-page> </form-login-config> </login-config>
Build the project and export the .war files to JBoss.
The previous example demonstrated the Form-based authentication. The J2EE container reads the web.xml file, the <auth-method> tag has the form attribute set. Then it further looks for the login.jsp file, which needs to be displayed to do form-based authentication. The <form-error-page> and <form-login-page> has the login file name and the error page that needs to be displayed on authentication failure. When the user tries to access the secured resource, the J2EE container redirects the request to the login page. The user credentials are submitted to j_security_check action. This action is identified by the container and does the authentication and authorization; on success the user is redirected to the secured resource and on failure the error page shows up.
The following are the screenshots of the workflow which shows the login page for the user and displays the user information on successful authentication:
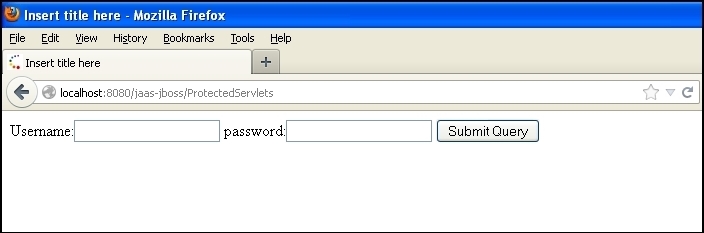
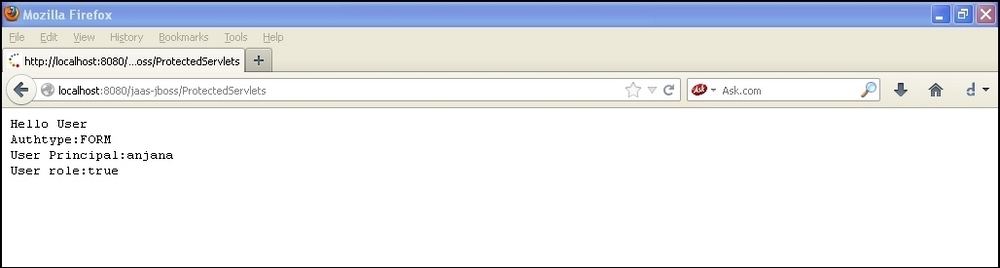
In this section we will see how we can authenticate users by retrieving the user information stored in open LDAP and JAAS. Open LDAP, as its name suggests, is a free version of the lightweight user directory protocol, which allows us to create groups and add users to it.
Download open LDAP, create roles, groups, and user.
In the JBoss application server, edit the login-config.xml file.
Perform the following steps to configure the application server to retrieve users from Open LDAP:
In the
login-config.xmlfile provide the LDAP port with the URL, credentials, and the domain that needs to be searched to find the username and password provided by the application:<application-policy name="example"> <authentication> <login-module code="org.jboss.security.auth.spi.LdapExtLoginModule" flag="required" > <module-option name="java.naming.factory.initial">com.sun.jndi.ldap.LdapCtxFactory</module-option> <module-option name="java.naming.provider.url">ldap://localhost:389</module-option> <module-option name="java.naming.security.authentication">simple</module-option> <module-option name="bindDN">cn=Manager,dc=maxcrc,dc=com</module-option> <module-option name="bindCredential">secret</module-option> <module-option name="baseCtxDN">ou=People,dc=maxcrc,dc=com</module-option> <module-option name="baseFilter">(uid={0})</module-option> <module-option name="rolesCtxDN">ou=Roles,dc=maxcrc,dc=com</module-option> <module-option name="rolesCtxDN">ou=Department,dc=maxcrc,dc=com</module-option> <module-option name="roleFilter">(member={1})</module-option> <module-option name="roleAttributeID">cn</module-option> <module-option name="searchScope">ONELEVEL_SCOPE</module-option> <module-option name="allowEmptyPasswords">true</module-option> </login-module> </authentication> </application-policy>In the
jboss-web.xmlfile, we will specify the lookup name for JAAS:jboss-web.xml <?xml version="1.0" encoding="UTF-8"?> <jboss-web> <security-domain>java:/jaas/example</security-domain> </jboss-web>
Build and deploy the WAR on JBoss, restart the server, and access the browser.
You will be prompted with a login form and JBoss authenticates the user based on the open LDAP credentials provided. The user is retrieved and is authorized with roles mentioned in the application policy. The container provides built-in APIs for authentication. The module org.jboss.security.auth.spi.LdapExtLoginModule handles the LDAP authentication process.
In the previous authentication mechanisms, the client sends the user credentials and the container validates.
The client doesn't attempt to encrypt the password.
So, our application is still not safe and is vulnerable to attacks.
This section is about passing an encrypted user credential to the server and telling the server which encryption algorithm can be used to decrypt the data.
JBoss is the application server that I have chosen to demonstrate it.
Modify
Login-config.xmlCreate
encrypt-users. propertiesCreate
encrypt-roles. properties
<login-config> <auth-method>DIGEST</auth-method> <realm-name>PACKTSecurity</realm-name> </login-config>Now, modify the
jboss-web.xmlfile. The realm name is used for hashing:<?xml version="1.0" encoding="UTF-8"?> <!-- <jboss-web> --> <!-- <security-domain>java:/jaas/other</security-domain> --> <!-- </jboss-web> --> <jboss-web> <security-domain>java:/jaas/encryptme</security-domain> </jboss-web>
Modify the
login-config.xmlfile<application-policy name="encryptme"> <!--this is used to demonstrate DIGEST Authentication --> <authentication> <login-module code="org.jboss.security.auth.spi.UsersRolesLoginModule" flag="required"/> <module-option name="usersProperties">encrypt-users.properties</module-option> <module-option name="rolesProperties">encrypt-roles.properties</module-option> <module-option name="hashAlgorithm">MD5</module-option> <module-option name="hashEncoding">rfc2617</module-option> <module-option name="hashUserPassword">false</module-option> <module-option name="hashStorePassword">true</module-option> <module-option name="passwordIsA1Hash">true</module-option> <module-option name="storeDigestCallback"> org.jboss.security.auth.spi.RFC2617Digest </module-option> </authentication> </application-policy>Now, we need to tell JBoss to encrypt the user's password. To do that perform the following steps:
Go to
E:\JBOSS5.1\jboss-5.1.0.GA\common\libGo to the folder where JBoss is installed. I have installed JBoss on my
E:Now on the command line, write
cd E:\JBOSS5.1\jboss-5.1.0.GA>And then paste the following command:
java -cp client/jboss-logging-spi.jar;common/lib/jbosssx-server.jar org.jboss.security.auth.spi.RFC2617Digest anjana "PACKTSecurity" role1
Now edit
Encrypt-users. properties:anjana=e3b6b01ec4b0bdd3fc1ff24d0ccabf1f
Encrypt roles and update
roles.properties
The previous example demonstrates the digest authentication mechanism. The password given in the J2EE container is encrypted using the MD5 algorithm. The container decrypts it and verifies the user credentials against the decrypted password. The authentication mechanism is digest and the container pops up a login dialog box for the digest mechanism similar to the basic authentication mechanism.
The following screenshot shows the workflow:

It behaves like basic authentication, but uses the encrypted password along with the realm name to decrypt.
The authentication configuration remains the same for JAX-WS and JAX-RS.
We need to give the JAX-WS or JAX-RS URL in <web-resource collection>.
Auth_type can be basic. The container would come with a form for the user to enter the username and password.
Authentication handled by container
We will first create a web service and then make the container handle the security on it.
Let's create an interface which will expose the service method and then declare an implementation class.
Let's use Tomcat 6.0 to demonstrate this.
In Eclipse-Indigo, create a dynamic web project
Server: Tomcat 6
JARs to be added to Tomcat
libfolder: https://jax-ws.java.net/2.2.7/Download the project and copy the
libfolder
Create an
interfaceand animplementationclass. Add the@WebServiceannotations to it. Create a package namedcom.packt.ws. Create an interface namedEmployeeProfileand animplementationClass:Interface:
package com.packt.ws; import javax.jws.WebMethod; import javax.jws.WebService; import javax.jws.soap.SOAPBinding; import javax.jws.soap.SOAPBinding.Style; @WebService @SOAPBinding(style = Style.RPC) public interface EmployeeProfile { @WebMethod String getSalary(); }Implementation:
package com.packt.ws; import javax.jws.WebService; import javax.jws.WebMethod; import javax.jws.WebService; @WebService(endpointInterface = "com.packt.ws.EmployeeProfile") public class EmployeeProfileImpl implements EmployeeProfile { @Override public String getSalary() { return "no salary for the month"; } }Also add the
sun-jaxws.xmlfile underWEB-INF<?xml version="1.0" encoding="UTF-8"?> <endpoints xmlns="http://java.sun.com/xml/ns/jax-ws/ri/runtime" version="2.0"> <endpoint name="EmployeeProfile" implementation="com.packt.EmployeeProfileImpl" url-pattern="/employee"/> </endpoints>Modify the
web.xmlfile as shown:<?xml version="1.0" encoding="UTF-8"?> <web-app xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://java.sun.com/xml/ns/javaee" xmlns:web="http://java.sun.com/xml/ns/javaee/web-app_2_5.xsd" xsi:schemaLocation="http://java.sun.com/xml/ns/javaee http://java.sun.com/xml/ns/javaee/web-app_2_5.xsd" id="WebApp_ID" version="2.5"> <display-name>JAX-WS-Authentication-Tomcat</display-name> <listener> <listener-class> com.sun.xml.ws.transport.http.servlet.WSServletContextListener </listener-class> </listener> <servlet> <servlet-name>employee</servlet-name> <servlet-class> com.sun.xml.ws.transport.http.servlet.WSServlet </servlet-class> <load-on-startup>1</load-on-startup> </servlet> <servlet-mapping> <servlet-name>employee</servlet-name> <url-pattern>/employee</url-pattern> </servlet-mapping> <security-role> <description>Normal operator user</description> <role-name>operator</role-name> </security-role> <security-constraint> <web-resource-collection> <web-resource-name>Operator Roles Security</web-resource-name> <url-pattern>/employee</url-pattern> </web-resource-collection> <auth-constraint> <role-name>operator</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>NONE</transport-guarantee> </user-data-constraint> </security-constraint> <login-config> <auth-method>BASIC</auth-method> </login-config> </web-app>Authenticate the web services. Edit the
tomcat-users.xmlfile and add this toserver.xml:<Realm className="org.apache.catalina.realm.UserDatabaseRealm" resourceName="UserDatabase"/>
It's generally not advisable to enable directory listing in your application. By default directory listing will be disabled on JBoss.
If it is enabled, go to your JBoss installation folder.
The following steps will help to disable and enable file listing in the application server:
Browse to the path
\server\default\deployers\jbossweb.deployer.Open
web.xmlin theWEB-INFfolder.Set the listing to
false.<servlet> <servlet-name>default</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup> </servlet>




















 Download code from GitHub
Download code from GitHub
