Security is arguably one of the most critical architectural components of any web-based application written in the 21st century. In an era where malware, criminals, and rogue employees are always present and actively testing software for exploits, smart and comprehensive use of security is a key element to any project for which you'll be responsible.
This book is written to follow a pattern of development that, we feel, provides a useful premise for tackling a complex subject—taking a web-based application with a Spring 3.1 foundation, and understanding the core concepts and strategies for securing it with Spring Security 3.1. We compliment this approach by providing sample code for each chapter in the form of complete web applications.
Whether you're already using Spring Security or are interested in taking your basic use of the software to the next level of complexity, you'll find something to help you in this book.
During the course of this chapter, we will:
Review the results of a fictional security audit
Discuss some common security problems of web-based applications
Learn several core software security terms and concepts
If you are already familiar with basic security terminology, you may skip to Chapter 2, Getting Started with Spring Security, where we start using the basic functionality of the framework.
It's early in the morning at your job as a software developer for the
Jim Bob Circle Pants Online Calendar (JBCPCalendar.com), and you're halfway through your first cup of coffee when you get the following e-mail from your supervisor:

What? You didn't think a lot about security when you designed the application? In fact, at this point, you are not even sure what a security audit is. Sounds like you'll have a lot to learn from the security auditors! Later in this chapter, we will review what an audit is, along with the results of the audit. First, let's spend a bit of time examining the application that's under review.
Although we'll be working through a contrived scenario, as we progress through this book, the design of the application and the changes that we'll make to it are drawn from real-world usage of Spring-based applications. The Calendar application allows users to create and view events.

After entering the details for a new event, you will be presented with the following screenshot:

The application is designed to be simplistic, to allow us to focus on the important aspects of security and not get tied up in the details of Object Relational Mapping (ORM) and complex UI techniques. We expect you to refer to other supplementary material in the Supplementary Materials section in Appendix, Additional Reference Material of this book to cover some of the baseline functionality that is provided as part of the sample code.
The code is written in Spring and Spring Security 3.1, but it would be relatively easy to adapt many of the examples to other versions of Spring Security. Refer to the discussion about the detailed changes between Spring Security 2 and 3.1 in Chapter 15, Migration to Spring Security 3.1, for assistance in translating the examples to the Spring Security 2 syntax. There should be no effort in translating the examples from Spring Security 3.1 to 3.0 since, other than the new features we leverage; the transition should be completely passive.
Please don't use this application as a baseline to build a real online calendar application. It has been purposely structured to be simple and to focus on the concepts and configuration that we illustrate in the book.
The web application follows a standard three-tier architecture, consisting of a web, service, and data access layer, as indicated in the following diagram:
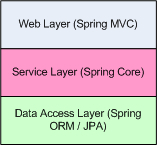
You can find additional material about MVC architectures in the Appendix, Additional Reference Material.
The web layer encapsulates MVC code and functionality. In this sample application, we use the Spring MVC framework, but we could just as easily use Spring Web Flow, Struts, or even a Spring-friendly web stack, such as Apache Wicket.
In a typical web application leveraging Spring Security, the web layer is where much of the configuration and augmentation of code takes place. For example, the EventsController is used to transform an HTTP request into persisting an event into the database. If you haven't had a lot of experience with web applications and Spring MVC specifically, it would be wise to review the baseline code closely and make sure you understand it before we move on to more complex subjects. Again, we've tried to make the website as simple as possible, and the construct of a calendar application is used just to give a sensible title and light structure to the site.
Tip
You can find detailed instructions on setting up the sample application within the Appendix, Additional Reference Material.
The service layer encapsulates the business logic for the application. In our sample application, we use DefaultCalendarService as a very light facade over the data access layer, to illustrate particular points around securing application service methods. The service layer is also used to operate on both Spring Security APIs and our Calendar APIs within a single method call. We will discuss this in greater detail in Chapter 3, Custom Authentication.
In a typical web application, this layer would incorporate business rules validation, composition and decomposition of business objects, and cross-cutting concerns, such as auditing.
The data access layer encapsulates the code responsible for manipulating contents of database tables. In many Spring applications, this is where you would see the use of an Object Relational Mapping (ORM), such as Hibernate or JPA. It exposes an object-based API to the service layer. In our sample application, we use a basic JDBC functionality to achieve persistence to the in-memory H2 database. For example, our JdbcEventDao is used to save Event objects to the database.
In a typical web application, a more comprehensive data access solution would be utilized. As ORM, and more generally data access, tends to be confusing for some developers, this is an area we have chosen to simplify, as much as possible, for the purposes of clarity.
We have endeavored to make the application as easy to run as possible, by focusing on some basic tools and technologies that almost every Spring developer would have on their development machine. Nevertheless, we provide the supplementary "getting started" information in Getting started with JBCP Calendar sample code section in Appendix, Additional Reference Material.
The primary method for integrating with the sample code is by providing Maven 3 compatible projects. Since many IDEs have rich integration with Maven, users should be able to import the code into any IDE that supports Maven. As many developers use Maven, we felt this was the most straightforward method of packaging the examples. Whatever development environment you are familiar with, hopefully you will find a way to work through the examples while you read the book.
Many IDEs provide Maven tooling that can automatically download the Spring and Spring Security 3.1 Javadoc and source code for you. However, there may be times when this is not possible. In such cases, you'll want to download the full releases of both Spring 3.1 and Spring Security 3.1. The Javadoc and source code are at the top notch, if you get confused or want more information, and the samples can provide an additional level of support or reassurance in your learning. Visit the Appendix, Additional Reference Material, to find additional information about Maven, which gives information about running the samples, obtaining the source code and Javadoc, and alternatives to building your projects without Maven.
Let's return to our e-mail and see how the audit is progressing. Uh-oh, the results don't look good:

APPLICATION AUDIT RESULTS
This application exhibits the following insecure behavior:
Inadvertent privilege escalation due to lack of URL protection and general authentication
Inappropriate or non-existent use of authorization
Missing database credential security
Personally-identifiable or sensitive information is easily accessible or unencrypted
Insecure transport-level protection due to lack of SSL encryption
Risk level is high
We recommend that this application be taken offline until these issues can be resolved.
Ouch! This result looks bad for our company. We'd better work to resolve these issues as quickly as possible.
Third-party security specialists are often hired by companies (or their partners or customers) to audit the effectiveness of their software security, through a combination of white hat hacking, source code review, and formal or informal conversations with application developers and architects.
White hat hacking or ethical hacking is done by professionals who are hired to instruct companies on how to protect themselves better rather than with the intent to be malicious.
Typically, the goal of security audits is to provide management or clients with an assurance that basic secure development practices have been followed to ensure integrity and safety of the customer's data and system function. Depending on the industry the software is targeted for, the auditor may also test using industry-specific standards or compliance metrics.
Tip
Two specific security standards that you're likely to run into at some point in your career are the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Privacy and Accountability Act (HIPAA) privacy rules. Both the standards are intended to ensure safety of specific sensitive information (credit card and medical information, respectively) through a combination of process and software controls. Many other industries and countries have similar rules around sensitive or Personally Identifiable Information (PII). Failure to follow these standards is not only a bad practice, but something that could expose you or your company to significant liability (not to mention bad press) in the event of a security breach.
Receiving the results of a security audit can be an eye-opening experience. However, following through with the required software improvements can be a perfect opportunity for self-education and software improvement, and can allow you to implement practices and policies that lead to a secure software.
Let's review the auditor's findings, and come up with a plan to address them in detail.
Inadvertent privilege escalation due to lack of URL protection and general authentication.
Authentication is one of the two key security concepts that you must internalize when developing secure applications (the other being authorization). Authentication identifies who is attempting to request a resource. You may be familiar with authentication in your daily online and offline life, in very different contexts:
Credential-based authentication: When you log in to your web-based e-mail account, you most likely provide your username and password. The e-mail provider matches your username with a known user in its database, and verifies that your password matches with what they have on record. These credentials are what the e-mail system uses to validate that you are a valid user of the system. First, we'll use this type of authentication to secure sensitive areas of the JBCP calendar application. Technically speaking, the e-mail system can check credentials not only in the database but anywhere, for example, a corporate directory server, such as Microsoft Active Directory. A number of these types of integrations are covered throughout this book.
Two-factor authentication: When you withdraw money from your bank's automated teller machine, you swipe your ID card and enter your personal identification number before you are allowed to retrieve cash or conduct other transactions. This type of authentication is similar to the username and password authentication, except that the username is encoded on the card's magnetic strip. The combination of the physical card and user-entered PIN allows the bank to ensure that you should have access to the account. The combination of a password and a physical device (your plastic ATM card) is an ubiquitous form of two-factor authentication. In a professional, security-conscious environment, it's common to see these types of devices in regular use for access to highly secure systems, especially dealing with finance or personally identifiable information. A hardware device, such as RSA's SecurID, combines a time-based hardware device with server-based authentication software, making the environment extremely difficult to compromise.
Hardware authentication: When you start your car in the morning, you slip your metal key into the ignition and turn it to get the car started. Although it may not feel similar to the other two examples, the correct match of the bumps on the key and the tumblers in the ignition switch function as a form of hardware authentication.
There are literally dozens of forms of authentication that can be applied to the problem of software and hardware security, each with their own pros and cons. We'll review some of these methods as they apply to Spring Security throughout the first half of this book. Our application lacks any type of authentication, which is why the audit included the risk of inadvertent privilege escalation.
Typically, a software system will be divided into two high-level realms, such as unauthenticated (or anonymous) and authenticated, as shown in the following screenshot:

Application functionality in the anonymous realm is the functionality that is independent of a user's identity (think of a welcome page for an online application).
Require a user to log into the system or otherwise identify themselves to be usable
Display sensitive information, such as names, addresses, credit cards, and orders
Provide functionality to manipulate the overall state of the system or its data
Unauthenticated areas of the system are intended for use by everyone, even by users who we haven't specifically identified yet. However, it may be that, additional functionality appears to identified users in these areas (for example, the ubiquitous Welcome {First Name} text). Selective display of content to authenticated users is fully supported through use of the Spring Security tag library, and is covered in Chapter 10, Fine-grained Access Control.
We'll resolve this finding and implement form-based authentication using Spring Security's automatic configuration capability in Chapter 2, Getting Started with Spring Security. Afterwards, we will explore various other means of performing authentication (which usually revolve around systems integration with enterprise or other external authentication stores).
Inappropriate or non-existent use of authorization.
Authorization is the second of two core security concepts that is crucial in implementing and understanding application security. Authorization uses the information that was validated during authentication to determine if access should be granted to a particular resource. Built around the authorization model for the application, authorization partitions the application functionality and data, such that availability of these items can be controlled by matching the combination of privileges, functionality, and data with users. Our application's failure at this point of the audit indicates that the application's functionality isn't restricted by the user role. Imagine if you were running an e-commerce site and the ability to view, cancel, or modify order and customer information was available to any user of the site!
Authorization typically involves two separate aspects that combine to describe the accessibility of the secured system.
The first is the mapping of an authenticated principal to one or more authorities (often called roles ). For example, a casual user of your website might be viewed as having visitor authority, while a site administrator might be assigned administrative authority.
The second is the assignment of authority checks to secured resources of the system. This is typically done at the time a system is developed, either through an explicit declaration in code or through configuration parameters. For example, the screen that allows viewing of other users' events should be made available only to those users having administrative authority.
Tip
A secured resource may be any aspect of the system that should be conditionally available based on the authority of the user.
Secured resources of a web-based application could be individual web pages, entire portions of the website, or portions of individual pages. Conversely, secured business resources might be method calls on classes or individual business objects.
You might imagine an authority check that would examine the principal, look up its user account, and determine if the principal is in fact an administrator. If this authority check determines that the principal who is attempting to access the secured area is, in fact, an administrator, then the request will succeed. If, however, the principal does not have sufficient authority, the request should be denied.
Let's take a closer look at the example of a particular secured resource, the All Events page. The All Events page requires administrative access (after all, we don't want regular users viewing other users' events), and, as such, looks for a certain level of authority in the principal accessing it.
If we think about how a decision might be made when a site administrator attempts to access the protected resource, we'd imagine that the examination of actual authority versus required authority might be expressed concisely in terms of the set theory. We might then choose to represent this decision as a Venn diagram for the administrative user:

There is an intersection between User Authorities (User and Administrator) and Required Authorities (Administrator) for the page, so the user is provided with access.
Contrast this with an unauthorized user:

The sets of authorities are disjoint, and have no common elements. So, the user is denied access to the page. Thus, we have demonstrated the basic principle of authorization of access to resources.
In reality, there's real code making this decision with the consequence of the user being granted or denied access to the requested protected resource. We'll address the basic authorization problem with Spring Security's authorization infrastructure in Chapter 2, Getting Started with Spring Security followed by more advanced authorization in Chapter 10, Fine-grained Access Control and Chapter 11, Access Control Lists.
Database credentials not secured and easily accessible.
Through the examination of the application source code and configuration files, the auditors noted that user passwords were stored in plain text in the configuration files, making it very easy for a malicious user with access to the server to gain access to the application.
As the application contains personal and financial data, a rogue user being able to access any data could expose the company to identity theft or tampering. Protecting access to the credentials used to access the application should be a top priority for us, and an important first step is ensuring that one point of failure in security does not compromise the entire system.
We'll examine the configuration of Spring Security's database access layer for credential storage, which uses JDBC connectivity, in Chapter 4, JDBC-based Authentication. In the same chapter, we'll also look at built-in techniques to increase the security of passwords stored in the database.
Personally identifiable or sensitive information is easily accessible or unencrypted.
The auditors noted that some significant and sensitive pieces of data were completely unencrypted or masked anywhere in the system. Fortunately, there are some simple design patterns and tools that allow us to protect this information securely with Spring Security's annotation-based AOP support.
Insecure transport-level protection due to lack of SSL encryption.
While in the real world, it's unthinkable that an online application containing private information would operate without SSL protection; unfortunately JBCP calendar is in just this situation. SSL protection ensures that communication between the browser client and the web application server are secure against many kinds of tampering and snooping.
In the HTTPS setup in Tomcat section in Appendix, Additional Reference Material, we'll review the basic options for using transport-level security as part of the definition of the secured structure of the application.
Spring Security 3.1 provides a wealth of resources that allow for many common security practices to be declared or configured in a straightforward manner. In the coming chapters, we'll apply a combination of source code and application configuration changes to address all of the concerns raised by the security auditors (and more), and give ourselves the confidence that our calendar application is secure.
With Spring Security 3.1, we'll be able to make the following changes to increase our application security:
Segment users of the system into user classes
Assign levels of authorization to user roles
Assign user roles to user classes
Apply authentication rules globally across application resources
Apply authorization rules at all levels of the application architecture
Prevent common types of attacks intended to manipulate or steal a user's session
Spring Security exists to fill a gap in the universe of Java third-party libraries, much as the Spring Framework originally did when it was first introduced. Standards such as Java Authentication and Authorization Service (JAAS) or Java EE Security do offer some ways of performing some of the same authentication and authorization functions, but Spring Security is a winner because it packages up everything you need to implement a top-to-bottom application security solution in a concise and sensible way.
Additionally, Spring Security appeals to many, because it offers out-of-the-box integration with many common enterprise authentication systems; so it's adaptable to most situations with little effort (beyond configuration) on the part of the developer.
It's in wide use, because there's really no other mainstream framework quite like it!
In this chapter, we have:
Reviewed common points of risk in an unsecured web application
Reviewed the basic architecture of the sample application
Discussed the strategies for securing the application
In the next chapter, we'll explore how to get Spring Security set up quickly and get a basic understanding of how it works.



















