The Need for Cyber Intelligence
In this chapter, you will learn about the necessity of transforming data into actionable intelligence. You will also learn that there is a difference between cyber intelligence and cyber threat intelligence. In this chapter, we will review:
- The need for cyber intelligence
- The application of intelligence in the military
- Different types of intelligence
- How intelligence drives operations
- Introduction to maneuver warfare
We will take a look at how intelligence has been used in the military and how the military incorporates intelligence to plan for missions. We will review high level concepts of maneuver warfare and use these as a new approach to understanding how to utilize information, so we can remove uncertainty and be proactive against threats to our environment.
Need for cyber intelligence
Are we using the data from our security software and services to transform the data into actionable intelligence that informs an organization's strategic and tactical business decisions?
In a recent SANS survey, phishing (72%), spyware (50%), ransomware (49%), and Trojans (47%) are the threats most seen by respondents' organizations in 2017. Organizations are being attacked daily by numerous threats. Alert fatigue is developing from the overwhelming amount of data to sort through and understand where to start remediating. There are many tools to discover vulnerabilities and potential threat vectors. In our world, sorting through this information is a challenge as there are always competing interests within the information security organization and the business. Leaders must strike the right balance of security and operations, as well as risk and compliance.
From textbooks, we've been taught that in security we should identify, contain, and eradicate vulnerabilities on the network so that we reduce the risk of being compromised. We've been led to believe that security will save the company from the bad guys and that we will be given the power to do that. However, the reality is much more complex, with chief information security officer (CISO) and managers balancing budgets, engineers trying to get change requests approved, lack of human resources due to burn out or availability, dealing with vendors, company culture, world culture, and organization processes hindering our ability to respond to these threats that can cause a considerable risk to the organization and its information. Uncertainty, fog of war, and friction are a part of life as a security professional.
The questions that come to mind are as follows:
- How do we reduce this uncertainty?
- What is the priority?
- How do we focus our efforts?
- How do we provide actionable information so that I can get my stakeholders on board?
- How do I train my team?
- Where do we begin to remediate? Can I even remediate?
The threat landscape is always changing. Every day we hear of a new group of hackers that are targeting systems that are vulnerable to X and Y. There are reports of nation-state cyber espionage attempts on the national media. The scary thing is that there may be an attack happening and no one has caught on. There seems to be general paranoia about who will be next and if that day comes, I hope it isn't me.
This book is meant to help executives and analysts understand their role in raising the bar, from effective communication of the state of their security, to gathering information about their environment. How we address this is by building a cyber intelligence capability that provides accurate information about the exploitation potential of vulnerabilities that exist within the environment by known adversaries, resulting in appropriate measures taken to reduce the risk to organizational property.
The application of intelligence in the military
Cyber threat intelligence is an analysis of an adversary's intent, opportunity, and capability to do harm. This is a discipline within information security that requires a specific skill set and tools used by threat intelligence analysts.
Cyber intelligence is the ability to gain knowledge about an enterprise and its existing conditions and capabilities in order to determine the possible actions of an adversary when exploiting inherit critical vulnerabilities. It uses multiple information security disciplines (threat intelligence, vulnerability management, security configuration management, incident response, and so on) and tool sets to gather information about the network through monitoring and reporting to allow decision makers at all levels to prioritize risk mitigation.
Over the past few years, we've seen a list of new certifications focusing on penetration testing and ethical hacking. These skills are perfect for the personnel on the ground looking for vulnerabilities within organizations using tools and methods that a malicious actor would use. There are so many tools that provide the ability to look, find, monitor, and report on their environment. How do we apply those same concepts to the architecture of an enterprise? How do we think like an attacker and build the capability within our architectures with the capability to mitigate and/or reduce the risk? The goal of the following few sections is to create a proactive defense mindset and lay the foundation for building a cyber intelligence capability architecture in your organization.
Intel stories in history
Having the capability to gather information on an adversary has been in practice in the art of warfare for centuries. The importance of using intelligence helps guide military commanders' decision-making for future operations. Military organizations have sections dedicated to operating their intelligence capability. In order to understand how to apply intelligence in our security operations, we should have an understanding of what intelligence is and how it has been used in military history.
The American Revolutionary War
In order to combat an intimidating and larger British force, General George Washington needed to do something to even the playing field. The odds were against the fledgling American army as they were understaffed, under trained, and had little to no budget. The answer to this problem was espionage.
The Americans needed to know about their adversary's actions in order for them to win the Revolutionary War. Washington needed patriots who were close to the British at all levels of society. So he employed ordinary people, such as farmers, tailors, housemaids, and other patriots to build spy rings. Additionally, he turned British spies into double agents. The Americans had established multiple networks of agents passing information between the lines, informing Washington of the whereabouts of the British and what their next plans were. As mail was intercepted, General Washington proposed to, "...contrive a means of opening them without breaking the seals, take copies of the contents, and then let them go on. By these means we should become masters of the whole plot." The intelligence that was gathered was used to conduct a massive man-in-the-middle / deception operation, actively changing the narrative, causing confusion, and disrupting communications for the British.
Napoleon's use of intelligence
Anyone who has opened a history book has heard of Napoleon Bonaparte. As a military leader, he led multiple campaigns during the French Revolutionary Wars and went on to lead France against other nations during the Napoleonic Wars. His military innovations in military tactics at the time are now studied by many military organizations and he is known to many as one of the greatest commanders in history.
What was Napoleon's take on the importance of intelligence? A study of The Jena Campaign of 1805 by Jay Luvaas stated that Napoleon directed intelligence gathering and actions, as follows:
"To reconnoiter accurately defiles and fords of every description. To provide guides that may be depended on. To interrogate the cure and postmaster. To establish rapidly a good understanding with the inhabitants. To send out spies. To intercept public and private letters. To translate and analyse their contents. In a word, to be able to answer every question of the general-in-chief when he arrives at the head of the army. A general should neglect no means of gaining information of the enemy's movements, and, for this purpose, should make use of reconnaissance, spies, bodies of light troops commanded by capable officers, signals, and questioning deserters and prisoners."
Napoleon had an understanding that intelligence is multi-faceted and was not limited to understanding the strengths and weaknesses of the opponent. He wanted to use the information gathered about the land to find the best place to move his army, to have the advantage and know where to avoid. His officers didn't send out spies arbitrarily to any town to gather information, they sent them to strategic areas of interest.
Some types of intelligence
To better understand the importance of an intelligence capability in the military, we must also recognize the different disciplines.
HUMINT or human intelligence
HUMINT is the collection by a trained HUMINT collector of foreign information from people and multimedia to identify elements, intentions, composition, strength, dispositions, tactics, equipment, personnel, and capabilities. It uses human sources as a tool and a variety of collection methods, both passive and active, to gather information to satisfy the commander's intelligence requirements and cross-cue other intelligence disciplines.
HUMINT operations collection can be executed overtly or by clandestine operations.
Overt collection is normally done in the open and through legal means without concealment. Clandestine collection is normally done by personnel who are trained in the foreign languages and cultures of the country they are assigned so that collection efforts are secret and that they mix in with the local populace.
Examples:
- Espionage
- Interrogation of personnel
- Patrolling
- Reconnaissance
IMINT or image intelligence
IMINT means the technical, geographic, and intelligence information derived through the interpretation or analysis of imagery and collateral materials.
Examples:
- Aerial reconnaissance photos
- Satellite imagery
MASINT or measurement and signature intelligence
MASINT is technically derived intelligence that detects, locates, tracks, identifies, and/or describes the specific characteristics of fixed and dynamic target objects and sources. It also includes the additional advanced processing and exploitation of data derived from IMINT and SIGINT collection.
OSINT or open source intelligence
OSINT is public information that has been deliberately discovered, discriminated, distilled, and disseminated to a select audience in order to address a specific question.
Examples:
- Anything that can be found on the internet: Facebook, Twitter, LinkedIn
- Information that is acquired from newspapers, magazines, television, radio, and so on
- Whitepapers, conference presentations, and public studies
- Photos
SIGINT or signals intelligence
SIGINT is intelligence derived from electronic signals and systems used by foreign targets, such as communications systems, radars, and weapons systems. SIGINT provides a vital window for our nation into foreign adversaries' capabilities, actions, and intentions.
Examples:
- Intercepting messages and using cryptanalysis to decipher them
- Listening to who is communicating and how many times they are communicating to a person or group
COMINT or communications intelligence
A sub-discipline within SIGINT where technical and intelligence information is derived from interception of foreign communications by other than the intended recipients; it does not include the monitoring of foreign public media or the interception of communications obtained during the course of counterintelligence investigations within the United States.
For example: listening in, analyzing, and decoding military radio traffic, teletype, and fax signals.
ELINT or electronic intelligence
Technical and geolocation intelligence derived from foreign non-communication, electromagnetic radiation emanating from anything other than nuclear detonations or radioactive sources that do not contain speech or text.
Examples:
- Analysis of beeps on magnetic tape
- Analysis of emanations of a source to identify what it is and where it is coming from
FISINT or foreign instrumentation signals intelligence
A subcategory of SIGINT, COMINT, and MASINT that consists of technical information and intelligence derived from the interception of foreign electromagnetic emissions associated with the testing and operational deployment of non-United States aerospace, surface, and subsurface systems.
Examples:
- Analysis of machine to machine language
- Remote access and control transmissions, such as from remote keyless systems, wireless doorbells, and wireless traffic light control systems
TECHINT or technical intelligence
Intelligence derived from the collection, processing, analysis, and exploitation of data and information pertaining to foreign equipment and materiel for the purposes of preventing technological surprise, assessing foreign scientific and technical capabilities, and developing countermeasures designed to neutralize an adversary's technological advantages.
Examples:
- Reconnaissance missions showing that the adversary has a new aircraft that is capable of doing X and Y
- Competing businesses developing a new product that is capable of reducing X percentage of work and decreasing Y percentage of price
MEDINT or medical intelligence
The category of intelligence resulting from collection, evaluation, analysis, and interpretation of foreign medical, bio-scientific, and environmental information that is of interest to strategic planning and to military medical planning and operations for the conservation of the fighting strength of friendly forces and the formation of assessments of foreign medical capabilities in both military and civilian sectors.
Example:
- Understanding where medical facilities are within an area and what their capabilities are
All source intelligence
The intelligence products, organizations, and activities that incorporate all sources of information and intelligence, including open source information, in the production of intelligence. All-source intelligence is a separate intelligence discipline, as well as the name of the function used to produce intelligence from multiple intelligence or information sources.
Examples:
- Drives collection to answer the priority information requirements
- Provides the enemy situation
- Provides intelligence summary reports and other intelligence reports
- Supports situational understanding
- Provides predictive estimates of enemy actions; specifically, enemy courses of action
- Provides all source target packages
Intelligence drives operations
Operations rely on sound decision-making from leaders who are capable of making them. Like many IT projects, we don't go from idea to reality in seconds. It takes planning, managing stakeholders, getting people on board with the idea, massaging egos, and so on. But how did we get that idea in the first place? It also didn't just pop up from nowhere.
Ideas are born from trying to fix or improve something that we've dealt with using data that we believe may or may not be true. Babies do not learn how to walk and crawl on their own. They see a toy, they get frustrated because they can't get it, and then they learn to crawl. They see people walking on two feet, practice, struggle to stand, and eventually take their first steps. This is because they had a problem, used data from their own experiences, tested their theories, and came to conclusions.
Every organization has a vision and a mission statement that is meant to be the core of its existence. It is the same way business leaders communicate their intent to their employees.
The military has a concept called commander's intent, which mirrors the intention of that particular unit, brigade, regiment, division, or corps. It drives all of the supporting units to a single unified purpose of meeting that intent so that they can complete the mission.
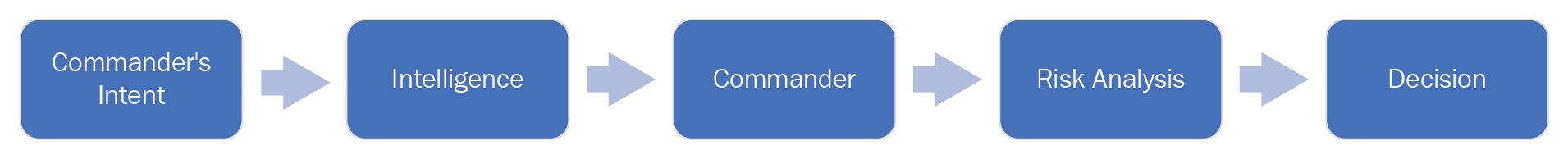
Commanders have a lot of responsibility and don't want to make a decision on every piece of data coming at them. They make decisions based on specific pieces of data that pertain to solving a specific question. Gathering of that information for the commander is based on a term called Priority Information Requirements (PIRs). These PIRs are what drives intelligence gathering operations as it provides guidance on what information is the most important to the commander so that they can plan for the next steps.
Good PIRs have three criteria:
- They ask only one question
- They focus on a specific fact, event, or activity
- They provide intelligence required to support a single decision
Military examples:
- What size force is defending objective A?
- Will enemy battalion X arrive before Y time on Z date?
- How many obstacles are on D road that will impede our movement?
Can we not apply the same logic within our IT/InfoSec organizations? The idea is no different to gathering metrics for Key Performance Indicators (KPIs). When we have targets, we need to measure them and analyze them to see whether or not we have met or missed the mark. Either way, the information gathered will decide what we do next.

Having a top-down approach when defining specific information to be derived from our security tools, will fuel our intelligence capabilities when evaluating the best way to move forward.
Let's use the Center for Internet Security Controls top five as commercial PIR examples. These are high level PIRs that can be filtered down to the tactical and operational teams to answer:
- Do we have an inventory of authorized and unauthorized devices?
- Tactical: Do we have a complete list of authorized devices?
- Operational: How are we continuing to gather this list?
- Tactical: Do we have the capability of identifying unauthorized devices?
- Operational: Where are we finding these devices?
- Tactical: Do we have a complete list of authorized devices?
- Do we have an inventory of authorized and unauthorized software?
- Tactical: Do we have a list of authorized software?
- Tactical: What are our most critical applications?
- Operational: Where are these located?
- Tactical: How are we protecting these?
- Operational: What security tools are in place to ensure that the information does not get compromised?
- Tactical: Do we have a list of unauthorized software?
- Operational: Where do the systems with this software exist?
- Do we have secure configurations for hardware and software?
- Tactical: What systems and software have secure configurations?
- Operational: How are we monitoring any deviation from the standard?
- Tactical: What systems and software do not have secure configurations?
- Operational: How do we develop secure configurations for systems and software?
- Tactical: What systems and software have secure configurations?
- Do we have a continuous vulnerability assessment and remediation capability?
- Tactical: Do we have the capability of scanning for vulnerabilities in all areas of the network?
- Operational: Do we have an accurate list of subnets allocated to the organization?
- Tactical: Do we have the capability to patch vulnerabilities that have been found?
- Operational: How can we influence application/system owners to patch when we do not have the authority to tell them to do it?
- Tactical: Do we have the capability of scanning for vulnerabilities in all areas of the network?
- Do we control the use of administrative privileges?
- Tactical: Do we have a list of privileged users?
- Operational: Who are they?
- Tactical: What are the levels of privileged user access?
- Operational: Who has what level of access?
- Tactical: Do we have a list of privileged users?
Once we begin to look at the different functions of an information security organization, we can treat them as separate disciplines of intelligence gathering internally and externally. We begin to see that each security team utilizes the answers from high level PIRs to provide the status to the senior leadership of the organization.
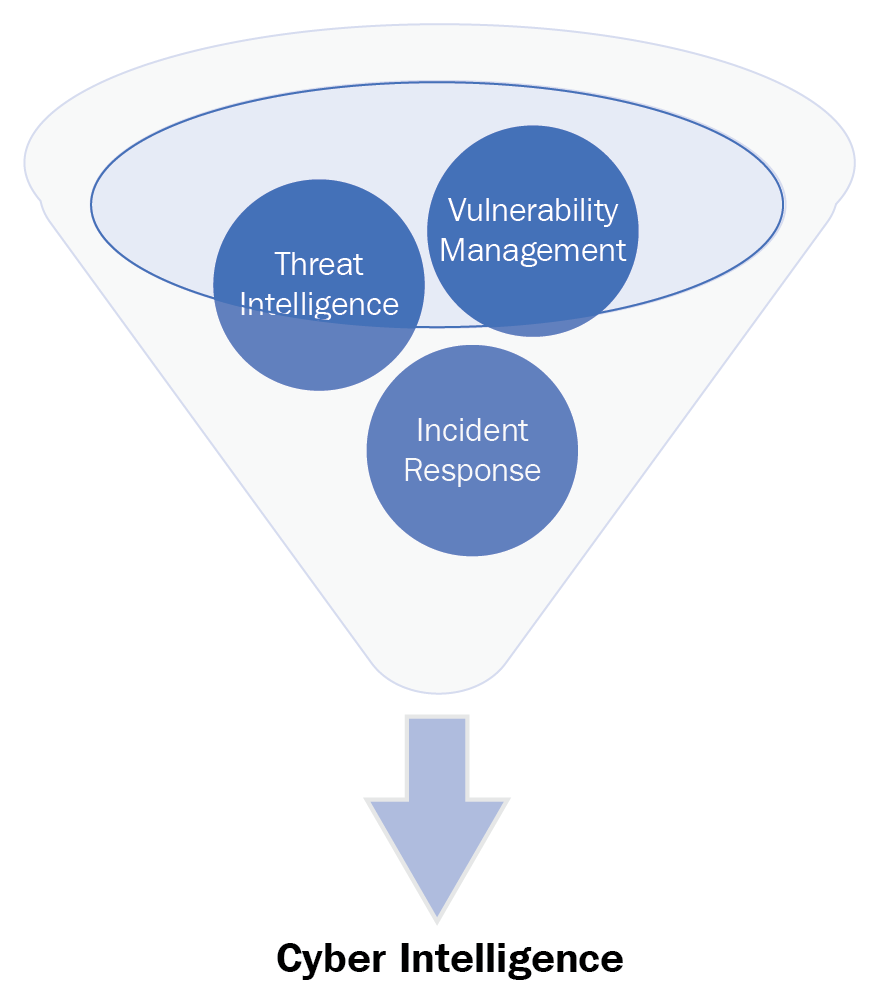
This would provide the capability of an organization's leadership to understand the environment, apply the risk management processes, and make a decision on where to dedicate resources:

The reality is that it is difficult to begin processing the information from multiple sources to make a big picture or battlespace. We have to accept that there will be ambiguity and not-clearly defined targets. Building this capability will take time, collaboration, and a mindset change at all levels.
Flow of IT/InfoSec operations can be seen in the following image:

Putting theory into practice isn't simple
Rachel was a friend that was asked by a CISO to solve a problem. At the time, her marching orders were simple. Identify vulnerabilities and report vulnerabilities. But she wondered, what does identifying and reporting vulnerabilities solve? It doesn't solve anything. She had identified a problem but there was no means to solve it. Why? She was in a huge environment stretching across the globe that required change requests to be put in and multiple entities to sign off on a single patch.
Let's not even talk about the sheer amount of patches that needed to be reviewed and approved by non-technical staff, or the fear of impacting operations. There isn't a simple solution for this problem as there were other dependencies and unknowns, such as vendors and shadow IT. Her team did not have the ability to patch, which was a huge problem. It was difficult to get anything done. There was an organizational culture change that needed to be addressed. There were policies and procedures that needed to be updated. There were multiple problems in security that need to be prioritized. There were organizational changes, personnel moves, people leaving, people on-boarded, that is, more dependencies.

Maybe a single set of services look like the preceding mind map. The IT operations and IT security operations in the organization were a complex beast. But this was just a small problem in the bigger picture.
The real question was, how does your piece of the pie keep this organization safe? Well, her piece of the pie didn't keep her organization safe. The reality was that she had a team that highlighted known vulnerabilities and provided inputs to a risk metric that was presented on a global risk dashboard. On this dashboard were other security teams' pieces of the pie. A dashboard that consisted of red, amber, and green. The more red there was meant the more you were going to be harassed. More green meant that you weren't going to be harassed. Sound familiar?
Does more green really mean that you are at less risk? Does being more red really mean that you are a risk?
The data isn't complete. Maybe it told her that there are certain areas that need attention, but what this didn't tell her is where she needed to pay attention the most as a service manager. More on her story later.
I can't imagine how it would be for the CISOs or security professionals who have to manage all of this data. It's like looking at a ship and knowing all of the holes but not knowing where to plug up first, all while asking for an additional supply of corks to use to fix them, because you may have five or six. Wait! One or two corks are rotted. It's a never-ending cycle of which holes to plug up first. What gator is closest to the boat? Which fiery hoop do I jump through now?
If organizations were castles, we'd have to man the walls and keep a constant eye out for trouble. But castles get breached and it doesn't matter how big or well defended the castle is because there will always be a blind spot. Where are your security blind spots?
So how is it that companies with plenty of resources for tools and personnel still get breached? How many conferences have I been to where I've seen the next big thing in security? There are tools for cyber deception. There are tools that use artificial intelligence and machine learning. We have heuristic analysis and two-factor authentication. NextGen AV! Defense in depth! We have best practices, certifications, and bootcamps. We are manning our castles with personnel who have the best equipment and training but we've still seen major institutions get hacked left and right. Target, JP Morgan, Dun & Bradstreet, they may or may not have been compliant, but they were not secure. We know that compliance is not security. Frameworks, compliance, standards, benchmarks, and so on are all foundation references to building a program but it shouldn't be where we stop. We need to level up, change how we think and operate.
Call it DevSecOps. Call it agility. Call it synergy or collaboration. Our teams have to be as flexible and adaptable as our adversary so that we can anticipate their next moves. We can only do that by processing all of the intelligence that we receive and utilizing it to guide how we decide to protect our organizations.
Understanding the maneuver warfare mentality
We've seen the movies, of soldiers lined up in rows marching towards each other with their officers shouting orders, horns blaring, armor glistening, and flags in the air. This is called attrition warfare, where the point of winning was wearing down the opponent by constantly reducing their resources, such as supplies and personnel. The one who was the victor typically was the one with more resources. This was considered normal until someone did something else that wasn't in the rulebook or wasn't expected. Officers were being targeted at the onset of battle, causing dysfunction in the lower ranks. Enemy soldiers did not have uniforms, causing paranoia for opposing forces. Suddenly, military organizations needed to change their tactics in order to survive in combat. They needed to adapt to opponents that did not follow conventional rules.
Follow the process, the process will save you
I went through some military training where the instructor had us all stand up in a room, raise our right hands, and do the wax-on, wax-off motion, and we repeated the word follow the process, the process will save you. It was meant for us to stay within our box and not deviate from the rules. It meant that we should not question the process because this process has been in existence and it is proven to work. There were people that loved the process so much that they breathed it. It was their doctrine. Groups of these people would band together and perfect the idiosyncrasies of the process. Processes are necessary for running operations, as they provide a sequence of what to do when and who will do what when. It is simple. Stay in your lane.
Well, today is different to yesterday. There have been processes that have been in place for years. Like lanes on a road, processes need to be reinforced, reworked, and improved. All organizations are different in the way that they run their IT operations. Maneuver warfare fits the description of what a malicious actor would utilize to get into a network. Defense in depth is another way of saying attrition warfare. Screened subnets, network segmentation, and sandboxing; it is the idea that we should be taking ground from our opponents at different levels to decrease the possibility of exploitation. We need to change the game. Our adversaries are maneuvering for our crown jewel information, finding different vectors, or avenues of approach, to gain access to it.
Defeat is extraction of information or critical loss of business capability.
How do we build processes within our organization that allow for agility, initiative, trust, and collaboration to take action? We need a strategy that allows us to be flexible and continuously monitor our strengths and weaknesses within our organizations' security programs. We must be able to adapt to change quickly and have the capability to anticipate the probability of exploitation of our critical vulnerabilities in strategic areas of interest. We need to have the support and authority to take initiative in exploiting opportunities to improve security.
If we continue to follow our processes, will they save us from compromise?
What is maneuver warfare?
A Prussian general and military theorist, Carl Von Clausewitz, introduced maneuver warfare to the world in his book On War. He was a combat veteran, and was interested in studying the art and science of war, in particular, the campaigns fought by Frederick the Great and Napoleon. Both of these men took their smaller armies and were able to carry out successful campaigns against their opponents through maneuvering.
Maneuver warfare advocates that strategic movement can bring about the defeat of an opposing force more efficiently than by simply contacting and destroying enemy forces until they can no longer fight.
There are six main elements of maneuver warfare. Each of them is explained in the following sections.
Tempo
Tempo is the rate or speed of motion or activity; pace.
KPIs are measurable values that provide a metric to gauge how well a function is achieving business objectives.
Here are a few examples from ITIL KPI Service Operation that we can use to understand how activity or tempo can be measured:
- Mean time to resolve: The average time between the start and resolution of an incident
- Mean time to detect: The average time to detect incidents
- Incident resolution effort: The average work effort for resolving incidents
We use KPIs to continuously improve processes within our organizations using values that we can be certain are true. Zero-day exploits, advanced persistent threats, new ransomware attacks—uncertainty is a constant for a security professional. It can be crippling to the decision-making process and it makes things much more difficult. Some are afraid to make a call because they haven't received all of the information yet. Some call it paralysis by analysis. How do you manage the uncertainty?
Let's take an excerpt about uncertainty from intelligence operations:
Identify and evaluate existing conditions and capabilities
On the basis of those existing conditions and capabilities, estimate possible enemy courses of action and provide insight into possible future actions
Aid in identifying friendly critical vulnerabilities that the threat may exploit
Assist in developing and evaluating friendly courses of action"
Military officers undergo training where they have to make decisions on data that is incomplete. It prepares them to make decisions when they are in critical or otherwise crisis situations. It is called recognitional decision-making. This method of decision-making can increase the tempo and the ability to maintain the initiative against the enemy. However it requires a large amount of study on the topic prior to the crisis occurring, moral courage, and the leader assuming the risk of quick planning without the aid of other experienced personnel.
The OODA Loop
Recognitional decision-making is taught using Boyd's cycle, also known as the OODA Loop:
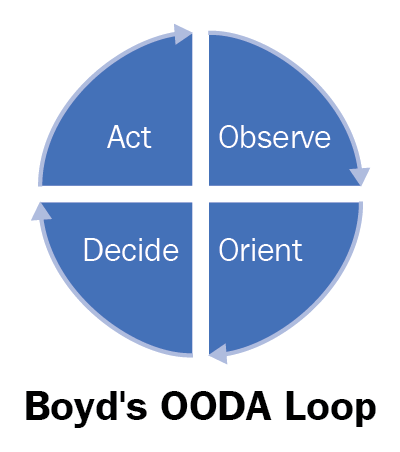
- Observe:
- Situational awareness of yourself, your environment and your adversaries; noting any changes surrounding those variables.
- From a security perspective, consider tool sets used by an adversary who scans a network, actively looks for vulnerabilities, tracks their targets, and is looking at what their target is doing or is about to do. In this regard, the defender can begin to anticipate future moves and get into the mind of the adversary.
- Orient:
- After observation, we begin to develop a mental image of the situation thus gaining awareness
- With this, we recognize that a decision is necessary in order to influence the situation
- We will diagnose, recognize, and analyze changes in the environment
- Decide:
- After recognition that a decision is necessary, a course of action is determined
- In this case, decisiveness is sought, frequently with an acceptable degree of risk
- Effective and succinct communication of this decision is key when we talk about leading subordinates
- Act:
- Timely and tactically sound decisions are useless alone
- In order to influence the situation effectively, leaders must turn decision into action in a time competitive environment
Every organization has their version of the OODA Loop. Every adversary has their version of the OODA Loop.
This decision-making model can be used in organizations to think about their ability to perform each step in the loop:
- What is the problem?
- Is my organization capable of observing a problem?
- Can my team(s) orient themselves in a position to address the problem?
- Who is responsible for making the call?
- How quickly and efficiently can we address the problem?
Decision-making is not a simple process in communicating. With so many components that are interfacing with each other, it is challenging to get a consensus on a topic without impacting another stakeholder. If business is a battlefield, it is wrought with uncertainty for a security leader of where to put their time and energy into. Using the concepts from maneuver warfare, we can begin to define how these tenets are applicable to our situation.
Center of gravity and critical vulnerability
The concept of center of gravity is the idea that each organization has a focal point of strength. It may be a specific capability that is possessed and being utilized. It may be a relationship of two or more factors that creates a larger source of strength. We want to use our centers of gravity and take away our adversaries' center of gravity. Maneuver warfare requires that the practitioner identify and understand what the other sides' center of gravity is. We should not try to eliminate that strength directly, however, we should concentrate our strength on some relative weakness that would adversely impact the enemy's center of gravity.
Where is the enemy weakest? Where is the flank? Where can we cause the most disruption to their operations? Our adversaries' center of gravity is their ability to move around the battlespace as they wish, and exploit opportunity at their will until they are discovered. Ethics, laws, and regulations prohibit us from counterattacking our opponents but we still have to defend our network in the following ways:
- By identifying the capabilities that we have established in our IT organizations, we can conduct gap analyses against known capability maturity models to find our critical vulnerabilities for each function as well as identify our center of gravity
- By understanding our current capabilities and identifying gaps in capability, we will begin to develop how the strategy to improve capability will support operations and how best we can employ our teams
- Once this is place, we start to look how our teams are able to understand how their work integrates with current operations, it opens the doors to possibilities to be proactive in our defense
Surprise – creating and exploiting opportunity
In addition to improving our decision-making and understanding our strength and weaknesses, we should be able to adapt to the unexpected. Imagine a car race, where you see individual vehicles go around the track, jockeying for position, and trying to win the race. With each lap, a car may make a move to pass if they see an opening between vehicles. In another moment, there may have been a crash where either you hit the vehicles involved or you get out of the way. All of these are examples of a set of circumstances that were not expected but created an opportunity to exploit.
How do we surprise our opponent if our job is to defend? Combining information about adversaries, their capabilities, and their intent as well as having a full understanding of our organization's capabilities and gaps provides us a view to possible threat vectors to our most coveted information. If we are able to estimate the path of least resistance, we may have a tactical advantage to reinforce known weak points in the architecture, process, or procedures.
Combined arms – collaboration
The armed forces do not consist of one mass force. It separates into each warfighting domain. The army emphasizes fighting on land, the navy focuses on the sea, the air force are masters of the air space, and the marines are amphibious. Each of these organizations are important and must combine their capabilities to ensure success of military campaigns. Prior to any engagement, leaders of the organizations are planning together to best use their tools to complete their mission objectives.
Collaboration and synergy are terms we have heard in the business world that express working with another group or organization to achieve business objectives. In large organizations, it is understandable that the complexity of IT and remote management of teams can cause silos to be formed and communication to be challenging. When we break down silos and establish proper communication channels we will be able to address incidents, problems, and solutions faster.
Flexibility
Where as collaboration tries to ensure communications between entities are smooth and seamless, a military organization must remain flexible in order to be able to react to an opponent(s) who changes their tactics. Flexibility is achieved through understanding the strengths and weaknesses of capabilities within the organization and training to address the different scenarios. It is the ability to establish redundant capabilities to reduce single points of failure in processes, people, and skills.
Decentralized command
Decentralized command is the delegation of authority to subordinates to carry out the commander's intent. Within the proper guidance, this allows leaders to take initiative in the planning, training, and execution of their assigned missions. By training the leaders to act independently, it allows for operational and tactical flexibility.
Summary
In this chapter, we've learned that intelligence is a capability and a discipline with various sub-disciplines. Understanding this concept, we can gain an abstract view of how intelligence can be gathered from different disciplines within an information security organization to provide our leaders with actionable data. This is only the tip of the iceberg. As organizations and technology grow more complex, it is necessary to have a process and capability established to grab data from multiple sources, aggregate it, and provide it to the team leads to take action on. We've reviewed the high-level tenets of maneuver warfare and its application in the information security domain. Maneuvers are dependent on having the right information given to commanders so that they can make a decision on what steps to take next. Understanding maneuver warfare gives us another view of how we can operate in an uncertain world. All of this does not mean anything if we do not have the capability to gather, analyze, and disseminate.
In the next chapter, we'll talk about the intelligence cycle and each of its phases so that we can develop the initial framework for an intelligence capability within your organization.




















