ISO27001 – Definitions and Security Concepts
My aim in writing this book is providing you a comfortable way to understand and enhance the cybersecurity and privacy within your entity. Of course this book is not targeted at seasoned experts in ISO27001 implementation; moreover, when I planned it, my targets were managers that know almost nothing about cybersecurity and privacy but want to improve company security, even using third-party consulting (and therefore wanting to know whether the external service is wasting internal budget), or novices that, for some reason, have to deal with IT security in a smoooth way.
It’s a long trip, although I will try my best to help you digest an enormous amount of information in a short, agile book. I hope you find it interesting and forgive those mistakes that, unfortunately, will appear no matter how many corrections I make.
Since it’s a long trip, I suggest you prepare by putting on a pair of comfortable slippers and making a huge cup of coffee (or tea, as you wish), and sit down and relax.
In this chapter, we will cover the following topics:
- The 27k family of standards
- Confidentiality, integrity, and availability
- Information security concepts and definitions
- Governance, policies, and incident management
- Differences of NIST
The 27k family of standards
There’s more than walls and fences, if any, to protect in your company. Let’s suppose your company has developed a new product. This product can guarantee a nine-figure income for at least the next decade. So, what’s the most important asset of your company?
As you continue to read this book, this sentence will soon become your mantra. Ensuring the confidentiality, integrity, and availability of information is the goal of information security. These fundamental information security factors aid in ensuring that an entity’s data is secure. So, getting back to your product, what does your company need to defend itself from?
The main pain points are the following:
- The leakage or disclosure of sensitive or confidential information, exposed either by accident or design
- The compromise of personally identifiable information
- Critical information being tampered with, either by mistake or on purpose, without the knowledge of the entity
- Critical corporate data disappearing without a trace or the possibility of recovery
- The unavailability of critical business information when it is required
The preceding statements lead us to a couple of valuable mantras about information:
Let’s put it simply: everyone within the company needs to understand and help out to improve the security posture, and often, just following the company policies and procedures (or even using common sense) will vastly improve the standard security. For instance, just adopting and respecting a clean desk policy may prevent the cleaning staff from viewing unauthorized documents (and we don’t know whether the cleaning staff is somehow ready to sell our company and/or private information – insiders can wear any kind of hat).
Let’s see another example: your company spends thousands of dollars on implementing privacy screens (privacy filters designed for computer users to keep their private and confidential information safe). But if you leave your laptop unattended, then they are completely useless.
Every entity can be at risk of data leakage by different means, and if a company wants to improve its security standards, it feels the need to improve those. The vast majority of companies (at least in Europe) use so-called frameworks (such as ISO 27001/27002, NIST, etc.) simply because they’re ready to apply and use. More specifically, in regard to European entities, by implementing ISO 27001, you are also implementing things such as General Data Protection Regulation (GDPR, aka the European privacy law) and security over the cloud. Basically, you’re killing three birds with one stone.
The following ISOs give us a foundation to establish an effective information management system:
- Information security management systems – ISO/IEC 27001:2017
- Security approaches – Requirements and ISO/IEC 27002:2022
While ISO 27001 has been prepared to provide requirements for establishing, implementing, maintaining, and continually improving an information security management system, ISO27002 is designed for organizations of all types and sizes. It is to be used as a reference for determining and implementing controls for information security risk treatment in an information security management system (ISMS) based on ISO/IEC 27001
Born as an independent, non-governmental entity, the International Organization for Standardization (ISO) comprises the national standards bodies from the 165 countries that make up its membership. There are more than 1,500 voluntary international standards developed by ISO.
According to Wikipedia:
Products and services of high quality can be produced by adhering to the standards. Using the standards, businesses can boost productivity while reducing waste and errors. Comparing products from different markets makes it easier for businesses to expand into new markets and helps global trade develop on an equal footing. The standards also protect consumers and end users of products and services by ensuring that certified products meet international minimum standards.
Since we are interested in the information security side of ISO, let’s set aside what’s irrelevant to our scope.
The ISO/IEC 27001 requirements for approved third-party Information Security Management System (ISMS) certifications can be applied to third-party accreditations of ISMSs. ISMS audits are conducted by accredited certification bodies as part of the accreditation process. With the help of ISO/IEC 27001, they can be confident that their management systems and procedures comply.
ISO/IEC 27002, a guidance document, provides information security best practices and implementation guidance. As part of the risk management process, ISO/IEC 27001-compliant entities can use these controls to protect their information assets.
Confidentiality, integrity, and availability
One of the main components of ISO 27k is something called the CIA triad (of course, this has nothing to do with either the Mafia and/or the US Central Intelligence Agency).
In information security, the CIA triad is widely accepted as a model. It’s not a single doctrine, and there is no single author of it either. On the contrary, the model seems to have evolved over time, with roots that go back as far as modern computing. It appears that Ben Miller, vice president of Dragos, is the only one who has done any research into the triad’s origins. When he went looking for the origins of this model, more than a decade ago, he couldn’t find anything. Concepts appear to have been pulled from a variety of sources, including a 1976 Air Force report and a paper from the 1980s comparing commercial and military computer systems.
It’s mostly based on a triangle made of confidentiality, integrity, and availability, which are the main pillars of IT security.

Figure 1.1 – CIA triad
Whatever the case may be, the CIA triad includes the following three elements:
- A company’s data must be kept private to maintain confidentiality. This usually means that data should only be accessed or modified by processes and users who have been granted permission to do so.
- Integrity is the quality of being able to have confidence in one’s data. An accurate and authentic record should be kept in a safe place where it cannot be changed or tampered with.
- Authorized users should be able to access data at any time (availability), just as it is critical to keep unauthorized users out of an entity’s data in the first place. Maintaining a stable network of computers, servers, and other devices is to be considered an integral part of availability.
Let’s see an example to better understand these concepts.
You are sending an email to me because you’d like me to clarify some concepts you don’t understand (probably because they were badly explained by me – who knows). While preparing the email, you also attach a document in which there’s the part you don’t understand. Finally, you send the email.
In this case, confidentiality means that you sent this email to me and to me only. Unless a third party was involved in our email exchange, this email is sent exclusively to me.
If you send me a message with a few words, including Dear Mr., some sort of body text, some salutation at the end, and an attachment, I will receive exactly that message body and that attachment (this is integrity; if we want, we can measure the number of kilobytes used to send that message and you can bet that the body text and attachment are the same size).
Finally, we can log in to an email server at any time, 24/7, using our email client, and check whether there are new messages: that’s availability.
But, of course, this is just an example of how to adopt the CIA triad.
Access control methods such as two-factor authentication and passwordless sign-on are examples of confidentiality. However, it’s not just about allowing authorized users access; it’s also about preventing certain files from being accessed. Both accidental disclosure and malicious attacks can be prevented by using encryption.
Access control and encryption can help maintain data integrity, but there are many other ways to protect data integrity, both from attacks and corruption. It can be as simple as making a file read-only at times. In some cases, data can be audited using hashing or data checksums, which ensure the integrity of the data. In some cases, the integrity of a system may be shielded from external influences.
Availability refers to the ability of your systems to remain operational in the event of an attack. Distributed Denial of Service (DDoS) attacks, for example, are based on a lack of resources. You can ensure uptime by building redundancy into your systems to combat DDoS attacks. In the absence of an attack, systems can still fail and become unavailable, so load balancing and fault tolerance can be used to prevent systems from failing.
It is important for security professionals of all kinds to understand these concepts. For information security professionals, the triad of these three concepts makes it easier to think about the interrelationships, overlaps, and conflicts between them. Security professionals can use the tension between the triad’s three legs to determine their information security priorities and procedures.
Information security concepts and definitions
Other best practices to remember are as follows:
- Know thy system.
Knowing the system is perhaps the most critical factor when attempting to defend it. It makes no difference whether you’re protecting a castle or a Linux server if you don’t understand the intricacies of what you’re defending.
Knowledge of what software is running on your systems is an excellent illustration of this in the area of information security. What daemons do you have running? What kind of exposure do they generate? A decent self-test for someone in a small- to medium-sized environment would be to choose an IP address at random from a list of your systems and see whether you can recall the precise list of ports that are open on the computers.
“It’s a web server, therefore everything’s just running on ports 80, 443, and 22 for remote management; that’s it,” a skilled administrator should be able to say—and so on for each sort of server in the ecosystem. When seeing port scan findings, there should be no surprises.
In this kind of test, you don’t want to hear, “Wow, what’s that port?” Having to ask that question indicates that the system administrator is not entirely aware of everything operating on the computer in question, which is exactly what we want to prevent.
- The least privilege
The next crucial principle is that of least privilege. Least privilege simply states that people and objects should be able to do only what they need to do their tasks. I include these kind of examples because administrators frequently configure automatic processes that must be able to perform specific activities, such as backups. What usually occurs is that the administrator adds the user performing the backup to the domain admins group, even if they could get it to function in another way. Why? Because it is less difficult.
Finally, this is a philosophy that is intended to directly contradict human nature, namely laziness. It is always more difficult to grant granular access that allows only specified tasks than it is to grant a higher level of access that covers everything that needs to be done.
This rule of least privilege just reminds us not to succumb to this temptation. Don’t back down. Take the time to make all access as granular and as minimal as feasible.
- Defense in depth
Defense in depth is likely the least understood of the four concepts. Many people believe that it is as simple as stacking three firewalls instead of one or running two antivirus applications instead of one. This is technically correct, but it is not the fundamental nature of defense in depth.
The true concept is to build various types of protection between an attacker and an asset. These layers don’t even have to be products; they might be applications of other notions, such as least privilege.
Consider an attacker on the internet attempting to breach a web server in the Demilitarized Zone (DMZ; basically a physical or logical subnetwork that contains and exposes an entity’s external-facing services). Given a huge vulnerability, this may be quite simple, but with an infrastructure utilizing defense in depth, it may be substantially more difficult.
We need to take into consideration activities such as hardening (appliances such as routers, firewalls, IPDs/IDSs, and target hosts) and widely implementing antivirus and antimalware—any of these procedures can potentially prevent an attack from being totally or partially successful. The notion is that instead of thinking about what has to be put in place to stop an attack, we should think about what needs to happen for it to be successful. Perhaps an assault had to pass via network infrastructures to get to the host, execute, build an outbound connection to a host outside, download stuff, run it, and so on.
What if any of those steps were to fail? The key to defense in depth is to place barriers at as many sites as possible. Our aim is to try to make it so that it’s hard for potential intruders to get into our network. By using this kind of approach, it will be difficult for hostile code to run on your systems, run your daemons and/or services as the least-privileged user, and so forth.
The advantage is straightforward: you have more chances to prevent an attack from succeeding. Someone may go all the way in, all the way to the box in question, and be stopped by the fact that the malicious code would not run on the host. However, once that code is modified so that it may run, it may be detected by an upgraded IPS or a more stringent firewall ACL. The goal is to secure whatever you can at every stage. Secure everything—file permissions, stack protection, ACLs, host IPSs, limiting admin access, running as limited users; the list is endless.
The core premise is also straightforward: don’t rely on a single solution to protect your assets. Consider each layer of your defense as though it were the only one. When you follow this method, you have a better chance of stopping attacks before they reach their aim.
Also, in IT security (and ISO 27001 itself, which is a framework that is continuously improving), new concepts are arising on almost a yearly basis, and one of the most interesting concepts around is called zero trust.
Conventional security models are based on perimeter security. In practice, the protection of the corporate ecosystem trusts all traffic and action flowing within the perimeter.
The zero trust approach, on the other hand, is designed to address even all those so-called lateral threats that move through networks. How? By exploiting an approach linked to microsegmentation and the definition of granular perimeters, based on users, data, and their location.
- Prevention is preferable, but detection is required.
This is a basic concept, yet it is incredibly significant. The concept is that while it is preferable to stop an attack before it is successful, if it is, it is critical that you are aware that it occurred. For example, you may have safeguards in place to prevent code from being executed on your system, but if code is executed and something is done, it is vital that you are notified and can act immediately.
The difference between learning about a successful attack within 5 or 10 minutes and learning about it weeks later is enormous. Having the knowledge early enough can often result in the attack not being successful at all; for example, the attacker may get on your box and add a user account, but you get to the machine and take it offline before they can do anything with it.
Regardless of the situation, detection is critical because there is no guarantee that your prevention actions will be effective.
Other remarkable best practices are as follows:
- Protection and utility must be balanced.
Computers in a workplace could be entirely safeguarded if all networks were destroyed and everyone was thrown out—but then they would be of no use to anyone.
- Determine your vulnerabilities and make a plan.
Not all of your resources are equally valuable. Some data is more vital than others, such as a database holding all accounting information on your clients, such as bank IDs, social security numbers, addresses, and other personal information (we’ll talk about privacy later). Identifying what data is more sensitive and/or significant will assist you in determining the level of protection required to safeguard it and designing your security tactics accordingly.
- Use uncorrelated defenses.
Using a single strong protection mechanism, such as authentication protocols, is only effective until it is breached. When numerous layers of separate defenses are used, an attacker must apply a variety of tactics to get past them.
Because the causes of breaches aren’t always obvious after the fact, it’s critical to have data to track backward. Even if it doesn’t make sense at first, data from breaches will eventually help to improve the system and prevent future attacks.
- Run frequent tests.
Hackers are constantly honing their skills, so information security must evolve to keep up. IT professionals should run tests, conduct risk assessments, reread the disaster recovery plan, double-check the business continuity plan in the event of an attack, and then repeat the process.
- The bottom line.
IT security is a difficult job that requires both attention to detail and a high level of awareness. However, like many seemingly complex tasks, IT security can be broken down into basic steps that can simplify the process. That’s not to say it’s easy, but it keeps IT professionals on their toes.
So, while we have seen some ways to improve your security posture, I am afraid to tell you that we have only scratched the tip of a huge iceberg. Although hardening is a very important topic and everyone dealing with security should at least understand these basic concepts, an entity is a bit more than a document with a plethora of how-tos.
An entity is the sum of many elements: core values, community, respect and many more, but also ethics, risk management, compliance, and administration, which form the governance of a company.
Governance, policies, and incident management
We are going to talk about what makes an entity (or company, association, or whatever you want to call it).
Governance
We can define corporate governance as “a toolkit that enables management and the board to deal more effectively with the challenges of running a company. Corporate governance ensures that businesses have appropriate decision-making processes and controls in place so that the interests of all stakeholders are balanced.” (This definition is taken from https://www.itgovernance.co.uk/.)
A strong corporate governance framework can assist you in meeting the requirements of laws and regulations such as GDPR, that is, the European privacy law.
GDPR, for example, requires data controllers and processors to verify compliance with its standards through specific documentation, such as applicable logs, rules, and procedures.
Throughout this book, I will use examples from GDPR, although there are several other legislations around, such as LGPD (the Brazilian privacy law) or CCPA from California, and many more about to come. But GDPR is, with the UK variant, an umbrella for roughly 400 million people in 28 countries and therefore, the most popular.
Using IT governance aspects will assist you in creating and maintaining proper policies and procedures to help satisfy your data privacy obligations.
IT governance is a component of corporate governance that aims to improve overall IT management and get more value from investments in information and technology.
IT governance frameworks have the following functions:
- Assisting entities in efficiently managing their IT risks and ensuring that information and technology operations are aligned with their overall business objectives
- Showing demonstrable achievements in relation to broader business plans and goals
- Complying with applicable legal and regulatory duties, such as those outlined in GDPR
- Assuring stakeholders that your entity’s IT services are trustworthy
- Facilitating a higher return on IT investment
- Following any business governance or public listing guidelines or procedures
According to ISACA (https://www.isaca.org), we can break IT governance (ISO 38500) into five different domains:
- Value delivery
- Strategic alignment
- Performance management
- Resource management
- Risk management
Consider that there are several frameworks and methodologies to comply with IT governance, such as ISO 27001, NIST, ISO 27000 (aka ITIL), COBIT, ISO 31000, ISO 38500, and ISO 22301. Since we are dealing with a security compliance framework, it would be better to stick to the most popular, that is, ISO27001 and NIST, alongside ISO 27701 (privacy framework).
Policies and procedures
Policies and procedures are the documents that describe how your business is run in the information security industry.
A policy is a set of rules or guidelines that your entity and its employees must follow in order to comply:
- Policies provide answers to the questions of what employees do and why they do it
- A procedure is a set of instructions for implementing a policy
So, what exactly is a policy?
A policy is defined as a set of rules or guidelines that your entity and employees must follow in order to achieve a specific goal (i.e., compliance).
What is the function of a policy?
An effective policy should outline what employees must and must not do, as well as directions, principles, and decision-making guidance. It should answer the questions What? and Why?. Both are related to the meaning of a policy and it’s important to understand what a policy is and why it is needed.
What exactly is a procedure?
A procedure is the inverse of a policy; it is the instructions on how to implement a policy:
- It is the step-by-step guide for implementing policies, outlined previously
- A policy defines a rule and a procedure defines who is expected to do what and how
- Procedures provide answers to questions such as how, when, and where
What is the importance of documented policies, procedures, and protocols?
Too many businesses regard policies and procedures as a necessary evil, failing to consider their purpose. It’s not about following best practices or becoming a soulless corporate entity; the goal of policies and procedures is to explain what management wants to happen and how it will happen.
I’ve come to believe that the primary difference between a small and medium business is not found in quantifying a company’s maturity by revenue or employee count, but rather in whether or not management has taken the time to develop, implement, and maintain policies and procedures.
So far, this definition has not disappointed me; companies with mature policies, procedures, and systems are easier to audit, have a better understanding of their security posture and risk, and appear to be operating far more sustainably than those that haven’t paid much attention to governance.
Objections about policies and procedures
Once management understands the definitions of policies and procedures, they will no longer ask, “What are policies and procedures?” or “What is the purpose of a policy?” and instead proceed to ask, “Why do I have to write policies and procedures?”
Management in small businesses generally has the same set of objections to writing down a set of policies and procedures, all of which are related to difficulty, company culture, and time constraints. But keep in mind that the benefits outweigh the inconvenience of policies and procedures. The goal of policies and procedures is much more than simply writing down some rules.
It’s difficult to create policies and procedures.
But it’s extremely difficult! Yes, but also no. Most businesses that do not have mature policies and procedures are doing fairly well; otherwise, they would not be in business. It’s certainly easier to define security from the start, but that doesn’t mean it can’t be simple to start with what you’re doing now and refine it later.
Sometimes, the real objection isn’t how difficult it is to write down policies and procedures, but how afraid most people are of writing down how they’re doing things incorrectly. Begin with where you are, and then be realistic about where you want to go. You may not be keeping up with best practices in some areas, but if you let embarrassment keep you from putting policies in writing, you’re missing the point. Knowing exactly what you’re doing now allows you to determine what you should be doing tomorrow. It’s how you can create a real budget, identify real enterprise risks, and respond effectively when something goes wrong.
But no worries, we’ll deep dive into these things later.
Incident management
The goal of the incident management procedure is to restore normal service operation as soon as possible and to minimize the negative effect on business activities while maintaining agreed-upon standards of service quality. The incident management process’s goals are to do the following:
- Ensure that standardized processes and procedures are utilized for effective and timely incident response, analysis, recording, continuous improvement and reporting
- Increase incident visibility and communication to business and IT support personnel
- Improve the business view of IT by taking a professional approach to addressing and communicating problems as they might arise
- Align incident management efforts and priorities with business priorities
- Maintain satisfaction among users with IT service quality
So, we conclude a very rapid journey on the essential topics concerning governance. Let’s move on to an interesting topic, differences of NIST.
Differences between ISO 27001 and NIST
As it has fewer controls to implement, and since there’s no control over it (NIST doesn’t have a certification scheme), NIST is considered somewhat less mature; also, as it is backed by the US government and not an international committee, it is not considered much outside the US. But if you like plain instructions and don’t want to spend a fortune, at least in the beginning, it can be a good idea to use NIST. Finally, it is possible to get the best of both worlds by implementing both at the same time.
What’s NIST?
The National Institute of Standards and Technology (NIST) is a non-regulatory US government agency founded in 1901 that develops technology, standards, and metrics to drive innovation in the US science and technology sectors. NIST is headquartered in Gaithersburg, Maryland.
NIST publishes the Special Publication 800 series, which contains guidance documents and recommendations. As part of the previous series, they released Special Publication 800-53, which catalogs 20 security and privacy control groups. NIST recommends that entities implement these security and privacy controls as part of their risk management strategies. These controls cover access control, security awareness training, incident response plans, risk assessments, and continuous monitoring.
The NIST compliance framework was developed to provide a customizable guide for entities on how to manage and reduce cybersecurity-related risks. In its guide, NIST combines existing standards, guidelines, and best practices. However, it is critical to understand that simply adhering to NIST guidelines will not make your entity 100% secure, which is why the NIST guidelines begin by instructing entities to use a value-based approach to protect their assets.
The NIST Cybersecurity Framework (CSF) is a voluntary (recommended by the Department of Commerce) cybersecurity framework that allows businesses to develop information security, risk management, and control programs. NIST standards are now used in fields ranging from nanotechnology to cybersecurity. Through an executive order in 2013, NIST was tasked with developing a cybersecurity framework, and in February 2014, it published version 1.0 of the Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1 was released to the public in April 2018.
The CSF is one of NIST’s voluntary programs that is based on existing standards and guidelines and is designed to assist entities in better managing and reducing cybersecurity risk. The CSF is presented in a 48-page document that details various cybersecurity activities and desired outcomes that entities can use to assess their cybersecurity risk, risk maturity, and information security infrastructure.
What is the purpose of the NIST CSF?
The CSF has three major components, the framework core, implementation tiers, and profiles, all of which are designed to help you benchmark your entity’s risk maturity and prioritize actions to improve it.
At its core, it has five functions: identify, protect, detect, respond, and recover.
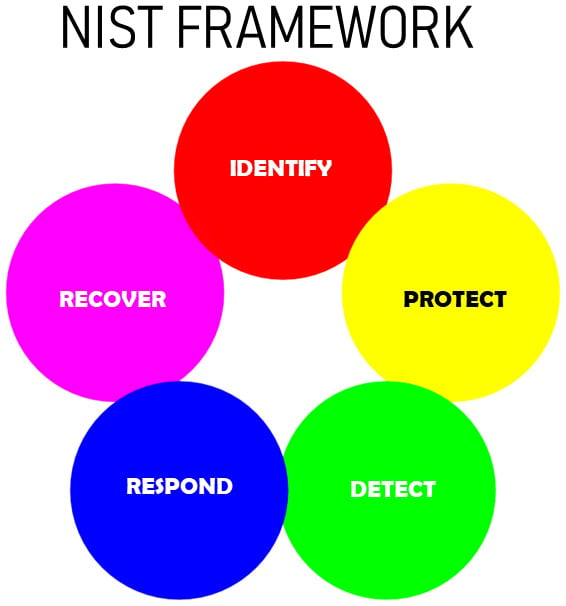
Figure 1.2 – The five functions, NIST
While the CSF focuses on cybersecurity issues, these activities are common in most risk management systems. The functions are further subdivided into 23 categories that cover the fundamentals of putting together a cybersecurity program.
The CSF has implementation tiers. For each of these five functions, the NIST CSF employs a ranking system on a scale of 0-4 to generate a final number that can be used to benchmark an entity’s level of risk maturity.
A profile, which is based on a tier, allows an entity to pinpoint its current level of risk tolerance and prioritize security controls and risk mitigation tactics. This section is intended to assist an entity in growing by comparing its current profile to target profiles, thereby assisting you in determining how to allocate budget and employee resources to improve cybersecurity practices over time.
What are the parallels between ISO and NIST?
When comparing NIST CSF and ISO 27001, both provide strong frameworks for cybersecurity risk management. It would be simple to integrate ISO 27001 standards and NIST CSF into a company that wants to become ISO 27001 compliant. Their control measures are comparable, and their definitions and code are fairly interchangeable across frameworks. Both frameworks provide simple vocabulary, which enables clear communication about cybersecurity issues across multidisciplinary teams and with external stakeholders.
What’s the distinction between ISO and NIST?
There are a few key differences between NIST CSF and ISO 27001, including risk maturity, certification, and cost.
Risk maturity
ISO 27001 is a good choice for operationally mature entities seeking certification, whereas the NIST CSF may be best for entities in the early stages of developing a cybersecurity risk management plan or attempting to mitigate previous failures or data breaches.
ISO 27001 certification provides globally recognized certification through third-party auditing, which can be costly but can improve your entity’s reputation as a business that stakeholders can rely on. The NIST CSF does not provide such certification.
Cost
The NIST CSF is free to use, whereas ISO 27001 requires a fee to access the documentation—another reason why a start-up might want to start with the NIST CSF and then make a larger investment in the process as it scales with ISO 27001.
NIST versus ISO – which is better for my company?
Finally, what is best for your company is determined by its maturity, goals, and specific risk management requirements. ISO 27001 is an excellent choice for operationally mature entities that are under external certification pressure. However, you may not be ready to embark on an ISO 27001 certification journey just yet, or your entity may be at a stage where it would benefit from the NIST CSF’s clear assessment framework. A NIST audit can provide you with an idea of where your entity stands before developing and implementing more stringent cybersecurity measures and controls.
As your entity matures, the two frameworks can be integrated—following the NIST CSF can be a useful precursor to your ISO 27001 certification journey. The NIST CSF provides a framework for growing entities to structure their Information Security (IS) risk assessments. If you already have these structures in place, you may want to pursue ISO security and compliance certifications. A proactive and efficient ISMS benefits from the right software, whether you’re starting with NIST CSF or growing with ISO 27001.
Summary
In this chapter, we spent some (hopefully useful) time understanding the basics of cybersecurity. We had a walk-through of ISO 27001 and 27002, then we discussed the definition of the CIA triad, alongside the definition of confidentiality, integrity, and availability, using some examples to better understand these concepts. Then, we had a look at information security concepts and definitions. We had a glance at governance, policies, and incident management. Then, we moved on to the NIST CSF and how ISO 27001 and NIST can be used at once.
In the next chapter, we will talk about ISMS, commitment, project management, context, scope policy, and objectives. We will look at how to identify, protect, detect, respond, and recover and ponder the question can ISO27001nd NIST coexist?




















 Download code from GitHub
Download code from GitHub
