Introduction to Wireshark Version 2
In this chapter, you will learn about:
- Wireshark version 2 basics
- Locating Wireshark
- Capturing data on virtual machines and on the cloud
- Starting the capture of data
- Configuring the start window
- Saving, printing, and exporting data
Wireshark Version 2 basics
In this chapter, we will cover the basic tasks related to Wireshark. In the Preface of this book, we talked a little bit about network troubleshooting, and we saw various tools that can help us in the process. After we reached the conclusion that we need to use the Wireshark protocol analyzer, it's time to locate it for testing in the network, configure it with basic configurations, and adapt it to be friendly.
While setting Wireshark for basic data capture is considered to be very simple and intuitive, there are many options that we can use in special cases; for example, when we capture data continuously over a connection and we want to split the capture file into small files, when we want to see names of devices participating in the connection and not only IP addresses, and so on. In this chapter, we will learn how to configure Wireshark for these special cases.
After this short introduction to Wireshark version 2, we present in this chapter several recipes to describe how to locate and start to work with the software.
The first recipe in this chapter is Locating Wireshark; it describes how and where to locate Wireshark for capturing data. Will it be on a server? On a switch port? Before a firewall? After it? On which side of the router should we connect it, the LAN side or on the WAN side? What should we expect to receive in each one of them? The first recipe describes this issue, along with recommendations on how to do it.
The next recipe is about an issue that has become very important in the last few years, and that is the recipe Capturing data on virtual machines that describes practical aspects of how to install and configure Wireshark in order to monitor virtual machines that have been used by the majority of servers in the last several years.
Another issue that has come up in recent years is how to monitor virtual machines that are stored in the cloud. In the Capture data on the cloud recipe, we have several issues to discuss, among them how to decrypt the data that in most of the cases is encrypted between you and the cloud, how to use analysis tools available on the cloud and also which tools are available from major cloud vendors like Amazon AWS, Microsoft Azure, and others.
The next recipe in this chapter is Starting the Capture of data, which is actually how to start working with the software, and configuring, printing and exporting data. We talk about file manipulations, that is, how to save the captured data whether we want to save the whole of it, part of it, or only filtered data. We export that data into various formats, merge files (for example, when you want to merge captured files on two different router interfaces), and so on.
Locating Wireshark
The first step after understanding the problem and deciding to use Wireshark is the decision on where to locate it. For this purpose, we need to have a precise network illustration (at least the part of the network that is relevant to our test) and locate Wireshark.
The principle is basically to locate the device that you want to monitor, connect your laptop to the same switch that it is connected to, and configure a port mirror or in Cisco it is called a port monitor or Switched Port Analyzer (SPAN to the monitored device. This operation enables you to see all traffic coming in and out of the monitored device. This is the simplest case.
You can monitor a LAN port, WAN port, server or router port, or any other device connected to the network.
In the example presented in this diagram, the Wireshark software is installed on the laptop on the left and a server S2 that we want to monitor:
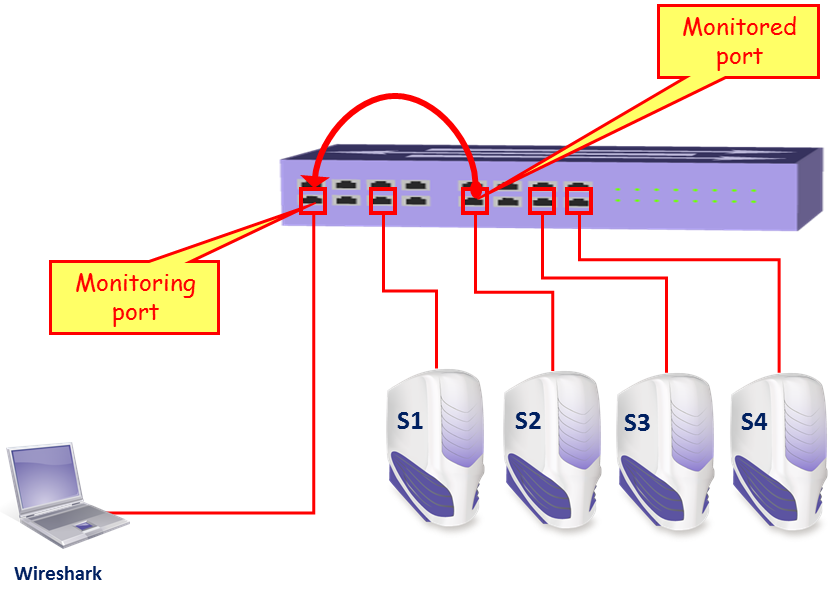
In the simplest case, we configure the port mirror in the direction as in the diagram; that will monitor all traffic coming in and out of server S2. Of course, we can also install Wireshark directly on the server itself, and by doing so we will be able to watch the traffic directly on the server.
Some LAN switch vendors also enable other features, such as:
- Monitoring a whole VLAN: We can monitor a server's VLAN, telephony VLAN, and so on. In this case, you will see all traffic on a specific VLAN.
- Monitoring several ports to a single analyzer: We can monitor traffic on servers S1 and S2 together.
- Filtering: Filtering consists of configuring whether to monitor incoming traffic, outgoing traffic, or both.
Getting ready
To start working with Wireshark, go to the Wireshark website and download the latest version of the tool.
An updated version of Wireshark can be found on the website http://www.wireshark.org/; choose Download. This brings you the Download Wireshark page. Download the latest Wireshark Version 2.X.X stable release that is available at https://www.wireshark.org/#download.
Each Wireshark Windows package comes with the latest stable release of WinPcap, which is required for live packet capture. The WinPcap driver is a Windows version of the UNIX libpcap library for traffic capture.
During the installation, you will get the package's installation window, presented in the following screenshot:

Usually in these setup windows, we simply check all and install. In this case, we have some interesting things:
- Wireshark: This is the Wireshark version 2 software.
- TSark: A command-line protocol analyzer.
- Wireshark 1: The good old Wireshark version 1. When you check this, the legacy Wireshark version 1 will be also installed. Personally, I prefer to install it for the next several versions, so if something doesn't work with Wireshark version 2 or you don't know how to work with it, you always have the good old version available.
- Plugins & Extensions:
- Dissector Plugins: Plugins with some extended dissections
- Tree Statistics Plugins: Extended statistics
- Mate: Meta-Analysis and Tracing Engine: User-configurable extension(s) of the display filter engine
- SNMP MIBs: For a more detailed SNMP dissection
- Tools:
- Editcap: Reads a capture file and writes some or all of the packets into another capture file
- Text2Pcap: Reads in an ASCII hex dump and writes the data into a pcap capture file
- Reordercap: Reords a capture file by timestamp
- Mergecap: Combines multiple saved capture files into a single output file
- Capinfos: Provides information on capture files
- Rawshark: Raw packet filter
How to do it...
Let's take a look at the typical network architecture, the network devices, how they work, how to configure them when required, and where to locate Wireshark:

Let's have a look at the simple and common network architecture in the preceding diagram.
Monitoring a server
This is one of the most common requirements that we have. It can be done by configuring the port monitor to the server (numbered 1 in the preceding diagram) or installing Wireshark on the server itself.
Monitoring a router
In order to monitor a router, we can use the following:
Case 1: Monitoring the switch port that the router is connected to:
- In this case, numbered 2 in the previous drawing, we connect our laptop to the switch that the router is connected to
- On the switch, configure the port mirror from the port that the router is connected to, to the port that the laptop is connected to
Case 2: Router with a switch module
- In this case, numbered 5 and 6 in the previous diagram, we have a switch module on the router (for example, Cisco EtherSwitch® or HWIC modules), we can use it the same way as a standard switch (numbered 5 for the LAN port and 6 for the WAN port, in the previous diagram)
- In this case, you will be able to monitor only those ports that are connected to the switch module
Case 3: Router without switch module
- In this case you can connect a switch between the router port and the Service Provider (SP) network, and configure the port monitor on this switch, as in the following diagram:

- In this case, configure the port monitor from the port the router is connected to, to the port your laptop is connected to.
Case 4: Router with embedded packet capture
In routers from recent years, you will have also an option for integrated packet capture in the router itself. This is the case, for example, in Cisco IOS Release 12.4(20)T or later, Cisco IOS-XE Release 15.2(4)S-3.7.0 or later, and also from SRX/J-Series routers from Juniper, Stealhead from Riverbed, and many other brands.
When monitoring a router, don't forget this: it might happen that not all packets coming in to a router will be forwarded out! Some packets can be lost, dropped on the router buffers, or routed back on the same port that they came in from, and there are, of course, broadcasts that are not forwarded by the router.
Monitoring a firewall
When monitoring a firewall, it is, of course, different whether you monitor the internal port (numbered 1 in the following diagram) or the external port (numbered 2 in the following diagram):

On the internal port, you will see all the internal addresses and all traffic initiated by the users working in the internal network, while on the external port, you will see the external addresses that we go out with (translated by NAT from the internal addresses), and you will not see requests from the internal network that were blocked by the firewall. If someone is attacking the firewall from the internet, you will see it (hopefully) only on the external port.
Test access points and hubs
Two additional devices that you can use are TAPs and Hubs:
-
Test Access Point (TAPs): Instead of connecting a switch to the link you wish to monitor, you can connect a device called a TAP, a simple three-port device that, in this case, will play the same role as the switch. The advantage of a TAP over a switch is the simplicity and price. TAPs also forward errors that can be monitored on Wireshark, unlike a LAN switch that drops them. Switches, on the other hand, are much more expensive, take a few minutes to configure, but provide you with additional monitoring capabilities, for example, SNMP. When you troubleshoot a network, it is better to have an available managed LAN switch, even a simple one, for this purpose.
-
Hubs: You can simply connect a hub in parallel to the link you want to monitor, and since a hub is a half-duplex device, every packet sent between the router and the SP device will be watched on your Wireshark. The biggest con of this method is that the hub itself slows the traffic, and therefore it influences the test. In many cases, you also want to monitor 1 Gbps ports, and since there is no hub available for this, you will have to reduce the speed to 100 Mbps that again will influence the traffic. Therefore, hubs are not commonly used for this purpose.
How it works...
For understanding how the port monitor works, it is first important to understand the way that a LAN switch works. A LAN switch forwards packets in the following way:
- The LAN switch continuously learns the MAC addresses of the devices connected to it
- Now, if a packet is sent to a destination MAC, it will be forwarded only to the physical port that the switch has learned that this MAC address is coming from
- If a broadcast is sent, it will be forwarded to all ports of the switch
- If a multicast is sent, and CGMP or IGMP is disabled, it will be forwarded to all ports of the switch (CGMP and IGMP are protocols that enable multicast packets to be forwarded only to devices on a specific multicast group)
- If a packet is sent to a MAC address that the switch has not learned (which is a very rare case), it will be forwarded to all ports of the switch
In the following diagram, you see an example for how a layer 2-based network operates. Every device connected to the network sends periodic broadcasts. It can be ARP requests, NetBIOS advertisements, and others. The moment a broadcast is sent, it is forwarded through the entire layer 2 network (dashed arrows in the drawing). In the example, all switches learn the MAC address M1 on the port they have received it from.

Now, when PC2 wants to send a frame to PC1, it sends the frame to the switch that it is connected to, SW5. SW5 has learned the MAC address M1 on the fifth port to the left, and that is where the frame is forwarded. In the same way, every switch forwards the frame to the port it has learned it from, and finally it is forwarded to PC1.
Therefore, when you configure a port monitor to a specific port, you will see all traffic coming in and out of it. If you connect your laptop to the network, without configuring anything, you will see only traffic coming in and out of your laptop, along with broadcasts and multicasts from the network.
There's more...
There are some tricky scenarios when capturing data that you should be aware of.
Monitoring a VLAN—when monitoring a VLAN, you should be aware of several important issues. The first issue is that even when you monitor a VLAN, the packet must physically be transferred through the switch you are connected to in order to see it. If, for example, you monitor VLAN-10 that is configured across the network, and you are connected to your floor switch, you will not see traffic that goes from other switches to the servers on the central switch. This is because in building networks, the users are usually connected to floor switches, in single or multiple locations in the floor, that are connected to the building central switch (or two redundant switches). For monitoring all traffic on a VLAN, you have to connect to a switch on which all traffic of the VLAN goes through, and this is usually the central switch:

In the preceding diagram, if you connect Wireshark to Switch SW2, and configure a monitor to VLAN30, you will see all packets coming in and out of P2, P4, and P5, inside or outside the switch. You will not see packets transferred between devices on SW3, SW1, or packets between SW1 and SW3.
Another issue when monitoring a VLAN is that you might see duplicate packets. This is because when you monitor a VLAN and packets are going in and out of the VLAN, you will see the same packet when it is coming in and going out of the VLAN.
You can see the reason in the following illustration. When, for example, S4 sends a packet to S2 and you configure the port mirror to VLAN30, you will see the packet once sent from S4 to the switch and entering the VLAN30, and then when leaving VLAN30 to S2:

See also
For information on how to configure the port mirror, refer to the vendor's instructions. It can be called port monitor, port mirror, or SPAN from Cisco.
There are also advanced features such as remote monitoring, when you monitor a port that is not directly connected to your switch, advanced filtering (such as filtering specific MAC addresses), and so on. There are also advanced switches that have capture and analysis capabilities on the switch itself. It is also possible to monitor virtual ports (for example, a LAG or EtherChannel groups). For all cases, and other cases described in this recipe, refer to the vendor's specifications.
For vendor information you can look, for example, at these links:
- Cisco IOS SPAN (for catalyst switches): http://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/10570-41.html
- Cisco IOS Embedded Packet Capture feature: http://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/ios-embedded-packet-capture/datasheet_c78-502727.html
- Check point Packet Sniffer feature: https://www.checkpoint.com/smb/help/utm1/8.2/2002.htm
- Fortinet FortiOS packet sniffer: http://kb.fortinet.com/kb/viewContent.do?externalId=11186
Capturing data on virtual machines
Getting ready
In the last few years, a significant amount of servers are moving to virtual environments—that is a large amount of servers on a single hardware device.
First, to put some order in the terms. There are two major terms to remember in the virtual world:
- A virtual machine is an emulation of a computer system that is installed on single or multiple hardware platforms. A virtual machine is mostly used in the context of virtual servers. The major platforms used for server virtualization are VMware ESX, Microsoft Hyper-V, or Citrix XenServer.
- A Blade server is a cage that holds inside server cards and LAN switches to connect them to the world.
In this section, we will look at each one of these components and see how to monitor each one of them.
How to do it...
Let's see how to do it.
Packet capture on a VM installed on a single hardware
A single hardware with virtual machines is illustrated in the following diagram:
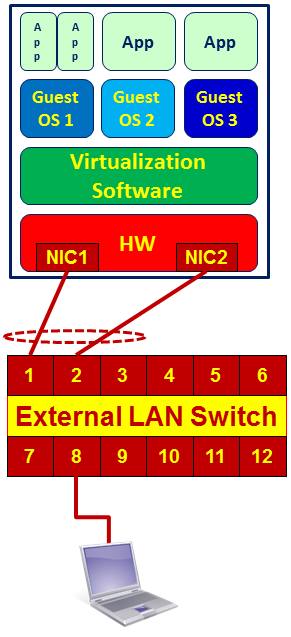
As you see in the preceding diagram, we have the applications that run on the operating systems (guest OS in the drawing). Several guest OSs are running on the virtualization software that runs on the hardware platform.
As mentioned earlier in this chapter, in order to capture packets we have two possibilities: to install Wireshark on the device that we want to monitor, or to configure port mirror to the LAN switch to which the Network Interface Card (NIC) is connected.
For this reason, in the case of a virtual platform on a single hardware, we have the following possibilities:
- Install Wireshark on the specific server that you want to monitor, and start capturing packets on the server itself.
- Connect your laptop to the switch 8, and configure a port mirror to the server. In the preceding diagram, it would be to connect a laptop to a free port on the switch, with a port mirror to ports 1 and 2. The problem that can happen here is that you monitor.
The first case is obvious, but some problems can happen in the second one:
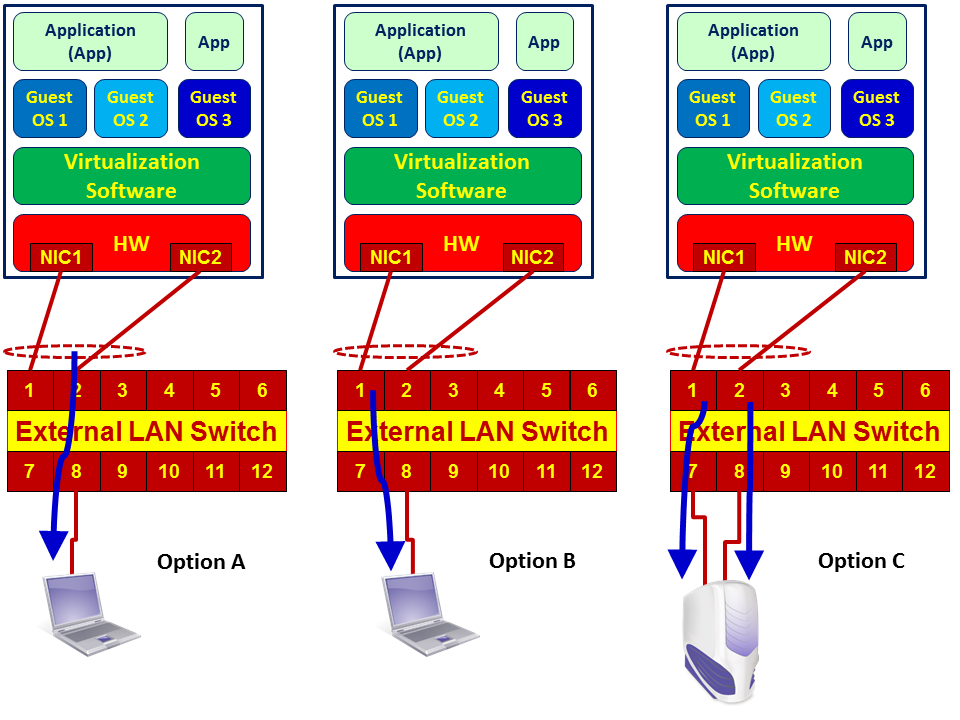
- As illustrated in the preceding diagram, there are usually two ports or more that are connected between the server and the LAN switch. This topology is called Link Aggregation (LAG), teaming, or if you are using Cisco switches, EtherChannel. When monitoring a server, check whether it is configured with load sharing or port redundancy (also referred to as Failover). If it is configured with port redundancy, it is simple: check what the active port is and configure the port mirror to it. If it is configured with load sharing, you have to configure one of the following:
- Port mirror to LAG interface: that is, port mirror to the virtual interface that holds the two or more physical interfaces. Usually, it is termed by the switch vendor as Port-Group or Port-Channel interface.
-
- The server NICs are configured in the port redundancy: the port mirror from one port to two physical ports (in the diagram to ports 1 and 2 of the switch).
- Configure two port mirrors from two interface cards on your PC to the two interfaces on the LAN switch at the same time. A diagram of the three cases is presented here:
-
- There is another problem that might happen. When monitoring heavy traffic on ports configured with load sharing, in Option A you will have a mirror of two NICs sending data to a single one, for example, two ports of 1 Gbps to a single port of 1 Gbps. Then of course, in case of traffic that exceeds the speed of the laptop, not all packets will be captured and some of them will be lost. For this reason, when you use this method, make sure that the laptop has a faster NIC than the monitored ports or use Option C (capture with two interfaces).
Packet capture on a blade server
In the case of using a BLADE Center, we have the following hardware topology:
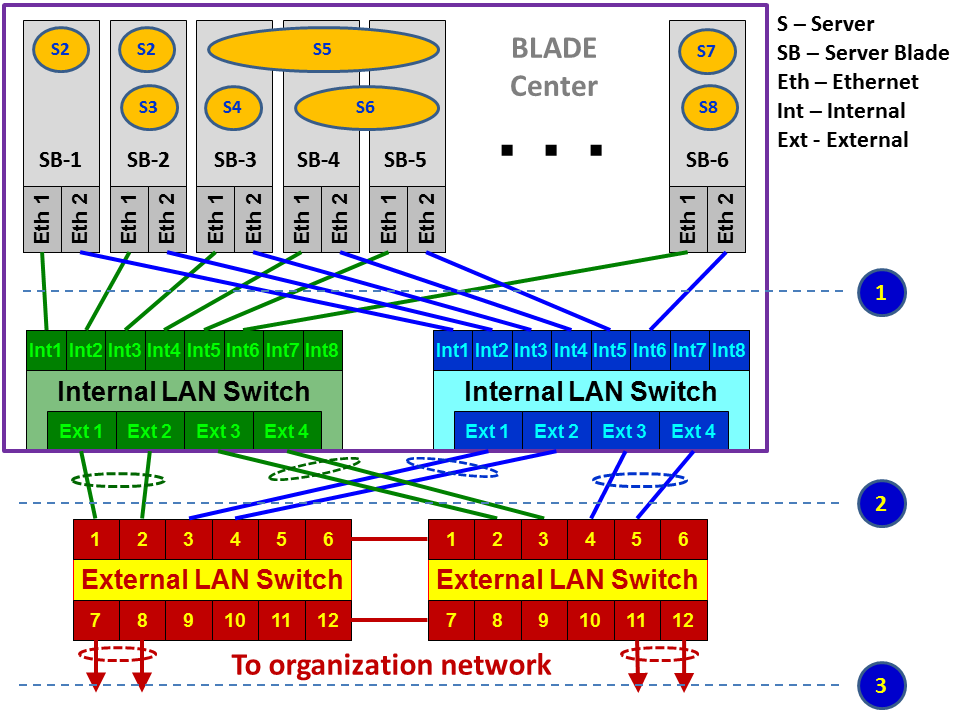
As illustrated, we have a BLADE Center that contains the following components:
- Blade servers: These are hardware cards, usually located at the front side of the blade.
- Servers: The virtual servers installed on the hardware servers, also called VMs.
- Internal LAN switch: Internal LAN switches that are installed at the front or back of the blade center. These switches usually have 12-16 internal or virtual ports (Int in the diagram) and 4-8 external or physical ports (Ext in the diagram).
- External switch: Installed in the communication rack, and it's not a part of the BLADE Center.
Monitoring a blade center is more difficult because we don't have direct access to all of the traffic that goes through it. There are several options for doing so:
- Internal monitoring on the blade center:
- For traffic on a specific server, install Wireshark on the virtual server. In this case you just have to make sure from which virtual ports traffic is sent and received. You will see this in the VM configuration, and also choose one interface a the time on the Wireshark and see to which one the traffic goes.
- A second option is to install Wireshark on a different VM and configure the port mirror in the blade center switch, between the server you wish to monitor and the VM with the Wireshark installed on it.
- From servers to blade center switch (1) in the previous diagram:
- For traffic that goes from the servers to the switch, configure, port mirror from the virtual ports the server is connected to, to the physical port where you connect the laptop. Most vendors support this option, and it can be configured.
- For external monitoring, traffic from the internal blade center switch to the external switches:
- Use a standard port mirror on the internal or external switches
How it works...
As described before, there are several types of virtual platforms. I will explain the way one operates on VMware, which is one of the popular ones.
On every virtual platform, you configure hosts that are provided with the CPU and memory resources that virtual machines use and give virtual machines access to these resources.
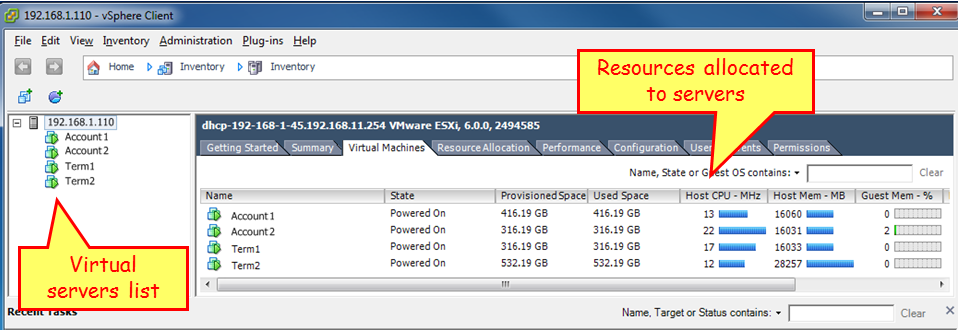
In the next screenshot, you see a virtualization server with address 192.168.1.110, configured with four virtual machines: Account1, Account2, Term1, and Term2. These are the virtual servers, in this case, two servers for accounting and two terminal servers:
When you go to the configuration menu and choose Networking, as illustrated in the next screenshot, you see the vSwitch. On the left, you see the internal ports connected to the servers, and on the right, you see the external port.
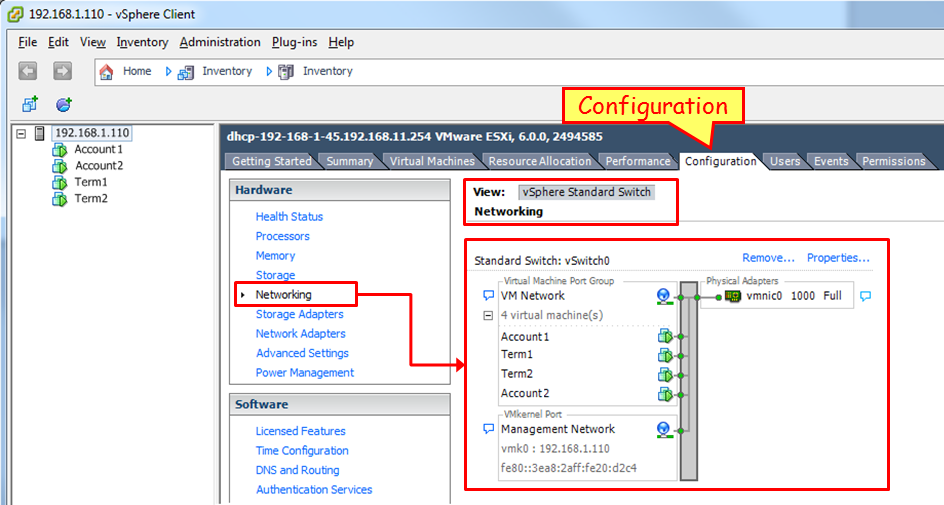
In this example, we see the virtual servers Account1, Account2, Term1 and Term2; on the right, we see the physical port vmnic0.
Standard and distributed vSwitch
The VMware platform vSphere offers two kinds of virtual switches, standard and distributed:
- The standard vSwitch is what every vSphere installation has, no matter what license it is running on
- Distributed vSwitches are only available for those who have an Enterprise Plus license
Port mirror is enabled in distributed vSwitch; how to configure it? You can find that out in the Working With Port Mirroring section on the VMware vSphere 6.0 documentation center: http://pubs.vmware.com/vsphere-60/index.jsp#com.vmware.vsphere.networking.doc/GUID-CFFD9157-FC17-440D-BDB4-E16FD447A1BA.html.
See also
For specific vendor's mirroring configuration:
- For Alteon (now Radware) blade switches: http://www.bladenetwork.net/userfiles/file/PDFs/IBM_GbE_L2-3_Applicat_Guide.pdf
- For Cisco blade switches (called SPAN): http://www.cisco.com/c/dam/en/us/td/docs/switches/blades/igesm/software/release/12-1_14_ay/configuration/guide/25K8411B.pdf, Page 340, SPAN and RSPAN Concepts and Terminology
Starting the capture of data
After we have located Wireshark in the network, in this recipe, we will learn how to start capturing data and what we will get in various capture scenarios.
Getting ready
After you've installed Wireshark on your computer, the only thing to do will be to start the analyzer from the desktop, program files, or the quick start bar.
When you do so, the following window will be opened (version 2.0.2):

In the start window, you will see the following sections:
- The main menu, with file, edit and view operations, capture, statistics, and various tools.
- The main toolbar that provides quick access to frequently used items from the menu.
- The filter toolbar, it provides access to the display filters.
In the main area of the start window, we have the following items:
- A list of files that were recently opened
- A Capture part that enables us to configure a capture filter and shows us the traffic on our computer interfaces
- The Learn part can take us directly to the manual pages
How to do it...
In Wireshark Version 2, it is very simple. When you run the software, down the main window, you will see all the interfaces with the traffic that runs over them. See the following screenshot:
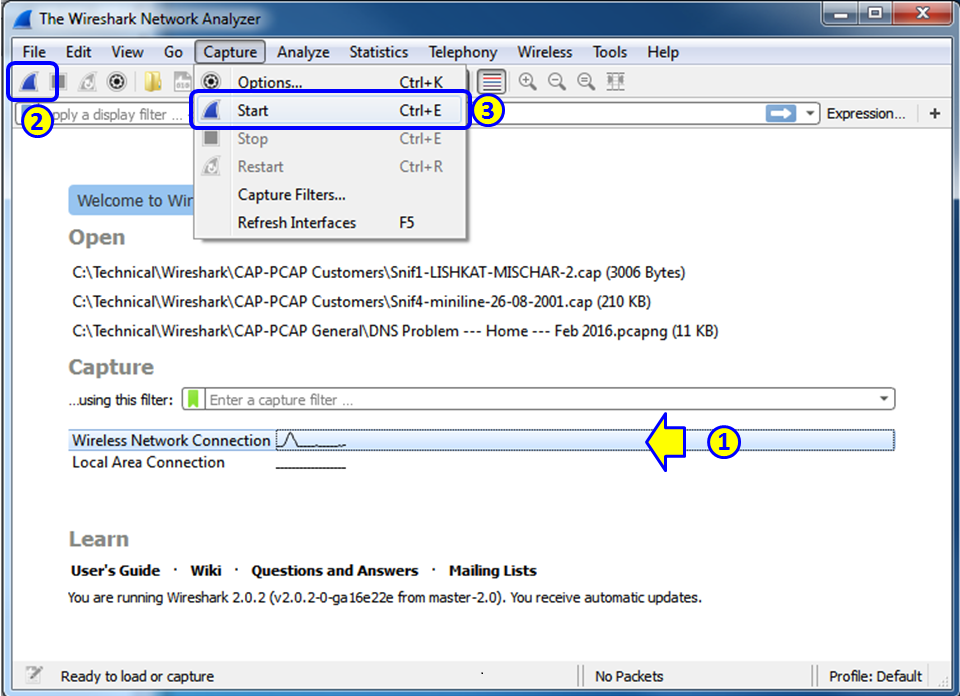
The simplest way to start a simple single-interface capture is simply to double-click on the active interface (1). You can also mark the active interface and click on the capture button on the upper-left corner of the window (2), or choose Start or Ctrl + E from the Capture menu (3).
Capture on multiple interfaces
In order to start the capture on multiple interfaces, you simply use Windows Ctrl or Shift keys, and left-click to choose the interfaces you want to capture data from. In the following screenshot, you see that the Wireless Network Connection and the Local Area Connection are picked up:
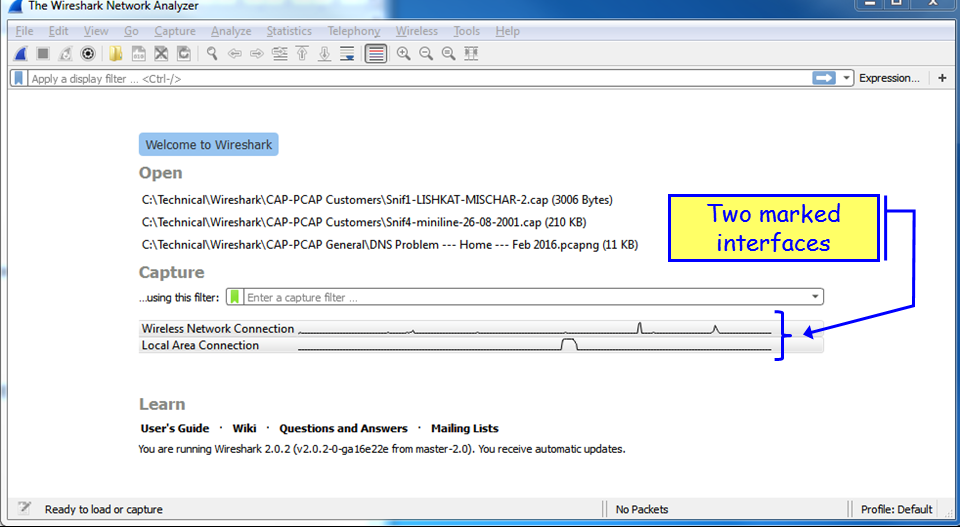
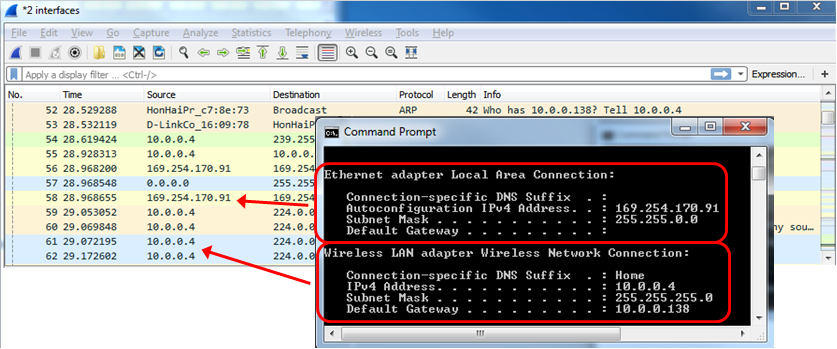
And the traffic that you will get will be from the two interfaces, as you can see from the next screenshot: 10.0.0.4 on the wireless interface, and 169.254.170.91 Automatic Private IP Address (APIPA) on the LAN interface.
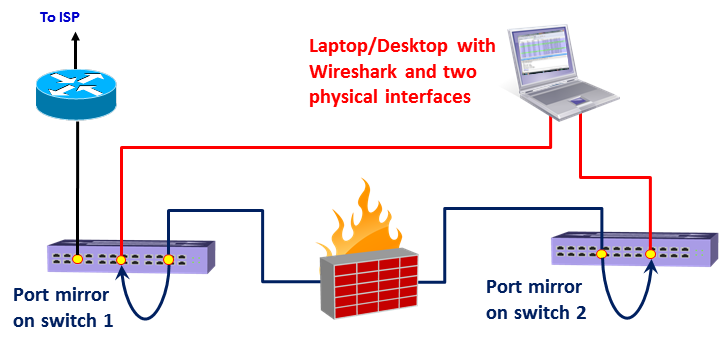
Using capture on multiple interfaces can be helpful in many cases, for example, when you have multiple physical NICs, you can port monitor two different servers, two ports of a router or any other multiple ports at the same time. A typical configuration is seen in the following screenshot:
How to configure the interface you capture data from
- To configure the interface you capture data from, choose Options from the Capture menu. The following window will appear:
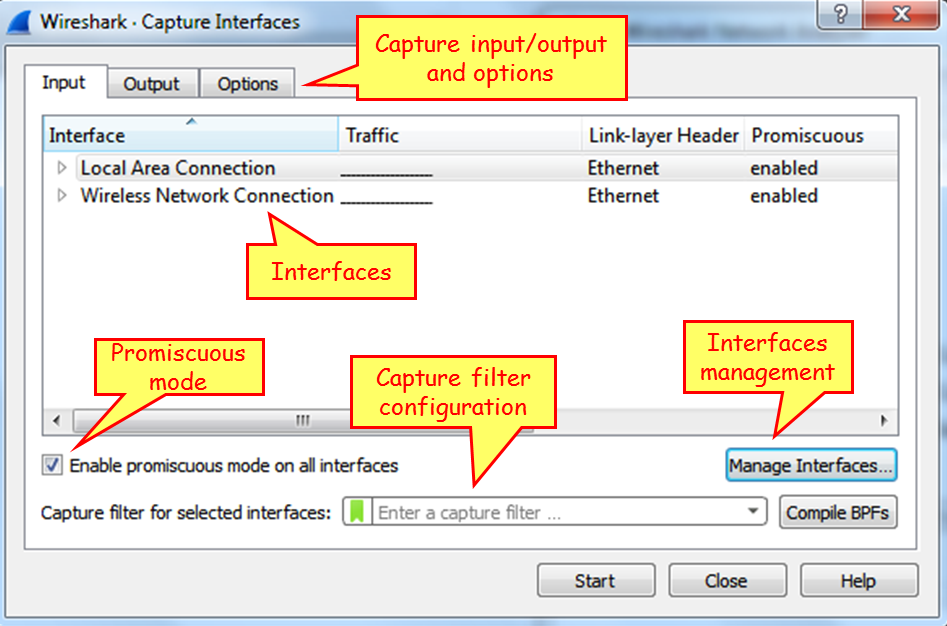
In this window you can configure the following parameters:
- On the upper side of the window, on the main window, choose the interface on which you want to capture the data from. If no additional configuration is required, click on Start to start the capture.
- On the lower-left side, you have the checkbox Use promiscuous mode on all interfaces. When checked, Wireshark will capture all the packets that the computer receives. Unchecking it will capture only packets intended for the computer.
- In the middle of the screen, right below the interfaces window, you can configure the capture filter. We will learn capture filters in Chapter 3, Using Capture Filters.
On top of the window, we have three tabs: Input (opens by default), Output, and Options.
Capture data to multiple files
Click on the Output tab, and the following window will open:
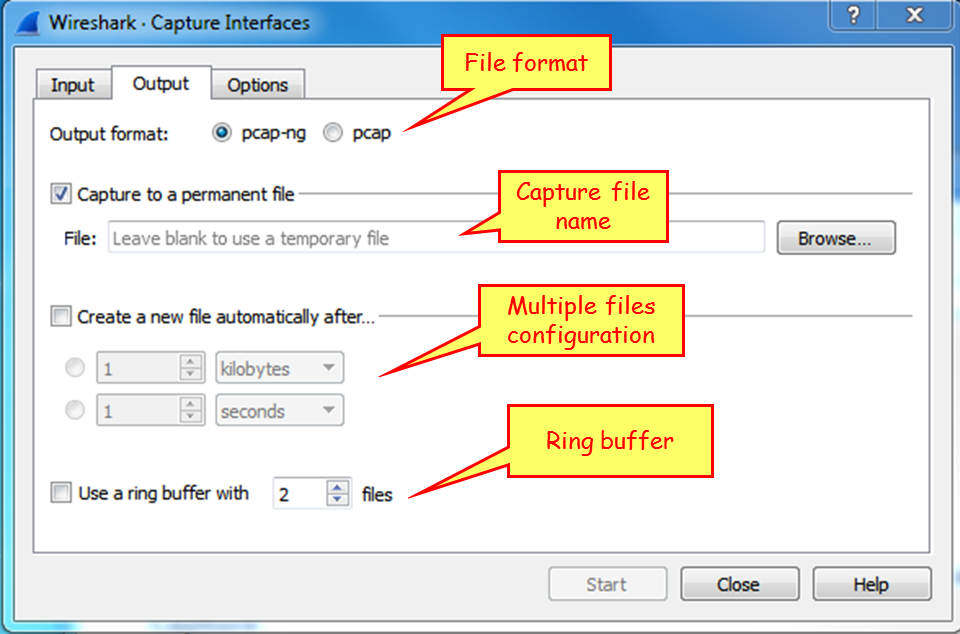
This window enables capture in multiple files. To configure this, write a filename in the Capture to a permanent file area. Wireshark will save the captured file under this name, with extensions 0001, 0002, and so on, all under the path that you specify in the Browse... button. This feature is extremely important when capturing a large amount of data, for example, when capturing data over a heavily loaded interface, or over a long period of time. You can tell the software to open a new file after a specific amount of time, file size, or number of packets.
Configure output parameters
- When you choose the Options tab, the following window will open.

- On the left (1), you can choose Display Options. These options are:
- Update list of packets in real-time: Upon checking this option, Wireshark updates packets in the packet pane in real time
- Automatic scroll during live capture: Upon checking this, Wireshark scrolls down packets in the packet pane as new packets come in
- Hide capture info dialog: By checking this, the capture info dialog is hidden
- On the right, there is the Name Resolution option. Here we can check for:
- The MAC address resolution that resolves the first part of the MAC address to the vendor ID.
- The IP address resolution that is resolved to DNS names.
- TCP/UDP port numbers that are resolved to application names. These are the port numbers; for example, TCP port 80 will be presented as HTTP, port 25 as SMTP, and so on.
Manage interfaces (under the Input tab)
- As you see in the following screenshot, on the bottom-right, you have the Manage Interfaces... button with three tabs; Local Interfaces, Pipes and Remote Interfaces. These are the options that Wireshark can capture data from:

- When you choose the Manage Interfaces... button and the Input tab, you will see a list of available local interfaces, including the hidden ones, which are not shown in the other list:

- Wireshark can also read captured packets from another application in real time.
Capture packets on a remote machine
For capturing data from a remote machine, perform the following actions:
- Install the pcap driver on the remote machine. You can find it at http://www.winpcap.org/ or install the entire Wireshark package instead.
- For capturing data on the remote machine, choose Options | Capture Interfaces |Manage Interfaces|Remote Interface. The following window will open:

- On the local machine:
- Host name: The IP address or host name of the remote machine
- Port: 2002: You can leave it open and it uses the default 2002
- Password authentication: The username and password of the remote machine.
- On the remote machine:
- Install WinPcap on the remote PCs that you want to collect data from. You can get it from http://www.winpcap.org/. You don't need to install Wireshark itself, only WinPcap.
- Configure the firewall is open to TCP port 2002 from your machine.
- On the remote PC, add a user to the PC user list, give it a password, and administrator privileges. You configure this from Control Panel | Users Accounts and Family Safety|Add or remove user accounts | create a new account.
- Right-click on the Start symbol down to the left of the Windows screen, choose Open Windows Explorer, right-click on Computer, and choose Manage. In the Manage window, open the services, as illustrated here:
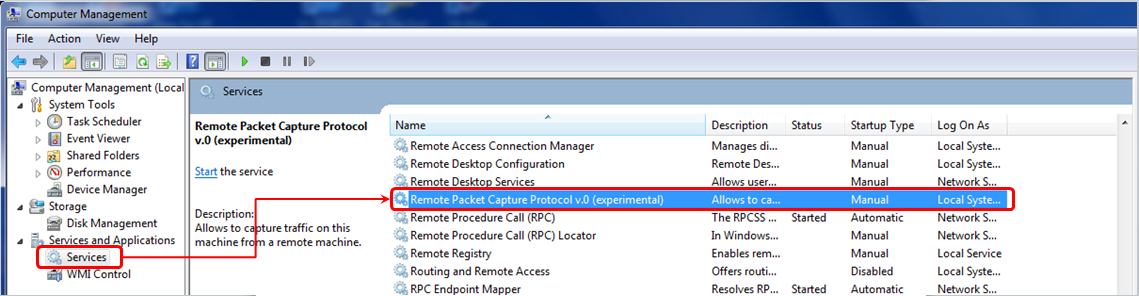
- You will see the interface you have configured on the remote interfaces, and when you click on OK, you will also see it on the local interfaces' list. Now you can capture packets on it as if it was a local interface on your machine.
This file is attached as Cap_B05518_01_01.
Start capturing data – capture data on Linux/Unix machines
In Linux and Unix devices, we have the good old TCPDUMP utility, actually the command that the Wireshark came from.
For using TCPDUMP, you have the following commands (the most common ones):
- Capture packets on a specific interface:
- Syntax is tcpdump -i <interface_name>
- Example is tcpdump -i eth0
- Capture and save packets in a file:
- Syntax is tcpdump -w <file_name> -i <interface_name>
- Example is tcpdump -w test001 -i eth1
- Read captured packets' file:
- Syntax is tcpdump -r <file_name>
- Example is tcpdump -r test001
To use capture filters, use the capture filters format described in Chapter 3, Using Capture Filters.
Collecting from a remote communication device
In this section, we will describe how to capture data from remote communication equipment. Since there are many vendors that support this functionality, we will provide the general guidelines for this feature for some major vendors, along with links to their website, to get the exact configurations.
The general idea here is that there are some vendors that allow you to collect captured data locally, and then to download the capture file to an external computer.
For Cisco devices, this feature is called Embedded Packet Capture (EPC), and you can find how to do it in the following link: http://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-embedded-packet-capture/116045-productconfig-epc-00.html. In this link you can find how to configure the capture for Cisco IOS and IOS-XE operating systems.
For Juniper devices, the command is called monitor traffic, and you can find a detailed description of it at http://www.juniper.net/techpubs/en_US/junos14.1/topics/reference/command-summary/monitor-traffic.html.
For check point firewalls, you can use the utility fw monitor, explained in detail at http://dl3.checkpoint.com/paid/a4/How_to_use_FW_Monitor.pdf?HashKey=1415034974_a3bca5785be6cf8b4d627cfbc56abc97&xtn=.pdf.
For additional information, check out the specific vendors. Although capturing data on the LAN switch, router, firewall, or other communication devices and then downloading the file for analysis is usually not the preferred option, keep it in mind and remember that it is there if you need it.
How it works...
Here the answer is very simple. When Wireshark is connected to a wired or wireless network, there is a software driver that is located between the physical or wireless interface and the capture engine. In Windows, we have the WinPcap driver; in Unix platforms, we have the Libpcap driver; and for wireless interfaces, we have the Airpcap driver.
There's more...
In cases where the capture time is important, and you wish to capture data on one interface or more, and you want to be time-synchronized with the server you are monitoring, you can use Network Time Protocol (NTP) for this purpose, and synchronize your Wireshark and the monitored servers with a central time source.
This is important in cases where you want to go through the Wireshark capture file in parallel to a server log file, and look for events that are shown on both. For example, if you see retransmissions in the capture file at the same time as a server or application error on the monitored server, then you will know that the retransmissions are because of server errors and not because of the network.
The Wireshark software takes its time from the OS clock (Windows, Linux, and so on). To configure the OS to work with a time server, go to the relevant manuals of the operating system that you work with.
In Microsoft Windows 7, configure it as follows:
- Go to Control Panel
- Choose Clock, Language, and Region
- Under Date and Time, Choose Set the time and date. Change to the Internet time tab
- Click on the Change Settings button
- Change the server name or IP address
NTP is a network protocol used for time synchronization. When you configure your network devices (routers, switches, fws, and so on) and servers to the same time source, they will be time synchronized to this source. The accuracy of the synchronization depends on the accuracy of the time server that is measured in levels or stratum. The higher the level is, it will be more accurate. Level 1 is the highest. The higher the level, the lower the accuracy. Usually you will have level 2 to 4.
NTP was first standardized in RFC 1059 (NTPv1) and then in RFC 1119 (NTPv2). The common versions in the last few years are NTPv3 (RFC1305) and NTPv4 (RFC 5905).
You can get a list of NTP servers on various websites, some of them are: http://support.ntp.org/bin/view/Servers/StratumOneTimeServers And http://wpollock.com/AUnix2/NTPstratum1PublicServers.htm
See also
You can get more information about the Pcap drivers from:
- For WinPcap visit: http://www.winpcap.org
- For Libpcap visit: http://www.tcpdump.org
Configuring the start window
In this recipe, we will see some basic configurations for the start window. We will talk about configuring the main window, file formats, and viewing options.
Getting ready
Start Wireshark, and you will get the start window. There are several parameters you can change here in order to adapt the capture window to your requirements:
- Toolbars configuration
- Main window configuration
- Time format configuration
- Name resolution
- Auto scroll in live capture
- Zoom
- Column configuration
First, let's have a look at the menu and the toolbars that are used by the software:
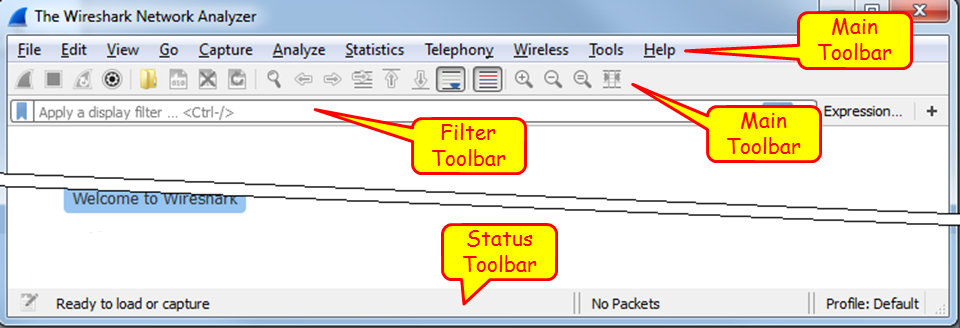
The main menu
Wireshark's main menu is located at the top of the main window. In the main toolbar you have the following symbols:
- File: File operations such as open and save file, export packets, print, and so on.
- Edit: To find packets, mark packets, add comments, and most importantly, use the preferences' submenu. This will be described in Chapter 2, Mastering Wireshark for Network Troubleshooting.
- View: For configuring Wireshark display, colorization of packets, zooming, font changes, showing a packet in a separate window, expanding and collapsing trees in packet details, and so on.
- : To go to a specific packet, for example, to the first packet in the capture, the last packet, a packet number, and so on.
- : To configure capture options and capture filters.
- : For analysis and display options like display filter configuration, decode options, to follow a specific stream, and so on.
- Statistics: To show statistics, starting from the basic hosts and conversations statistics up to the smart IO graphs and stream graphs.
- : For displaying IP telephony and cellular protocols information, for example, RTP and RTCP, SIP flows and statistics, GSM or LTE protocols, and so on.
- Wireless: For showing Bluetooth and IEEE 802.11 wireless statistics, later described in Chapter 9, Wireless LAN.
- Appendix 4 Lua programming.
- : For user assistance, sample capture updates, and so on.
The main toolbar
The main toolbar provides quick access to frequently used items from the menu. This toolbar can be hidden using the View menu.
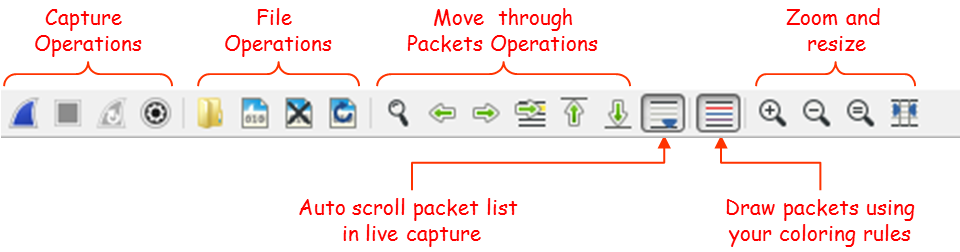
The four left-most symbols are for capture operations, then you have symbols for file operations, go to packet operations, auto-scroll, draw packets using coloring rules, zoom and resize.
Display filter toolbar
In the filters toolbar, you have the following symbols:
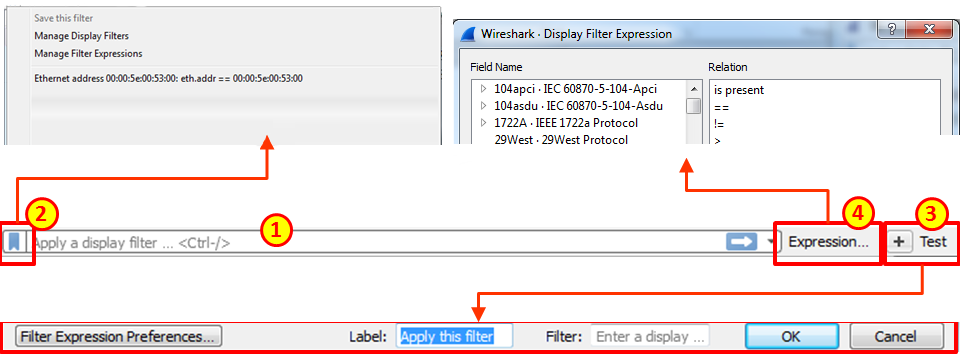
In the display filter toolbar we can:
- Type in a display filter string, with auto complete while showing us previously configured filters
- Manage filter expressions that allow you to bring up filter construction dialog for filter construction assistance
- Configure a new filter and add it to the preferences
- Use filter predefined expressions, and choose a filter
An enhanced description of splay filters is provided in Chapter 4, Using Display Filters.
Status bar
In the status bar, at the lower side of the Wireshark window, you can see the following data:
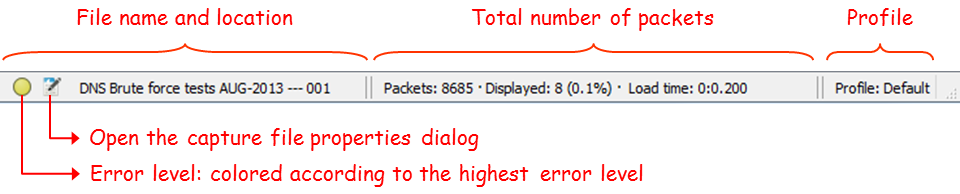
You can see here:
- Any errors in the expert system.
- The Capture file properties, including file information, capture time, time and general statistics.
- The name of the captured file (during capture, it will show you a temporary name assigned by the software).
- Total number of captured packets, displayed packets (those which are actually displayed on the screen), and load time, that is, the time it took to load the capture file.
- The profile you work with. For more information of profiles, you can read Chapter 2, Mastering Wireshark for Network Troubleshooting.
How to do it...
In this part, we will go step by step and configure the main menu.
Toolbars configuration
Usually for regular packet capture, you don't have to change anything. This is different when you want to capture wireless data over the network (not only from your laptop); you will have to enable the wireless toolbar, and this is done by clicking on it under the view menu, as shown in the following screenshot:
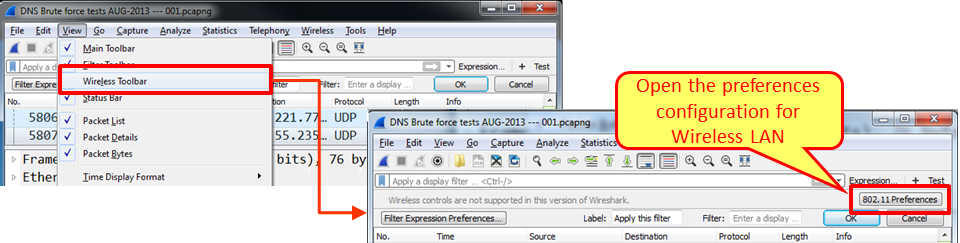
When marking the Wireless Toolbar option in the View menu, the wireless toolbar opens. The only option available in the current version is to start the preferences' configuration window. There is more about Wireless LAN analysis in Chapter 9, Wireless LAN.
Main window configuration
To configure the main menu for capturing, you can configure Wireshark to show the following windows:
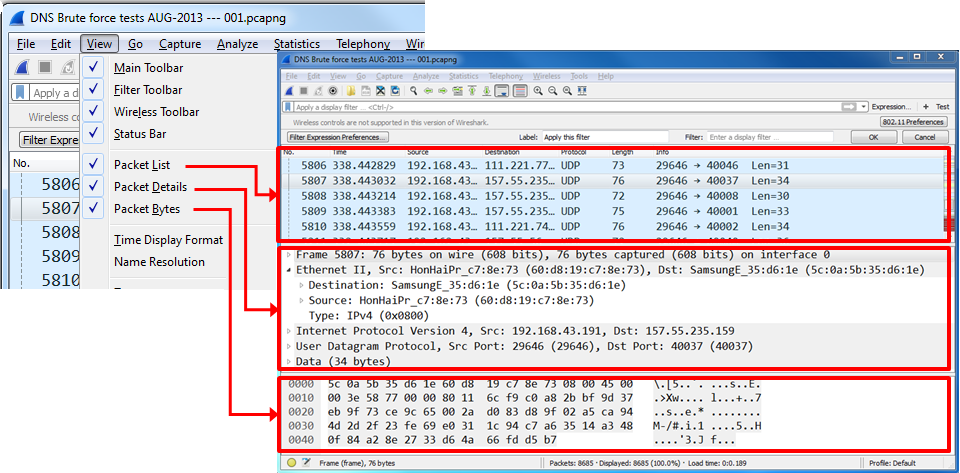
In most of the cases, you will not need to change anything. In some cases, when you don't need to see the packet bytes, you can cancel them, and you will get more space for the packet list and details.
Name resolution
Name Resolution is the translation of layer 2 (MAC addresses), layer 3 (IP addresses), and layer 4 (port numbers) into meaningful information.
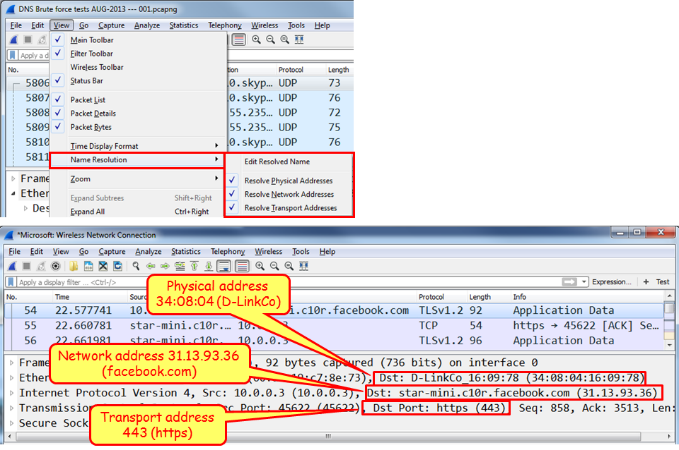
In the screenshot, we see that the MAC address 34:08:04:16:09:78 (from D-Link), the website (that is, www.facebook.com), and the HTTPs port number (that is 443).
Colorize packet list
Usually you start a capture in order to establish a baseline profile of what normal traffic looks like on your network. During the capture, you look at the captured data and you might find a TCP connection, IP, or Ethernet connectivity that are suspects, and you'll want to see them in another color.
To do so, right-click on the packet that belongs to the conversation you want to color, choose Ethernet, IP, or TCP/UDP (TCP or UDP will appear depending on the packet), and choose the color for the conversation.
In the example, you see that we want to color a TCP conversation.
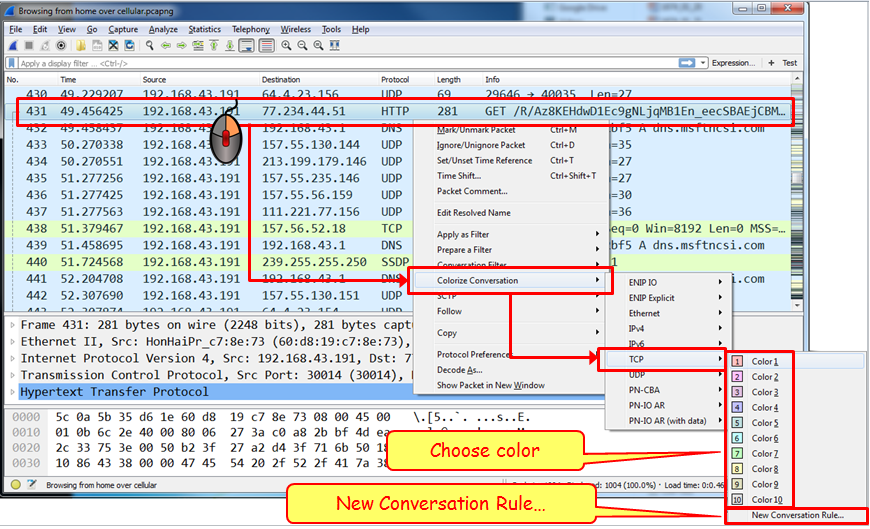
To cancel the coloring rule:
- Go to the View menu
- In the lower part of the menu, choose Colorize Conversation and then Reset Colorization or simply click on Ctrl + space bar
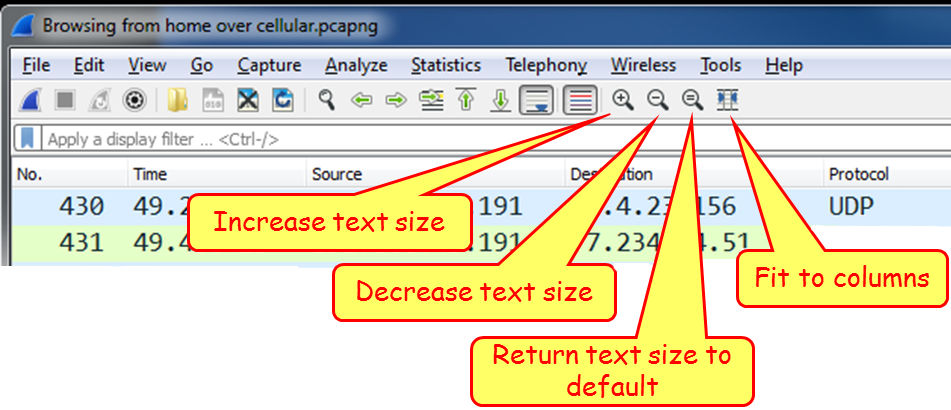
Zoom
As you see in the following screenshot, for zooming in and out:
- Go to the View menu
- Click on Zoom In on the main toolbar or press Ctrl++ to zoom in
- Click on Zoom Out on the main toolbar or press Ctrl +- to zoom out