Chapter 2. Networking for Packet Analysts
Packet analysis is all about analyzing how applications transfer useful data from point A to point B over networks. So, an understanding of how networks function is essential.
In this chapter, we will cover the following topics:
Why the seven-layer OSI model matters
IP networks and subnets
Switching and routing packets
Ethernet frames and switches
IP addresses and routers
WAN links
Wireless networking
The seven-layer OSI model will be mapped to the most common networking terms, and we'll review frames, switching, IP addressing, routing, and a few other networking topics of interest. The goal is to develop a mental model of networking that lends itself well to packet-level analysis.
The OSI model – why it matters
The Open Systems Interconnections (OSI) reference model is an industry recognized standard developed by the International Organization for Standardization (ISO) to divide networking functions into seven logical layers to support and encourage (relatively) independent development while providing (relatively) seamless interconnectivity between each layer from different hardware/software environments, platforms, and vendors. There's also a somewhat simpler four-layer
Defense Advanced Research Projects Agency (DARPA) model that maps to the OSI model, but the OSI version is the most commonly referred to. I'll reference both models when discussing the various layers.
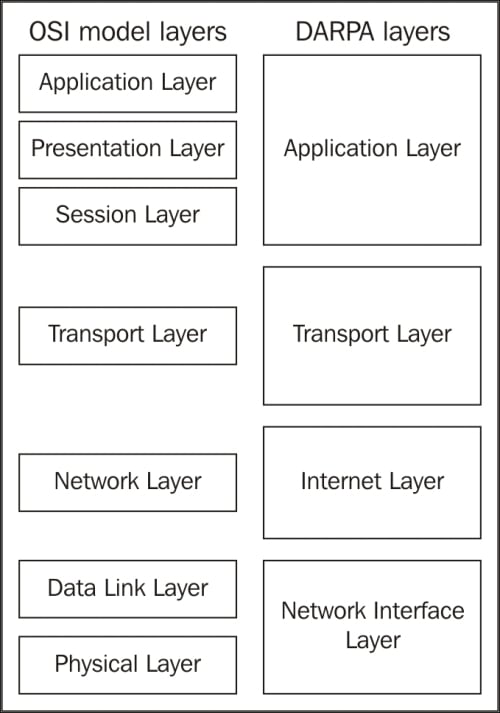
The following diagram compares the OSI and DARPA reference models:
Unless you're in the business of writing protocols, there's no need to study any of the seven layers in great depth, but it is helpful to understand them conceptually because these layers are referred to by the industry and your IT peers...
Before moving on, a short review of typical IP subnetting terms and typical applications should help clarify the terms used in this book and will act as a refresher for those already versed in IP addressing.
A /24 designator placed after a network IP address in diagrams or device configurations is a Classless Inter-Domain Routing (CIDR) designator that indicates the following:
The first 24 out of the 32 bits in the 4-byte IP address represents the network portion of any IP address on this network. This network is designated as 10.1.1.0 (the next /24 network would be 10.1.2.0, then 10.1.3.0, and so on).
The last 8 bits of the 32-bit address can be used to give workstations, hosts, and other devices an IP address, with the following exceptions:
The first host address on this network is reserved as a network designator to build routing tables: 10.1.1.0 (typically called the loopback address)
The last host address on this network is reserved as an IP broadcast address: 10...
Switching and routing packets
So far, we've covered the topics required to discuss how packets of data get routed from computer A to host B across LANs and/or WANs over distances that may range from across a room to across the globe. The important concepts to remember are that Ethernet frames work with switches and IP packets work with routers to accomplish this feat, which we'll cover in the next section.
Ethernet frames and switches
To reiterate what was outlined in the layer 2 (the data-link layer) discussion, Ethernet frames are switched from the entry port to the appropriate destination port based on the destination MAC address. Network switches build tables of which MAC addresses belong to each port, compare a frame's destination MAC address to these tables, and switch the frame to the appropriate egress port if the destination is on the same switch or out a trunk port to another switch or router otherwise.
Note that the first time a switch sees a destination MAC address it doesn't recognize...
Actually, network packets may traverse several routers and WAN links to reach the destination network, and each router traversed is called a hop. In the context of packet analysis, you should be aware that WAN links can introduce packet delivery delays or latency due to the following four major factors:
Physical speed-of-light propagation delay: This is the amount of time required for electrical or light signals to travel across copper/fiber cables over long distances.
Network routing/geographical distance: The WAN link routes are never in a straight line between points. They have to traverse major telephony switching centers and route along railways, roads, and other opportunistic paths.
Serialization delay into and across WAN links: The WAN links are often slower speed links, and it takes a finite amount of time to send packet data across these links one bit at a time.
Queuing delays: In network device buffers, including additional delays that may be induced by Quality of Service...
Wireless networks utilize a range of 802.11 specifications to provide connectivity over 2.4 or 5 GHz frequency bands at a variety of speeds. The significant differences between wireless frames and those found on wired networks are as follows:
Wireless networks employ carrier sense (every station is listening), multiple access (shared medium), and collision avoidance (avoiding collisions instead of just recovering from them) techniques, which reduce the throughput
In addition to data frames, which get forwarded to the wired network, wireless frame types include the following:
Wireshark can be used to capture and analyze packets on Wireless networks. However, in order to analyze the control and management frames, as well as select the radio channels to capture on without having to associate with a specific...
The important points covered in this chapter included how Ethernet frames are switched to the appropriate switch ports on a LAN based on destination MAC addresses that packets are routed across and to remote networks based on destination IP addresses, and how the frames carrying packets destined for remote networks based on the destination IP address are sent to the default gateway's port MAC address.
We also covered how and why slower and/or longer distance WAN links can add significant amounts of delay to packet transmissions, which slows application data exchanges and increases user response times. We finished the chapter by discussing how Wireshark can capture and analyze packets on 802.11 wireless networks using specialized adapters.
In the next chapter, we'll cover in detail how to capture and filter packets using Wireshark.