For the more advanced Splunker, search modes are quite important, and can save you plenty of time when speaking with a user that isn't very Splunk savvy. I will simply recap these, and mention that by default, Splunk runs in Smart Mode.
If you would like to change the mode in a search, just use the mode selector drop-down menu, below the time range picker, after you run a query.
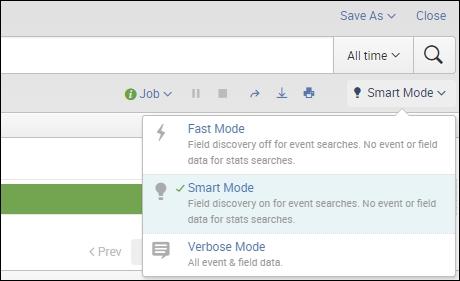
Fast Mode in Splunk will search all of the data you ask for, and then only return the essential parts of that data in its result set, as well as the fields you mentioned in your query. This will omit any unused fields, and no event data. So basically you will have sourcetype, source, host, and whatever fields you ask for from your data in your result set and that is all.
Note
Note that Field Discovery is off on Fast Mode, which is why it will only return the fields you ask for.
Here is an example of running a fast search:
index=network sourcetype=fw | stats count by service | sort - count | head...





























































