G Suite is built with a security-first mindset. It's designed to meet the highest security standards and is subject to regular independent third-party audits by several national and international agencies and organizations.
One key difference between the free and business versions is the security features. Free accounts are not designed to be handled individually, so there is no easy way to monitor or enforce security.
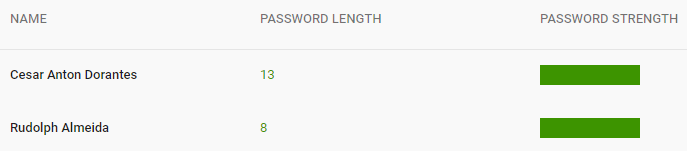
Business accounts, on the other hand, allow administrators to enforce advanced security like two-step verification and login challenges to prevent attacks, even when some user credentials are compromised.
The Security center allows administrators to easily adjust all settings related to domain security and user account protection. The& Security center is divided into different sections, each showing its name and a short description....