We have come to the final chapter, dear readers. Maybe this is a misnomer, but in the context of the book, it kind of makes sense. Ordinarily, red teaming refers to a holistic approach to testing. It's debated whether this is the best, worst, or just another form of testing. I'm using it as a term for bringing together all the earlier types of testing that I've covered.
This last chunky portion will cover two full implementations of the stuff I've told you so far, so you can copy, I mean, learn from them and design your own challenges. I will cover sections from each of the earlier chapters and show them in a working environment. I will also present some alternative ideas, suggest further opportunities, and cry a bit at the end when I've finally finished. In this chapter, we will cover the following in detail:
Scoring systems
Setting the scenario
Reporting examples
Variations for assault courses
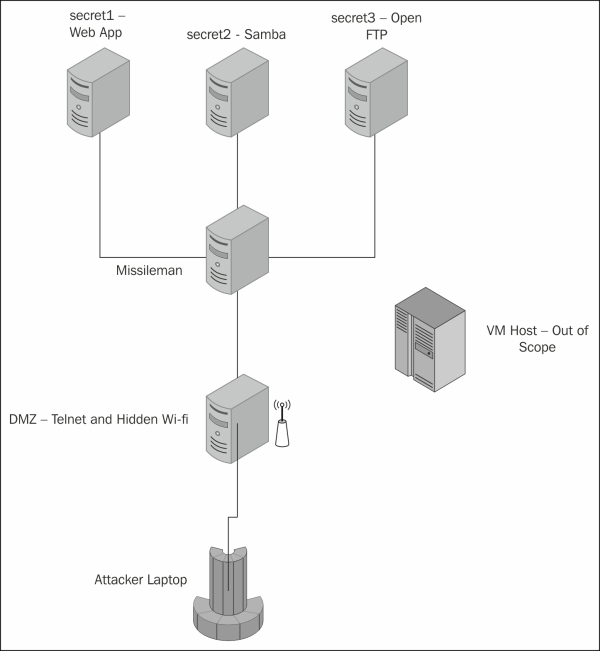
The missile silo scenario
The vulnerability assessment scenario