IBM Worklight provides various security roles to protect applications, adapter procedures, and static resources from an unauthorized access.
Each role can be defined by a security test that comprises one or more authentication realms. The authentication realm defines a process that will be used to authenticate the users.
The authentication realm has the following parts:
Authenticator and login module: This is a component on the server
One authentication realm can be used to protect multiple resources. We will look into each component in detail.
Device Request Flow: The following screenshot shows a device that makes a request to access a protected resource, for example, an adapter function, on the server. In response to the request, the server sends back an authentication challenge to the device to submit its authenticity:
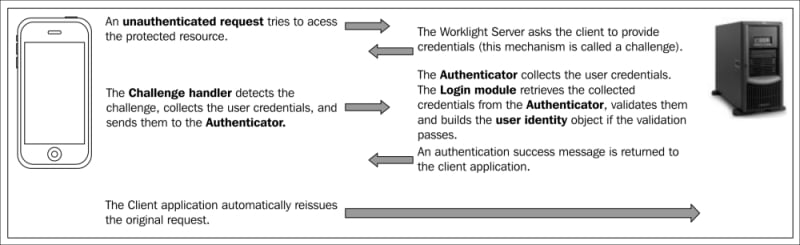
Request/Response flow between Worklight application and...























































