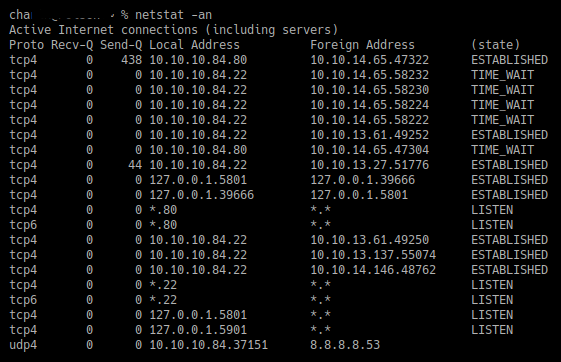
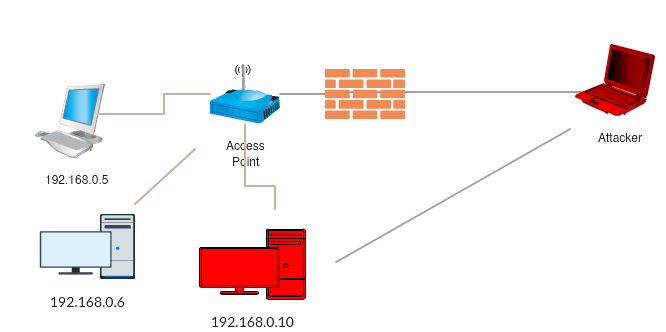
Once we have gained access to a system using either a web application or service exploitation, our next goal is to gain access to the internal network that the system might be connected to. Before we explore the details of this, let's first try to understand a bit about port forwarding. Port forwarding is a method which is used to authorize an external device's access to an internal network.
This is most commonly used by gamers. For example, imagine you're playing Counter Strike and you want to play with your friends by creating a game server. However, those friends are not on the same network as you. To overcome this, you port forward an external port of your public IP to your machine's local port number:
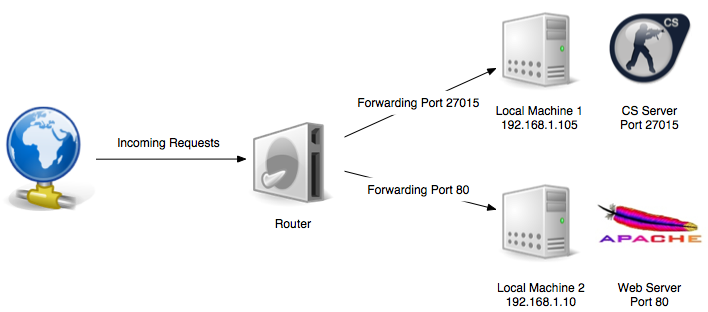
The simplest method of port forwarding is through...