Configuring, Crawling, Auditing, and Reporting with Burp
This chapter will help testers calibrate Burp Suite settings at both the project and user levels for optimization against the target application. For example, tweaks to the Crawling and Auditing options can assist with less abusive and less noisy brute-forcing attacks. Likewise, testers can find themselves in interesting network situations when trying to reach a target. Thus, several features are included in Burp Suite for testing sites running over Hypertext Transport Protocol Secure (HTTPS) or accessing sites through a SOCKS proxy or a port forward. Many settings are available at both the project and user levels. Finally, Burp Suite provides out-of-the-box functionality to generate a report for found issues.
In this chapter, we will cover the following recipes:
- Establishing trust over HTTPS
- Setting project configurations
- Setting user configurations
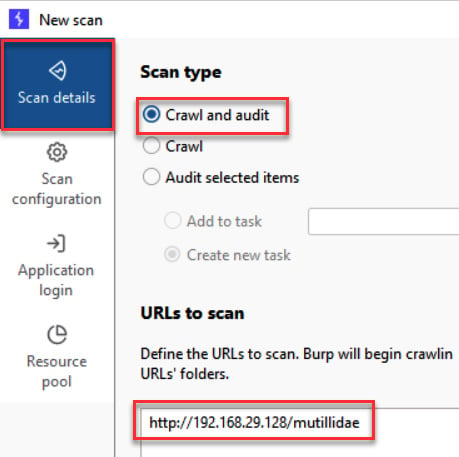
- Crawling target sites
- Creating a custom scan script...