How is Industry 4.0 being leveraged?
The power of artificial intelligence (AI) tools has led to the evolution of Industry 4.0. Various sectors—such as manufacturing, healthcare, finance, the public sector, consumer goods, retail, and smart city planning and building—use intelligent machines to help subject matter experts (SMEs) streamline processes, thus helping to meet highly competitive industry demands. How is this leveraged by different industry verticals?
The following figure describes how Industry 4.0 is leveraged by different industry verticals:
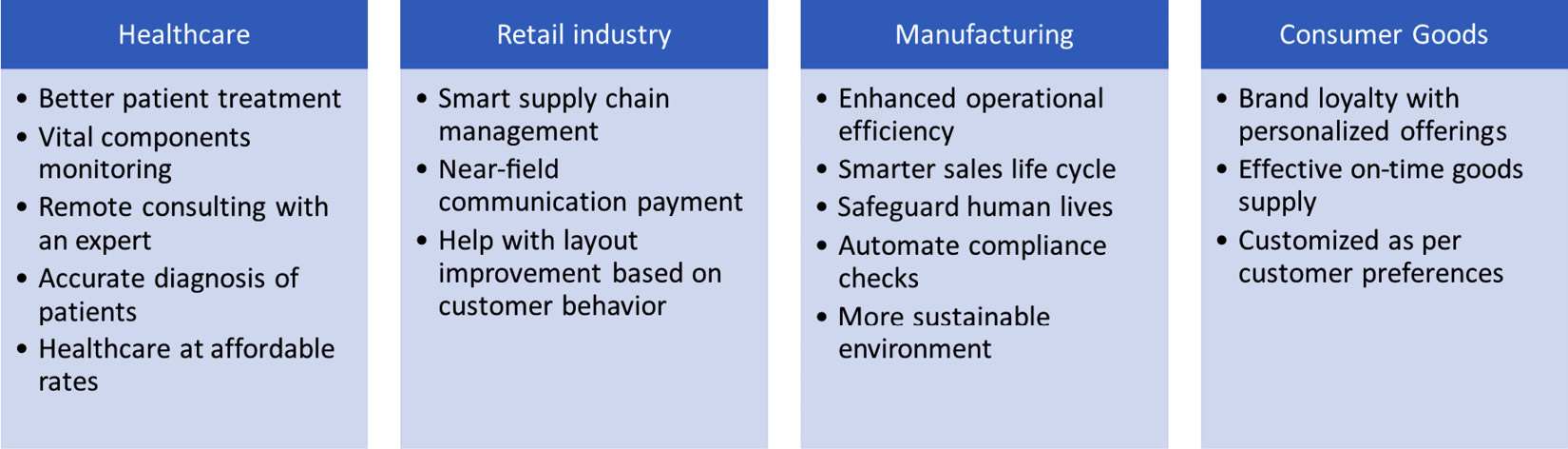
Figure 1.2 – Industries leveraging industry 4.0
The factors that are common across all verticals are the reduced cost of operations and enhanced customer experience, ultimately making companies more secure, efficient, productive, and profitable.
Now that we have seen some of the verticals leveraging and benefiting from Industry 4.0, we can go into detail regarding how these industries operate in the real world. In the real world, the convergence of information technology (IT) and OT brings about new challenges to conquer – that is, cybersecurity – and this convergence is bound to happen in pursuit of better business results, profits, data analytics, and much more.
Let us quickly learn a few basic terms:
- OT is hardware and software that detects or causes a change through directly monitoring and/or controlling industrial equipment, assets, processes, and events.
- The IoT is the concept of interconnected computer devices, mechanical and digital machines, objects, animals, or people, armed with unique identifiers (UIDs) and the ability to transmit data over a network, without intervention or computer interaction.
- The EIoT refers to how digital transformation and enterprise strategies being connected enables seamless collaboration between people and technology. It also provides more insight and improves the productivity of an enterprise by reducing the amount of manual work and optimizing business outcomes.
- The Industrial Internet of Things (IIoT) refers to the expansion and use of the IoT in industrial applications. It focuses strongly on machine-to-machine (M2M) communication, big data, and machine learning (ML). The IIoT enables industries and businesses to make their operations more efficient and reliable. It encompasses industrial applications, including robotics, medical devices, and software-defined manufacturing processes.
- Supervisory control and data acquisition (SCADA) is a control system architecture that includes computers, networked data communications, and graphical user interfaces to monitor machinery and processes at a high level. This includes sensors and other devices, such as programmable logic controllers (PLCs), that are connected to process systems or machines.
- A distributed control system (DCS) is an automated control system for a process or plant, usually with many control loops, in which self-contained controls are distributed throughout the system, but there is no centralized operator supervision. This is in contrast to systems with centralized controllers, discrete controllers in a central control room, or a central computer. The DCS concept increases reliability and reduces installation costs by placing control functions close to the process installation with remote monitoring.
The following figure provides more insight into the convergence of IT and OT, along with the IoT:
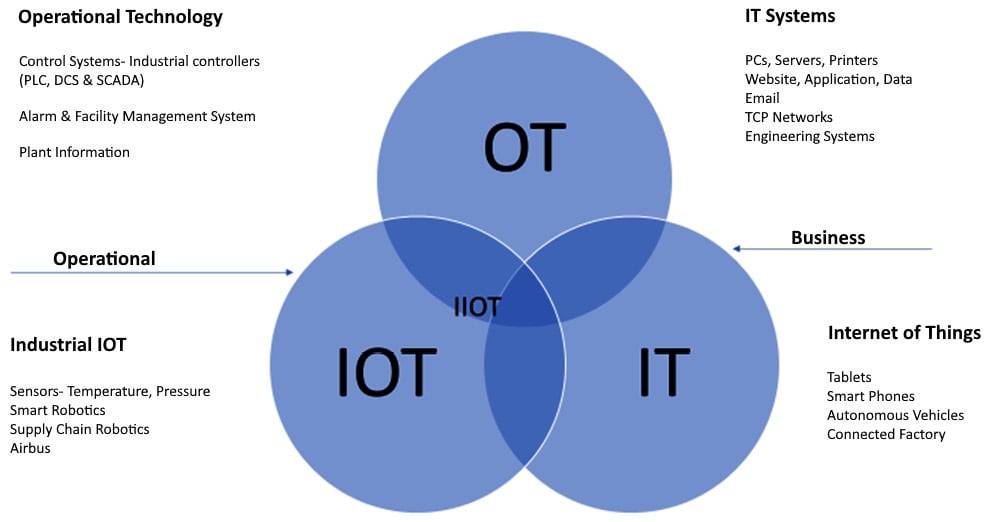
Figure 1.3 – Convergence of IT, OT, and the IoT
While OT covers control systems such as PLCs and DCS, IT covers PCs, servers, websites, and applications hosted within the organization or leveraged by an organization. The IT industry focuses on data while OT is focused on operations and the IoT focuses on M2M communication over the internet.
The IIoT industry, on the other hand, is about the use of smart sensors and actuators to enhance the outcome of industrial processes. This represents the intersection between OT and the IoT.
The legacy model of operation for organizations required IT and OT to be isolated. However, the convergence of IT and OT has brought about a successful transformation for the OT and IoT industries.
The IoT has already crossed the nascent stage and it has become mainstream. In fact, the number of IoT devices has already surpassed the number of IT devices. This proliferation of IoT devices has brought about increased attention, and adversaries and threat actors have already started targeting them for quick monetary gain by exploiting their vulnerabilities.
Industry 4.0 has three important stages:
- Digitization: Digitized outputs that are connected to industrial assets lead to the convergence of the digital and physical worlds. Connecting digitized outputs to security information and event management (SIEM) solutions can provide visibility to all incidents and actions in real time.
- Sensorization: Adding sensors to industry processes helps bring about better interconnection. This enables the autodetection of issues or changes in temperature, pressure, humidity, and so on, as it helps ascertain that the continuous monitoring of inputs and any sudden changes to them is in place. This prevents mishaps, too.
- Optimization: With the AI and ML world we live in, data analytics is leveraged to improve business and process outcomes. Leveraging data analytics and simulations leads to optimized results, which bring about profits for the organization through the management of time and effort.
So far, we have understood the impact of and the blazing changes brought in by Industry 4.0, and how a connected world and its disruptive technology (the use of AI and ML) have changed our future trajectory in general.
































































