Windows VSS
VSS is a feature of Windows OSs that allows users to take snapshots of the state of their hard drive at a specific point in time. These snapshots, known as shadow copies, can be used to restore previous versions of files and directories in the event of data loss or corruption.
From a digital forensics perspective, volume shadow copies can be a valuable source of evidence. They provide a historical record of the state of the hard drive, including deleted and altered files. This information can be used to reconstruct the chain of events that occurred on the system and to identify any suspicious activity.
Volume shadow copies are stored as part of the VSS, which is a component of Windows that provides the functionality to create and manage shadow copies. VSS maintains a list of all shadow copies on a particular volume, allowing a user to select and restore the desired shadow copy.
One of the key benefits of volume shadow copies is that they are created automatically in the background, without the user’s intervention. This means that even if a user is unaware of the feature, it can still contain valuable evidence. In addition, the shadow copies are stored in a hidden and protected area of the hard drive, making it difficult for attackers to tamper with or destroy them.
When conducting a digital forensics examination, it is important to capture and preserve shadow copies to ensure that evidence remains intact. This can be done by creating a forensic image of a hard drive, which can then be analyzed for the presence of shadow copies. Once the shadow copies have been identified, the forensic examiner can extract and analyze the contents to identify any relevant information.
By using VSS, we can track changes in an New Technology File System (NTFS) filesystem. However, it does not store data every time a user changes a file; instead, it typically stores data once a week or as configured by a user on the machine.
When conducting a digital forensic investigation and searching for any suspicious or malicious activity, such as file deletion, we can utilize the VSS to obtain valuable forensic evidence. By comparing the original content of the hard drive with that stored in VSS, we can determine whether any changes or tampering have occurred.
To check VSS on your local machine, you can run CMD.exe with admin privileges and use the following command to list the shadow copies:
Vssadmin list shadows
The following screenshot shows the output of the preceding command:
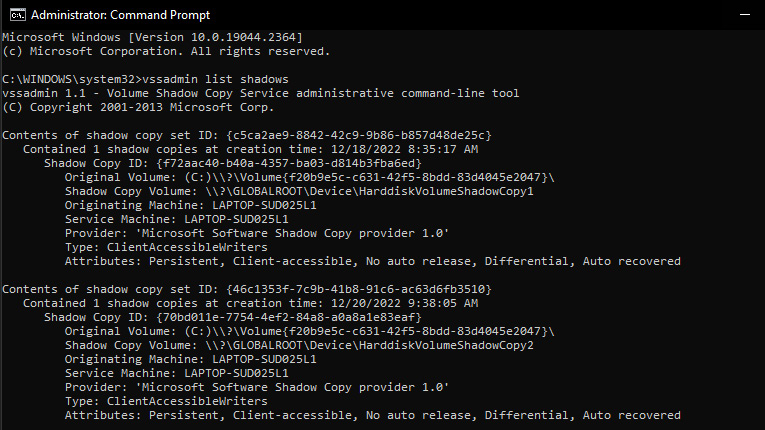
Figure 1.6 – Vssadmin command output
Another useful trick is mounting a shadow copy using a Windows command line. On a live machine, we can manually mount and browse VSS data using the following mklink command, which creates a symbolic link to VSS. To do this, we need to invoke cmd.exe to use the mklink utility, as powershell.exe will not work:
mklink /d C:\shadow_copy_test \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\
Create a symbolic link to VSS by using the following command line:
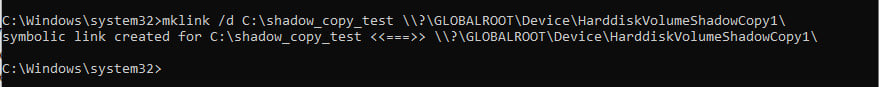
Figure 1.7 – Mounting a volume shadow using mklink
Now, in the C drive, we can see a new symbolic link has been created and linked to the shadow copy, and we can browse it as a normal file:
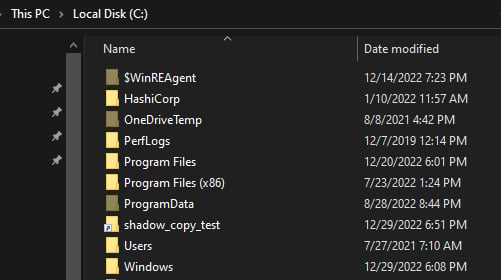
Figure 1.8 – Mapped shadow copy in the C drive
There are other utilities and tools that help to mount VSS, such as Arsenal Image Mounter and VSCMount; however, we will leave the option to you to explore more tools and test them within the labs.
In the next section, we will discuss and prepare the lab environment for digital forensic investigations.































































