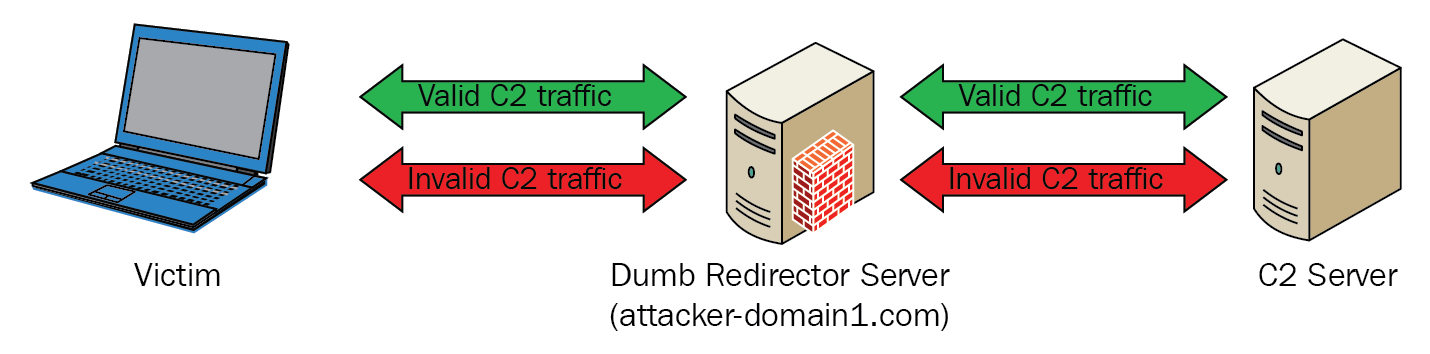
In the previous chapter, we learned about the basics of C2 server and how we can use file-sharing services like Dropbox and OneDrive as a C2 server. However, from the blue team's perspective, the unfamiliar IPs will be blacklisted after knowing what those IPs are for. If our C2 server is blacklisted, our engagement will fail. Consequently, to protect our C2 servers from being detected by the defenders of the organization, we will hide our team servers behind another server. This server is called a Redirector and it'll be responsible for redirecting all the communication to our C2 server.
In this chapter, we will cover the following topics:
- Introduction to redirectors
- Obfuscating C2 securely
- Short-term (ST) and long-term (LT) redirectors
- Payload stager redirection
- Domain fronting