Chapter 1: Getting Started with Ghidra
In this introductory chapter, we will provide an overview of Ghidra in some respects. Before starting, it would be convenient to know how to acquire and install the program. This is obviously something simple and trivial if you want to install a release version of the program. But I guess you probably want to know this program in depth. In which case, I can tell you in advance that it is possible to compile the program by yourself from the source code.
Since the source code of Ghidra is available and ready to be modified and extended, you will probably also be interested in knowing how it is structured, what kind of pieces of code exist, and so on. This is a great opportunity to discover the enormous possibilities that Ghidra offers us.
It is also interesting to review the main functionalities of Ghidra from the point of view of a reverse engineer. This will arouse your interest in this tool since it has its own peculiarities, and this is precisely the most interesting thing about Ghidra.
In this chapter, we're going to cover the following main topics:
- WikiLeaks Vault 7
- Ghidra versus IDA and many other competitors
- Ghidra overview
Technical requirements
The GitHub repository containing all the necessary code for this chapter can be found at the following link:
https://github.com/PacktPublishing/Ghidra-Software-Reverse-Engineering-for-Beginners
Check out the following link to see the Code in Action video: https://bit.ly/3qD1Atm
WikiLeaks Vault 7
On March 7, 2017, WikiLeaks started to leak Vault 7, which became the biggest leak of confidential documents on the US Central Intelligence Agency (CIA). This leak included secret cyber-weapons and spying techniques divided into 24 parts, named Year Zero, Dark Matter, Marble, Grasshopper, HIVE, Weeping Angel, Scribbles, Archimedes, AfterMidnight and Assassin, Athena, Pandemic, Cherry Blossom, Brutal Kangaroo, Elsa, OutlawCountry, BothanSpy, Highrise, UCL/Raytheon, Imperial, Dumbo, CouchPotato, ExpressLane, Angelfire, and Protego.
While Michael Vincent Hayden, the director of the CIA between 2006 and 2009 and director of the NSA between 1999 and 2005, as the spokesperson, did not confirm or deny the authenticity of this enormous leak, some NSA intelligence officials anonymously did leak the material.
The existence of Ghidra was leaked in the first part of Vault 7: Year Zero. This first part consists of a huge leak of documents and files stolen from the CIA's Center for Cyber Intelligence in Langley, Virginia. The leak's content is about the CIA's malware arsenal, zero-day weaponized exploits, and how Apple's iPhone, Google's Android, devices Microsoft's Windows devices, and even Samsung TVs are turned into covert microphones.
Ghidra was referenced three times in this leak (https://wikileaks.org/ciav7p1/cms/index.html), showing things such as how to install it, a step-by-step tutorial (with screenshots) of how to perform a manual analysis of a 64-bit kernel cache by using Ghidra, and the latest Ghidra version available at the time, which was Ghidra 7.0.2.
NSA release
As announced during RSA Conference 2019 in San Francisco, Rob Joyce, senior advisor for cybersecurity at NSA, explained the unique capabilities and features of Ghidra during a session called Get your free NSA reverse engineering tool, and Ghidra program binaries were also published.
During this session, some features were explained:
- Team collaboration on a single project feature
- The capabilities to extend and scale Ghidra
- The generic processor model, also known as
SLEIGH - The two working modes: interactive and non-GUI
- The powerful analysis features of Ghidra
Finally, on April 4, 2019, the NSA released the source code of Ghidra on GitHub (https://github.com/NationalSecurityAgency/ghidra), as well as on the Ghidra website, where you can download Ghidra release versions that are ready to use: https://ghidra-sre.org. The first version of Ghidra that was available on this website was Ghidra 9.0. Ghidra's website is probably not available to visitors outside the US; if this is the case, you can access it by using a VPN or an online proxy such as HideMyAss (https://www.hidemyass.com/).
Unfortunately for the NSA, a few hours later, the first Ghidra vulnerability was published by Matthew Hickey, also known as @hackerfantastic, at 1:20 AM, March 6, 2019. He said the following via Twitter:
Then, a lot of suspicions about the NSA and Ghidra arose. However, taking into account the cyber-espionage capabilities of the NSA, do you think the NSA needs to include a backdoor in its own software in order to hack its users?
Obviously, no. They don't need to do this because they already have cyber-weapons for that.
You can feel comfortable when using Ghidra; probably, the NSA only wanted to do something honorable to improve its own image and, since Ghidra's existence was leaked by WikiLeaks, what better way to do that than to publish it at RSA Conference and release it as open source?
Ghidra versus IDA and many other competitors
Even if you have already mastered a powerful reverse engineering framework, such as IDA, Binary Ninja, or Radare2, there are good reasons to start learning Ghidra.
No single reverse engineering framework is the ultimate one. Each reverse engineering framework has its own strengths and weaknesses. Some of them are even incomparable to each other because they were conceived with different philosophies (for instance, GUI-based frameworks versus command line-based frameworks).
On the other hand, you will see how those products are competing with and learning from each other all the time. For instance, IDA Pro 7.3 incorporated the undo feature, which was previously made available by its competitor, Ghidra.
In the following screenshot, you can see the epic and full-of-humor @GHIDRA_RE official Twitter account's response to IDA Pro's undo feature:

Figure 1.1 – IDA Pro 7.3 added an undo feature to compete with Ghidra
Differences between frameworks are susceptible to change due to the competition, but we can mention some current strengths of Ghidra:
- It is open source and free (including its decompiler).
- It supports a lot of architectures (which maybe the framework you are using does not support yet).
- It can load multiple binaries at the same time in a project. This feature allows you to easily apply operations over many related binaries (for example, an executable binary and its libraries).
- It allows collaborative reverse engineering by design.
- It supports big firmware images (1 GB+) without problems.
- It has awesome documentation that includes examples and courses.
- It allows version tracking of binaries, allowing you to match functions and data and their markup between different versions of the binary.
In conclusion, it is recommended to learn as many frameworks as possible to know and take advantage of each one. In this sense, Ghidra is a powerful framework that you must know.
Ghidra overview
In a similar way as happened at RSA Conference, we will provide a Ghidra overview in order to present the tool and its capabilities. You will soon realize how powerful Ghidra is and why this tool is not simply another open source reverse engineering framework.
At the time of writing this book, the latest available version of Ghidra is 9.1.2, which can be downloaded from the official website mentioned in the previous section of this chapter.
Installing Ghidra
It is recommended to download the latest version of Ghidra (https://ghidra-sre.org/) by clicking on the red Download Ghidra v9.1.2 button, but if you want to download older versions, then you need to click on Releases:
Figure 1.2 – Downloading Ghidra from the official website
After downloading the Ghidra archive file (ghidra_9.1.2_PUBLIC_20200212.zip) and decompressing it, you will see the following file structure:
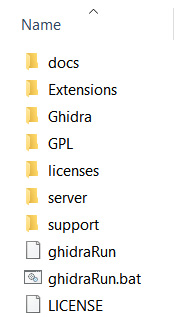
Figure 1.3 – The Ghidra 9.1.2 structure after it is decompressed
The content can be described as follows (source: https://ghidra-sre.org/InstallationGuide.html):
docs: Ghidra documentation and some extremely useful resources, such as learning Ghidra courses for all levels, cheatsheets, and a step-by-step installation guideExtensions: Optional Ghidra extensions allowing you to improve its functionality and integrate it with other toolsGhidra: The Ghidra program itselfGPL: Standalone GPL support programslicenses: Contains licenses used by Ghidraserver: Contains files related to Ghidra Server installation and administrationsupport: Allows you to run Ghidra in advanced modes and control how it launches, including launching it to be debuggedghidraRun: The script used to launch Ghidra on Linux and iOSghidraRun.bat: Batch script allowing you to launch Ghidra on WindowsLICENSE: Ghidra license file
In addition to downloading a release version of Ghidra (which is precompiled), you can compile the program on your own, as will be explained in the next section.
Compiling Ghidra on your own
If you want to compile Ghidra on your own, then you can download the source code from the following URL: https://github.com/NationalSecurityAgency/ghidra.
You can then build it using Gradle by running the following command:
gradle --init-script gradle/support/fetchDependencies.gradle init gradle buildGhidra gradle eclipse gradle buildNatives_win64 gradle buildNatives_linux64 gradle buildNatives_osx64 gradle sleighCompile gradle eclipse -PeclipsePDE gradle prepDev
This will produce a compressed file containing the compiled version of Ghidra:
/ghidra/build/dist/ghidra_*.zip
Before starting Ghidra, make sure your computer meets the following requirements:
- 4 GB RAM
- 1 GB storage (for installing Ghidra binaries)
- Dual monitors strongly recommended
Since Ghidra is written in Java, if it is executed before installing the Java 11 64-bit runtime and development kit, some of the following error messages could be displayed:
- When Java is not installed, you will see the following:
"Java runtime not found..."
- When the Java Development Kit (JDK) is missing, you will see the following:
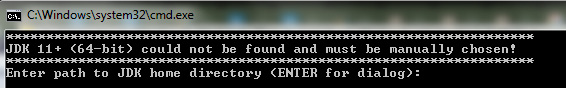
Figure 1.4 – Missing JDK error
Therefore, if you get any of those messages, please download the JDK from one of the following sources:
- https://adoptopenjdk.net/releases.html?variant=openjdk11&jvmVariant=hotspot
- https://docs.aws.amazon.com/corretto/latest/corretto-11-ug/downloads-list.html
How to solve installation issues
Ghidra's step-by-step installation guide, including known issues, can be found in Ghidra's documentation directory at
docs\InstallationGuide.html.It is also available online at the following link: https://ghidra-sre.org/InstallationGuide.html.
Note that you can report new issues you find in Ghidra through the following link: https://github.com/NationalSecurityAgency/ghidra/issues.
After installing Ghidra, you will be able to launch it using ghidraRun on Linux and iOS and ghidraRun.bat on Windows.
Overview of Ghidra's features
In this section, we will look at an overview of some fundamental Ghidra features in order to understand the overall functionality of the program. It is also a good starting point to get familiar with it.
Creating a new Ghidra project
As you will notice, differently than other reverse engineering tools, Ghidra doesn't work with files directly. Instead, Ghidra works with projects. Let's create a new project by clicking on File | New Project…. You can also do this faster by pressing the Ctrl + N hotkey (the complete list of Ghidra hotkeys is available at https://ghidra-sre.org/CheatSheet.html and also in Ghidra's documentation directory):
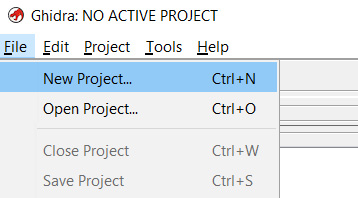
Figure 1.5 – Creating a new Ghidra project
Furthermore, projects can be non-shared or shared projects. Since we want to analyze a hello world program without collaboration with other reverse engineers, we will choose Non-Shared Project, and then click on the Next>> button. Then, the program asks us to choose a project name (hello world) and where to store it:
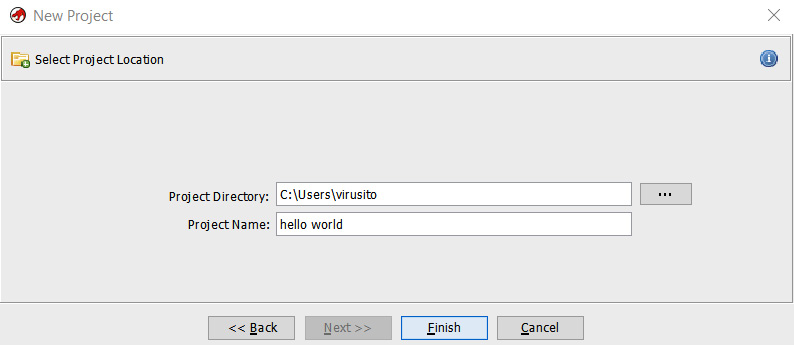
Figure 1.6 – Choosing a project name and directory
The project is composed of a hello world.gpr file and a hello world.rep folder:
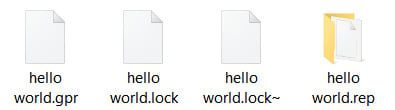
Figure 1.7 – Ghidra project structure
A Ghidra project (the *.gpr file) can only be opened by a single user. Therefore, if you try to open the same project twice at the same time, the concurrency lock implemented using the hello world.lock and hello world.lock~ files will prevent you from doing so, as shown in the following screenshot:
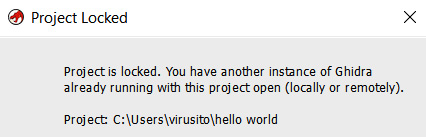
Figure 1.8 – Ghidra's project locked
In the next section, we will cover how to add binary files to our project.
Importing files to a Ghidra project
We can start to add files to our hello world project. In order to analyze an extremely simple application with Ghidra, we will compile the following hello world program (hello_world.c) written in the C programming language:
#include <stdio.h>
int main(){
printf("Hello world.");
}
We use the following command to compile it:
C:\Users\virusito\Desktop\hello_world> gcc.exe hello_world.c C:\Users\virusito\>\
Let's analyze the resulting Microsoft Windows Portable Executable file: hello_world.exe.
Let's import our hello world.exe file to the project; to do that, we have to go to File | Import file. Alternatively, we can press the I key:
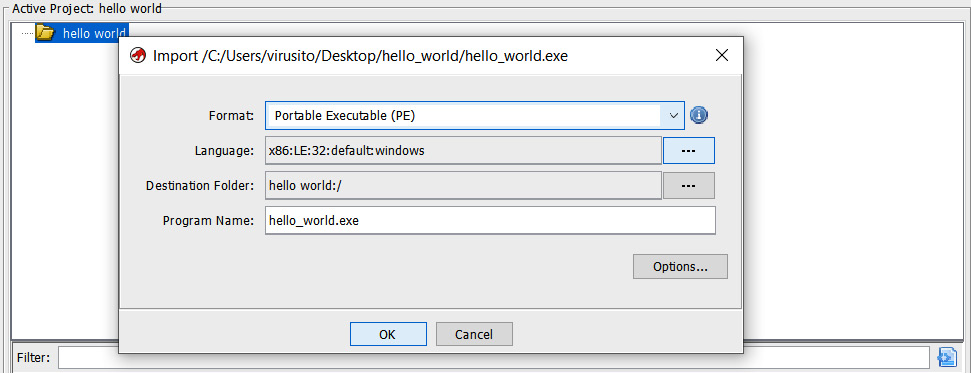
Figure 1.9 – Importing a file to the Ghidra project
Ghidra automatically identified the hello_world.exe program as an x86 Portable Executable binary for 32-bit architectures. As it was successfully recognized, we can click OK to continue. After importing it, you will see a summary of the file:
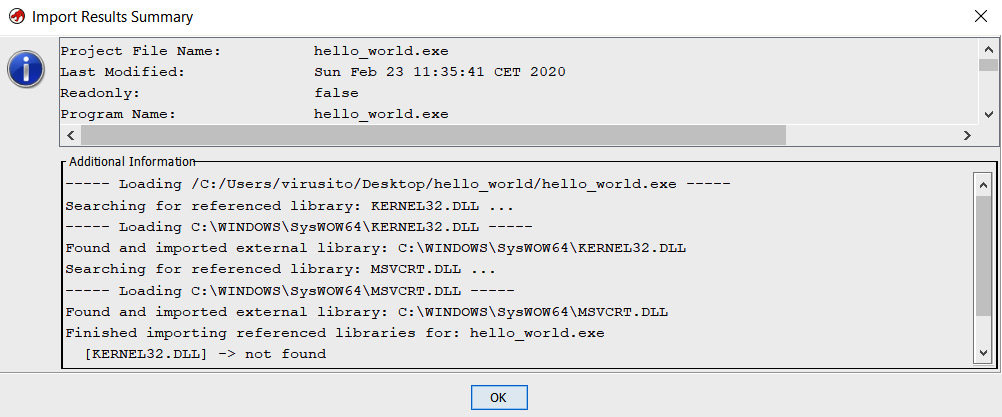
Figure 1.10 – Ghidra project file import result summary
By double-clicking the hello_world.exe file or clicking on the green Ghidra icon of Tool Chest, the file will be opened and loaded by Ghidra:
Figure 1.11 – A Ghidra project containing a Portable Executable file
After importing files into your project, you can start to reverse engineer them. This is a cool feature of Ghidra, allowing you to import more than one file into a single project, because you can apply some operation (for example, search) over multiple files (for example, an executable binary and its dependencies). In the next section, we will see how to analyze those files using Ghidra.
Performing and configuring Ghidra analysis
You will be asked whether to analyze the file, and you probably want to answer Yes to this because the analysis operation recognizes functions, parameters, strings, and more. Usually, you will want to let Ghidra get this information for you. A lot of analysis configuration options do exist. You can see a description of every option by clicking on it; the description is displayed in the upper-right Description section:
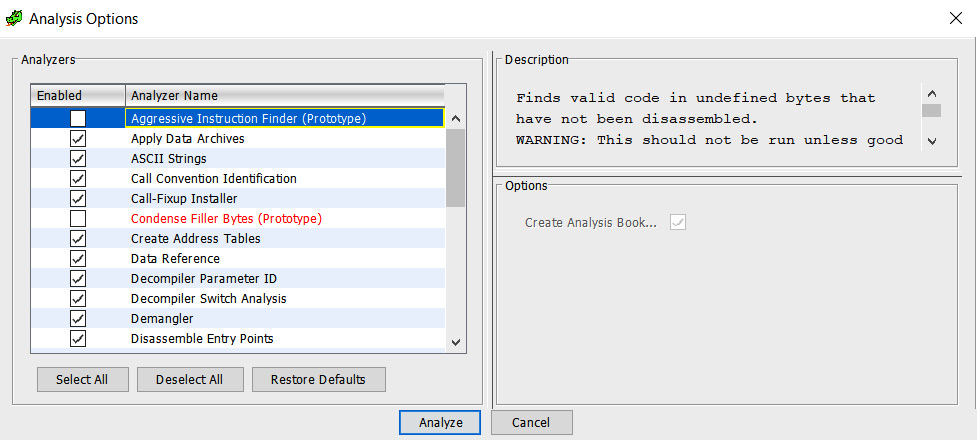
Figure 1.12 – File analysis options
Let's click on Analyze to perform the analysis of the file. Then, you will see the Ghidra CodeBrowser window. Don't worry if you forget to analyze something; you can reanalyze the program later (go to the Analysis tab and then Auto Analyze 'hello_world.exe'…).
Exploring Ghidra CodeBrowser
Ghidra CodeBrowser has, by default, a pretty well-chosen distribution of dock windows, as shown in the following screenshot:
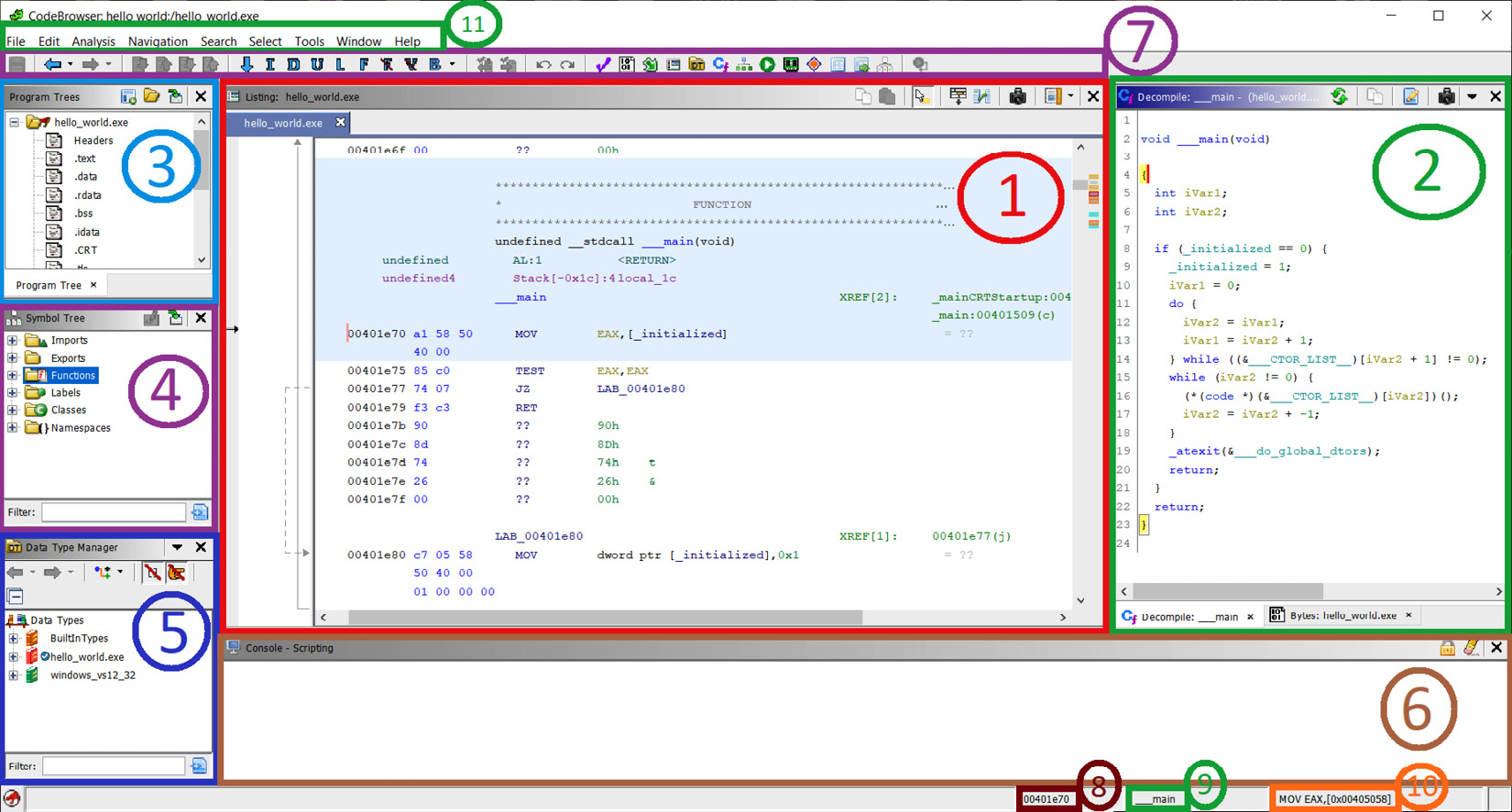
Figure 1.13 – Ghidra's CodeBrowser window
Let's see how CodeBrowser is distributed by default:
- As usual, by default in reverse engineering frameworks, in the center of the screen, Ghidra shows a disassembly view of the file.
- As the disassembly level is sometimes a too low-level perspective, Ghidra incorporates its own decompiler, which is located to the right of the disassembly window. The main function of the program was recognized by a Ghidra signature, and then parameters were automatically generated. Ghidra also allows you to manipulate decompiled code in a lot of aspects. Of course, a hexadecimal view of the file is also available in the corresponding tab. These three windows (disassembly, decompiler, and the hexadecimal window) are synchronized, offering different perspectives of the same thing.
- Ghidra also allows you to easily navigate in the program. For instance, to go to another program section, you can refer to the Program Trees window located in the upper-left margin of CodeBrowser.
- If you prefer to navigate to a symbol (for example, a program function), then go just below that, to where the Symbols Tree pane is located.
- If you want to work with data types, then go just below that again, to Data Type Manager.
- As Ghidra allows scripting reverse engineering tasks, script results are shown in the corresponding window at the bottom. Of course, the Bookmarks tab is available in the same position, allowing you to create pretty well-documented and organized bookmarks of any memory location for quick access.
- Ghidra has also a quick access bar at the top.
- At the bottom right, the first field indicates the current address.
- Following the current address, the current function is shown.
- In addition to the current address and the current function, the current disassembly line is shown to complete the contextual information.
- Finally, at the topmost part of CodeBrowser, the main bar is located.
Now that you know the default perspective of Ghidra, it's a good time to learn how to customize it. Let's address this in the following section.
Customizing Ghidra
This is the default perspective of Ghidra, but you can also modify it. For instance, you can add more windows to Ghidra by clicking on the Window menu and choosing one that piques your interest:
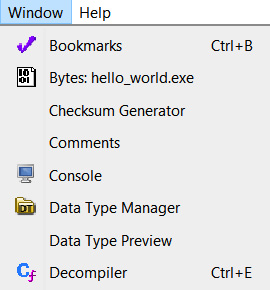
Figure 1.14 – Some items in the Ghidra Window submenu
Ghidra has a lot of awesome functionalities – for instance, the bar located on the upper-right bar of the disassembly window allows you to customize the disassembly view by moving fields, adding new fields, extending the size of a field in the disassembly listing, and more:
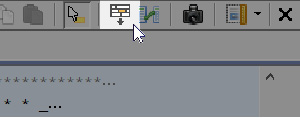
Figure 1.15 – Disassembly listing configuration
It also allows you to enable a very interesting feature of Ghidra, which is its intermediate representation or intermediate language, called PCode. It allows you to develop assembly language-agnostic tools and to develop automated analysis tools in a more comfortable language:
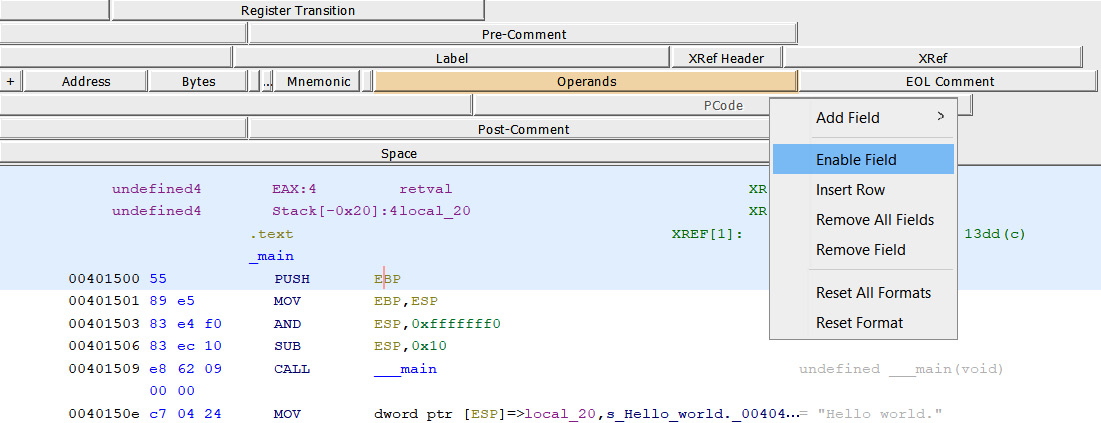
Figure 1.16 – Enabling the PCode field in the disassembly listing
If it is enabled, then PCode will be shown in the listing. As you will soon realize, PCode is less human-readable, but it is sometimes better for scripting reverse engineering tasks:
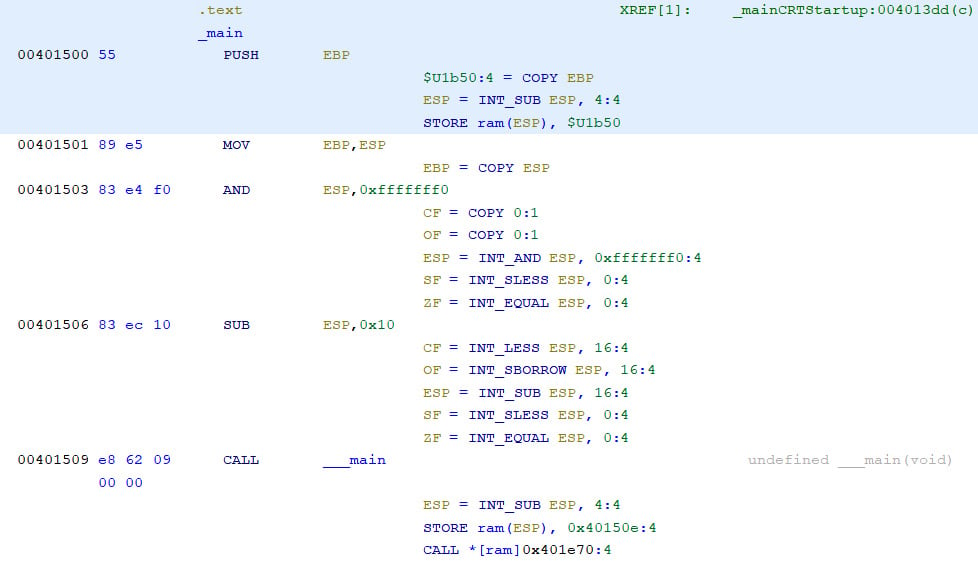
Figure 1.17 – Disassembly listing with PCode enabled
Discovering more Ghidra functionalities
Some powerful features available in other reverse engineering frameworks are also included in Ghidra. For instance, as in other reverse engineering frameworks, you also have a graph view:
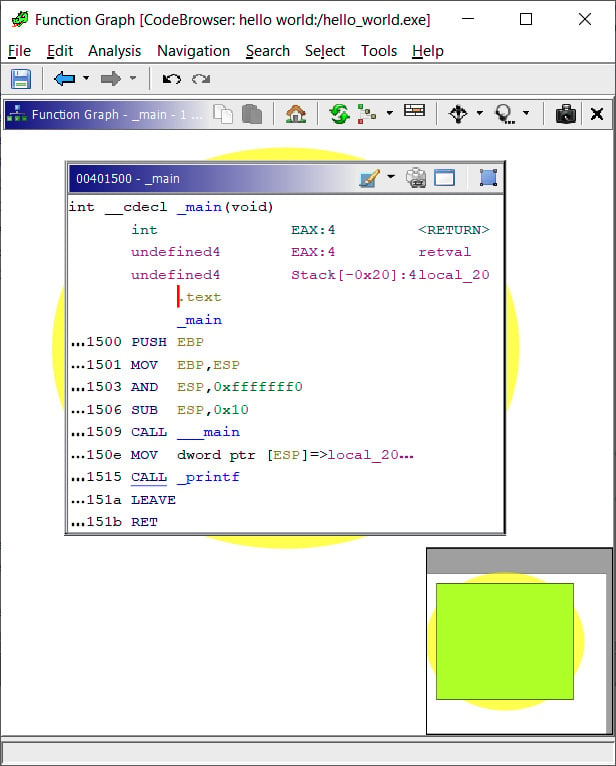
Figure 1.18 – Graph view of a hello world program's main function
As you will notice, Ghidra has a lot of features and windows; we will not cover all of them in this chapter, nor modify and/or extend them all. In fact, we haven't mentioned all of them yet. Instead, we will learn about them through practice in the following chapters.
Summary
In this chapter, we addressed the exciting and quirky origins of Ghidra. Then, we covered how to download, install, and compile it on our own from the source code. You also learned how to solve issues and how to report new ones to the Ghidra open source project.
Finally, you learned the structure of Ghidra and its main functionalities (some of them have not been covered yet). Now, you are in a position to investigate and experiment a little bit with Ghidra on your own.
This chapter helped you understand the bigger picture of Ghidra, which will be useful in the following chapters generally, which are more focused on specifics.
In the next chapter, we will cover how to automate reverse engineering tasks by using, modifying, and developing Ghidra plugins.
Questions
- Is there one reverse engineering framework that is absolutely better than the others? What problems does Ghidra solve better than most frameworks? Cite some strengths and weaknesses.
- How can you configure the disassembly view to enable PCode?
- What is the difference between the disassembly view and the decompiler view?




















 Download code from GitHub
Download code from GitHub






