Emerging technologies such as blockchain and AI have reached the pinnacle of visibility, acceptance, and also some speculation from various academics and industry experts. With a common aim to reduce operational inefficiency and add transparency, these two emerging technologies are now in great demand. From disruptive start-ups to large-scale enterprises, everyone is racing toward the opportunity to become a leader in blockchain- and AI-based solutions. This book aims to prepare you for the next leap of convergence of these two technologies and guide you to become technically capable of building these solutions.
This chapter provides a brief overview of the current blockchain landscape. The key topics covered in this chapter are as follows:
- Blockchain versus distributed ledger technology versus distributed databases
- Public versus private versus permissioned blockchain
- Privacy in blockchains
- Understanding Bitcoin
- Introduction to Ethereum
- Introduction to Hyperledger
- Other blockchain platforms – Hashgraph, Corda, and IOTA
- Consensus algorithms
- Building DApps with blockchain tools
Technical requirements
This chapter assumes you have a basic awareness of blockchain and its impact on traditional systems for transactions.
Blockchain versus distributed ledger technology versus distributed databases
There have been several debates on how to differentiate blockchains from Distributed Ledger Technology (DLT) and distributed databases. Based on some of the user- and application-level features and heuristics, we can observe the following differences:
|
Feature |
Blockchain |
DLT |
Distributed Database |
|
Immutability |
The information persisted in blockchains cannot be removed or updated without a new identifier to the target data. |
Although most DLTs are pro-immutability, there are a few exceptions where immutability is not a design constraint. |
Most distributed databases are not immutable due to design limitations. |
|
Logical execution |
Smart contracts can be used to enforce business logic on data from a blockchain. |
DLTs offer the execution of logic on the data within them, as well as on user inputs. |
User-defined functions and stored procedures are normal approaches that are used here. |
|
Accessibility |
Data in a public blockchain is stored in the form of a transaction or account states in a block and is visible and accessible with middleware. |
Data is private in a DLT and may, in some cases, be encrypted in the DLT entry. Data can only be accessed by participating stakeholders. |
Data is persisted within the distributed data clusters spread across the globe for faster access, using traditional client-server techniques. |
|
Verifiability |
All the transactions are verified before a change is made to the state of an account. |
Most DLTs do not offer verification algorithms or modules as a design restriction to applications. |
The verifiability of data is not offered as the state of accounts is not persisted in a specific structure. |
|
Incentivization |
Most blockchains use several economic models to incentivize their stakeholders. |
Stakeholders in a DLT group host the nodes and are self-incentivized to run their business more confidently. |
The company manages the data for sustainability and so no extra incentivization can be observed. |
Let's now compare these technologies with an example use case discussed in the following section.
Comparing the technologies with examples
The following scenario is provided to aid your understanding of the core differences between the preceding three implementations.
Imagine that you plan to create a new digital platform for stock photography. If you want to invite photographers all over the world to use the platform and allow them to upload their work and be incentivized with their royalties automatically paid off by the consumers, you'd want to use blockchain to offer public access and incentivization and to transfer the royalties directly from the consumer to the photographer, thereby eliminating the need for a third party performing the duty payment collection, guaranteeing the return of royalties but with a service fee.
However, if you want your platform to form a private consortium of photographers, with their art exclusively available to a limited audience, and to handle royalties in conjunction with other means, you would use a DLT.
Finally, if you intend to use your platform to exhibit art by an eligible set of photographers that are accessible across the globe, with or without royalties (which is handled offline), you'd form a cluster of nodes that host this data and logic to handle access and payments. So, you would use distributed databases.
Let's now further discuss the types of blockchains available for different use cases.
Public versus private versus permissioned blockchains
Public blockchains were designed and developed with a focus on ensuring that any number of interested parties can execute the business logic and access transactional information. Similarly, any interested party can also verify and validate the transactions incoming to the network, as well as be rewarded for the process.
Private blockchains are implemented to ensure that access to business information is limited and only accessible to a limited set of participating stakeholders.
Permissioned blockchains are a hybrid implementation of what both public and private blockchains have to offer. Permissioned blockchains are implemented if data is to be accessed by a specific stakeholder. This is achieved by leveraging private networking, as well as the encryption of transactional user data, which is also stored in blocks that may consist of transactions relating to other stakeholders in the consortium.
Comparing usage scenarios
The following table shows how the three types of blockchain can be used in various scenarios. They are:
|
Attribute versus variant |
Public blockchains |
Private blockchains |
Permissioned blockchains |
|
Network barrier |
Access to the network is not restricted. The details inside public blockchains are widely accessible to all users. |
Access to the network is limited by an IP or a DNS. Only a few people with suitable credentials can join the network. |
Access to the network is limited to verified participants. Only selected people can join the network with limited permissions to read, write, or both. |
|
Restrictions |
There are many different actions that the user can perform, such as develop a smart contract and use it, host a node as a validator, and so on. |
Virtually, there are only two common roles for members in a private blockchain—facilitated nodes as validators and DApps users. |
Based on the role of the members, the users may be able to deploy DApps, use DApps, validate transactions, or all three. |
|
Encryption |
Almost all of the user data in blocks is not encrypted as the general goal is to serve the information to a public audience. |
Encryption may not be used if there is a trust quotient between the participating stakeholders. |
Encryption is widely used as it involves various stakeholders in the networks with potential conflicts of interest. |
In the next section, we will further understand the privacy options in blockchains.
Privacy in blockchains
Blockchains add new values, such as transparency and provenance of information. However, many people mistakenly believe that all transactions are publicly viewable in a blockchain. However, in reality, not all the blockchains necessarily facilitate transactions with public viewability:
- Motivations: Several applications on blockchains are not just built for enterprise use cases. Many blockchain applications are now targeting mass consumer audiences. The internet, in recent years, has become a testbed for various approaches in preserving the privacy of users. Unlike any other trend or improvement on the current state of the internet, most blockchain projects aim to deliver a privacy-first mode of operation to users by leveraging pseudonymous cryptographic wallets without revealing the identity of the senders and receivers. Some examples of privacy-first blockchains include Monero, Quorum, and Zcash.
- Approaches: As we already know, public blockchains have design limitations with respect to privacy. As global access to user data is one of the prominent objectives of a public blockchain, we see very few applications of cryptography in them. However, the emerging blockchains such as Zcash, Monero aim to offer untraceable, secure, and analysis-resistant transactional environments for users with their own cryptocurrencies. This is made possible by leveraging a Zero-Knowledge proof mechanism that prevents double spend of the same cryptocurrencies, but at the same time preserves the fundamental values of blockchain.
On the other hand, private and permissioned blockchains consider protecting the privacy of the participating stakeholders as high priority. One well-known private implementation is the Quorum blockchain, which was developed by JP Morgan Chase & Co. Quorum offers transaction-level privacy, yet at the same time offers network-level transparency on the actions by all the stakeholders in the network by using a privacy engine called Constellation. Constellation encrypts the transaction payload with a special key generated from the public/private key pair of the users involved in the transaction. It also facilitates the deployment and operation of private smart contracts within an existing network.
Let's now explore Bitcoin, the earliest cryptocurrency with the largest market capitalization of them all.
Understanding Bitcoin
Bitcoin is a virtual currency on a peer-to-peer network with users and validators distributed across the network. With the help of the Bitcoin blockchain network, users can transfer cryptocurrency in a truly decentralized manner, without a need for either a central bank, a clearing house, or an intermediary. The transfer of Bitcoin between users is recorded in the form of a transaction, which is later verified, mined, and added to a canonical link of blocks.
Bitcoin is believed to have been created by a group work working under the pseudonym Satoshi Nakamoto, with most of its features and functionalities derived based on existing techniques in cryptographic hashes, peer-to-peer network communication, and immutable data structures.
In the following diagram, we have illustrated how Bitcoin mining works in a single node, as well as in pool environments:

You can check it out in detail by going to, https://git.io/JJZzN and https://git.io/JJZzx.
A brief overview of Bitcoin
This section offers historical background on the Bitcoin cryptocurrency, along with factual information on its current state as well as the technical and architectural limitations perceived by experts in the market.
We will now quickly dive into some of the necessary details required for further chapters:
- Motivation: One of the core motivations behind this cryptocurrency was that the currencies rolled out by central banks could not be trusted as they may not be backed by real collateral. This led to the adoption of a free-market approach to the production, distribution, and management of the money, with proof of work for every Bitcoin minted, thereby eliminating the need for central banks and other intermediaries.
- Facts: The virtual currency was open sourced in 2009 with a maximum supply of 21 million Bitcoin that can be minted. Around 18.3 million Bitcoin has been mined to date, with at least three forks.
The following are the prominent Bitcoin forks:
- Bitcoin Cash (with larger block sizes)
- Bitcoin Gold (preserving GPU-based Proof of Work (PoW) mining instead of ASICs) and Bitcoin Adjustable Block-Size Cap (ABC) with 32 MB of blocksize)
- Bitcoin Satoshi's Vision (SV) with an increased block size of 128 MB
At the time of writing this book, each Bitcoin was valued at around USD 6,806.00. The Bitcoin blockchain network incentivizes validating miners by charging users who transfer Bitcoin with a small fee, which is awarded to the winning block maker as per the PoW algorithm. - Criticism: The cryptocurrency is alleged to be one of the prime choices of medium for illicit transactions. One of the major crackdowns of this sort of use came from a renowned online black market on the darknet, Silk Road. The FBI shut down the website in late 2013.
With basic knowledge of blockchains, let's now move on and learn about Ethereum.
Introduction to Ethereum
Ethereum is a public blockchain that was designed by Vitalik Buterin in 2013 as an enhancement to the incumbent Bitcoin blockchain, by including transaction-based state management with business logic scripting using a special-purpose programming language and a virtual machine called the Ethereum Virtual Machine (EVM).
The following diagram outlines the basics of block creation in Ethereum:
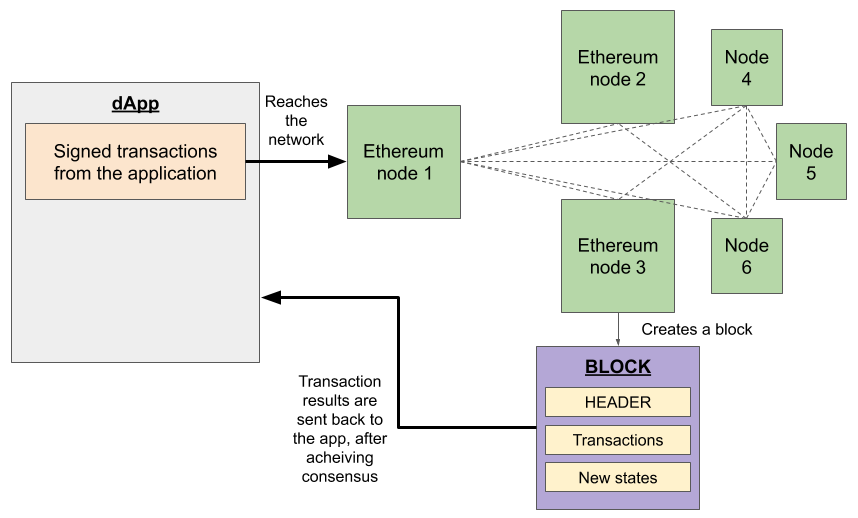
In the next section, we will look at a brief description of Ethereum.
A brief overview of Ethereum
This section offers historical background on the Ethereum cryptocurrency, along with factual information on its current state as well as the technical and architectural limitations perceived by experts in the market:
- Motivation: The main motivation behind Ethereum was to support building decentralized applications on the powerful medium of blockchain. Unable to convince the Bitcoin community of the need for a scripting language, Vitalik and a like-minded group of people created Ethereum.
- Facts: The project was open sourced with an initial release date of July 30, 2015. The research and development upgrades to the Ethereum network is managed under the Ethereum Foundation, financially supported by the initial crowd sale of the Ether (ETH) token from July to August 2014. Around 105 million ETH has been minted so far. Ethereum has one major fork called Ethereum Classic (the original Ethereum blockchain that denied the DAO hard fork and retained the original unaltered state of the Ethereum network). At the time of writing this book, each ETH is valued at around USD 156.00. The Ethereum blockchain network also incentivizes the validating nodes by charging users who make transactions on DApps or transfer ETH with a small fee, which is awarded to the winning block maker. The rules of creating blocks and the acceptance of blocks are specified by consensus algorithms called PoW or Proof of Stake (PoS). We will explore PoW and PoS in more detail in the upcoming sections of this chapter.
- Criticism: The Ethereum community has had to face some of the earliest criticism due to the hard-fork decision taken by the team, thereby contradicting some of the ideology and values of blockchain, such as immutability and immunity from human political dynamics. The network was later criticized and heavily scrutinized by the regulatory authorities due to the alleged Ponzi schemes offered by the Initial Coin Offerings (ICOs) without a stable product or service.
With this basic understanding of Ethereum, let's move on to look at the Hyperledger platform.
Introduction to Hyperledger
Hyperledger is an open source project hosted by the Linux Foundation in collaboration with various industry leaders in finance, banking, supply chain, manufacturing, and other domains to create standard blockchain technologies. We will now dive deeper into Hyperledger and some of the projects under the Hyperledger umbrella.
Overview of the project
Linux Foundation announced the Hyperledger project on February 9, 2016, with an initial 30 founding corporate members, including Accenture, IBM, DTCC, Intel, and R3, among others. At the time of writing, the Hyperledger governing board consists of 21 board members and around 200 corporate members around the globe. The project hosts a dozen code repositories of blockchain frameworks and tools. A few significant examples are mentioned in the following section.
Hyperledger Fabric
Hyperledger Fabric is a blockchain framework initially developed by the IBM and Digital Assets members. Fabric is a DLT that aims to provide a modular architecture for developers to use only what is needed. The framework supports the execution of logic abstracted into containers called chaincode. Using Fabric is easily enabled by the plethora of documentation, tutorials, and tools available for deploying business networks without much hassle.
Hyperledger Sawtooth
Hyperledger Sawtooth is a blockchain framework that offers enterprises a secure leadership election of nodes in the network, with special modes for executing instructions. Sawtooth offers a powerful, developer-friendly Software Development Kit (SDK) for a majority of languages to write and deploy smart contracts. Notably, Sawtooth is one of the early live projects to experiment with WebAssembly (WASM) as a virtual medium for the execution of smart contracts.
Other Hyperledger frameworks and tools
Some of the other notable projects incubated under the Hyperledger umbrella are as follows:
- Hyperledger Indy: A blockchain platform to specially handle decentralized identities from inside or external systems
- Hyperledger Grid: A WASM-based project for building supply chain solutions
- Hyperledger Quilt: A blockchain tool to connect blockchain realms of different protocols using the Interledger Protocol (ILP) specifications
- Hyperledger Caliper: A blockchain benchmarking tool to assess the performance of a specific blockchain with specific parameters such as Transactions Per Second (TPS), transaction latency, resource utilization, and so on
With this basic understanding of Hyperledger, let's now explore other blockchain platforms available to developers.
Other blockchain platforms – Hashgraph, Corda, and IOTA
Hashgraph is a DLT with a superior consensus mechanism leveraging Directed Acyclic Graphs (DAGs). Notably, the implementation of this project is not fully open source. The algorithm was designed and published by Leemon Baird and was initially released in 2017.
Corda is an open source DLT maintained by the financial services consortium R3. Corda offers a smart contracts platform to allow businesses to execute complex agreements, associating multiple variants of asset classes across various business domains, including supply chain, healthcare, and finance.
IOTA is an open source DLT that offers payment automation and secure communication between IoT devices. This project is maintained by the non-profit IOTA Foundation. Quoted as one of the promising ICOs, the project has delivered impressive wallets, a data marketplace for sensor data, and payment channels for quicker transaction settlements using a new special data structure called Tangle, eliminating the need for miners and traditional canonical representations of transactional data in blocks.
With this basic knowledge of blockchain platforms, let's now move on to look at the internal components of a typical blockchain network.
Consensus algorithms
The laws that human society relies on to function are much more difficult to enforce when it comes to computers. Consensus algorithms are the specific instructions programmed on computers in a network so that they have a common definition of objects and instructions to agree on changes. Crashes, failures, and Byzantine faults in computers led to a better approach in forming an agreement in a digital network and so consensus algorithms rose to great heights, well before the dawn of the internet. This concept has been revisited thanks to the new leap in innovation to blockchains.
The following sections look at some of the important consensus algorithms used by blockchains.
Proof of work
Proof of work (PoW) is a consensus algorithm introduced by the anonymous founder of Bitcoin—Satoshi Nakamoto. The PoW consensus algorithm is one of the earliest consensus algorithms used in a blockchain environment. It leverages a combination of cryptography, P2P network communications, and a Merkle data structure to offer a distributed, immutable, and cumulative state of accounts in the Bitcoin blockchain. The solution computed by the first node is verified by the remaining nodes and the block producer is broadcast in the network:
- Merit: The PoW algorithm has been time tested in the Bitcoin blockchain network and there is not a single hack/compromise of the account states in the network leading to double spend.
- Demerit: As the PoW algorithm needs to find a solution to a mathematical problem, significant CPU cycles are required to generate hashes and so it is an energy-intensive technique.
Proof of stake
Proof of stake (PoS) is a new consensus algorithm designed and developed to address some of the trade-offs of the PoW algorithm. The block-producing node is determined by an application of mathematical function involving a few determining factors, such as the stake (for example, ETH), the age of the node, and the randomization of eligible node candidates:
- Merit: The PoS algorithm is energy-efficient as there are fewer computational requirements and it does not select a block-producing node based on a solution-verification model.
- Demerit: Although the PoS algorithm is efficient in its block times and is environment-friendly, there have been criticisms relating to the algorithm's vulnerability to capitalist attacks on the network of the node owner and tries to compete with other candidates with a stupendous amount of cryptocurrency at stake, higher than all the other candidates.
Proof of burn
Proof of Burn (PoB) is a consensus algorithm with an interesting approach to solving transition problems from one version of cryptocurrency to another in the blockchains. Through the PoB algorithm, the old cryptocurrency (or its preceding version) is burnt in order to reduce its supply and gradually increase the supply of the new cryptocurrency (or its succeeding version). This consensus algorithm is practiced in various forms, including a method wherein users can transfer the old cryptocurrency to an unspendable wallet address in exchange for new ones:
- Merit: The PoB algorithm is convenient during the transition of cryptocurrencies and network upgrades if the system trusts the participating entities.
- Demerit: The PoB algorithm is usually applicable in PoW-based blockchains and so has a limitation of applicability. This is due to the requirement of verifiable proofs and the ability to decay the burnt coins over time, which is naturally capable through PoW algorithms.
Delegated Proof of Stake
Delegated Proof of Stake (dPOS) is a consensus algorithm developed and used by the Block.one EOS platform. Under dPOS, the token holders reserve the right to nominate the validators (also called block producers). The selection of block producers is a continuous process and performs the duties of packaging user transactions into blocks with Byzantine fault-tolerant safety:
- Merit: dPOS is Byzantine Fault Tolerance (BFT) -ready and scales easily in a public network environment.
- Demerit: Although dPOS is efficient, it is prone to capitalistic efforts to supersede other minor token stakeholders.
Proof of authority
As the name suggests, the Proof of Authority (PoA) algorithm facilitates a distributed consensus with a few eligible verifiable nodes preserving the right to add transactions to blocks, if some criteria is met. There are many variants of the PoA algorithm, with or without the reputations of the validating nodes used in the public, private, and permissioned blockchains:
- Merit: The PoA algorithm is energy-efficient and not prone to capitalistic pitfalls as the validator nodes are authorized to add transactions to blocks based on their reputation. If the node is observed to malfunction, its reputation is severely affected and cannot proceed as a validator.
- Demerit: The PoA algorithm is partially centralized as the authority of adding or rejecting transactions lies in the purview of very few nodes in the network.
Practical Byzantine fault tolerance
Practical Byzantine Fault Tolerance (PBFT) is one of the replication algorithms brought to light by academic research. Authored by Miguel Castro and Barbara Liskov in 1999 (http://pmg.csail.mit.edu/papers/osdi99.pdf), this algorithm was primarily aimed at solving the Byzantine faults caused by the arbitrary point of failures in the nodes of a network.
Notably, the PBFT algorithm is used by the Hyperledger Fabric blockchain framework:
- Merit: The PBFT algorithm is efficient, with fast transaction processing and scalable to hundreds of nodes in a private network.
- Demerit: The algorithm is based on a gatekeeper technique and is hence criticized for its centralized approaches. PBFT is not suitable for public blockchains.
Proof of elapsed time
Proof of Elapsed Time (PoET) is a consensus algorithm developed and used by the Hyperledger Sawtooth blockchain framework. The PoET algorithm ensures security and randomness involved in the leadership of validator nodes with special CPU instructions available in most of the advanced processors featuring secure virtual environments:
- Merit: PoET allows anyone with eligible hardware to participate as a validator node, allowing legitimate ways of verifying the leader election.
- Demerit: Although PoET does not involve staking cryptocurrencies to form a validatory node, the cost of affording specialized hardware does not come cheap. So, there have been criticisms highlighting this as an unfair bar to enter the network.
RAFT
RAFT is a consensus algorithm designed and developed by Diego Ongaro and John Ousterhout with the main motivation to bring about a distributed consensus algorithm that is much easier to understand than Paxos. Notably, RAFT ensures safe leader election, appending log entries in a distributed manner, and state machine consistency. The RAFT consensus is implemented in the Quorum blockchain to inherit the preceding described safety features:
- Merit: RAFT is one of the fastest algorithms in processing complex transaction payloads with the security of leadership and state machine consistency.
- Demerit: RAFT is suitable for permissioned or private blockchains only.
Ternary augmented RAFT architecture
Ternary Augmented RAFT Architecture (TARA) is a consensus algorithm designed for large-scale Byzantine-distributed networks. It is an enhanced version of the RAFT consensus algorithm to address heterogeneous transactions identifiable by their asset classes by leveraging PBFT hardening and cryptographic message exchanges. TARA introduces dynamic hierarchy to networks to ensure that their authority is not concentrated among a few nodes:
- Merits: TARA offers service clusters to ensure high availability, throughput, and scale. It has the hardware of all form factors with the ability to compute and store transactions can participate. TARA can be applied in all three environments—public, private, and permissioned blockchain networks.
- Demerit: Leadership election is not inherently dependent on the node's reputation, thereby allowing a potential attack on systems. These constraints must be implemented explicitly.
Avalanche
The Avalanche consensus is a protocol for distributed systems, introducing leaderless Byzantine fault tolerance, using a metastable mechanism achieving the same level of security and consistency among the nodes. Avalanche depends on the Snowball family to form a DAG, which stores the user transactional data, instead of blocks:
- Merit: Avalanche guarantees liveness and is immune to race conditions in the network.
- Demerit: Leadership consensus may not be applicable to all blockchain environments as there is not a carefully analyzed set of heuristics to ensure consistency.
With this detailed analysis of consensus algorithms, let's now go through the development tools available to blockchain developers.
Building DApps with blockchain tools
One of the main causes of the mainstream adoption of blockchain is the developer-led wave of evangelism for the technology. This has been observed in the form of frameworks and tools at developer's disposal. In the following section, we will go through the various tools and platforms that are available for public consumption to build blockchain-based software solutions.
Blockchain toolchains and frameworks
The following list introduces several blockchain toolchains and frameworks that are popular with both developers and the associated solution community:
- Truffle: The Truffle framework was developed by ConsenSys as an open source project, offering a pipeline for the development, testing, and deployment of smart contracts targeted on the EVM.
- Embark: The Embark framework was developed by Status as an open source project, offering a debugging and integration environment for Ethereum smart contract developers. Notably, Embark offers tighter integration with IPFS for the decentralized storage of contract data.
- Hyperledger Composer: This is an open source effort from the Linux Foundation, which offers tools to assist developers with converting requirements into proof of concept for the DevOps process, for spinning a new network as required.
- MetaMask: This is a middleware that bridges an application running in the browser with the Ethereum blockchain. It is an open source initiative supported and consumed widely by all Ethereum developers. Users can perform transactions in a web application through MetaMask.
- Ethers.js: This is a JavaScript-based library with full implementation of the Ethereum wallet as per the specification. Developers use this open source library to create user wallets, perform transactions, and much more. This library is also well known for its recent support for Ethereum Name Service (ENS).
- Nethereum: This is an open source library used to build Ethereum-based blockchain solutions in .NET environments. Nethereum offers .NET developers an SDK called NuGet, which is integrated into the Visual Studio Integrated Development Environment (IDE) for using web3 functionalities across web and mobile applications.
Next, let us look into developing smart with IDEs and plugins.
Developing smart contracts using IDEs and plugins
Traditional software developers are more familiar and comfortable with working in IDEs, and the vibrant developer communities of blockchain have considered this. In the following section, we will observe a few famous web-based IDEs and plugins available for standalone IDEs.
The Remix IDE
Remix has been the de facto IDE for smart contract development and deployment. This open source IDE is used by developers who are interested in developing, debugging, and deploying solidity smart contracts for Ethereum network. Notably, this IDE works well with private networks and offers regular updates.
The EthFiddle IDE
EthFiddle is an open source initiative by Loom Network to facilitate code experimentation online and provides the ability to share experimental code snippets of solidity smart contracts among developers for easier collaboration.
The YAKINDU plugin for Eclipse
Several enterprise developers have yearned for plugins for current IDEs, and this plugin offers just that. YAKINDU offers basic syntax highlighting and other common language package features for solidity smart contract development in the Eclipse IDE.
The Solidity plugin for Visual Studio Code
This plugin can be installed on Visual Studio Code, one of the most used IDEs. It boasts to be one of the leading plugins used for solidity smart contract development.
The Etheratom plugin for Visual Studio Code
Etheratom is a plugin available for GitHub's Atom editor, offering IDE features such as syntax highlighting, including a deployment interface to a local Ethereum node. It uses web3.js to interact with a local Ethereum node.
Summary
Blockchain has enjoyed a lot of hype, and we are now observing some of the excitement that came out of this hype coming to fruition in the form of well-established practices, frameworks, tools, and live use cases. Understanding the current landscape of blockchain and its current offerings helps us to assess the ability to convert the emerging requirements into products, with less friction to the market.
In this chapter, we explored what blockchain is, and we are now confidently able to identify the similarities and differences between DLT and distributed databases. We also observed different types of design patterns within open and private blockchain with practical examples. We enumerated multiple blockchain projects, cryptocurrency implementations, frameworks, and tools.
In the next chapter, we will introduce you to the contemporary basics of AI, and we will observe different types and forms of AI, as well as more applications of AI.




















 Download code from GitHub
Download code from GitHub






