In this chapter, we will cover the following recipes:
- Installing Metasploit on Windows
- Installing Linux and macOS
- Installing Metasploit on macOS
- Using Metasploit in Kali Linux
- Setting up a penetration testing lab using VMware
- Setting up SSH connectivity
- Connecting to Kali using SSH
- Configuring Metasploit to use PostgreSQL
- Creating workspaces
- Using the database
- Using the
hostscommand - Understanding the
servicescommand
Metasploit is currently the world's leading penetration-testing tool, and one of the biggest open-source projects in information security and penetration testing. It has totally revolutionized the way we can perform security tests on our systems. The reason Metasploit is so popular is the wide range of tasks that it can perform to ease the work of penetration testing to make systems more secure. Metasploit is available for all popular operating systems. The working process of the framework is almost the same for all of them. In this book, we will primarily work on Kali Linux as it comes with the preinstalled Metasploit Framework and other third-party tools which run over the framework.
Let's proceed with a quick introduction to the framework and the various terminologies related to it:
- Metasploit Framework: This is a free, open-source penetration-testing framework started by H. D. Moore in 2003, which was later acquired by Rapid7. The current stable versions of the framework are written using the Ruby language. It has the world's largest database of tested exploits and receives more than a million downloads every year. It is also one of the most complex projects built in Ruby to date.
- Vulnerability: This is a weakness which allows an attacker/pentester to break into or compromise a system's security. This weakness can exist in the operating system, the application software, or even in the network protocols.
- Exploit: An exploit is a piece of code which allows an attacker/tester to take advantage of the vulnerable system and compromise its security. Every vulnerability has its own corresponding exploit. Metasploit has more than 1,700 exploits.
- Payload: This is the actual code which does the work. It runs on the system after exploitation. It is mostly used to set up a connection between the attacking and victim machines. Metasploit has more than 500 payloads.
- Module: Modules are the small building blocks of a complete system. Every module performs a specific task and a complete system is built by combining several modules to function as a single unit. The biggest advantage of such an architecture is that it becomes easy for developers to integrate new exploit code and tools into the framework.
The Metasploit Framework has a modular architecture and the exploits, payload, encoders, and so on are considered to be separate modules:

Let's examine the architecture diagram closely.
Metasploit uses different libraries that hold the key to the proper functioning of the framework. These libraries are a collection of predefined tasks, operations, and functions that can be utilized by different modules of the framework. The most fundamental part of the framework is the Ruby extension (Rex) library. Some of the components provided by Rex include a wrapper socket subsystem, implementations of protocol clients and servers, a logging subsystem, exploitation utility classes, and a number of other useful classes. Rex itself is designed to have no dependencies, other than what comes with the default Ruby installation.
Then we have the MSF Core library that extends Rex. Core is responsible for implementing all of the required interfaces that allow for interacting with exploit modules, sessions, and plugins. This core library is extended by the framework base library, which is designed to provide simpler wrapper routines for dealing with the framework core, as well as providing utility classes for dealing with different aspects of the framework, such as serializing a module state to different output formats. Finally, the base library is extended by the framework's user interface (UI) that implements support for the different types of UIs to the framework itself, such as the command console and the web interface.
There are two different UIs provided with the framework, namely msfconsole and a web interface. Checking out bought interfaces is highly recommended but, in this book, we will primarily work on the msfconsole interface. This is because msfconsole provides the best support to the framework, leveraging all of the functionalities.
The msfconsole interface is by far the most talked-about part of the Metasploit Framework, and for good reason, as it is one of the most flexible, character-rich, and well-supported tools within the framework. It actually provides a handy all-in-one interface for every choice and setting attainable in the framework; it's like a one-stop shop for all of your pen-testing dreams. We can use msfconsole to do anything, including launching an exploit, loading an auxiliary, executing enumeration, producing listeners, or executing mass exploitations in contrast to an entire network.
A web interface is available for you to work with Metasploit Community, Express, and Pro. To launch the web interface, open a web browser and go to https://localhost:3790.
Note
To see the operating systems that are currently supported and the minimum system requirements, please visit https://www.rapid7.com/products/metasploit/system-requirements.
Installation of the Metasploit Framework on Windows is simple and requires almost no effort. The framework installer can be downloaded from the Metasploit official website (http://www.metasploit.com/download). In this recipe, we will learn how to configure Metasploit on Windows.
You will notice that there are four editions of Metasploit available:
To follow along with this book, it is recommended to download the latest framework edition of Metasploit (https://windows.metasploit.com/metasploitframework-latest.msi), which contains the console and all other relevant dependencies.
Once you have completed downloading the installer, simply run it and sit back. It will automatically install all the relevant components. Once the installation is complete, you can access the framework through various shortcuts created by the installer:

Note
While installing Metasploit on Windows, you should disable the antivirus protection, as it may detect some of the installation files as potential viruses or threats and can block the installation process. Once the installation is complete, make sure that you have white-listed the framework installation directory in your antivirus software, as it will detect the exploits and payloads as malicious.
The quick installation script will import the Rapid7 signing key and set up the package for all supported Linux and macOS systems:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstallThe packages will integrate into the OS's native package management and can either be updated with the msfupdate command or by using your preferred package manager.
The full installation process is as follows:
# curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \ > chmod 755 msfinstall && \ > ./msfinstall % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 5394 100 5394 0 0 17618 0 --:--:-- --:--:-- --:--:-- 17627 Updating package cache..OK Checking for and installing update.. Reading package lists... Done Building dependency tree Reading state information... Done The following NEW packages will be installed: metasploit-framework ... Run msfconsole to get started W: --force-yes is deprecated, use one of the options starting with --allow instead. # msfconsole # cowsay++ ____________ < metasploit > ------------ \ ,__, \ (oo)____ (__) )\ ||--|| * ... msf >
The latest macOS installer package is available at https://osx.metasploit.com/metasploitframework-latest.pkg.
Download and launch the installer to install Metasploit Framework with all of its dependencies. Once installed, you can launch msfconsole as /opt/metasploit- framework/bin/msfconsole:

The Metasploit Framework initial setup will help you set up a database and add Metasploit to your local PATH as shown:
$ /opt/metasploit-framework/bin/msfconsole ** Welcome to Metasploit Framework Initial Setup ** Please answer a few questions to get started. Would you like to add msfconsole and other programs to your default PATH? yes You may need to start a new terminal or log in again for this to take effect. Would you like to use and setup a new database (recommended)? yes Creating database at /Users/user/.msf4/db Starting database at /Users/user/.msf4/db...success Creating database users Creating initial database schema ** Metasploit Framework Initial Setup Complete *
Kali Linux is the most popular operating system for security professionals for two reasons. First, it has all the popular penetration-testing tools preinstalled in it, so it reduces the cost of a separate installation. Secondly, it is a Linux-based operating system, which makes it less prone to virus attacks and provides more stability during penetration testing. It saves you time as you don't have to install the relevant components and tools, and who knows when you may encounter an unknown error during the installation process.
Either you can have a separate installation of Kali Linux on your hard disk, or you can also use it over a host on a virtual machine. The installation process is simple and the same as installing any Linux-based operating system.
To set up a Metasploit development environment on Kali Linux or any Debian-based Linux environment, you can use the following commands:
sudo apt update sudo apt -y install autoconf bison build-essential curl git-core libapr1 libaprutil1 libcurl4-openssl-dev libgmp3-dev libpcap-dev libpq-dev libreadline6-dev libsqlite3-dev libssl-dev libsvn1 libtool libxml2 libxml2-dev libxslt-dev libyaml-dev locate ncurses-dev openssl postgresql postgresql-contrib wget xsel zlib1g zlib1g-dev curl -sSL https://rvm.io/mpapis.asc | gpg --import - curl -L https://get.rvm.io | bash -s stable source ~/.rvm/scripts/rvm cd /opt sudo git clone https://github.com/rapid7/metasploit-framework.git sudo chown -R `whoami` /opt/metasploit-framework cd metasploit-framework rvm --install $(cat .ruby-version) gem install bundler bundle install
You can download Kali Linux ISO images from the official site, https://www.kali.org/downloads/, create a bootable USB drive, or burn the ISO image to a DVD-ROM and use it to install Kali Linux as a separate OS on your hard disk or simply boot the Kali ISO image in Live Mode. Another way is to run Kali Linux inside a virtual machine; for that, you can either use the ISO image to install Kali Linux from scratch or just download a Kali Linux VMware, VirtualBox, or ARM image from the official site.
For this book, we will use a Kali Linux VMware virtual machine:
- When booting the Kali Linux virtual machine, you will be asked to enter the username and password. The default username for the root user is
rootand the password istoor. - Upon successful login, the easiest way to get the Metasploit Framework up and running is to start Metasploit from the
Applicationsmenu.
- To launch Metasploit from the
Applicationsmenu, go toApplications|Exploitation Tools|metasploit framework, as shown in the following screenshot:

Note
Starting Metasploit Framework from the Applications menu will automatically set up the PostgreSQL database. It will create the database user, the msf and msf_test databases, configure Metasploit to use the database, create the database schema, and start msfconsole by running the following command: service postgresql start && msfdb init && msfconsole.
Creating database user 'msf' Enter password for new role: Enter it again: Creating databases 'msf' and 'msf_test' Creating configuration file in /usr/share/metasploit-framework/config/database.yml Creating initial database schema # cowsay++ ____________ < metasploit > ------------ \ ,__, \ (oo)____ (__) )\ ||--|| * =[ metasploit v4.16.8-dev- ] + -- --=[ 1683 exploits - 964 auxiliary - 299 post ] + -- --=[ 498 payloads - 40 encoders - 10 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf >
Alternatively, you can start the Metasploit Framework by typing msfconsole from a Terminal window.
As a rolling distribution, upgrading Kali Linux is simple. It's recommended to upgrade Kali Linux regularly, to ensure that you will get the latest security updates. To upgrade, use apt update followed by apt upgrade; apt will look for installed packages that can be upgraded without removing any packages, this way being the least intrusive.
For major version upgrades and important upgrades, use apt full-upgrade; this will do a complete upgrade and, if necessary, remove obsolete packages or install new dependencies.
Creating a penetration-testing lab is essential, it will allow you to practice and test new techniques and exploits in a secure environment. Using virtual machines for your lab environment will give you portability, flexibility, and low maintenance. You can work simultaneously on more than one operating system, set up complex network scenarios, and perform penetration tests on multiple targets. So, let's have a quick look at how we can set up a penetration-testing lab using virtualization.
For your lab, you can use the hypervisor of your choice; the most common hypervisors are VirtualBox, VMware Workstation Pro, VMware Fusion Pro (for Mac), VMware ESXi, and Microsoft Hyper-V. For the penetration testing lab used in this book, I would recommend you to use VirtualBox since it is an open source hypervisor and a requirement for building one of the virtual machines.
Note
Although you need to build the virtual machine using VirtualBox, after building the machine you can import it to any of the hypervisors you like.
This is the network diagram for the penetration-testing lab:

We will use four virtual machines with Kali Linux, a Linux server, a Windows server, and a Windows 10 client. In this lab, we have a modern scenario that will allow us to test and practice the latest techniques and exploits.
For the Kali Linux machine, the Linux server, and the Windows 10 client, the setup is simple. We can download the Kali Linux virtual machine from the official site, https://www.kali.org/downloads/; for the Linux server, we will use the Metasploitable 2 machine which you can download from SourceForge at https://sourceforge.net/projects/metasploitable/files/Metasploitable2/; and for the Windows 10 client, we can download a 90-day trial from the Microsoft Developer site at https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/.
For the last machine, we will use Metasploitable 3, a Windows virtual machine that we will build, with many security vulnerabilities for us to test. To build the Metasploitable 3 machine, we have to install Packer, Vagrant, the Vagrant Reload plugin, and VirtualBox. The build scripts and documentation, as well as the most up-to-date build instructions, can be found at the official GitHub repository: https://github.com/rapid7/metasploitable3. To build the machine automatically, perform the following steps:
- Run the
build_win2008.shscript if using Bash, orbuild_win2008.ps1if using Windows. - Upon successful completion, run
vagrant up. - When the process completes, you should be able to open the VM within VirtualBox and log in using the username
vagrantand passwordvagrant.
Before you start your virtual machines, there is an important configuration that you will have to make in order to set up the network communication for the lab:
- Select the Kali Linux virtual machine and click on
Settings. Then, move toRemovable Devices. In theNetwork Adapteroption, the network adapter should be configured to useInternet Sharing|Share with my Mac, which will allow the virtual machine to access the internet, sharing the IP address of the host machine, since it will provide Network Address Translation (NAT) for network traffic from the virtual machine.
- The network adapter of the Metasploitable 3 virtual machine and the first network adapter of the Metasploitable 2 virtual machine should also be configured to use NAT:
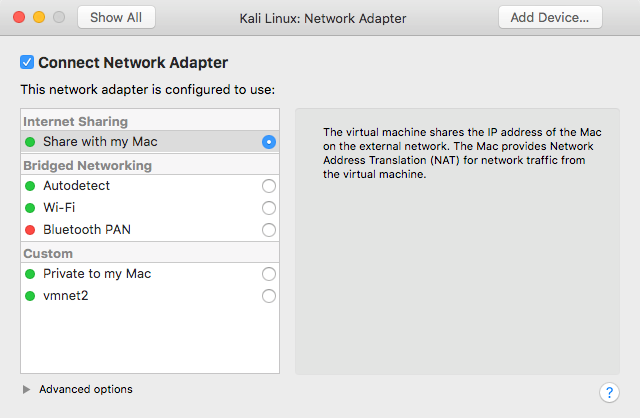
- In VMware Fusion, go to
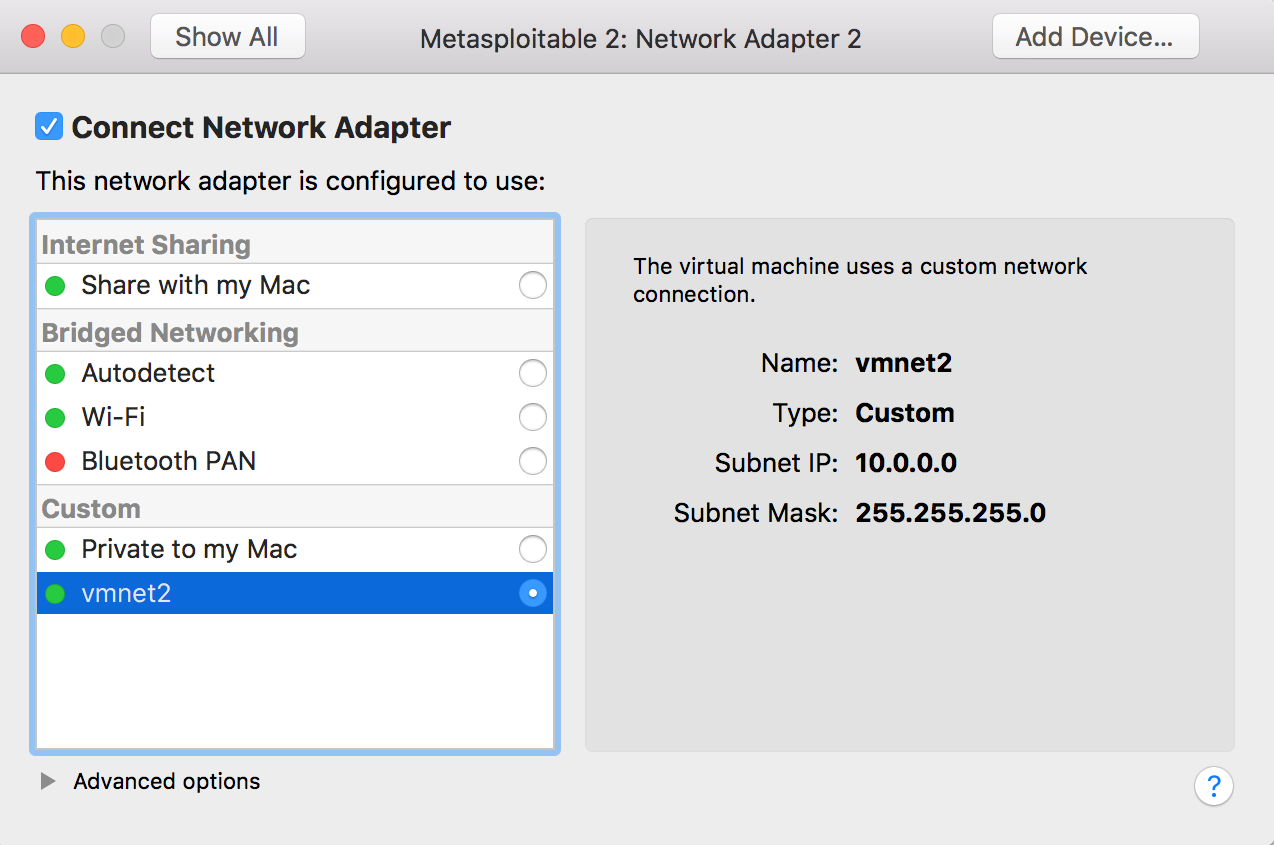
Preferences, select theNetworktab, and create a custom network. Check the box to provide addresses on this network via DHCP; use theSubnet IPof10.0.0.0and theSubnet Maskof255.255.255.0:

- Now that you have created the custom network, select the Windows 10 virtual machine, click on
Settings, then go to theNetwork Adaptersettings. ChooseCustomnetwork and select the custom network we have created. Repeat the process for the secondNetwork Adapterof the Metasploitable 2 virtual machine:
- To verify the configuration, log in to the Metasploitable 2 machine and use the
ip acommand. The default username for the root user ismsfadminand the password ismsfadmin:

By creating two NAT networks, we can simulate internet-facing servers using the first NAT network and internal machines using the custom network we have created, thus providing a more realistic scenario, and giving you the possibility to learn how to do reconnaissance of internal targets, pivoting, and lateral movement.
Secure Shell (SSH) allows you to connect to a remote host securely over an unsecured network.
To configure the Kali Linux machine for remote logins, we will start by changing the default root password and generating new SSH host keys.
To change the root password, use the passwd command as follows:
root@kali:~# passwd Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
To generate new SSH host keys, the steps are also relatively straightforward: remove the current SSH host keys, use the dpkg-reconfigure openssh-server command to reconfigure the OpenSSH server, and generate new SSH host keys:
root@kali:~# rm /etc/ssh/ssh_host_* root@kali:~# dpkg-reconfigure openssh-server Creating SSH2 RSA key; this may take some time ... 2048 SHA256:Ok/J4YvIGYieDI6YuOLDXADm5YUdrJSnzBKguuD9WWQ root@kali (RSA) Creating SSH2 ECDSA key; this may take some time ... 256 SHA256:eYU5TtQVzFYQtjo6lyiVHku6SQWbgkMPMDtW8cgaAJ4 root@kali (ECDSA) Creating SSH2 ED25519 key; this may take some time ... 256 SHA256:8nj2LMKQNOLKS9S9OsWcBArslPgpFfD/5h4vNrwI4sA root@kali (ED25519)
For lab purposes, we'll edit the OpenSSH server configuration /etc/ssh/sshd_config file to permit root login by changing the line #PermitRootLogin without-password to PermitRootLogin yes as you can see in the following example:
... # Authentication: #LoginGraceTime 2m PermitRootLogin yes #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 ...
To start the OpenSSH service automatically on boot, run the systemctl enable ssh and finish the configuration by restarting the service using the systemctl restart ssh command, as follows:
root@kali:~# systemctl enable ssh Synchronizing state of ssh.service with SysV service script with /lib/systemd/systemd-sysv-install. Executing: /lib/systemd/systemd-sysv-install enable ssh root@kali:~# systemctl restart ssh root@kali:~#
To connect to the Kali machine, all we need is an SSH client. Most Unix, Linux, and macOS operating systems already have an SSH client installed; however, if you are using Windows to connect to the Kali Linux machine, you will need to install a client such as PuTTY, which is one of the most popular and free SSH clients for Windows.
- To connect to the Kali Linux virtual machine, you need to know its IP address. To find the IP address, log in to the virtual machine, open a Terminal window, and enter the
ip addresscommand, orip afor short:
root@kali:~# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:b6:03:93 brd ff:ff:ff:ff:ff:ff inet 192.168.216.5/24 brd 192.168.216255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:feb6:393/64 scope link valid_lft forever preferred_lft forever
Note down the IP address of the second interface, in this example 192.168.216.5.
- Now, use the SSH client on the host operating system. Enter the username
rootfollowed by the@symbol and the IP address of the Kali Linux virtual machine,192.168.216.5:

In this SSH session, we can now interact with the Kali Linux virtual machine using the SSH client.
An important feature of Metasploit is the backend database support for PostgreSQL, which you can use to store your penetration-testing results. Any penetration test consists of lots of information and can run for several days, so it becomes essential to store the intermediate results and findings, such as target host data, system logs, collected evidence, and report data. As a good penetration-testing tool, Metasploit has proper database integration to store the results quickly and efficiently. In this recipe, we will be dealing with the installation and configuration process of a database in Kali Linux.
To configure PostgreSQL, we will first start the service and then use the Metasploit msfdb command to initialize the database.
- To set up our Metasploit database, we first need to start up the PostgreSQL server, using the following command:
root@kali:~# systemctl start postgresql- Then we need to create and initialize the
msfdatabase with themsfdbcommand with theinitoption:
root@kali:~# msfdb init Creating database user 'msf' Enter password for new role: Enter it again: Creating databases 'msf' and 'msf_test' Creating configuration file in /usr/share/metasploit-framework/config/database.yml Creating initial database schema
The msfdb command allows you to manage the Metasploit Framework database, not just initialize the database. To display all the msfdb options, run the command as follows:
root@kali:~# msfdb Manage a metasploit framework database msfdb init # initialize the database msfdb reinit # delete and reinitialize the database msfdb delete # delete database and stop using it msfdb start # start the database msfdb stop # stop the database
- To modify the database configuration file, we can edit the
database.ymlfile located in/usr/share/metasploit-framework/config/database.yml:
root@kali:~# cat /usr/share/metasploit-framework/config/database.yml development: adapter: postgresql database: msf username: msf password: 3HcNhAtdH6F9F2iGa4z3wJVoI7UK1Ot+MG1zuKjYzn4= host: localhost port: 5432 pool: 5 timeout: 5 production: adapter: postgresql database: msf username: msf password: 3HcNhAtdH6F9F2iGa4z3wJVoI7UK1Ot+MG1zuKjYzn4= host: localhost port: 5432 pool: 5 timeout: 5 test: adapter: postgresql database: msf_test username: msf password: 3HcNhAtdH6F9F2iGa4z3wJVoI7UK1Ot+MG1zuKjYzn4= host: localhost port: 5432 pool: 5 timeout: 5
Notice the default username, password, and default database that has been created. If necessary, you can also change these values according to your preference.
- Now, let's launch the
msfconsoleinterface and confirm that Metasploit is successfully connected to the database using thedb_statuscommand:
msf > db_status [*] postgresql connected to msf
To connect to a database manually, you can use the db_connect command followed by the credentials, host, and database you want to connect to, using the following syntax:
db_connect <user:pass>@<host:port>/<database>To test the db_connect command, we can use the values of the username, password, database name, and port number, from the database.yml file:
msf > db_disconnect msf > db_status [*] postgresql selected, no connection msf > db_connect msf:3HcNhAtdH6F9F2iGa4z3wJVoI7UK1Ot+MG1zuKjYzn4=@127.0.0.1/msf [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to msf
We can also use db_connect with the -y option and the path to the database configuration file:
msf > db_disconnect msf > db_status [*] postgresql selected, no connection msf > db_connect -y /usr/share/metasploit-framework/config/database.yml [*] Rebuilding the module cache in the background... msf > db_status [*] postgresql connected to msf
If you want the database to connect every time you launch msfconsole, copy the database configuration file to the .msf4 directory which was created in your home directory by the Metasploit installer.
Workspaces in Metasploit are used to separate datasets, allowing you to stay organized. It is a good idea to create a new workspace to organize all your collected data before starting a new penetration test, thereby avoiding contamination by previous tests.
- The default workspace is selected when connecting to the database, which is represented by the
*character before its name:
msf > workspace * default
- To display the usage for the
workspacecommand, use the-hoption as follows:
msf > workspace -h Usage: workspace List workspaces workspace -v List workspaces verbosely workspace [name] Switch workspace workspace -a [name] ... Add workspace(s) workspace -d [name] ... Delete workspace(s) workspace -D Delete all workspaces workspace -r <old> <new> Rename workspace workspace -h Show this help information
- To add a new workspace, use the
-aoption followed by the name of the workspace:
msf > workspace -a book [*] Added workspace: book
msf > workspace default * book
- To delete a workspace, use the
-doption followed by the name of the workspace:
msf > workspace -d book [*] Deleted workspace: book [*] Switched workspace: default
- To change the current workspace, use the
workspacecommand followed by the name of the workspace you want to change to:
msf > workspace book [*] Workspace: book
- To rename a workspace, use the
workspacecommand with the-roption followed by the old workspace name and the new workspace name:
msf > workspace -r book metasploit [*] Switched workspace: metasploit
Once the database is configured, we can start using it. First, we will take a look at how to import data from external tools using the db_import command.
To view how to use the command and list the currently supported file types in msfconsole, run the db_import command:
msf > db_import Usage: db_import <filename> [file2...] Filenames can be globs like *.xml, or **/*.xml which will search recursively Currently supported file types include: Acunetix Amap Log Amap Log -m Appscan Burp Session XML Burp Issue XML ... Qualys Asset XML Qualys Scan XML Retina XML Spiceworks CSV Export Wapiti XML
- To test the
db_importcommand, we will use thenmapcommand, a free security scanner, port scanner, and network exploration tool, with the-oXoption to save the result to an XML file. Here is the syntax used to scan the Metasploitable 3 target machine:
nmap -Pn -A -oX report 192.168.216.10- To import the scan report, you can use the
db_importcommand followed by the path to the report you want to import:
msf > db_import /root/report [*] Importing 'Nmap XML' data [*] Import: Parsing with 'Nokogiri v1.8.0'</strong> [*] Importing host 192.168.216.10 [*] Successfully imported /root/report
Alternatively, you can run the db_nmap command directly from msfconsole, and the results will be saved in your current database. The db_nmap command works the same way as the regular nmap command:
msf > db_nmap -Pn -A 192.168.216.129 [*] Nmap: Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-17 05:05 EDT [*] Nmap: Nmap scan report for 192.168.216.129 [*] Nmap: Host is up (0.00092s latency). [*] Nmap: Not shown: 977 closed ports [*] Nmap: PORT STATE SERVICE VERSION [*] Nmap: 21/tcp open ftp vsftpd 2.3.4 [*] Nmap: |_ftp-anon: Anonymous FTP login allowed (FTP code 230) [*] Nmap: | ftp-syst: [*] Nmap: | STAT: ... [*] Nmap: |_ System time: 2017-10-04T09:11:38-04:00 [*] Nmap: |_smb2-time: Protocol negotiation failed (SMB2) [*] Nmap: TRACEROUTE [*] Nmap: HOP RTT ADDRESS [*] Nmap: 1 0.92 ms 192.168.216.129 [*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . [*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 31.88 seconds
Now that we have data in the database, we can start by using the hosts command to display all the hosts stored in our current workspace:

- Issuing the
hostscommand with-hwill display the help menu:
msf > hosts -h Usage: hosts [ options ] [addr1 addr2 ...] OPTIONS: -a,--add Add the hosts instead of searching -d,--delete Delete the hosts instead of searching -c <col1,col2> Only show the given columns (see list below) -h,--help Show this help information -u,--up Only show hosts which are up -o <file> Send output to a file in csv format -O <column> Order rows by specified column number -R,--rhosts Set RHOSTS from the results of the search -S,--search Search string to filter by -i,--info Change the info of a host -n,--name Change the name of a host -m,--comment Change the comment of a host -t,--tag Add or specify a tag to a range of hosts Available columns: address, arch, comm, comments, created_at, cred_count, detected_arch, exploit_attempt_count, host_detail_count, info, mac, name, note_count, os_family, os_flavor, os_lang, os_name, os_sp, purpose, scope, service_count, state, updated_at, virtual_host, vuln_count, tags
- Using the
-coption, we can select which columns to display:


The services command allows us to display the services running on the hosts. To view the help for the services command, we can use the -h option:
msf > services -h Usage: services [-h] [-u] [-a] [-r <proto>] [-p <port1,port2>] [-s <name1,name2>] [-o <filename>] [addr1 addr2 ...] -a,--add Add the services instead of searching -d,--delete Delete the services instead of searching -c <col1,col2> Only show the given columns -h,--help Show this help information -s <name1,name2> Search for a list of service names -p <port1,port2> Search for a list of ports -r <protocol> Only show [tcp|udp] services -u,--up Only show services which are up -o <file> Send output to a file in csv format -O <column> Order rows by specified column number -R,--rhosts Set RHOSTS from the results of the search -S,--search Search string to filter by Available columns: created_at, info, name, port, proto, state, updated_at

- The
servicescommand allows us to filter the stored information with granularity, allowing us to search for a specific service name:

- Search for a port number as follows:

- Like the
hostscommand, we can use the-Soption to search for specific strings:
























