In this chapter, we are going to cover the key concepts of the penetration testing process, with particular reference to wireless penetration testing.
Penetration testing is the process of simulating attacks against a system or a network to point out its misconfigurations, weaknesses, or security vulnerabilities and their relative exploits that could be used by real attackers to gain access to the system or network.
The process of identifying and evaluating vulnerabilities is called vulnerability assessment and it is sometimes used as a synonym for penetration testing, but they are actually distinct processes; indeed, penetration testing generally includes vulnerability assessment and also the successive attack phase to practically exploit the vulnerabilities that are found. In some cases, depending on the scope of the penetration test, a full vulnerability assessment is not required as the penetration test may only focus on specific vulnerabilities to attack.
A penetration test can be external or internal. An external penetration test (sometimes also referred as a black box penetration test) tries to simulate a real external attack, with no prior information about the target systems and networks being given to penetration testers, while an internal penetration test (also referred as white box) is performed by penetration testers who are given access as insiders and try to exploit the network vulnerabilities to increase their privileges and do things they are not authorized to do, for example, launching man-in-the-middle attacks, as we will see in Chapter 7, Wireless Client Attacks.
In this book, we are mainly going to focus on external penetration testing.
The process of penetration testing can be divided into four main phases or stages, which are as follows:
Planning
Discovery
Attack
Reporting
A useful guideline for the penetration testing process and methodology that describes these phases in detail is the NIST CSRC SP800-115 Technical Guide to Information Security Testing and Assessment (see the reference section 1.1 of the appendix) at http://csrc.nist.gov/publications/nistpubs/800-115/SP800-115.pdf.
A scheme of the four phases penetration testing methodology is represented in the following diagram, taken from the preceding publication that was just referenced:
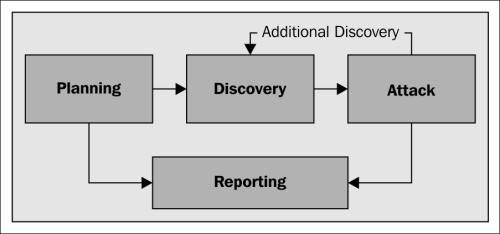
We are now going to explore each of the four phases.
The planning phase is a crucial part of penetration testing, though it is not always given the importance that it should have. In this phase, we define the scope and the so-called rules of engagement of a penetration test, as a result of an agreement between the penetration testers and the client that will be formalized in a contract between the two parties. It must be clear that a penetration tester should never operate without a contract or outside the scope and the rules of engagement established in the contract, because otherwise he/she could stumble into serious legal troubles. The scope is about which networks to test and the goals and objectives the client wants to achieve with the penetration test.
In this, we need to consider, for example, the area to scan for wireless networks, the coverage range of the signal of the networks to test, and their size in terms of the number of clients that will supposedly be connected. We also define the objectives of the test, such as specific vulnerabilities that should be assessed and their priorities; whether rogue and hidden access points should be enumerated and whether wireless attacks against clients should be conducted.
The rules of engagement include, among others, the estimated timeline and the days and times when to perform the test, the legal authorization from the client, the format of the report to produce, payment terms, and a nondisclosure agreement clause, according to which the results of the test are kept confidential by the testers.
Note
Worksheets for defining the scope and rules of engagement are available at the links provided with references 1.4 and 1.5 in the appendix (registration to the SANS Institute website is required).
Once the scope and rules of engagement are established, the penetration testing team defines the resources and the tools to employ for test execution.
In the discovery phase, we collect as much information as possible about the networks that are in the scope of the penetration test. This phase is also called the information gathering phase and it is very important because it precisely defines the targets of our test and allows to collect detailed information about them and to expose their potential vulnerabilities.
In particular, for our scope, we would collect information such as:
Hidden networks and rogue access points
Clients connected to the networks
The type of authentication used by the networks; we would like to find out networks, which are open or use WEP, and therefore, are vulnerable
The area outside of the organization's perimeter reachable by wireless signals
The discovery phase could be realized through two main types of wireless network scanning, active and passive. Active scanning implies sending out probe request packets to identify visible access points, while passive scanning means capturing and analyzing all wireless traffic and also allowing to uncover hidden access points.
We will see more about wireless scanning and how to use the wireless scanners included in Kali Linux, such as airmon, airodump, and Kismet, to carry out the discovery phase of wireless penetration testing in Chapter 3, WLAN Reconnaissance.
The attack phase is the most practical part of the penetration testing process, where we try to exploit the vulnerabilities identified in the discovery phase to gain access to the target networks.
This is called the exploitation subphase and in our case could involve attempting to crack authentication keys to connect to the network, setting up rogue and honeypot access points and directly attacking clients to recover the keys. The next stage (if required in the contract) is referred to as post-exploitation and involves attacking the network and the infrastructure after we have gained access to it, for example, taking control of the access points and performing man-in-the-middle attacks against the clients.
It is worth repeating that we should never conduct attacks that are not explicitly required in the contract. Moreover, the attack phase should be performed according to the terms and modalities established with the client, defined in the rules of engagement. For example, if the targets are production systems or networks, we could agree with the client to conduct such attacks outside the working hours, as wireless connectivity and the services provided may be disrupted.
We will cover the attack phase from Chapter 4, WEP Cracking to Chapter 7, Wireless Client Attacks.
Reporting is the final phase of penetration testing. The previous phases are very important because they are where we plan and execute the test but it is still important to communicate its results and findings in an effective manner to the client. The report is useful as a reference point for defining countermeasures and mitigation activities to address the identified vulnerabilities. It is usually formed by two major sections, the executive summary and the technical report.
The executive summary is a high-level summary of the objectives, methods and findings of the test and it is mainly intended for the non-technical management. Thus, the summary should be written in a clear language and using an understandable terminology, avoiding too many technical terms and expressions.
The executive summary should include:
A description of the objectives of the test
An overview and description of the issues found
A definition of the security risk profile of the client organization
A plan for the remediation of the vulnerabilities found and to mitigate the risk
Recommendations to improve the organization's security posture
The technical report includes an in-depth description of the penetration test and detailed information about the findings of the discovery and attack phases, as well as an assessment of the risk that the identified vulnerabilities entail for the client and a plan for risk mitigation. Thus, the technical report covers the same as the executive summary but from a technical point of view and it is addressed mainly to IT executives that should then apply the remediation activities provided in the report.
We will cover the reporting phase in Chapter 8, Reporting and Conclusions.
In this chapter, we introduced wireless penetration testing and provided a brief description of the four main phases in which it is divided: planning, discovery, attack, and reporting.
In the next chapter, we will see how to install Kali Linux on your computer and we will examine the requisites that your wireless adapter must meet to get started with wireless penetration testing.





















