Introduction to Social Engineering
In any battle, there is no better knowledge than knowing about the enemy's tactics. This chapter will introduce you to the world of social engineering and look at what social engineering is all about. Social engineering is a set of techniques that are widely being used in cyberattacks to orchestrate some of the most successful attacks. Social engineering uniquely targets a weak component in the cybersecurity chain—the user. Unlike systems and networks, users cannot be protected from social engineering by means of expensive tools, such as firewalls and antivirus programs. They are always in the open and they are always giving out information that can be used by attackers to hit them when least expected. People also have the higher return on investment compared to systems. Within an hour, a social engineering expert can make away with as much information as it would have taken him or her 100 hours to gather trying to attack a protected system directly. Attackers are aware of the current sophistication of the security elements that protect systems. Most organizations use multiple layers of security. Even if one is compromised, the hacker cannot get past the others easily. It has, therefore, become harder to try to attack the systems themselves. At the same time, hackers are discovering that it is easy to hack today's users and this has been confirmed by the rising number of mediated social engineering attacks. This chapter will give an overview of social engineering. It will cover the following topics:
- Elicitation
- Pretexting
- Mind tricks
- Persuasion
- Tools used in social engineering
Overview of social engineering
One of the biggest cyber attacks of the century happened on Yahoo!, where it is believed that attackers were able to breach its systems in 2014 and make away with the account details of over 500 million users. The FBI has confirmed that social engineering was used in the attack to get the attackers past the scrutiny of the layers upon layers of security tools and systems used to protect such data. This attack on Yahoo!, a giant tech company, therefore confirms that social engineering is more dangerous than it's given credit for. No one is secure if one of the oldest email service providers that invests heavily in cyber security tools can be compromised so easily using this technique.
Social engineers have also been able to make away with huge sums of money using simple social engineering attacks. In 2015, a company called Ubiquiti Networks, which makes networking equipment, was hit by a social engineering technique. The attackers were able to collect information about the CEO and effectively assume his personality. They used this impersonation to direct the finance department to channel huge amounts of money to some overseas company that had informed him of a change in their payment preferences. Without question, a finance department member of staff transferred the money only to discover later on that the orders did not come from the real CEO and that the attackers had already made away with millions of the organization's hard-earned money. Further investigations revealed that the security systems were still in place and not compromised and the theft was only done through a social engineering con.
Both these incident emphasize the fact that human weakness cannot be discounted in the cyber security chain. It is fast becoming the widely used method for attacking organizations:

Today's cybercriminals are fortunate since users are exposing themselves to social engineering attacks. The rise of the use of social media platforms has been a key contributing factor to the increased number of social engineering attacks. This is because today's users are living their lives on social media and giving details about their daily lives, family, workplace, personal preferences, and so on that can all be used for a social engineering attack. An attacker needs only to go through a user's social media accounts to get enough information to stage a successful social engineering attack. There is more than enough information on Facebook, Twitter, Instagram, and Snapchat to enable a social engineer to assume the personality of most users. It is also surprisingly easy to create a fake social media account of a senior executive. This account commands instant respect and compliance with any orders issued to a target and can thus be used to rake money from junior employees at an organization.
Another method used on social media has been the creation of honeypot accounts of non-existent people that are used to attack real people. In July 2017, a senior IT operations employee at a Middle Eastern Telecommunications Company (METCO) escaped by a whisker shortly after approving a friend request from a honeypot account. The attack seems to have been highly targeted at, a male amateur photographer. This is because the attackers had created an attractive profile of a young girl called Mia that said she was an upcoming photographer in London and she shared very many hobbies with the target. The target was obviously quick to accept the friend request believing that they had a strong connection. After a few weeks of chats, Mia sent the man a photography survey. Unknown to the IT staffer, the survey was a file that contained a malware called Pupy RAT, which is used to steal login credentials when it is opened. Luckily, the company's computer was secured with effective end-host antivirus programs that quickly detected and disinfected the malware before any damage was done. Further investigations were able to reveal the hacking group behind the attempted social engineering attack. It was confirmed that the group had previously tried to attack the company using phishing emails but none were successful. The employees had been educated about fake emails and clicking on suspicious links or opening email attachments. It seems that the hacking group was able to come up with the social engineering attack and target one employee through Facebook.
This incident confirms that users, irrespective of the departments that they work in, are prone to social engineering attacks. The target here was IT-knowledgeable and yet the guise of a young, attractive lady who shared his interests was able to get his guard down. He opened a file inside the organization's network that could have stolen login credentials or even spread through the network and infected other computers. If a stronger malware had been used, the attack would probably have gone through. Users are all faced with the same weaknesses when it comes to social engineering. All it takes is for the attacker to find the weak spots in one personality. This could be blind obedience to any authority, loneliness, financial needs, or investment needs among others.
Okenyi and Thomas conducted a study on the anatomy of human hacking, which can be translated to social engineering.
They said that humans are always open to being manipulated by social engineers; all it takes are the right knobs to be turned. They found out that humans were obedient to authority above them and were thus ready to execute commands passed down from their superiors. This is a weakness that social engineers use frequently to try and pass down malicious commands using fake profiles of senior management staff at an organization. The two authors also came to the realization that humans are sympathetic to and trustful of strangers. Humans are caring and are willing to help strangers and this puts them in the unfortunate spot of being able to be manipulated by common crooks. Courtesy, trust, and sympathy have been used to get people to give out details to hackers on their personal devices containing very sensitive data. These hackers are able then to install malware or copy the sensitive data before the target is aware of this. Women, especially pregnant or disabled women, have been used to get targets to give out their device's details only for malware to be planted or data to be copied or wiped off. The authors discovered that humans are always interested in certain rewards and are willing to take actions that will supposedly earn them rewards.
A commonly used phishing tactic is to tell users that they stand the chance of winning hefty prizes if they click on certain links. Many people want the prizes and will, therefore, click on links supposedly leading them to giveaway pages only to find that the links lead to malicious websites. Humans also have a sense of guilt, a desire to please, and feelings of moral duty. These are among the psychological issues that will be discussed in the forthcoming chapters.
It is good to understand that social engineering is not generally a bad practice; it has both good and malicious applications. It is effective both ways because the targets share the same characteristics previously detailed and thus are always open to attack. Social engineering plays a key role in society; it enables people to get favors. Regardless of whether they are good or bad, it gets people to make decisions favorable to the person requesting them. It is only that social engineering is now being used by the bad guys to commit huge crimes. The framework of the tactics used for manipulating people during criminal acts is the same as that used for positive outcomes. The weaknesses being exploited are relatively the same and all humans share them.
One of the oldest social engineering scams is the Nigerian scam. It might have been the first widely successful social engineering attack mediated by email technology. Since it came up in the early days of emails, many people fell for it. Attackers pretended to be a well-off Nigerian prince that had a lucrative deal that only needed a target to offer some help and get a big cut. The con was executed when the targets were being asked to resolve certain problems by paying some cash in order to have a large payout released to them. The problems kept on coming until a target would eventually realize that there was no money to be released. A few human characteristics were being exploited in this attack which are discussed as follows:
- The first one is greed where targets were made to believe that they would indeed get a big cut from a huge fortune. Everyone wants money and, if it comes so easily, then many people will be willing to do what is being asked. It is not a strange characteristic that was only present in the victim; it is a characteristic present in everyone.
- Another characteristic exploited was commitment. Humans naturally want to see things to the end. This is the reason why the attackers discovered that they could fleece people of money by assuring them that the sooner they make the payment, the sooner the payout would be released. Again, it is a characteristic present in everyone.
- The last characteristic is trust and it was the core part of the attack. Strangers were being manipulated to trust another stranger on another continent and believe that all they were told was true. Trust is powerful and the strangers were quick to give the supposed Nigerian prince the benefit of the doubt when an error occurred in the processing of the payout. Exploiting three human weaknesses at once, the attack was very powerful and some people ended up losing as much as $50,000.
The following is an example of spam email:
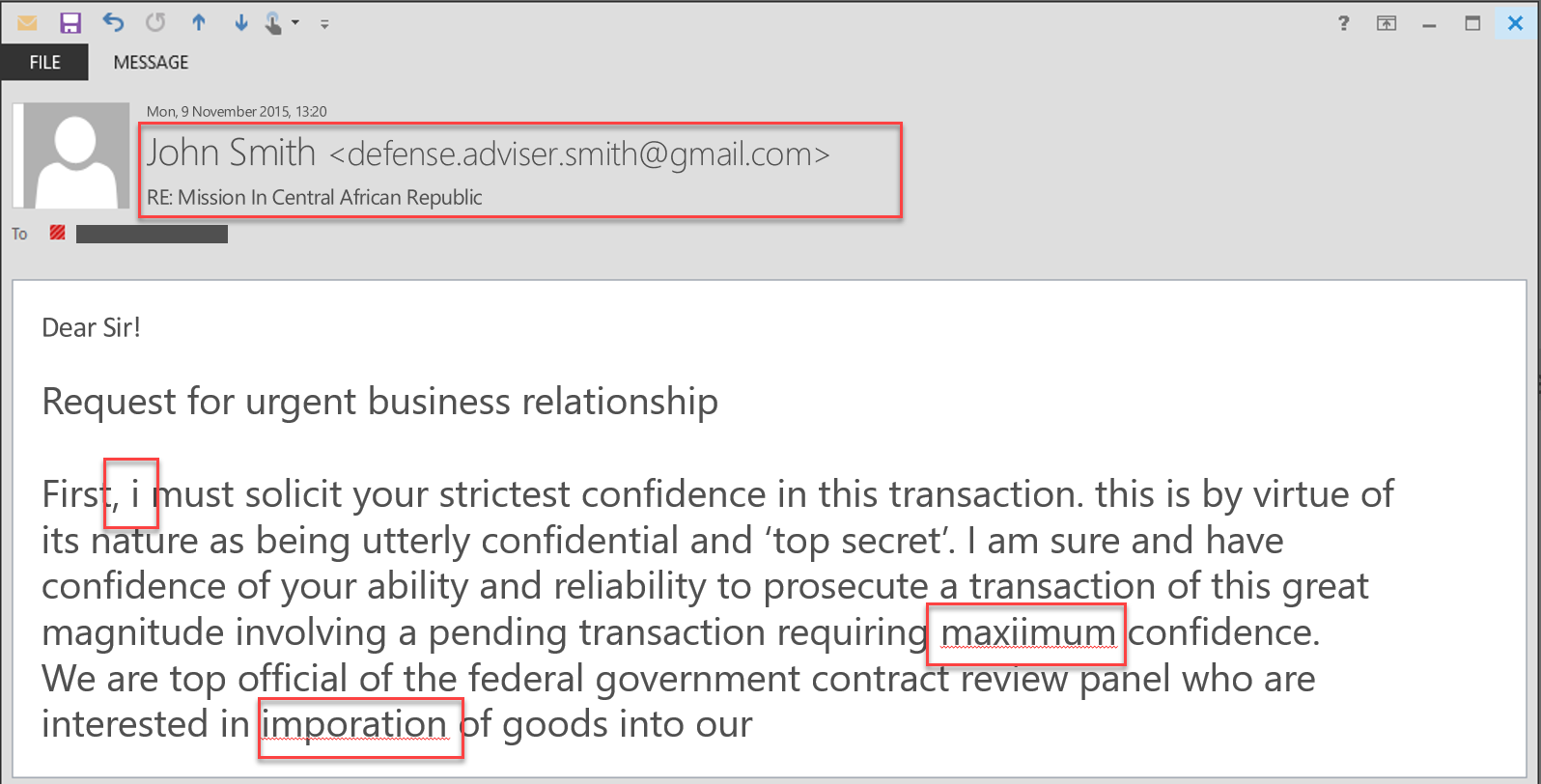
The preceding instance describes a well-structured social engineering attack that exploits human characteristics for malicious purposes. It is important to note that the same characteristics are used for positive outcomes. Trust is used every day in agreements or when making transactions and it is only in unfortunate scenarios that it is used maliciously. Commitment is used in almost all undertakings to ensure that they are successfully completed. Humans get a certain internal reward for completing tasks and are therefore committed to seeing through everything they start.
Greed is not necessarily a bad characteristic either. It is only human to be subtly greedy. Money is sought after and it is subtle greed that allows people to seek for it in all possible ways. It is therefore, only during unfortunate scenarios that these characteristics are exploited for malicious purposes.
Consider the following figure based on Verizon's Data Breach report, 2015:
Applications of social engineering
Social engineering is actually used in many setups and professions by people and institutions, discussed here as follows:
- Lawyers and psychologists: These groups of people have to get people into a certain state of mind to manipulate their minds. They use the same tactics as any other social engineer would use. It is just that they use them with non-malicious intentions. Through these tactics, they are able to conduct successful interrogations and interviews and get people to reveal information that they would otherwise withhold.
- Governments: Governments have to use social engineering to have control over the people that they govern. One of the key ways of social engineering people is by using authority. Governments are in control of most of the authority in the country and human brains are conditioned to adhere to authority. Another way is by using scarcity. If it is not there, governments will create scarcity so that they can retain the perception in people's minds that they (governments) are the ones still in charge. Scarcity can be of many things, such as information, money, or even food. In countries such as North Korea, food and information scarcity is abused by the regime in power to keep people obedient.
- Salespeople: They have mastered the art of convincing people to buy things including those that they have no need for. Salespeople are good social engineers since they are good at using multiple people skills to elicit demand for their products from potential customers. Today, salespeople are leveraging technology to assist them with information gathering and influencing people to buy certain products. Social engineering is playing a key role in all this.
- Recruiters: The human resource (HR) departments in most organizations are occupied by expert social engineers. Recruiters have mastered the art of reading people's minds to find out what really drives them and their suitability for advertised positions. Social engineering is used to get applicants to open up and divulge information that could help HR determine whether or not to hire them.
- Spies: Spies are extensively taught special social engineering techniques that they employ to fool people into believing that they are the people they have been posted as. They are also taught how to use social engineering tactics to collect intelligence from unsuspecting people. Spies can easily get confessions from hardcore criminals due to social engineering. Even when compromised, they can recover their secret identities using social engineering. Social engineering means survival for them and they are therefore extremely good at it.
- Scammers: Scams are mostly made possible by social engineering. A con artist must know how to attract people into buying a con without question. Con artists identify their marks from afar and study them over time. They pick up critical cues about their marks until they have enough information to hit them. Scammers have perfected the art of creating certain scenarios that are irresistible to their marks. It is through social engineering that all this is made possible.
- Identity thieves: Identity theft is a crime bigger than just stealing someone's name, bank account, address, and financial details. An identity thief at times has to become the person that he or she has stolen an identity from in order to commit a bigger crime that has higher returns. This is where social engineering comes into play. An identity thief will use different tactics to get along with people in the life of the victim. An identity thief will exploit the status of the victim's profile to get favors done for him. If the identity that has been stolen is of a senior staff member at an organization, the identity thief could use authority to coerce finance employees to make some unverified payments. Identity theft is highly supported by social engineering.
All these people use social engineering in both positive and negative ways. However, the focus of this book is social engineering for malicious purposes. It is a major concern for many people, organizations, and governments. It has made many lose faith in the protection of their systems.
The social engineering framework
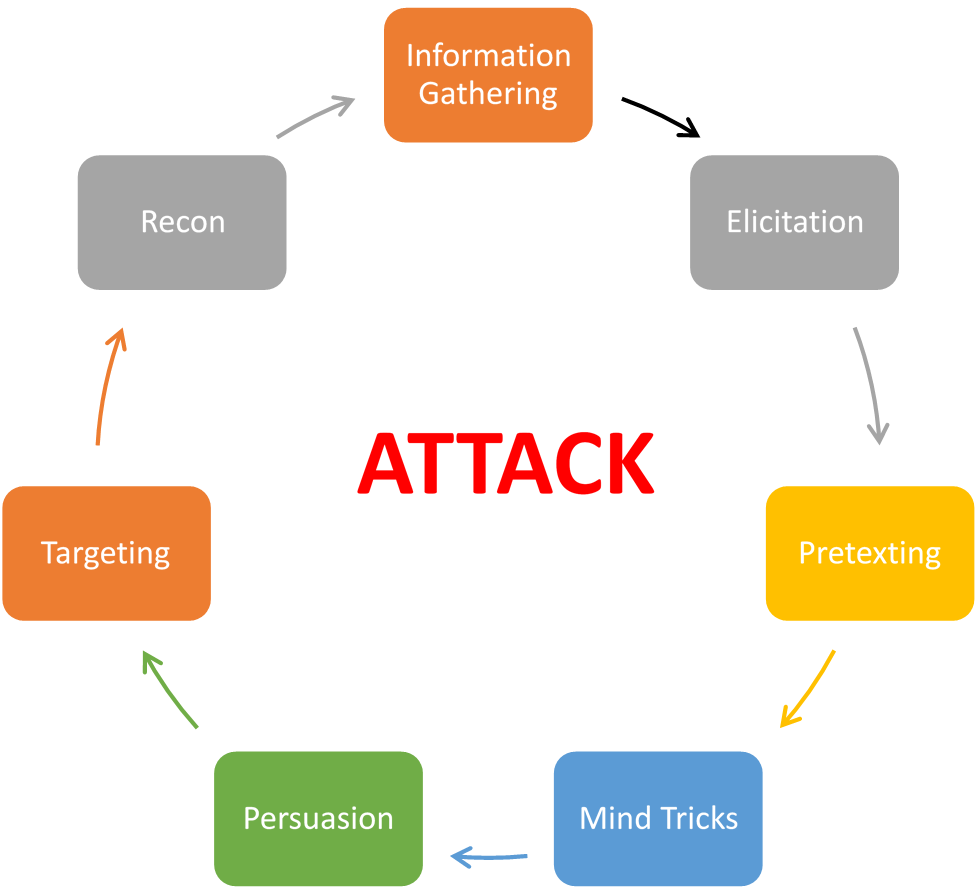
In any successful social engineering attack, a certain framework is followed. The framework has seven discrete steps that guide a social engineer on a path towards knowing more about the target, choosing an attack strategy, and then executing it meticulously. The framework is as follows:
Information gathering
This is regarded as the most tortuous step in the whole social engineering exercise and may last anywhere from a few hours to a few years. Not only is it long, it is demanding and requires an attacker to always be keen in observing the target. Today's social engineer needs to be well-informed of the data to look for and the software tools that can help with this. The quick adoption of social media platforms by a large percentage of people has made this process somewhat simpler. However, this data is at times insufficient or too fabricated to be of help and therefore, more data sources may be required. An attacker may, therefore, be forced to gather data using specialized software tools or using soft skills to get this data directly from the target without raising alarm.
Information is rarely gathered all at once. Doing so is hard and therefore it is common for a social engineer to collect small pieces of data and combine them to complete a puzzle about the target. For instance, if gathering information about a CEO, an attacker may start by interviewing people that the CEO comes across or talks to. Janitors, secretaries, subordinates, or even visitors may be interviewed to find out small pieces of information that may not be so useful discretely, but very powerful when put together. Even the most insignificant of people that a target interacts with may have a key to unlocking a much larger puzzle. Therefore, any source of information is treated as valuable.
There are two main methods of data gathering that can be employed by an attacker—nontechnical and technical methods.
Nontechnical
These methods disregard the use of any technological means to collect data. They may be more tiresome but they are most likely to find more accurate data about the target. The non-technical methods are discussed as follows:
- Dumpster diving: This involves going through the paper waste of a target to find out valuable information that may have been disposed of. Even with paper shredders, humans are still lazy enough to carelessly throw away some valuable data that attackers may find by dumpster diving.
- Physically tailing a target: This gives the attacker information about the target's routines, schedules, likes, dislikes, and so on. The end game involves approaching the target with some questions and then presenting offers that they cannot refuse. With this, a social engineer can potentially get a ton of information and access to restricted places. The rationalization of a target, once figured out, can be abused to get a lot more. Non-technical methods are, however, being phased out and today most information gathering is done through technical methods:
Technical
These methods include the use of technological products for obtaining information about the client. One of these methods is by stalking the target on their social media accounts. Most targets will have active profiles on LinkedIn, Facebook, Twitter, Instagram, or Snapchat. Users on these platforms are so careless with their data that social engineers need not look far in many instances. Even after repeated warnings for people to change their privacy settings, it is more likely than not that the target's account will be visible to the public and thus anyone. Users have put out their entire lives to strangers and anything that can get a like is likely to be posted. Information that was once private is now put indiscriminately on public domains. This makes it even easier for a social engineer to collect the data available about the target. However, in some instances, the attacker might not be so fortunate either because the data given is too little or the account is set as private. This, therefore, requires the social engineer to create a fake account that matches the preferences and likes of the target. With this, a client may request the target to either become friends or follow them. Another common approach has been through the use of a fake account created in the name of someone known to the target. Close friends, relatives, and bosses at work have been used in many social engineering attacks with a high success rate.
The second commonly used technical social engineering method is a search on search engines. Search engines index many sites and some of these store user information collected from many sources and pooled together at a central place. There are special Google queries that can be used to mine information about people contained on websites. These will be discussed in detail in the next chapter about data gathering. An example is the following query:
"David Wilson" intitle:"curriculum vitae" "phone" "address" "email""
This is a very powerful query that can be used to unearth any information about a person called David Wilson. The query will make Google look for any website that has an entry by the name David Wilson and has titles such as curriculum vitae, phone, and address:

Many job boards that keep the data of job seekers keep the job seekers information in the public domain. Therefore, it will be easy to find a person called David Wilson from where personal details can be retrieved. This query might even bring up the resume of David Wilson if there is a site that has kept information about it:

A site known as Pipl (https://pipl.com) is one of the largest archives of information about a large number of people. For each person it has on its database, the site keeps the person's email address, social media accounts, phone number, and physical address. The site claims to have details of over three billion people:

It is fast approaching half the human population on earth. This site is a goldmine for social engineers as they can find out rather personal information about their targets without much hassle. There are many other sites like it dishing out private information about people to anyone that requests such information. These sites have a wide source for these records, which include social platforms, data sold by third parties, data released by hackers, data stolen from other websites, and data in government agency websites. They keep updating their data as often as their sources can. Unfortunately, such sites are not illegal and therefore it is hard for anyone to compel such sites to have their data removed.
Another technical source of information that is still in use by social engineers is the use of telephones. This is commonly targeted at older people since they are easy to fool. The callers always claim to be from reputable companies or government agencies. They use enticing offers or grave threats to get the targets to send them some cash. There are reports of some callers that claim to be the police and threaten to arrest the targets if they do not send some amount of money within a certain period. Other people are also targeted and the greatest asset that social engineers have is some information about the target. Just knowing a target's bank account could be enough incentive to get the client to trust that it is the bank calling. They can use a bank account number to get the target to reveal even more data including social security numbers. When the targets come to the realization that it might not be the bank calling, it is normally too late. The social engineers will have enough information to plot an attack.
Data gathering is indeed tedious, lengthy, and tasking. It is, however, worth it. The amount of information gathered from the targets is vital in the planning of an attack. The best data gathering method is one that does not preempt the motive of the social engineer. Therefore, data gathering is done discreetly. Small chunks of information are pulled bit by bit and pooled together. With time, the social engineer will have more than enough information to profile a target. The social engineer will know more about a target's life than the target's family or spouse. This is the information that will determine the success of an attack. There are very many other data-gathering methods and tools that are used in this process. The ones that have been discussed have also not been discussed in depth. These will, however, be discussed in the following topic about data gathering. The chapter will identify all the methods and tools, describe them, and give examples of the use of each. At the end of the chapter, one will be proficient at collecting data about targets exactly as a social engineer does.
Elicitation
Even with their weaknesses, humans will generally be withdrawn at first about confiding with anyone. It takes skills to be able to break people from their security comfort zones so that they can start spewing out private information. Elicitation is more than building rapport with strangers; it's a technique used in interrogation rooms, used by therapists, and by doctors to get information from people that would otherwise withhold such information. Elicitation, therefore, is the second step in the social engineering framework that is followed during social engineering attacks. The attackers use elicitation techniques after gathering enough information about a target to initialize a conversation.
Elicitation can be defined as the act of drawing something out using logic. It is done through stimulation to get one to act in a certain class of behaviors. The definition, therefore, means that elicitation is the ability to draw out people from their security comfort zones by stimulating them to act in a certain way. A social engineer will have mastered the art of elicitation to a point where they can bring a target to a point of just wanting to respond truthfully to any question posed. Spies and interrogators are trained in how to use this skill to draw information during normal conversations. This shows that it is already a skill valued by governments. It is difficult for a target to detect an elicitation attempt. It appears so innocent and occurs in normal settings. The following are some of the factors that make elicitation so effective:
- Most humans will try to be polite when talking to a stranger
- Professionals, when questioned, will want to appear knowledgeable
- Most people would not lie to someone who appears genuinely concerned
- It is more likely than not for someone to respond to well-posed questions about themselves
In elicitation, a social engineer will be looking to tie a target into a certain path so that they openly share sensitive information without second thoughts. It is presented as a simple question-answer interaction while in a real sense, the target is conned into divulging secretive information. The social engineer will try to keep the target compliant with answering some questions that may be uncomfortable in the first place. The target will keep on answering them as long as the social engineer plays their cards right. When it comes to playing their cards right, there are a number of things that a social engineer is strict about. These are as follows:
- Being natural: One of the best ways to keep a conversation going without raising eyebrows is by keeping the target comfortable by sounding genuine and natural. It is easy to spook a target if the conversation appears to be unnatural or scripted. Therefore, a social engineer will engage a target in a conversation that he/she (the social engineer) is conversant with. The social engineer will also work on his or her posture, body language, and assertion of knowledge. Everything has to be made to look perfectly normal so that the social engineer appears confident and natural. It is common for social engineers to role-play with their friends so as to get their act together before making the actual elicitation attempt.
- Being knowledgeable: Knowledge is the perfect shield for a social engineer during their interaction with a target. Therefore, whatever questions one will have for the target, he or she must be knowledgeable about their expected response. This will allow the social engineer either to acknowledge or differ with the target using some knowledge and this will keep the conversation going. Of course, the social engineer is not expected to be very knowledgeable about the responses to be given; this might raise a red flag. All that is needed is the basic knowledge to be able to give follow-up questions and to respond to the answers given by the target.
- Avoiding greed: Social engineers need to ensure that they do not appear to be greedy to their targets. If it becomes evident to the target that the social engineer is after particular information, the target will most likely shut off the social engineer. Therefore, a common practice is for the social engineer to practice give and take. The social engineer comes up with fake information and offers it to the target. Upon seeing this openness, the target reciprocates by giving out some information, but, in this case, it happens to be factual information.
These three are the essential cards that any social engineer needs to have up his or her sleeves when interacting with a target. Apart from this, it is very important for the social engineer to use the correct facial expressions at the right time. There are some expressions that are hard to fake and therefore require the social engineer to do extensive trials to get them right. Facial expressions affect the way that people respond to questions. Therefore, the social engineer needs to employ expressions that show interest and uplift the mood of the target if necessary. Facial expressions say a lot and can potentially affect the outcome of an elicitation attempt. In any case, the social engineer needs to be able to appear really into the conversation.
Elicitation is a core step in social engineering. There are several proven elicitation skills. These and the ones already highlighted will be discussed further in the Chapter 6, Elicitation of the book. The chapter will train a newbie on how to master the art of elicitation to the point of a professional. The knowledge gained will be applicable in and out of social engineering.
Pretexting
This is normally the third step in a social engineering attack. It is where the attacker becomes anyone in a position to influence the target into making some decisions. The attacker chooses a certain personality that befits the character he or she opts to become during the social engineering attempt. With the advent of the internet, it is easy to become anyone.
There are so many information resources that a social engineer can use to adapt the character of anyone. Pretexting is an imperative skill that any social engineer needs in order to accomplish an attack. Pretexting is more than just acting the role of a person; it can be considered as becoming the person. There should not be an iota of doubt to the target that the social engineer is not the person he or she claims to be. The social engineer's character, their manner of speech, body language, and any other noticeable characteristic must fit that of the person he or she is pretending to be. It is a vital skill that will allow a social engineer to carry out an attack unsuspected.
There are very many dynamics involved when it comes to pretexting. They ensure that a social engineer is able to invent a scenario and get the target to take some actions or release some sensitive information. In most recent attacks, social engineers have been noted increasingly to use people in certain highly respected jobs or the profiles of senior employees in some organizations. Social engineers are willing to put an adequate amount of time to research the roles that they will take with their new personalities. They train until they get to a point where they are perfect clones of the people that they want to impersonate. They can then use these impersonations to persuade their targets into doing what they want them to easily.
Pretexting is highly effective and it is commonly used in other fields. Doctors, lawyers, and even therapists have some sort of pretexting techniques whenever they interact with people in their professional lives. They are able to get people into a comfort zone where they release information that they have been holding back. Social engineers work towards achieving the same amount of persuasion and trust in their pretexting attempts.
In the previous discussion about information gathering, it was noted that information gathering is a key determinant of the success of the whole social engineering attack. This is one of the stages where the information gathered counts. Social engineers must be careful to use pretexts that they are absolutely sure that a target will fall for. If in an unfortunate event a social engineer uses a pretext that the target cannot relate to, the entire attack is sabotaged. For instance, if a target uses Bank B and a social engineer calls saying that he is an official from Bank A, the target will know that this is a setup and the attack will fail. Moreover, the target will be so spooked that not even another attempt will get him or her to fall for the con. There is little that a social engineer can do once the target realizes that he or she is being targeted by attackers. The only advisable thing is to bail out and abandon the whole attack.
Therefore, it is extremely important for the pretext attempt to be successful. There are some general principles that are followed in pretexting, including the following:
- Research more: There are better chances for a pretexting attempt if the social engineer has done adequate research. The target might start asking some questions and it is extremely important for the social engineer to have some information that can be used to answer them according to the knowledge expected of his or her impersonated personality.
- Use personal interests: Pretexting puts a person in the skin of another and this is a very challenging task. There are some things that one cannot easily fake. That is why social engineers may divert a little bit from the personalities of the people they pretend to be and use their actual interests. Nothing can be as disastrous as a shameful discovery that a social engineer is not knowledgeable about any of the interests he or she conveys to a target. It is better to correct an assumption by the target of certain personal interests than to play along only to get to a point where the target starts having doubts. It is good for self-confidence and for the sake of trust building that the social engineer uses interests he or she is conversant with when building rapport with a target.
- Practice expressions or dialects: It is easy for a target to know that a person is not who he or she claims to be just by keenly listening to the dialect or expression. There are some jargons present in some professional fields and these help to solder the assumption by the target that the social engineer is indeed the person he or she claims to be. Plain talk might not be so assuring to a target about the personality taken by the social engineer. If the social engineer assumes the personality of a lawyer, for instance, there should be some level of legal jargon, such as the mention of some laws, bills, or penalties for certain crimes. This will quickly build up the belief by the client that the social engineer is a real lawyer. Therefore, dialects are very important in pretexting and social engineers usually pay lots of attention to them.
- Use simpler pretexts: The more complex a pretext becomes, the less chance it has of being successful. This is because it will take more research and effort to maintain it and it might end up failing. A simpler pretext, on the other hand, will be quicker and easier to perfect and this means that there will be higher chances of the target falling for it. Therefore, only legendary social engineers have the option of choosing complex pretexts since they have more knowledge and experience in handling such pretexts. This also means that there are many low-level social engineering attacks that can easily be staged. From the victim's side, it is more likely that one will be approached with the pretext of an old friend, a relative, or an old classmate. They are easy to fake.
- Logical conclusions: Social engineering attacks are well-coordinated. From the point of elicitation to the pretext stage, there should be a general pattern followed. The steps must be logical. In the pretext stage, information provided at the beginning must match with what the social engineer wants. A pretext of a lawyer cannot, for instance, be used to get a target to reveal work login credentials. The pretext should logically bring a target to a certain conclusion. An IT support officer pretext can be used easily to persuade a target to give out login credentials. A target could be told that there are some systems that have encountered some problems and the company is switching to backup systems and therefore the old credentials are required to facilitate the migration. This scenario has a logical conclusion. It is more likely to work than if a pretext of a lawyer is used to acquire the same information. There will be no connection and it will be hard for the target to connect the dots and give out the required information.
There are many other principles that social engineers use. These will be discussed in-depth in the Chapter 7, Pretexting. In summary, pretexting is very challenging and many social engineering attempts can fail at this stage. From a defense perspective, users should be taught about how to question suspected social engineers in order to foil attacks at this point. Pretexting is more than assuming a falsified identity; it is more of living that identity. It is difficult but if it is successful, the social engineering attack will have been plotted on the right course. There are several tools used in this step and they will be discussed in this chapter.
Mind tricks
The whole social engineering attack is based on mind tricks so this is a step that is used in many of the other parts of the social engineering attack framework. This part of the social engineering attack involves the use of specially crafted tricks to alter the thought patterns of victims. Mind tricks are used to some degree in many other areas in life, such as in sales to make product prices appear less costly and in interrogation rooms to make suspects take a plea. Mind tricks are more of a psychological affair and they are used to unlock the minds of the targets exposing them to the control of the social engineer. An excellent social engineer is a good mind reader and this is achieved by mastering a number of mind tricks.
Mind tricks begin with a rapport. It is the primal effort used to gain the trust and confidence of the targets. From there, the social engineer uses several tricks aimed at altering the normal thinking of the target's brain. It can only be likened to a hacking technique called buffer overflow. This is where a program is supplied with more data than it can contain in its buffers. Consequently, the program begins behaving erratically due to the overflow of information. The human brain can have its reasoning capacity similarly overwhelmed, opening it to manipulation from social engineers. There are three modes of thinking that can be exploited in a human, as shall be seen in Chapter 2, The Psychology of Social Engineering - Mind Tricks Used. These are as follows:
- Visual thinking: Visual thinkers are people that process information visually. They are good at picturing things and their decision making is normally based on the overall image that they create in their brains. Visual thinkers are therefore targeted with things that are visually appealing rather than those that are necessarily beneficial to them. Men tend to be majorly visual thinkers and that is why their products are made to be visually appealing in adverts. To get into the minds of visual thinkers, social engineers also focus on giving them visual inputs.
- Auditory thinking: Auditory thinkers are very good at reasoning from the sound of things. They are easily won over by voices since they are biased on how they process information from different sounds. They are easily touched by sounds and they easily create memories using them. It is good to note that they must not necessarily be talked to physically. They can be put into a state of thinking where they can assume a certain voice as they read through any text. They are more concerned with the careful selection of words and will pay very little attention to low-effort word choices.
- Kinesthetic thinking: Kinesthetic thinkers are emotional thinkers and they connect to emotions brought out from a conversation. They become warm if a conversation is warm, sympathetic if a conversation relates sorrowful ordeals, alongside many other emotions. Their emotions are up for grabs whenever they engage in a conversation and this puts them at a major disadvantage since emotions tend to be very powerful. Emotions can be used to make them change their decisions abruptly without any questions. Women majorly fall into this category where their emotions can be easily swayed.
These are the three basic modes of thinking that are present in humans. It should be noted that humans are not generally tied to a particular mode of thinking. They could have all three modes of thinking but one will be more dominant over the others. This is the mode of thinking that a social engineer will be looking for. Upon discovering it, the rest will be child's play. It will be very easy to come up with the scenarios that will make the target forfeit normal reasoning and act as the social engineer would wish.
The biggest hurdle is always discerning the dominant method of thinking. This calls for a conversation from which the social engineer can try out different contexts of stories and see whether they evoke the dominant sense in the target.
A visual thinker can be determined by the use of visual questions and comments. If the target seems to respond in kind, citing more visual aspects, it can be concluded that he or she is a visual thinker. A kinesthetic thinker, on the other hand, can be determined by the use of touching stories. He or she can also be determined by the willingness to touch and feel things. Therefore, if a target is eager to touch and feel a cloth or a watch, most likely he or she is a kinesthetic thinker. Similarly, if small stories filled with emotions seem to move the target, it can be said that the target is a kinesthetic thinker. A dominantly auditory thinker can be determined by observing his or her reactions when listening to or reading something. Those that hardly flinch are non-auditory thinkers. On the other hand, those that seem to be connecting to the words spoken or written are auditory thinkers.
The topic of mind tricks is very long and it will be looked at in more depth in the Chapter 2, The Psychology of Social Engineering - Mind Tricks Used. However, it is important to note that mind tricks are not a science. They rely on active adjustments on the social engineer's part. The discussed modes of thinking, for example, are not easy to determine. The only thing that a social engineer can do is observe as much as possible. The use of questions to discover one's mode of thinking can be irritating and off-putting. Therefore, the best weapon is observation. There are very many other things tied to thinking that will be discussed in the chapter. As was mentioned, mind tricks tend to be cross-cutting all the steps in the social engineering framework. They are not reserved for a certain event; they are brought in to play the moment a social engineering attack begins. Information gathering, elicitation, and pretexting are used to build up a more open stage for them to be employed. They are vital in the social engineering attack since they can make it shorter and more successful. After conquering the target's mind, the attack is as good as done. This interesting topic will be discussed in a future chapter.
Persuasion
Just like mind tricks, persuasion is a cross-cutting topic in the whole of the social engineering process and thus cannot be constrained to a certain step. To persuade a target, a social engineer needs to appeal to the target's interests first. Persuasion gets targets to react, think, and do exactly as the social engineer wants.
Persuasion leads to unquestionable influence in the minds of the targets. So that the attack is successful, social engineers perfect their persuasion skills. They make sure that the influence they have on the targets is undetectable but far-reaching. Persuasion can be best understood through the five fundamentals used by social engineers to instill it in the target's mind in the first place. They include:
- Clear goals: This is defined so that a target may helplessly fall under the control of the social engineer; he or she must appear to be having clear goals during engagements. It all comes down to the saying that if you focus on something, you are likely to become it. A social engineer will have clear goals already set up and they will all be logically structured. The goals should facilitate the achievement of the goals following them. Therefore, in any engagement that the social engineer will have with the target, say bumping into them in a coffee shop, there will already be a predefined goal and the achievement of this goal will facilitate the achievement of another goal. No goal is solitary; if it is, it can be ignored since it will not affect the success of the attack.
- Rapport: Rapport is built to ensure that the target trusts the social engineer. To build a rapport that will allow the social engineer to be persuasive to the target, the social engineer must have an understanding of the target's mind. There are different modes of thinking that have been discussed in the previous section. These are very crucial in building this rapport. Additional information about understanding the target's brain will be discussed in Chapter 2, The Psychology of Social Engineering - Mind Tricks Used.
- Being in tune: Social engineers are always aware of themselves and their surroundings. This enables the social engineer to have an external view and note when the attack is or is not moving as expected. It is essential for any social engineer who wants to be very persuasive to be a master of both watching and listening. A social engineer is also human and will naturally give off some communication or signals to the target. However, a social engineer should be able to mask the true facial expressions, gestures, microexpressions, and even their breathing rate and replace them with faked ones according to the progress of the attack. Therefore, the social engineer should learn how to observe those signals as an external entity and judge his or her appeal to the target. He or she should be aware of nonverbal cues given by the body and tune them to suit the attack environment. This awareness will enable him or her to appeal continually to the target.
- Flexibility: Persuasion is not a guaranteed method of getting to a target. It is not a chemical reaction where certain reactants will lead to a certain result or solution. Sometimes, even with the best tricks, a target might not appear convinced or persuaded. This might call the social engineer to move out of the scripted attack and come up with other tricks that may eventually win the target over. Therefore, planning ahead is not always an assurance that the attack will work and in many instances, the social engineer will be required to adjust his or her methods.
- Reciprocation: This is one of the commonly used tactics for persuading targets. Reciprocation in this context refers to the characteristic of a target wanting to pay back a favor done by the social engineer. Humans are accustomed to this to the point that reciprocation is done almost unconsciously. It is a trick used to unconsciously control the minds of people into doing things in someone's favor. For instance, a pharmaceutical company that comes and gifts hospital staff with free things such as clothes, pens, books, and hats does not do this in vain. It knows that when it comes to selecting medicine for patients, staff will want to reciprocate the favors and end up picking the company's drugs over others. Reciprocation works in the same fashion as social engineering. It follows a four-step cycle which is discussed as follows:
- At first, the social engineer will give something valuable away
- The target that receives it gets an indebted feeling
- After some time, the social engineer will make a simple request
- The target will be more than willing to grant that request
With this, the social engineer gains control of the target's brain.
Persuasion will be discussed in more detail in future chapters. It is a very valuable tactic for any social engineer. It keeps the attack moving and ensures that the target is put in a position where he or she only can support the progress of the attack. As mentioned, it might not always pan out as expected and therefore there should be backup plans in all persuasion attempts. The social engineering roadmap is shown in the following figure:
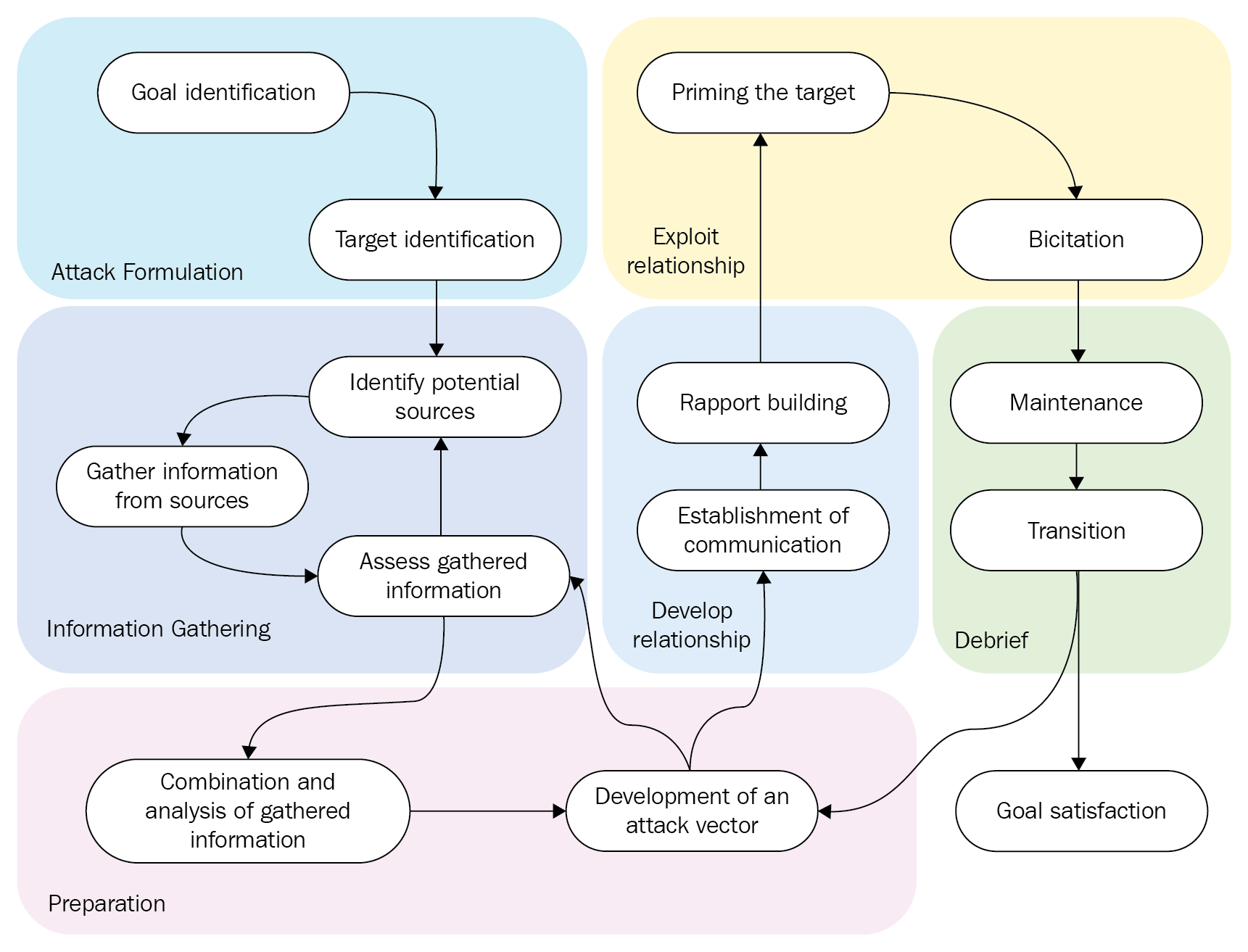
Tools used in social engineering
Social engineering is best done with the aid of tools so as to bring the social engineer closer to success. It is important to note that just owning or having access to the tools is not enough; one needs to understand the intrinsic details of how to use them effectively. That knowledge is the difference between success and failure. There are two main categories of tools used in social engineering—physical and software-based. To the social engineering framework, tools are normally a welcome addition as they complement the manual efforts of the social engineer.
Physical tools
Physical tools refer to all the tools used to facilitate a social engineering attack that does not involve the use of computers. Organizations and individuals invest in physical security measures to ensure that they limit physical access to a few authorized people. It is the reason why homes have doors, or even better, are surrounded by a fence and a gate. Social engineers will, if needed, have to break through all the physical security systems that their targets have put in place. There are a number of physical tools used which are as follows:
- Lock-picking tool: It is used to gain entry into places whose access is blocked by locks. Lock picking works on very many locks and this is why it is still a big threat today. Organizations are responding to lock picking by using more computerized physical access controls such as magnetic badge cards. It is surprising how organizations will protect thousand-dollar hardware using a $30 lock.
- Shove knife: This tool is used to gain access to doors that have knob locks. Many homes and server rooms will have these types of doors and a shove knife is the best tool to break into them. It slips into position and releases the latch. It does so without damaging the door.
- Bump key: A closely related tool is the bump key, which is a special key that has teeth designed to bump onto a lock's pins causing them to move to the right alignment and allow the plug to turn. Similarly, it does not damage the lock.
All the tools used to gain physical access are normally used to allow the social engineer to access some items or information that either finalizes or assists in the progress of an attack. For instance, a social engineer that has brought a target to the point of revealing a secret room in a house that contains a chest full of gems will use these tools to finalize the attack and steal the gems.
Software-based tools
Software-based social engineering tools are those that involve the use of computers. It is important to note that these are tools that can be used for many other purposes, not just social engineering. As a matter of fact, social engineers borrow some of these tools, which are discussed as follows, from people such as spies:
- GPS tracker: One of these is a GPS tracker. Is there a better way to accidentally bump into targets than tracking all their movements and knowing exactly where to find them? A good example is a $200 SpyHawk that is magnetically stuck on a target's car and uses GPS to send back the exact coordinates of the vehicle. Today, most of the software-based social engineering tools are online. They can gather information about a target from online sources.
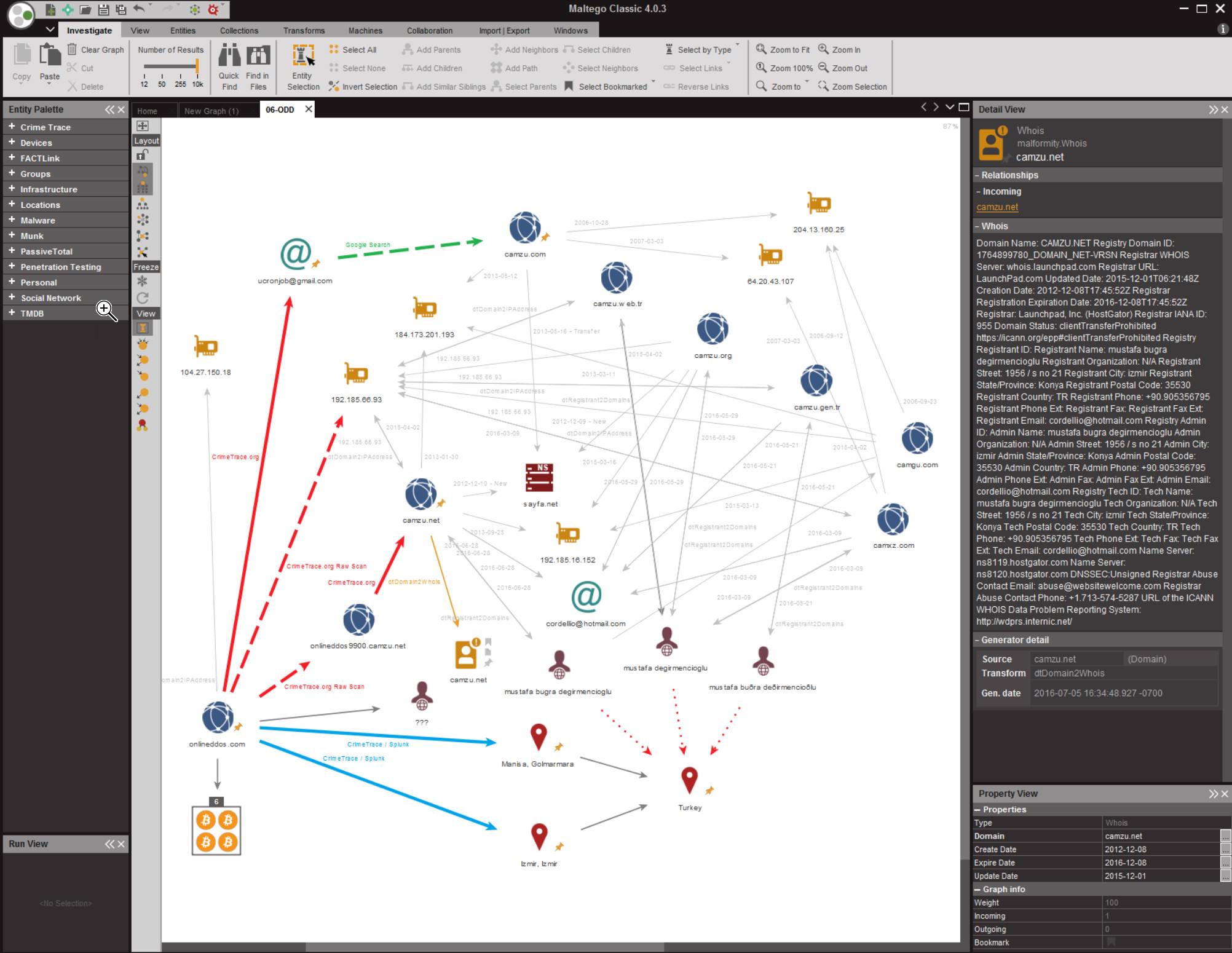
- Maltego: It is an online site that catalogs information about domains, IP addresses, organizations, and people among many other things. It is every social engineer's dream come true.
Maltego is able to bundle up the tiniest bits of information concerning a person, including reviews written on less-known e-commerce stores. It can find out information about a person, family members, relatives, close friends, and so many other details that it will be easy to find a weakness to hit the target with. From a social engineer's perspective, the main goal is to give the target an offer he or she cannot refuse. Natural greed will take care of the rest and soon enough the target will be begging for the offer:
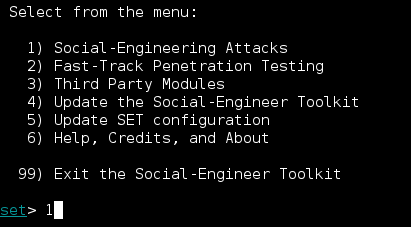
- Social Engineer Toolkit (SET): As the name suggests, the SET contains a set of tools that the social engineer can use in many attacks. Primarily, the kit is used to create malicious files that can be sent through email to targets. The main objective is to infect the target's device with malware that can be used either to collect more information or do malicious damage on the device. The SET is the primary tool used in spearfishing attacks. Once the target's email is known, the SET is left to do the conjuring of a spell: a file that will attack the target after it is downloaded and opened. The SET is also used to clone websites and host them. It can clone Facebook and send a target a link to allow Facebook authentication and when the target enters the credentials, an error is thrown back. This technique is used for mass information gathering, especially for credentials used in email and online banking systems.
Other software-based tools include spoofers and password profilers, among a variety of very many others.
The SET screenshot from Kali Linux is as follows:
Social engineering examples from Hollywood
It's really hard not to fall for a social engineer's trickery; it can be embarrassing, as long as it happens to someone else. Movies are great resources to help you understand social engineering better. The following are my top three Hollywood movies, which can help you to picture and learn how social engineering works:
Matchstick Men (2003)
Conmen Roy and Frank start their scam by calling victims and trying to sell their customers water filtration systems for hundreds of dollars, which were available for just $50 in actual stores. The two conmen use many classic social engineering moves, such as passing the phone from Frank to Roy who poses as Frank's boss, giving the operation more credibility and playing with victims minds to make everything more realistic and gain their victim's trust. There are many more social engineering techniques used during the story. It is a good way to visualize some of the techniques that you will read about in this book.
Catch Me If You Can (2002)
This is based on the life story of Frank Abagnale, who is one of the most infamous social engineers. He started his journey while he was a teenager. Abagnale ran away from home and managed to pose as a Pan Am pilot and scam thousands of miles of free flights around the world, making people believe that he was a real pilot.
This was not all. Abagnale also pretended to be a doctor and a teacher before he was caught by the FBI (years later). The movie is a good example of how social engineering is the art of human hacking, and how vulnerable we humans are.
Ocean's Eleven (2001)
Danny Ocean (George Clooney) and his 11 accomplices planned to rob three Las Vegas casinos simultaneously. Mr. Ocean and his accomplices used social engineering, technical smarts, and strategically placed insiders to penetrate the Bellagio's comprehensive, state-of-the-art security system and abscond with $160 million.
In this, even the best defenses could not immunize the organization against penetration by concerted adversaries.
Tips
Consider the tips as follows:
- There is no patch for human stupidity or, in other words, there is always a way to manipulate humans (as you will read about in this book). As a result, you or your employees are the most difficult and the biggest resource that you have to protect.
- Conduct a user awareness session often. There is always room for improvement in any social engineering training.
- Do not share anything sensitive with anyone. Keep in mind, once a secret is known by two people, it's not a secret anymore.
- If you are not sure about anything, proceed with caution.
- Ensure physical security.
- Classify information against dumpster-diving attacks. Even big corporations used this kind of attack in the past.
- Keep in mind, based on ISACA in 2016, social engineering was, at 52%, the top cyber threat facing organizations. Regardless of when you are reading this section, social engineering will be still one of most dangerous attack types
Summary
The overview of social engineering provided in this chapter has shown that there are very many aspects to this type of an attack. These range from mind tricks and persuasion tactics to online, software-based social engineering tools. The overview has brought out an important realization that human weaknesses can be exploited. The human brain can be hacked just as computers can. This makes it possible for social engineers to manipulate people into taking actions that they would normally not. The introduction has brought some level of awareness about the capabilities of social engineers, from mind reading to tracking movement using GPS locators. Future chapters will discuss all these in further detail. At the end of the final chapter, an avid reader will have acquired social engineering skills that will most likely be used teach you how social engineers think so you can protect against them.
The next chapter will start on the psychology of social engineering. It will discuss the mind tricks used and the techniques social engineers rely on to persuade targets. It will also take a deeper look into the modes of thinking of humans and how each can be exploited. The reader will also be taught how to interact with the target and gain information and win favors without raising alarms.

























