Security is a complex matter, and Java EE is not an exception to this rule. To make things even more complicated, WebLogic extends standard security with some important and useful features that will be explored in this chapter; they are as follows:
Identity Assertion
Credential Mappers
Java Authentication Service Provider Interface for Containers (JASPIC) and Java Authentication and Authorization Service (JAAS)
Java standard security is implemented with the security manager and policy files, and is extended by the Java Enterprise Edition in a completely transparent way for the developer; like every other service offered by the platform.
If you are an Enterprise Bean developer, you can develop knowing that the container will take care of the sensitive task of securing your data in the same way it takes care of remoting, translating from HTTP protocol to servlet method call, and transaction management. Obviously, it is impossible for the container to be aware of the infrastructure in which it will be deployed, so there are a lot of standard ways to extend it in order to let it work with a new RDBMS: installing the Java Database Connectivity (JDBC) driver JAR files or a new transactional resource that implements the resource adapter contract.
This principle applies to security as well; but until Java EE 6 there were no standard methods of implementing a new Authentication Provider, or whatever is inherent to security. As we'll see, this new version makes it mandatory that containers implement JASPIC 1.0, but many of them implement it in parallel and WebLogic 12c is no exception. If you need to implement something that is not "simple", custom Providers with custom API are required.
In Java EE, the developer interacts with the container using declarative annotations or XML descriptors. When you need to secure a URL managed by a servlet, all you need to do is annotate that servlet with the @ServletSecurity annotation along with a list of allowed roles, as shown in the following code snippet:
@WebServlet("/mysecuredurl")
@ServletSecurity(@HttpConstraint(rolesAllowed={"myrole"}))
public class MySecuredServlet extends HttpServlet {
...
}This single line of meta-code opens up the magic world of Java EE security, as explained in the following points:
If the user is not authenticated, the web container will ask him/her for his/her credentials; how the user will be asked depends on the configuration of the web application and the kind of client the user is using.
The user agent accepts the credentials and sends that information to the server. The server then tries to validate them using an Authentication Provider. If this is successful, a suitable container for user principals will be created (a Subject), and this will be mapped to the authenticating agent using a sort of session cookie.
Once the user principals are known, they are mapped to the application roles that are declared on the custom deployment descriptors of your application server.
If the servlet needs additional resources or needs to make a call to an EJB method, the security context will be "propagated" (see Java EE 6 specs, v.3.2, at http://www.oracle.com/technetwork/java/javaee/tech/index.html).
Every single step described here involves a bunch of very complex tasks, and all of them are free for the Java EE developer; they are made behind the curtain by the container.
WebLogic security architecture
is based on a set of classes in the weblogic.security.* package in the WebLogic Security Framework (WSF), which are used to develop Security Providers that run under the auspices of WebLogic Security Service.
This runtime is the orchestrator that allows application components such as EJBs and servlets to communicate with server resources, with the intermediation of the Security Provider.
Here, we will review some basic concepts of WSF that we need to understand to develop custom providers.
WebLogic follows the JAAS architecture of Java SE for its security infrastructure: Subjects, Principals, and Credentials. These are explained as follows:
Subject: Information related to the entity that is requesting the secured resources, such as identities (principal) or attributes (credentials)
Principal: Identity associated with the authenticated entity, such as its full name, the username, a Lightweight Directory Access Protocol (LDAP) group, and everything that identifies it
Credentials: Attributes related to the entity that is authenticated; they may be security-related, such as a Kerberos ticket (
sun.security.krb5.Credentials) or not security-related, such as attributes that are used by the application
In JAAS, when the login() method is called on the current LoginContext class, a new Subject object is created and the configured LoginModule is called in sequence to enrich that object with principals.
So, for instance, it is possible to configure a LoginModule interface that adds Kerberos credentials, another LoginModule, like WebLogic's UsernamePasswordLoginModule, that adds PasswordCredential. These are then used by WebLogic to access restricted resources.
Java EE 6 defines the security of components such as an EJB or a connection to an Enterprise Information System (EIS); WebLogic resources extend this level of security. The following is a quote defining resources from the official WebLogic 12c documentation:
A structured object used to represent an underlying WebLogic Server entity that can be protected from unauthorized access.
This means that a DataSource object can't be accessed directly but only through a JDBCResource object, and every resource is also represented as a hierarchy; if security is not specified for the leaf, its single parent can be inspected until a suitable configuration is found.
Suppose, for example, the container is checking if the user is allowed to access a certain method of an EJB, whose resource representation is as follows:
type=<ejb>, app=SecuredApp, module=EJBModule, ejb=VeryImportantEJB, method=callItSecure, methodInterface=Home, methodParams={String, int}If the EJBResource class can't find a suitable policy for that method, it will ask its parent, the Enterprise Bean, which can verify if the user is allowed or not.
Java Management Extensions (JMX) is a mandatory part of the Java EE 6 specification that defines standards for the monitoring and management of Enterprise applications in a dynamic and nonintrusive way. Using JMX, it is possible to query an arbitrary application for diagnostic information without knowing anything about the way it is being implemented, but only using a standard tool like JConsole or VisualVM. This is implemented in a structured way, where JMX defines the runtime, the way Management Beans are developed, and how to access that information. Implementation is straightforward; you only need to define what you want to, as follows:
@MXBean
public interface MyManagedProperties {
public int getCached();
public void callOperation();
}And the implementation—in Java EE 6 it's really a few lines of code—is as follows:
@Singleton
@Startup
public class MyManagedPropertiesBean implements MyManagedProperties {
private MBeanServer platformMBeanServer;
private ObjectName objectName = null;
@PostConstruct
public void registerInJMX() {
try {
objectName = new ObjectName("MyMXBean :type=" + this.getClass().getName());
InitialContext ctx = new InitialContext();
platformMBeanServer = (MBeanServer) ctx.lookup("java:comp/env/jmx/runtime");
ctx.close();
platformMBeanServer.registerMBean(this, objectName);
} catch (Exception e) {
throw new IllegalStateException("Problem during registration of Monitoring into JMX:" + e);
}
}
public int getCached() {//doSomething}
public void callOperation() {//doSomething}
@PreDestroy
public void unregisterFromJMX() {
try {
platformMBeanServer.unregisterMBean(this.objectName);
} catch (Exception e) {
throw new IllegalStateException("Problem during unregistration of Monitoring into JMX:" + e);
}
}
}An MXBean interface is implemented in the previous code; it is a Managed Bean that can be accessed by a JMX client, which doesn't need to know anything about our application. It is the duty of the agent to convert every domain-specific class to simple properties.
Unfortunately, developing MBeans for WebLogic is not that easy, because of a custom way to generate the MBeans that execute in the MBeanServer interface. It is necessary to write a custom XML file, called
MBean Definition File (MDF), and then generate a JAR file that can be installed on the WebLogic server using WebLogic's MBeanMaker tool.
Developing an Authentication Provider is a fairly complex task with many concepts that need to be understood. Here, we will introduce the concepts regarding the composing parts of a provider and different kinds of authentication.
Authentication is completely delegated to entities called Authentication Providers, which are a set of classes and configuration files that incorporate an MBean and a LoginModule interface. Every time you request a protected resource, every configured Provider is requested to add the principals extracted from the credentials provided.
This mechanism is very similar to the one configurable on the client with only JAAS (and jaas.config); the main difference is that it's done with the administration console. This console allows us to configure parameters visually, through the automatically-generated JSP page, without touching any XML file, as shown in the following screenshot:

Under WebLogic Security Framework, everything is wrapped by MBeans. The standard JAAS security infrastructure is created and invoked using an MBean, which can be configured using the standard console. This makes sense because the console and every utility that runs under the WebLogic ecosystem has to be consistent and there are a lot of technologies around Java that have to be integrated.
So, if you need to implement your own LoginModule interface, remember that you need to "decorate" it with the correct MBean, which in turn is automatically generated for you by the WebLogic MBeanMaker tool.
Every Provider has only one chance to contribute to the authentication process: it receives Credentials and eventually adds Principals to the current Subject. This scenario of security has very limited potentialities if interaction with the user agent is required. For example, for negotiating an authentication mechanism, redirecting to a remote login site, or even implementing a challenge/response handshake, this is a suitable task for servlet filters, but if they are configured for a protected resource they are not called until you are authenticated.
WebLogic Security Framework gives developers a chance to return an array of filters that are executed on behalf of the standard Authentication mechanism, but not under the application component's security context.
A lot of organizations have heterogeneous systems that need security services, and many of these systems interact with users that have already declared who they are, for example, during the login phase of their workstation at the beginning of their working day.
This is the basis to introduce the concept of a Perimeter, where authentication is made once and then always trusted during the day. The same happens when you use your badge to enter into your company; you are trusted to be allowed into the buildings, with the need to expose the badge to express that you are an employee. In case of Perimeter Authentication, a token released by a third party is used to extract who the user is, by performing an Identity Assertion and not full authentication.
This means that when developing LoginModule interfaces for Identity Assertion providers, Credentials are used not to decide if the user is authenticated, but simply to populate the Subject with the Principals that can be found using the token.
Prior to Java EE 6 and the introduction of the SecurityContext interface in Java EE Connector Architecture (JCA) 1.6 specification (see the SecurityContext interface in JCA 1.6 specifications at http://jcp.org/en/jsr/detail?id=322), there were no standard ways to map the current SecurityContext security object to the ConnectionSpec interface of a resource adapter.
This could mean the following two things:
No end-to-end Single Sign-On from the user to the EIS
Code into application components that implement mapping of credentials
WebLogic Security Framework supports the mapping of credentials from the current authenticated user to a format that can be understood by the resource adapter/EIS.
The implementation is really straightforward. Before calling the execute()method on the interaction in the ConnectionSpec interface, the Mapper is asked to convert the current Credentials stored into the Subject into one or more Credentials valid for the remote system.
Currently, if BasicPassword is the current authentication mechanism type and PasswordCredential is the interface that has to be used for the communication, it's sufficient for the developer of the custom Credentials Mapping provider to write a function that maps the local security space to that of the called EIS.
Conceptually, this is not much different from what is done with Identity Assertion and Perimeter Authentication; but this time the trust is between WebLogic and an external system, with the former responsible for security. Of course, there may also be Mappings that are able to make full authentication, but in both cases the weak link is the Java Application Server that has the chance to authenticate users to a remote system.
After so many pages talking about security and how to implement it in WebLogic, the question is: why is all this custom-made and not regulated by Java EE?
Java EE 6 has the correct answer to this question: the JASPIC 1.0 specification, a message processing framework that is protocol-independent and that can do what an Authentication Provider does for us; that is, populate Subjects with Principals and therefore authenticate a remote user agent.
In a manner that is different from WebLogic Security Framework, where everything is inside a secure framework API because the message and the protocol are managed by the application server, this is done at the message level. In this way, it enforces the concept that security is something related to the protocol and the way information is exchanged.
In fact, currently we have three profiles that are part of the standard specification, one that is able to authenticate HTTP clients, another that works with SOAP messages, and a third profile that tries to bridge the new specification with the existing JAAS login module on the market.
This is the first implementation in WebLogic and its immaturity is apparent from the total lack of documentation and the fact that the configuration is not integrated into the custom deployment descriptors. So, consider using it only on noncritical systems.
Java Authorization Contract for Containers (JACC) is an extension of the standard policy-based security of the JVM for role mapping and authorization of servlets and EJBs. The working of this policy-based security is shown in the following screenshot:
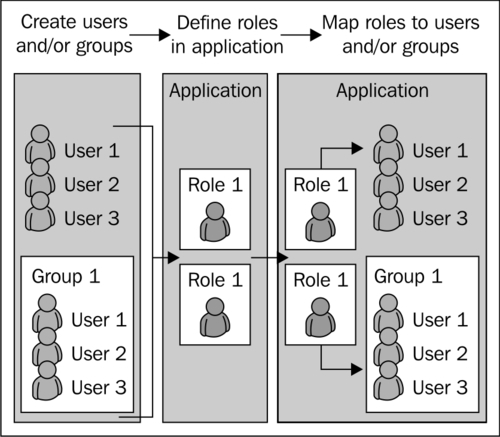
Although it is implemented by WebLogic, Oracle itself discourages its use because of the lack of features and flexibility compared to custom providers, and also because of performance issues. For these reasons, JACC will not be covered in this book.
This chapter was a quick introduction to WebLogic security fundamentals learning theory that will be used later when a custom provider will be developed or configured inside our domain using the WebLogic console.
It started from Java EE security and then declined to the WebLogic Security Framework, from MBeans to resources.
Finally, two Java Specification Requests (JSR) specs were covered, JASPIC and JACC, to show how limited they are compared to custom providers.